信息网络安全 ›› 2024, Vol. 24 ›› Issue (2): 272-281.doi: 10.3969/j.issn.1671-1122.2024.02.010
一种基于深度学习的SRv6网络流量调度优化算法
- 1.华中科技大学网络空间安全学院,武汉 430074
2.华中科技大学网络与计算中心,武汉 430074
-
收稿日期:2023-10-18出版日期:2024-02-10发布日期:2024-03-06 -
通讯作者:于俊清 E-mail:yjqing@hust.edu.cn -
作者简介:赵鹏程(1996—),男,湖北,硕士研究生,主要研究方向为网络安全、软件定义网络|于俊清(1975—),男,内蒙古,教授,博士,CCF会员,主要研究方向为数字媒体处理与检索、网络安全、多核计算与流编译|李冬(1979—),男,湖北,高级工程师,博士,主要研究方向为计算机网络、软件定义网络、网络安全 -
基金资助:国家重点研发计划(2020YFB1805601);中国高校产学研创新基金(2021FNA02005)
An Optimal Algorithm for Traffic Scheduling in SRv6 Network Based on Deep Learning
ZHAO Pengcheng1, YU Junqing1,2( ), LI Dong2
), LI Dong2
- 1. School of Cyber Science and Engineering, Huazhong University of Science and Technology, Wuhan 430074, China
2. Network and Computation Center, Huazhong University of Science and Technology, Wuhan 430074, China
-
Received:2023-10-18Online:2024-02-10Published:2024-03-06 -
Contact:YU Junqing E-mail:yjqing@hust.edu.cn
摘要:
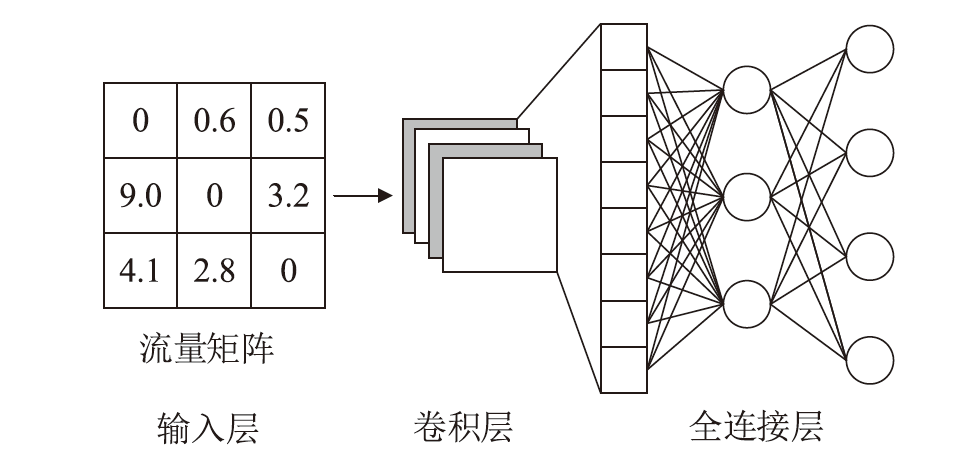
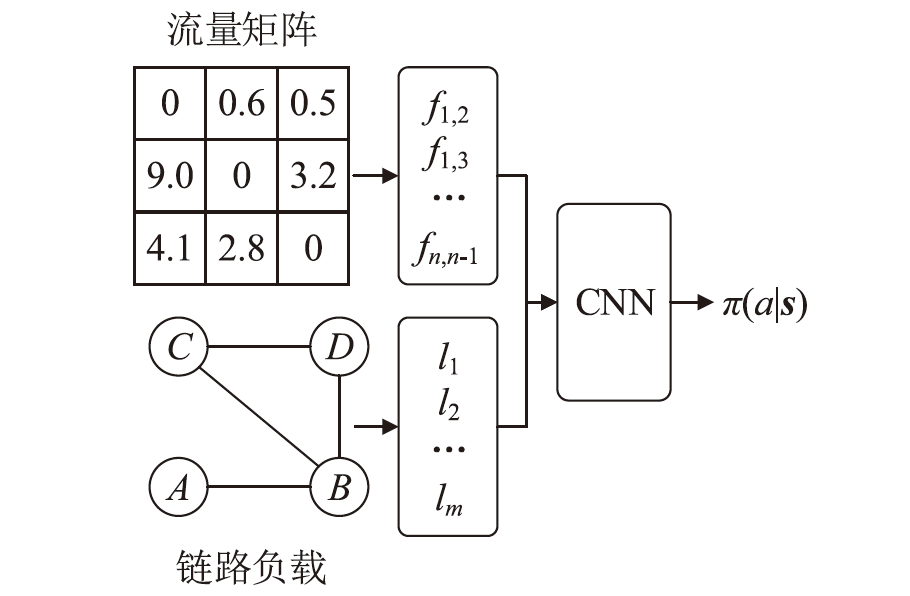
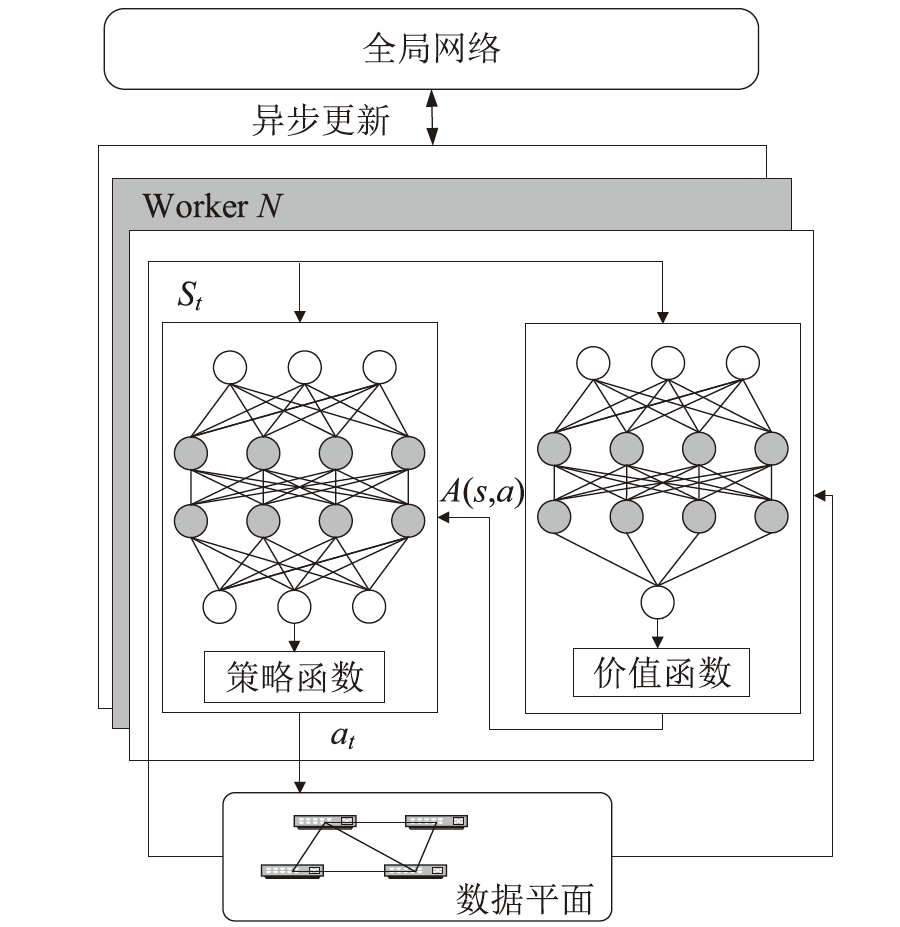
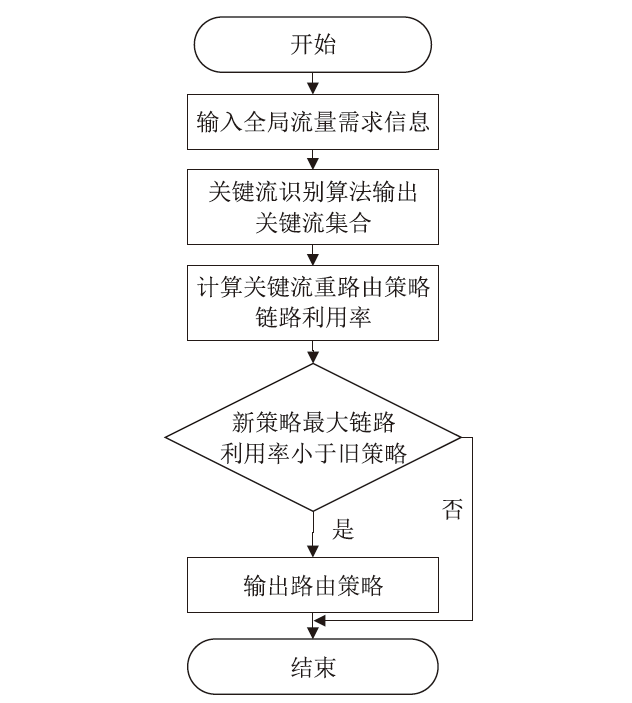
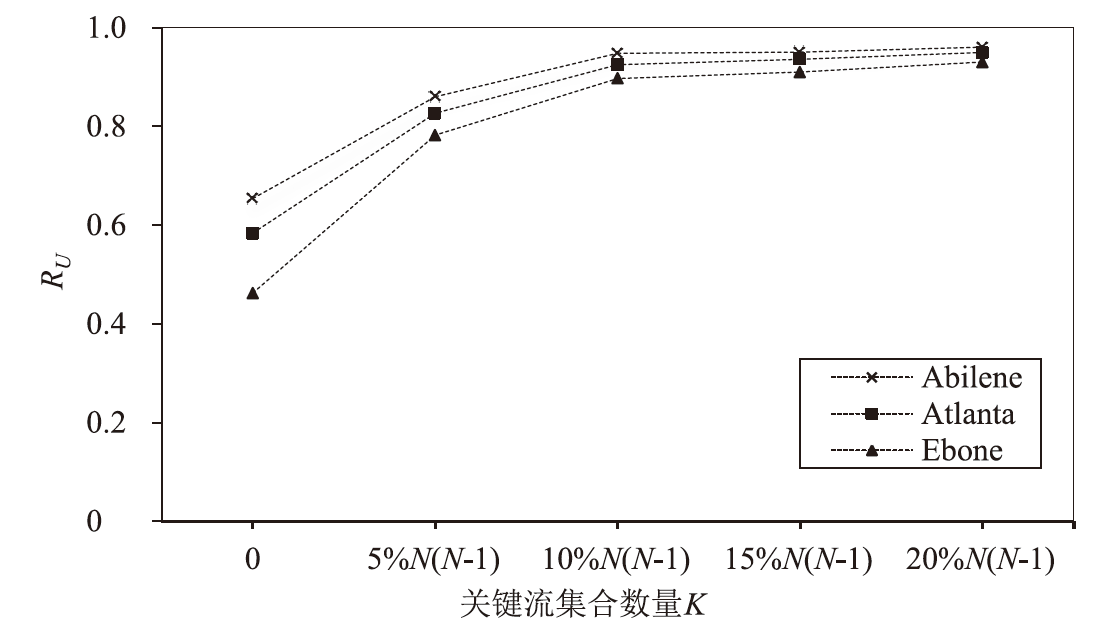
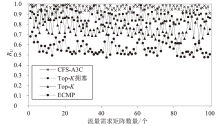
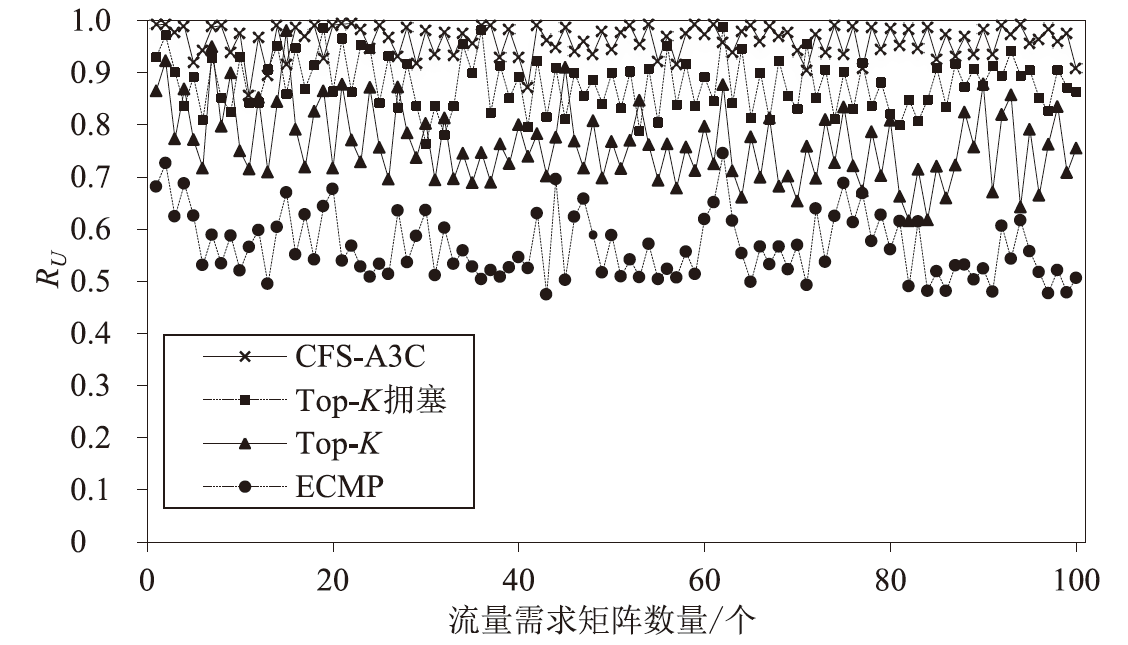
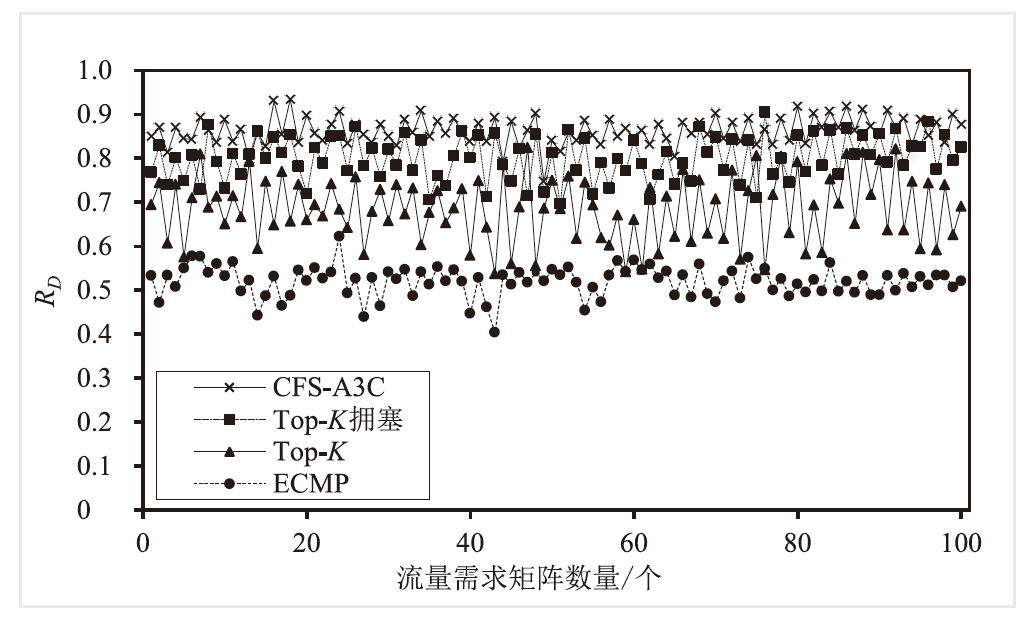
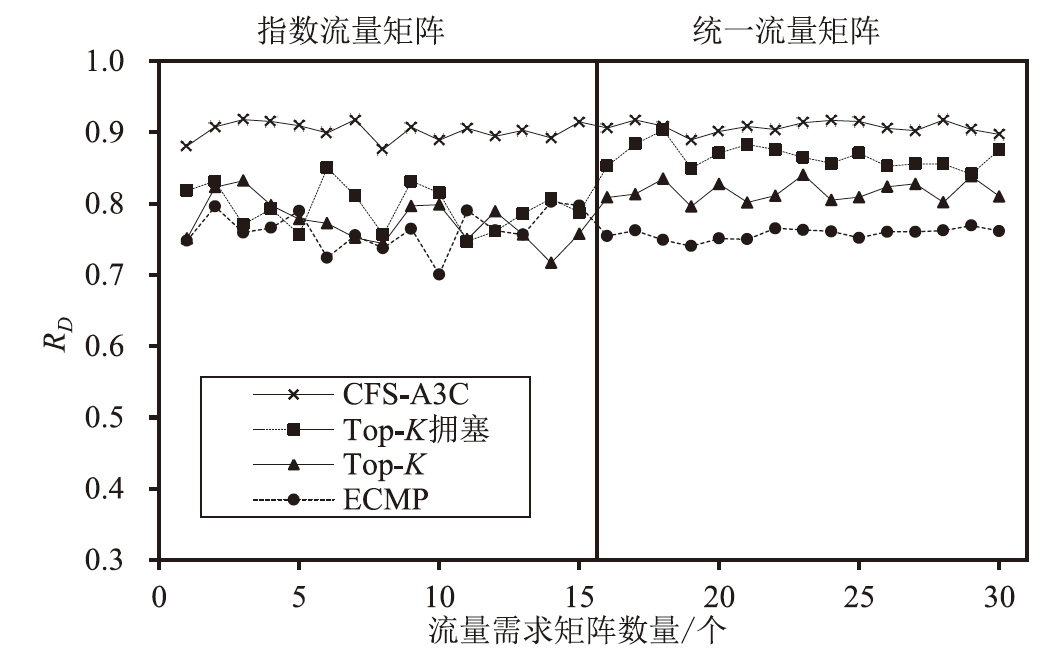
目前SRv6网络中的流量调度方法主要是基于固定或启发式规则的方法,缺乏灵活调度整体网络流量的能力,难以适应动态的网络环境变化。针对SRv6网络缺乏关键流识别能力的问题,文章提出一种基于深度强化学习的关键流识别算法,建立适应网络动态变化的关键流学习模型,在不同的流量矩阵中识别出对网络性能影响最大的关键流集合。针对SRv6网络流量调度问题,文章提出一种基于关键流的流量调度优化算法,采用线性规划求解出每一条关键流的最优显式路径,并采用不同的路由方式对普通流和关键流进行负载均衡。实验结果表明,该算法可显著提升SRv6网络流量负载均衡能力,降低网络端到端传输延迟。
中图分类号:
引用本文
赵鹏程, 于俊清, 李冬. 一种基于深度学习的SRv6网络流量调度优化算法[J]. 信息网络安全, 2024, 24(2): 272-281.
ZHAO Pengcheng, YU Junqing, LI Dong. An Optimal Algorithm for Traffic Scheduling in SRv6 Network Based on Deep Learning[J]. Netinfo Security, 2024, 24(2): 272-281.
| [1] |
KREUTZ D, RAMOS F M V, VERISSIMO P E, et al. Software-Defined Networking: A Comprehensive Survey[J]. Proceedings of the IEEE, 2014, 103(1): 14-76.
doi: 10.1109/JPROC.2014.2371999 URL |
| [2] | VENTRE P L, SALSANO S, POLVERINI M, et al. Segment Routing: A Comprehensive Survey of Research Activities, Standardization Efforts, and Implementation Results[J]. IEEE Communications Surveys & Tutorials, 2020, 23(1): 182-221. |
| [3] |
CHENG Weiqiang, LIU Yisong, JIANG Wenying, et al. Research and Application of G-SRv6 Head Compressions Optimization Technology[J]. Telecommunications Science, 2020, 36(8): 22-27.
doi: 10.11959/j.issn.1000-0801.2020254 |
|
程伟强, 刘毅松, 姜文颖, 等. G-SRv6 头压缩优化技术研究与应用[J]. 电信科学, 2020, 36(8):22-27.
doi: 10.11959/j.issn.1000-0801.2020254 |
|
| [4] |
WU Wei, ZHANG Wenqiang, YANG Guangming, et al. SRv6 +EVPN Technology Research and Scale Deployment of 5G Bearer Network[J]. Telecommunications Science, 2020, 36(8): 43-52.
doi: 10.11959/j.issn.1000-0801.2020253 |
|
吴伟, 张文强, 杨广铭, 等. 5G 承载网的“SRv6+ EVPN”技术研究与规模部署[J]. 电信科学, 2020, 36(8):43-52.
doi: 10.11959/j.issn.1000-0801.2020253 |
|
| [5] |
CHEN Kefan, ZHAO Shanghou, LV Na, et al. Segment Routing Based Traffic Scheduling for the Software-Defined Airborne Backbone Network[J]. IEEE Access, 2019, 7: 106162-106178.
doi: 10.1109/ACCESS.2019.2930229 |
| [6] | STAMPA G, ARIAS M, SÁNCHEZ-CHARLES D, et al. A Deep-Reinforcement Learning Approach for Software-Defined Networking Routing Optimization[EB/OL]. (2017-09-20)[2023-08-10]. https://arxiv.org/abs/1709.07080.pdf. |
| [7] | CASAS N. Deep Deterministic Policy Gradient for Urban Traffic Light Control[EB/OL]. (2017-03-27)[2023-08-10]. https://arxiv.org/pdf/1703.09035.pdf. |
| [8] | TENG Yuantao, XIA Zhengyou. A Traffic Engineering Technology Based on Segment Routing in SDN[C]// IEEE. 2020 16th International Conference on Mobility, Sensing and Networking(MSN). New York:IEEE, 2020: 636-641. |
| [9] | LI Cheng, MAO Jianwen, PENG Shuping, et al. Application-Aware G-SRv6 Network Enabling 5G Services[C]// IEEE. 2021 IEEE Conference on Computer Communications Workshops(INFOCOM WKSHPS). New York:IEEE, 2021: 1-2. |
| [10] |
REN Bangbang, GUO Deke, YUAN Yali, et al. Optimal Deployment of SRv6 to Enable Network Interconnection Service[J]. IEEE/ACM Transactions on Networking, 2021, 30(1): 120-133.
doi: 10.1109/TNET.2021.3105959 URL |
| [11] |
ANAND R, AGGARWAL D, KUMAR V. A Comparative Analysis of Optimization Solvers[J]. Journal of Statistics and Management Systems, 2017, 20(4): 623-635.
doi: 10.1080/09720510.2017.1395182 URL |
| [12] | MAO Hongzi, ALIZADEH M, MENACHE I, et al. Resource Management with Deep Reinforcement Learning[C]// ACM. 15th ACM Workshop on Hot Topics in Networks. New York: ACM, 2016: 50-56. |
| [13] | WILLIAMS R J. Simple Statistical Gradient-Following Algorithms for Connectionist Reinforcement Learning[J]. Reinforcement Learning, 1992, 8: 5-32. |
| [14] | JIANG J R, HUANG H W, LIAO J H, et al. Extending Dijkstra’s Shortest Path Algorithm for Software Defined Networking[C]// IEEE. The 16th Asia-Pacific Network Operations and Management Symposium. New York: IEEE, 2014: 1-4. |
| [15] |
CIANFRANI A, LISTANTI M, POLVERIN M. Incremental Deployment of Segment Routing into an ISP Network: A Traffic Engineering Perspective[J]. IEEE/ACM Transactions on Networking, 2017, 25(5): 3146-3160.
doi: 10.1109/TNET.2017.2731419 URL |
| [16] |
SPRING N, MAHAJAN R, WETHERALL D. Measuring ISP Topologies with Rocketfuel[J]. ACM SIGCOMM Computer Communication Review, 2002, 32(4): 133-145.
doi: 10.1145/964725.633039 URL |
| [17] |
KODIALAM M, LAKSHMAN T V, ORLIN J, et al. Oblivious Routing of Highly Variable Traffic in Service Overlays and IP Backbones[J]. IEEE/ACM Transactions on Networking, 2008, 17(2): 459-472.
doi: 10.1109/TNET.2008.927257 URL |
| [18] | TUNE P, ROUGHAN M. Spatiotemporal Traffic Matrix Synthesis[C]// ACM. 2015 ACM Conference on Special Interest Group on Data Communication. New York: ACM, 2015: 579-592. |
| [19] | ZHANG Junjie, XI Kang, ZHANG Liren, et al. Optimizing Network Performance Using Weighted Multipath Routing[C]// IEEE. 21st International Conference on Computer Communications and Networks(ICCCN). New York:IEEE, 2012: 1-7. |
| [20] | ZHANG Hailong, GUO Xiao, YAN Jinyao, et al. SDN-Based ECMP Algorithm for Data Center Networks[C]// IEEE. 2014 IEEE Computers, Communications and IT Applications Conference. New York: IEEE, 2014: 13-18. |
| [21] | LIU Jing, LI Jie, SHOU Guochu, et al. SDN Based Load Balancing Mechanism for Elephant Flow in Data Center Networks[C]// IEEE. 2014 International Symposium on Wireless Personal Multimedia Communications(WPMC). New York:IEEE, 2014: 486-490. |
| [22] | YAO Guohao, WU Muqing, XU Yang. A Data Center Load Balancing Algorithm Based on Artificial Bee Colony Algorithm[C]// IEEE. 2020 IEEE 6th International Conference on Computer and Communications(ICCC). New York:IEEE, 2020: 1770-1775. |
| [1] | 冯光升, 蒋舜鹏, 胡先浪, 马明宇. 面向物联网的入侵检测技术研究新进展[J]. 信息网络安全, 2024, 24(2): 167-178. |
| [2] | 金志刚, 丁禹, 武晓栋. 融合梯度差分的双边校正联邦入侵检测算法[J]. 信息网络安全, 2024, 24(2): 293-302. |
| [3] | 薛羽, 张逸轩. 深层神经网络架构搜索综述[J]. 信息网络安全, 2023, 23(9): 58-74. |
| [4] | 刘宇啸, 陈伟, 张天月, 吴礼发. 基于稀疏自动编码器的可解释性异常流量检测[J]. 信息网络安全, 2023, 23(7): 74-85. |
| [5] | 蒋英肇, 陈雷, 闫巧. 基于双通道特征融合的分布式拒绝服务攻击检测算法[J]. 信息网络安全, 2023, 23(7): 86-97. |
| [6] | 赵彩丹, 陈璟乾, 吴志强. 基于多通道联合学习的自动调制识别网络[J]. 信息网络安全, 2023, 23(4): 20-29. |
| [7] | 谭柳燕, 阮树骅, 杨敏, 陈兴蜀. 基于深度学习的教育数据分类方法[J]. 信息网络安全, 2023, 23(3): 96-102. |
| [8] | 徐占洋, 程洛飞, 程建春, 许小龙. 一种使用Bi-ADMM优化深度学习模型的方案[J]. 信息网络安全, 2023, 23(2): 54-63. |
| [9] | 陈得鹏, 刘肖, 崔杰, 仲红. 一种基于双阈值函数的成员推理攻击方法[J]. 信息网络安全, 2023, 23(2): 64-75. |
| [10] | 文伟平, 朱一帆, 吕子晗, 刘成杰. 针对品牌的网络钓鱼扩线与检测方案[J]. 信息网络安全, 2023, 23(12): 1-9. |
| [11] | 刘军, 武志超, 吴建, 谭振华. 一种融合图像空间特征注意力机制的恶意代码识别模型[J]. 信息网络安全, 2023, 23(12): 29-37. |
| [12] | 廖丽云, 张伯雷, 吴礼发. 基于代价敏感学习的物联网异常检测模型[J]. 信息网络安全, 2023, 23(11): 94-103. |
| [13] | 王智, 张浩, 顾建军. SDN网络中基于联合熵与多重聚类的DDoS攻击检测[J]. 信息网络安全, 2023, 23(10): 1-7. |
| [14] | 贾凡, 康舒雅, 江为强, 王光涛. 基于NLP及特征融合的漏洞相似性算法评估[J]. 信息网络安全, 2023, 23(1): 18-27. |
| [15] | 高博, 陈琳, 严迎建. 基于CNN-MGU的侧信道攻击研究[J]. 信息网络安全, 2022, 22(8): 55-63. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||