信息网络安全 ›› 2022, Vol. 22 ›› Issue (3): 20-28.doi: 10.3969/j.issn.1671-1122.2022.03.003
V2G中一种轻量级的跨域双向认证方案
- 华北电力大学控制与计算机工程学院,北京 102206
-
收稿日期:2021-07-11出版日期:2022-03-10发布日期:2022-03-28 -
通讯作者:石润华 E-mail:rhshi@ncepu.edu.cn -
作者简介:石润华(1974—),男,安徽,教授,博士,主要研究方向为量子信息安全|王树豪(1996—),男,山东,硕士研究生,主要研究方向为智能电网、车联网|李坤昌(1992—),男,河南,博士研究生,主要研究方向为能源互联网数据共享和隐私保护 -
基金资助:国家自然科学基金(61772001)
A Lightweight Cross-domain Mutual Authentication Scheme in V2G Networks
SHI Runhua( ), WANG Shuhao, LI Kunchang
), WANG Shuhao, LI Kunchang
- School of Control and Computer Engineering, North China Electric Power University, Beijing 102206, China
-
Received:2021-07-11Online:2022-03-10Published:2022-03-28 -
Contact:SHI Runhua E-mail:rhshi@ncepu.edu.cn
摘要:
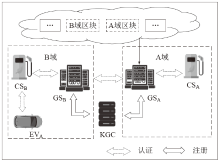
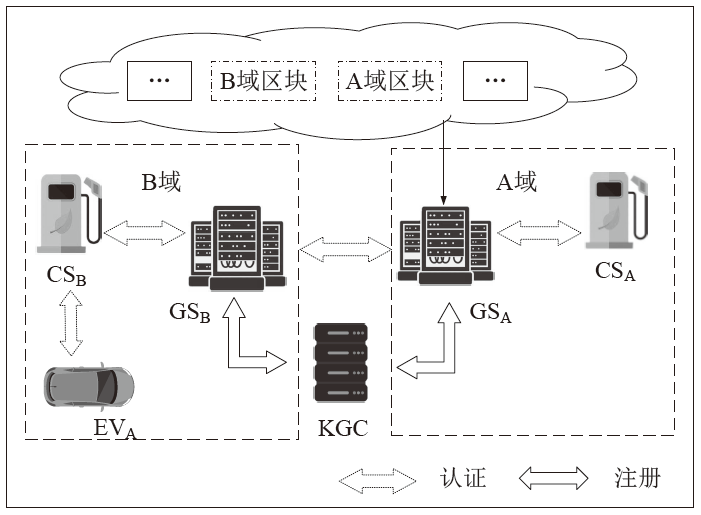
针对车辆与电网充放电时身份隐私泄露问题,文章提出一种轻量级的跨域身份认证方案。方案采用ECC和ECDSA保证电网服务器之间数据的隐私性和身份的真实性,同时利用区块链托管服务器公钥证书。对于充电桩到电网服务器之间的认证,采用速度更快的对称加密算法AES和消息认证码MAC保证数据的隐私性和真实性。文章利用PUF技术的轻量级和抗物理攻击特性提高了方案的实用性和有效性。通过与其他方案对比和实验仿真表明,该方案具有更好的安全性、完整性、轻量级和高效性。
中图分类号:
引用本文
石润华, 王树豪, 李坤昌. V2G中一种轻量级的跨域双向认证方案[J]. 信息网络安全, 2022, 22(3): 20-28.
SHI Runhua, WANG Shuhao, LI Kunchang. A Lightweight Cross-domain Mutual Authentication Scheme in V2G Networks[J]. Netinfo Security, 2022, 22(3): 20-28.
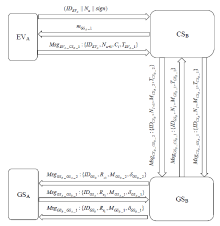
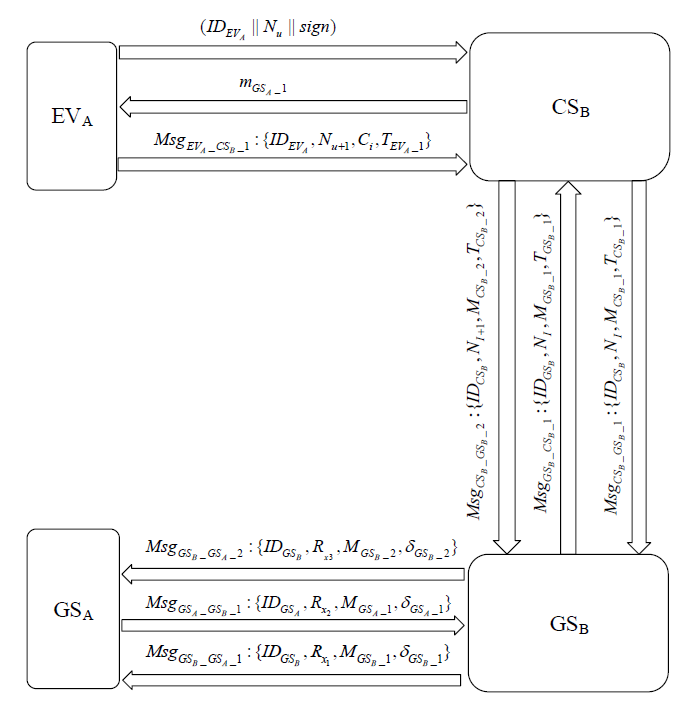
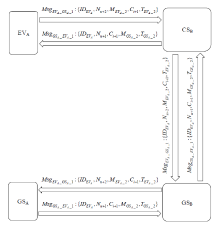
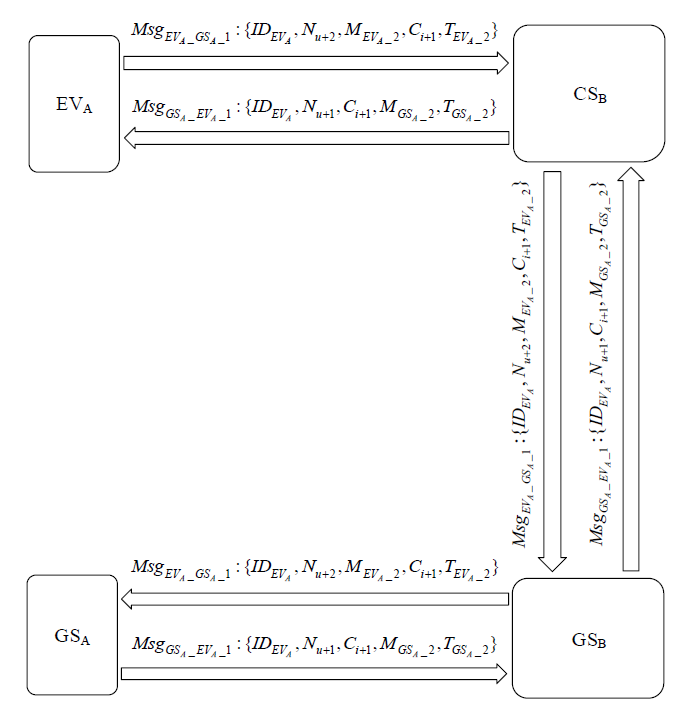
表1
符号及含义
| 符号 | 含义 | 符号 | 含义 |
|---|---|---|---|
| EVA | A域车辆 | $P{{K}_{G{{S}_{B}}}},S{{K}_{G{{S}_{B}}}}$ | GSB的公私钥对 |
| CSB | B域充电桩 | $P{{K}_{G{{S}_{A}}}},S{{K}_{G{{S}_{A}}}}$ | GSA的公私钥对 |
| GSA | A域服务器 | $h,{{H}_{1}}$ | 哈希函数 |
| GSB | B域服务器 | psw | 用户密码 |
| PKG | 密钥生成中心 | β | 用户指纹 |
| (C, R) | PUF产生的挑战响应对 | || | 连接操作符 |
| MAC | 消息认证码 | $\oplus $ | 异或操作符 |
| ${{k}_{C{{S}_{B}}\_G{{S}_{B}}}}$ | B域服务器和充电桩的会话密钥 | SM | 用户登录智能卡 |
| $Block\_D{{C}_{G{{S}_{B}}}}$ | GSB在区块链上的数字身份 | NU, NI | 随机数 |
| $Block\_D{{C}_{G{{S}_{A}}}}$ | GSA在区块链上的数字身份 | $MA{{C}_{{{k}_{C{{S}_{B}}\_G{{S}_{B}}}}}}$ | CSB和GSB间的消息认证码 |
| $P{{K}_{PKG}},S{{K}_{PKG}}$ | PKG的公私钥对 | $Ms{{g}_{P\_Q}}$ | 实体P到Q的消息 |
表1
| [1] |
LI Fangxing, QIAO Wei, SUN Hongbin, et al. Smart Transmission Grid: Vision and Framework[J]. IEEE Transactions on Smart Grid, 2010, 1(2):168-177.
doi: 10.1109/TSG.2010.2053726 URL |
| [2] |
KEMPTON W, TOMIC J. Vehicle-to-grid Power Fundamentals: Calculating Capacity and Net Revenue[J]. Journal of Power Sources, 2005, 144(1):268-279.
doi: 10.1016/j.jpowsour.2004.12.025 URL |
| [3] |
PARK J, KIM H, CHOI J Y. Improving TCP Performance in Vehicle-to-Grid(V2G) Communication[J]. Electronics, 2019, 8(11):1206-1223.
doi: 10.3390/electronics8111206 URL |
| [4] | SAXENA N, GRIJALVA S, CHUKWUKA V, et al. Network Security and Privacy Challenges in Smart Vehicle-to-Grid[J]. IEEE Wireless Communications, 2017, 24(4):88-98. |
| [5] |
GUO Huaqun, WU Yongdong, BAO Feng, et al. UBAPV2G: A Unique Batch Authentication Protocol for Vehicle-to-Grid Communications[J]. IEEE Transactions on Smart Grid, 2011, 2(4):707-714.
doi: 10.1109/TSG.2011.2168243 URL |
| [6] |
LIU Hong, NING Huansheng, ZHANG Yan, et al. Aggregated-proofs Based Privacy-preserving Authentication for V2G Networks in the Smart Grid[J]. IEEE Transactions on Smart Grid, 2012, 3(4):1722-1733.
doi: 10.1109/TSG.2012.2212730 URL |
| [7] |
LIU Hong, NING Huansheng, ZHANG Yan, et al. Role-dependent Privacy Preservation for Secure V2G Networks in the Smart Grid[J]. IEEE Transactions on Information Forensics and Security, 2013, 9(2):208-220.
doi: 10.1109/TIFS.2013.2295032 URL |
| [8] |
SAXENA N, CHOI B J. Authentication Scheme for Flexible Charging and Discharging of Mobile Vehicles in the V2G Networks[J]. IEEE Transactions on Information Forensics and Security, 2016, 11(7):1438-1452.
doi: 10.1109/TIFS.2016.2532840 URL |
| [9] | TSENG H R. A Secure and Privacy-preserving Communication Protocol for V2G Networks [C]//IEEE. 2012 IEEE Wireless Communications and Networking Conference(WCNC), April 1-4, 2012, Paris, France. New Jersey: IEEE, 2012: 2706-2711. |
| [10] |
ABDALLAH A, SHEN X S. Lightweight Authentication and Privacy-preserving Scheme for V2G Connections[J]. IEEE Transactions on Vehicular Technology, 2016, 66(3):2615-2629.
doi: 10.1109/TVT.2016.2577018 URL |
| [11] |
SHEN Jian, ZHOU Tianqi, WEI Fushan, et al. Privacy-preserving and Lightweight Key Agreement Protocol for V2G in the Social Internet of Things[J]. IEEE Internet of Things Journal, 2017, 5(4):2526-2536.
doi: 10.1109/JIOT.2017.2775248 URL |
| [12] |
GOPE P, SIKDAR B. An Efficient Privacy-preserving Authentication Scheme for Energy Internet-based Vehicle-to-Grid Communication[J]. IEEE Transactions on Smart Grid, 2019, 10(6):6607-6618.
doi: 10.1109/TSG.5165411 URL |
| [13] |
BANSAL G, NAREN N, CHAMOLA V, et al. Lightweight Mutual Authentication Protocol for V2G Using Physical Unclonable Function[J]. IEEE Transactions on Vehicular Technology, 2020, 69(7):7234-7246.
doi: 10.1109/TVT.25 URL |
| [14] | GARG S, KAUR K, KADDOUM G, et al. An Efficient Blockchain-based Hierarchical Authentication Mechanism for Energy Trading in V2G Environment [C]//IEEE. 2019 IEEE International Conference on Communications Workshops(ICC Workshops), May 20-24, 2019, Shanghai, China. New Jersey: IEEE, 2019: 1-6. |
| [15] |
WANG Huaqun, WANG Qihua, HE Debiao, et al. BBARS: Blockchain-based Anonymous Rewarding Scheme for V2G Networks[J]. IEEE Internet of Things Journal, 2019, 6(2):3676-3687.
doi: 10.1109/JIOT.2018.2890213 |
| [16] |
AITZHAN Z, SVETINOVIC D. Security and Privacy in Decentralized Energy Trading through Multi-signatures, Blockchain and Anonymous Messaging Streams[J]. IEEE Transactions on Dependable and Secure Computing, 2016, 15(5):840-852.
doi: 10.1109/TDSC.8858 URL |
| [17] | PATIL A S, HAMZA R, HASSAN A, et al. Efficient Privacy-preserving Authentication Protocol Using PUFs with Blockchain Smart Contracts[EB/OL]. https://www.sciencedirect.com/science/article/pii/S0167404820302340, 2021-11-12. |
| [18] | LIU Donglan, LI Dong, LIU Xin, et al. Research on a Cross-domain Authentication Scheme Based on Consortium Blockchain in V2G Networks of Smart Grid [C]//IEEE. 2nd IEEE Conference on Energy Internet and Energy System Integration(EI2), October 20-22, 2018, Beijing, China. New Jersey: IEEE, 2018: 1-5. |
| [19] | MAES R. Physically Unclonable Functions: Concept and Constructions[M]. Heidelberg: Springer, 2013. |
| [20] | CHEN Q, CSABA G, LUGIL P, et al. The Bistable Ring PUF: A New Architecture for Strong Physical Unclonable Functions [C]//IEEE. 2011 IEEE International Symposium on Hardware-oriented Security and Trust, June 5-6, 2011, San Diego, CA, USA. New Jersey: IEEE, 2011: 134-141. |
| [21] | PANDEY S, DEYATI S, SINGH A, et al. Noise-resilient SRAM Physically Unclonable Function Design for Security [C]//IEEE. IEEE 25th Asian Test Symposium(ATS), Noveber 21-24, 2016, Hiroshima, Japan. New Jersey: IEEE, 2016: 55-60. |
| [22] |
CHUANG K H, BURY E, DEGRAEVE R, et al. A Physically Unclonable Function Using Soft Oxide Breakdown Featuring 0% Native BER and 51.8 fJ/bit in 40-nm CMOS[J]. IEEE Journal of Solid-state Circuits, 2019, 54(10):2765-2776.
doi: 10.1109/JSSC.4 URL |
| [23] |
LU Xuyang, HONG Lingyu, SENGUPTA K. CMOS Optical PUFs Using Noise-immune Process-sensitive Photonic Crystals Incorporating Passive Variations for Robustness[J]. IEEE Journal of Solid-state Circuits, 2018, 53(9):2709-2721.
doi: 10.1109/JSSC.4 URL |
| [24] |
WANG Weiche, YONA Y, DIGGAVI S N, et al. Design and Analysis of Stability-guaranteed PUFs[J]. IEEE Transactions on Information Forensics and Security, 2017, 13(4):978-992.
doi: 10.1109/TIFS.2017.2774761 URL |
| [25] | BRON M, HANKERSON D, LOPEZ J, et al. Software Implementation of the NIST Elliptic Curves over Prime Fields [C]//Springer. 2001 Cryptographers’ Track at the RSA Conference, April 8-12, 2001, San Francisco, CA, USA. Heidelberg: Springer, 2001: 250-265. |
| [26] |
JOHNSON D, MENEZES A, VANSTONE S. The Elliptic Curve Digital Signature Algorithm(ECDSA)[J]. International Journal of Information Security, 2001, 1(1):36-63.
doi: 10.1007/s102070100002 URL |
| [1] | 冯怡婷, 马兆丰, 徐单恒, 段鹏飞. 跨链接入的区块链安全强度评估方法[J]. 信息网络安全, 2023, 23(1): 84-92. |
| [2] | 张光华, 刘永升, 王鹤, 于乃文. 基于BiLSTM和注意力机制的智能合约漏洞检测方案[J]. 信息网络安全, 2022, 22(9): 46-54. |
| [3] | 胡艺, 佘堃. 基于区块链和智能合约的双链车联网系统[J]. 信息网络安全, 2022, 22(8): 26-35. |
| [4] | 黄保华, 赵伟宏, 彭丽, 谢统义. 基于MPT索引的高效链上PKI模型[J]. 信息网络安全, 2022, 22(8): 72-80. |
| [5] | KELEKET GOMA Christy Junior Yannick, 易文哲, 王鹃. 一种基于SGX的轻量Fabric链码可信执行环境构建方法[J]. 信息网络安全, 2022, 22(7): 73-83. |
| [6] | 王姝爽, 马兆丰, 刘嘉微, 罗守山. 区块链跨链安全接入与身份认证方案研究与实现[J]. 信息网络安全, 2022, 22(6): 61-72. |
| [7] | 于克辰, 郭莉, 阴宏伟, 燕雪松. 面向数据中心场景的基于区块链与博弈论的高价值数据共享模型[J]. 信息网络安全, 2022, 22(6): 73-85. |
| [8] | 冯景瑜, 张琪, 黄文华, 韩刚. 基于跨链交互的网络安全威胁情报共享方案[J]. 信息网络安全, 2022, 22(5): 21-29. |
| [9] | 刘嘉微, 马兆丰, 王姝爽, 罗守山. 基于区块链的隐私信用数据受限共享技术研究[J]. 信息网络安全, 2022, 22(5): 54-63. |
| [10] | 崔皓宇, 马利民, 王佳慧, 张伟. 基于区块链的属性加密多授权机构安全模型研究[J]. 信息网络安全, 2022, 22(5): 84-93. |
| [11] | 陈彬杰, 魏福山, 顾纯祥. 基于KNN的具有隐私保护功能的区块链异常交易检测[J]. 信息网络安全, 2022, 22(3): 78-84. |
| [12] | 王健, 张蕴嘉, 刘吉强, 陈志浩. 基于区块链的司法数据管理及电子证据存储机制[J]. 信息网络安全, 2022, 22(2): 21-31. |
| [13] | 刘峰, 杨成意, 於欣澄, 齐佳音. 面向去中心化双重差分隐私的谱图卷积神经网络[J]. 信息网络安全, 2022, 22(2): 39-46. |
| [14] | 侯雨桐, 马兆丰, 罗守山. 基于区块链的数据安全共享与受控分发技术研究与实现[J]. 信息网络安全, 2022, 22(2): 55-63. |
| [15] | 王勇, 陈莉杰, 钟美玲. 基于零知识证明的区块链方案研究进展[J]. 信息网络安全, 2022, 22(12): 47-56. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||