信息网络安全 ›› 2020, Vol. 20 ›› Issue (7): 19-29.doi: 10.3969/j.issn.1671-1122.2020.07.003
基于字节码搜索的Java反序列化漏洞调用链挖掘方法
- 北京大学软件与微电子学院,北京 100080
-
收稿日期:2020-05-02出版日期:2020-07-10发布日期:2020-08-13 -
通讯作者:文伟平 E-mail:weipingwen@ss.pku.edu.cn -
作者简介:杜笑宇(1996—),女,北京,硕士研究生,主要研究方向为网络安全、Web攻击与漏洞挖掘|叶何(1998—),男,安徽,硕士研究生,主要研究方向为网络安全、系统安全、云计算|文伟平(1977—),男,湖南,教授,博士,主要研究方向为系统与网络安全、大数据与云安全、智能计算安全 -
基金资助:国家自然科学基金(61872011)
Java Deserialization Vulnerability Gadget Chain Discovery Method Based on Bytecode Search
DU Xiaoyu, YE He, WEN Weiping( )
)
- School of Software and Microelectronics, Peking University, Beijing 100080, China
-
Received:2020-05-02Online:2020-07-10Published:2020-08-13 -
Contact:Weiping WEN E-mail:weipingwen@ss.pku.edu.cn
摘要:
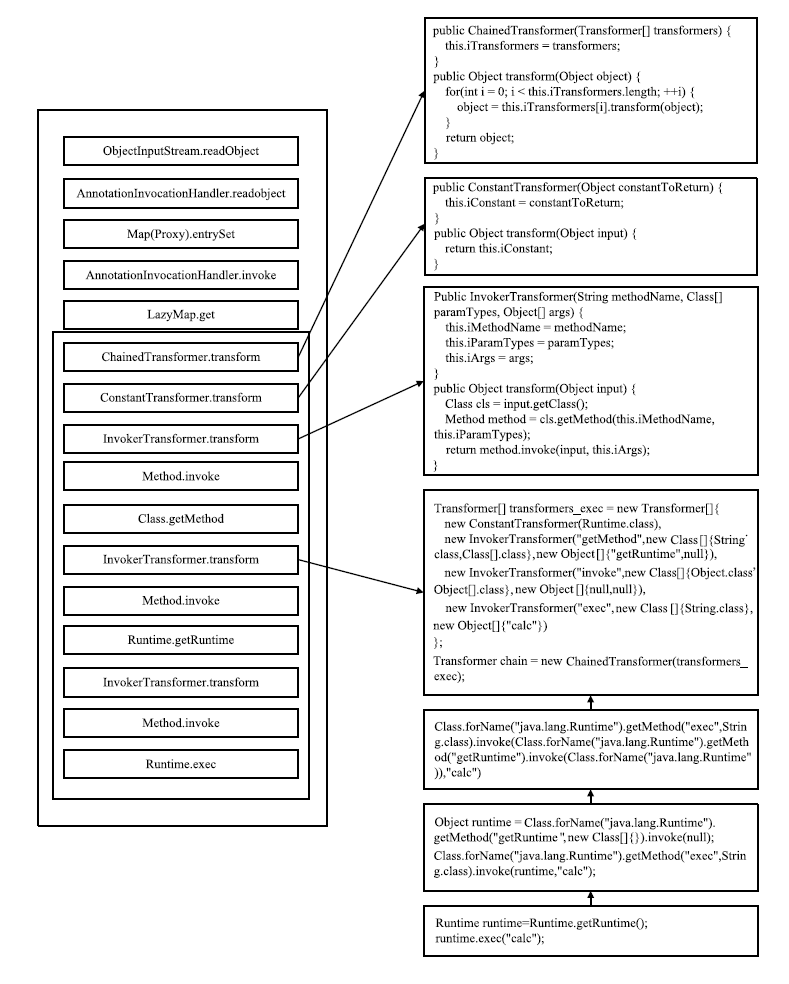
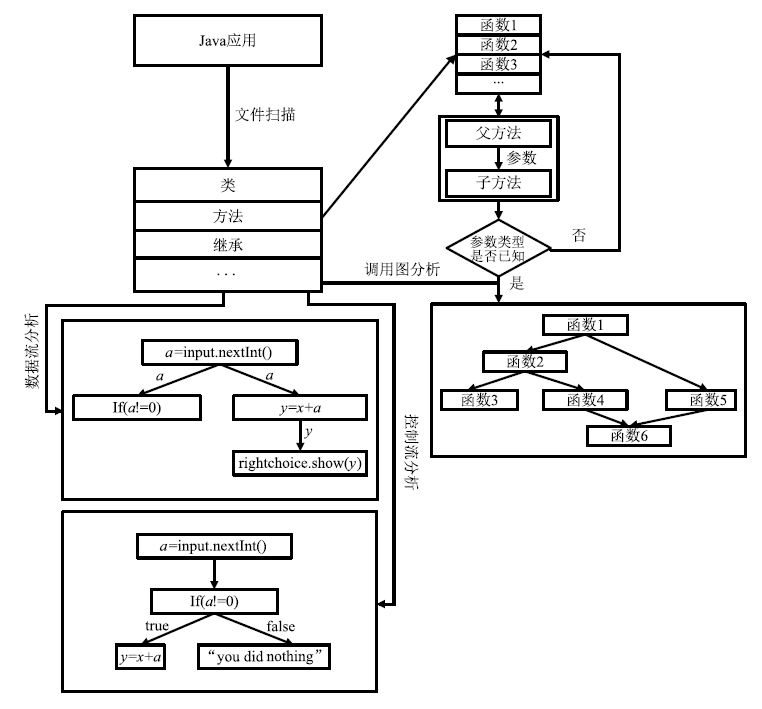
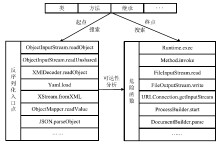
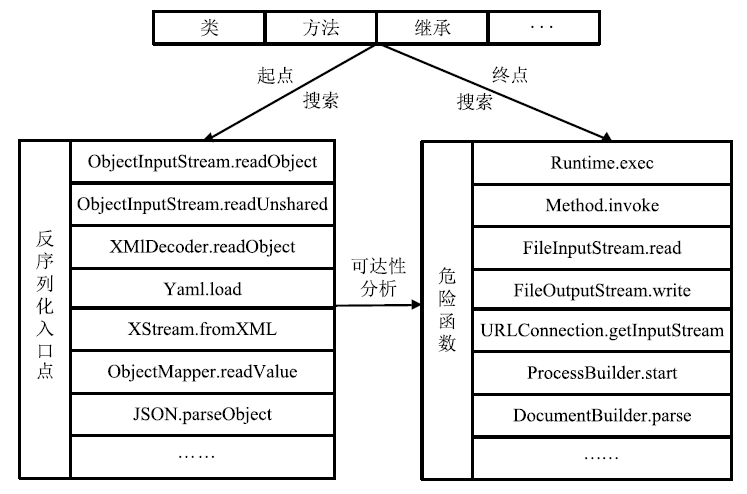
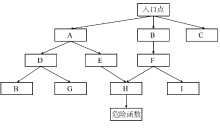
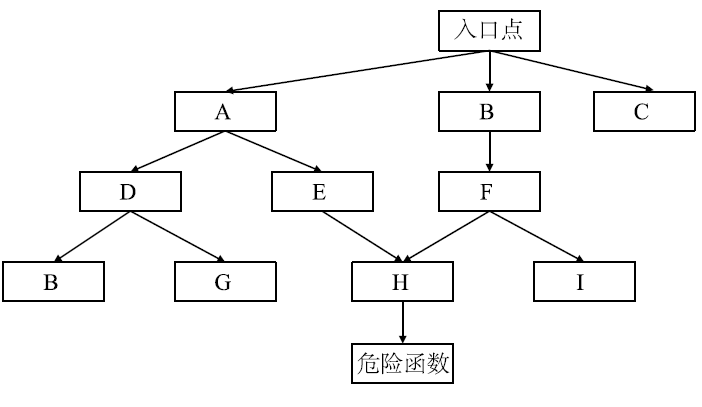
反序列化漏洞是近年来应用安全研究的热点之一。随着Java类库的功能不断更新和扩展,反序列化漏洞的潜在范围更加广泛。手工进行反序列化漏洞挖掘需要大量的时间和人力对调用链进行筛查和构造。文章介绍了Java反序列化漏洞的原理、常见场景和反序列化漏洞调用链的构造方法,并结合常见的漏洞挖掘方法,提出一种调用链挖掘方法,同时将该方法实现为调用链挖掘工具Zero Gadget。文章方法采用污点分析与符号执行技术生成从反序列化漏洞入口点到危险函数的调用树,利用深度优先搜索算法搜索调用树并生成相关调用链。文章选取常见的Java基础库进行调用链挖掘效果的测试。实验结果表明,文章方法可成功挖掘潜在调用链并具有较高的准确率,对于反序列化漏洞调用链的自动化挖掘有着积极的意义。
中图分类号:
引用本文
杜笑宇, 叶何, 文伟平. 基于字节码搜索的Java反序列化漏洞调用链挖掘方法[J]. 信息网络安全, 2020, 20(7): 19-29.
DU Xiaoyu, YE He, WEN Weiping. Java Deserialization Vulnerability Gadget Chain Discovery Method Based on Bytecode Search[J]. Netinfo Security, 2020, 20(7): 19-29.
表1
部分解析库/组件及其相关漏洞
| 库名称 | 类别 | 相关漏洞 |
|---|---|---|
| Jackson | JSON | CVE-2017-7525、CVE-2017-15095、CVE-2019-12384 |
| SnakeYAML | YAML | CVE-2016-9606、CVE-2017-3159、CVE-2016-8744 |
| BlazeDS | AMF4 | CVE-2017-3066、CVE-2017-5641 |
| Red5 IO AMF | AMF | CVE-2017-5878 |
| XMLDecoder | XML | CVE-2017-3506、CVE-2017-10352、CVE-2019-2725 |
| Hessian | binary/XML | CVE-2019-9212、CVE-2017-12633 |
| XStream | XML/various | CVE-2017-7947、CVE-2017-9805、CVE-2019-10173 |
| Weblogic | Middleware | CVE-2015-4852、CVE-2016-0638、CVE-2016-3510 |
| JBoss | Middleware | CVE-2017-7504 、CVE-2017-12149 |
| ActiveMQ | Middleware | CVE-2015-5254 |
| Jenkins | Application | CVE-2015-8103、CVE-2016-0792、CVE-2016-9299 |
| Apache Log4j | Components | CVE-2017-5645、CVE-2017-17571 |
| …… | …… | …… |
表3
Gadget Inspector对于Commons-collections-3.2.1的搜索结果
| 序号 | 入口点 | 关键点 |
|---|---|---|
| 1 | org/apache/log4j/spi/LoggingEvent.readObject | org/apache/log4j/spi/LoggingEvent. readLevel |
| 2 | org/apache/log4j/pattern/LogEvent.readObject | org/apache/log4j/pattern/LogEvent.readLevel |
| 3 | java/awt/Component.readObject | org/apache/commons/collections/map/DefaultedMap.get |
| 4 | com/sun/corba/se/spi/orbutil/proxy/CompositeInvocationHandlerImpl.invoke | org/apache/commons/collections/map/DefaultedMap.get |
表4
Zero Gadget对于Commons-collections-3.2.1发现的额外调用链
| 序号 | 入口点 | 关键点 |
|---|---|---|
| 1 | sun/reflect/annotation/Annotation- InvocationHandler.readObject | org/apache/commons/collections/map/LazyMap.get |
| 2 | java/util/HashSet.readObject | org/apache/commons/collections/map/LazyMap.get |
| 3 | java/util/Hashtable.readObject | org/apache/commons/collections/functors/InstantiateTransformer |
表5
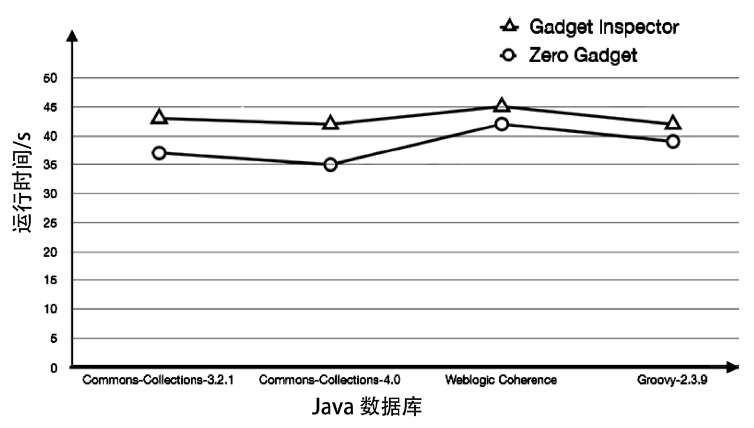
两个工具对于Commons-Collections-4.0、Weblogic Coherence和Groovy-2.3.9的部分挖掘结果
| 库名 | Gadget Inspector | Zero Gadget |
|---|---|---|
| Commons- Collections 4.0 | (1)org/apache/log4j/spi/Logging-Event.readObject (2)org/apache/log4j/pattern/Log-Event.readObject | (1)java/util/PriorityQueue.read-Object (2)org/apache/log4j/spi/LoggingEvent. readObject (3)org/apache/log4j/pattern/LogEvent. readObject (4)org/apache/commons/collections4/bag/TreeBag.readObject |
| Weblogic Coherence | (1)com/tangosol/coherence/com- ponent/util/Daemon.finalize (2)org/apache/log4j/spi/Logg-ingEvent.readObject (3)java/security/cert/Certificate-RevokedException.readObject (4)org/apache/log4j/pattern/Log-Event.readObject (5)com/tangosol/coherence/com-ponent/util/Daemon.finalize | (1)javax/management/BadAttribute-ValueExpException.readObject (2)com/tangosol/coherence/Component (3)com/tangosol/coherence/component/application/console/Coherence$ CacheItem.readObject (4)org/apache/log4j/pattern/LogEvent.readObject (5)org/apache/log4j/spi/LoggingEvent.readObject |
| Groovy- 2.3.9 | (1)org/apache/log4j/pattern/Log-Event.readObject (2)org/apache/log4j/spi/Logging-Event.readObject (3)org/codehaus/groovy/trans-form/tailrec/TailRecursiveAST Transformation$_replaceRecur-siveReturnsInsideClosures_closure9. doCall (4)org/codehaus/groovy/runtime/MethodClosure.doCall | (1)java/util/PriorityQueue.readObject (2)org/apache/log4j/pattern/LogEvent. readObject (3)org/apache/log4j/spi/LoggingEvent. readObject (4)org/codehaus/groovy/runtime/Me-thodClosure.doCall (5)org/codehaus/groovy/transform/tailrec/TailRecursiveASTTransfor-mation$_replaceRecursiveReturns-InsideClosures_closure9.doCall |
| [1] | SCHOENEFELD M. Pentesting J2EE[EB/OL]. https://www.researchgate.net/publication/267774292_Pentesting_J2EE, 2020-4-29. |
| [2] | LAWRENCE G,. Marshalling Pickles[EB/OL]. http://frohoff.github.io/appseccali-marshalling-pickles/, 2020-4-29. |
| [3] | MUNOZ A. Friday the 13th: JSON Attacks[EB/OL]. https://www.blackhat.com/docs/us-17/thursday/us-17-Munoz-Friday-The-13th-Json-Attacks.pdf, 2020-4-29. |
| [4] | BALZAROTTI D, COVA M, FELMETSGER V, et al. Saner: Composing Static and Dynamic Analysis to Validate Sanitization in Web Applications[C]// IEEE. 2008 IEEE Symposium on Security and Privacy (sp 2008), May 18-22, 2008, Oakland, CA, USA. NJ: IEEE, 2008: 387-401. |
| [5] | KING J C. Symbolic Execution and Program Testing[J]. Communications of the ACM, 1976,19(7):385-394. |
| [6] | SONG Xuejiao. Research and Application of Symbolic Execution in Software Security[D]. Chengdu: Xihua University, 2018. |
| 宋雪勦. 符号执行在软件安全领域中的研究与应用[D]. 成都:西华大学, 2018. | |
| [7] | GODEFROID P, KLARLUND N, SEN K. DART: Directed Automated Random Testing[J]. ACM SIGPLAN Notices, 2005,40(6):213-223. |
| [8] | XIE Yichen, AIKEN A. Static Detection of Security Vulnerabilities in Scripting Languages[C]// USENIX. The 15th Conference on USENIX Security Symposium, July 31-August 4, 2006, Vancouver, B. C. , Canada.Berkeley: USENIX Association, 2006: 179-192. |
| [9] | TRIPP O, PISTOIA M, COUSOT P, et al. Andromeda: Accurate and Scalable Security Analysis of Web Applications[M]// Springer. Fundamental Approaches to Software Engineering. Heidelberg: Springer, Berlin, Heidelberg, 2013: 210-225. |
| [10] | CHEN Zhe, WANG Xiaojuan, ZHANG Xinxin. Dynamic Taint Analysis with Control Flow Graph for Vulnerability Analysis[C]// IEEE. 2011 First International Conference on Instrumentation, Measurement, Computer, Communication and Control, October 21-23, 2011, Beijing, China. NJ: IEEE, 2011: 228-231. |
| [11] | WANG Lei, LI Feng, LI Lian, et al. Principle and Practice of Taint Analysis[J]. Journal of Software, 2017,28(4):860-882. |
| 王蕾, 李丰, 李炼, 等. 污点分析技术的原理和实践应用[J]. 软件学报, 2017,28(4):860-882. | |
| [12] | JOVANOVIC N, KRUEGEL C, KIRDA E. Static Analysis for Detecting Taint-style Vulnerabilities in Web Applications[J]. Journal of Computer Security, 2010,18(5):861-907. |
| [13] | LIVSHITS B, LAM M S. Finding Security Vulnerabilities in Java Applications with Static Analysis[EB/OL]. , 2020-4-29. |
| [14] | ALHUZALI A, GJOMEMO R, ESHETE B, et al. NAVEX: Precise and Scalable Exploit Generation for Dynamic Web Applications[C]// USENIX. The 27th USENIX Conference on Security Symposium, August 15-17, 2018, Baltimore, MD, USA. Berkeley: USENIX Association, 2018: 377-392. |
| [15] | BALZAROTTI D, COVA M, FELMETSGER V, et al. Saner: Composing Static and Dynamic Analysis to Validate Sanitization in Web Applications[C]// IEEE. 2008 IEEE Symposium on Security and Privacy (sp 2008), May 18-22, 2008, Oakland, CA, USA. NJ: IEEE, 2008: 387-401. |
| [16] | FELMETSGER V, CAVEDON L, KRUEGEL C, et al. Toward Automated Detection of Logic Vulnerabilities in Web Applications[EB/OL]. https://www.usenix.org/legacy/events/sec10/tech/full_papers/Felmetsger.pdf, 2020-4-29. |
| [17] | CARETTONI L. Defending against Java Deserialization Vulnerabilities[EB/OL]. https://www.ikkisoft.com/stuff/Defending_against_Java_Deserialization_Vulnerabilities. pdf, 2020-4-29. |
| [18] | HAKEN I. Automated Discovery of Deserialization Gadget Chains[EB/OL]. https://i.blackhat.com/us-18/Thu-August-9/us-18-Haken-Automated-Discovery-of-Deserialization-Gadget-Chains-wp.pdf, 2020-4-29. |
| [19] | GUO Rui. Research of Java Deserialization Vulnerability[J]. Information Security and Technology, 2016,7(3):27-30. |
| 郭瑞. Java反序列化漏洞研究[J]. 信息安全与技术, 2016,7(3):27-30. | |
| [20] | ERNST P. Look-ahead Java Deserialization[EB/OL]. https://www.ibm.com/developerworks/library/se-lookahead/, 2013-1-15. |
| [21] | ORACLE . The Java Tutorials[EB/OL]. https://docs.oracle.com/javase/tutorial/reflect/index. html, 2020-4-29. |
| [1] | 陈震杭, 王张宜, 彭国军, 夏志坚. 针对未知PHP反序列化漏洞利用的检测拦截系统研究[J]. 信息网络安全, 2018, 18(4): 47-55. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||