信息网络安全 ›› 2022, Vol. 22 ›› Issue (3): 29-38.doi: 10.3969/j.issn.1671-1122.2022.03.004
面向网络架构的系统攻击面建模方法
- 1. 中国民航大学信息安全测评中心,天津 300300
2. 中国民航大学计算机科学与技术学院,天津 300300
3. 中国民航大学航空工程学院,天津 300300
-
收稿日期:2021-09-08出版日期:2022-03-10发布日期:2022-03-28 -
通讯作者:隋翯 E-mail:suihe0514@163.com -
作者简介:顾兆军(1966—),男,山东,教授,博士,主要研究方向为网络与信息安全、民航信息系统|杨睿(1995—),女,河北,硕士研究生,主要研究方向为网络与信息安全、民航信息系统|隋翯(1987—),男,吉林,讲师,博士,主要研究方向为网络与信息安全、工业控制系统 -
基金资助:民航安全能力建设基金(PESA2020100);民航安全能力建设基金(PESA2021007);民航安全能力建设基金(PESA2021009);中国民航大学研究生科技创新基金(2020YJS030)
System Attack Surface Modeling Method in Network
GU Zhaojun1,2, YANG Rui1,2, SUI He1,3( )
)
- 1. Information Security Evaluation Center, Civil Aviation University of China, Tianjin 300300, China
2. College of Computer Science and Technology, Civil Aviation University of China, Tianjin 300300, China
3. College of Aeronautical Engineering, Civil Aviation University of China, Tianjin 300300, China
-
Received:2021-09-08Online:2022-03-10Published:2022-03-28 -
Contact:SUI He E-mail:suihe0514@163.com
摘要:
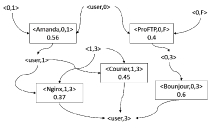
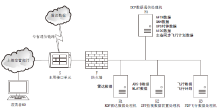
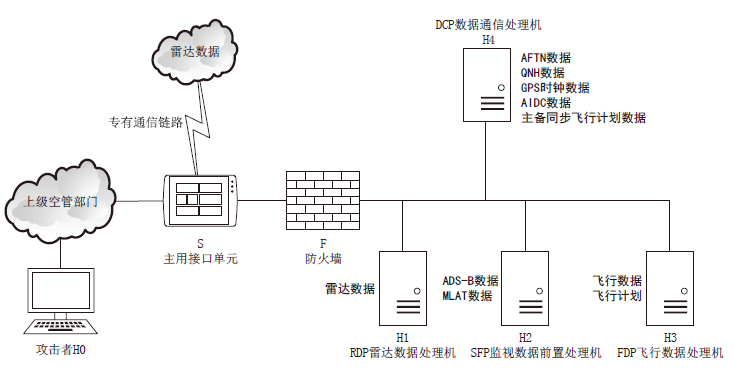
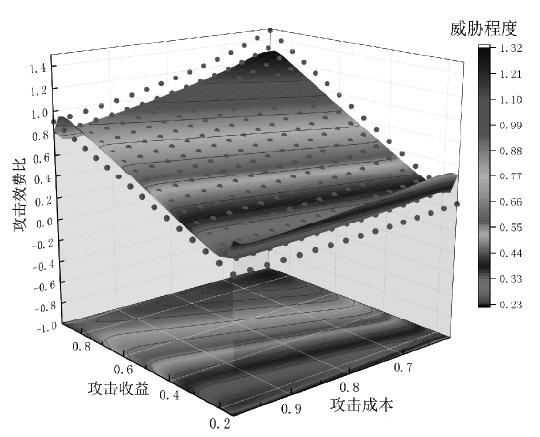
针对空管信息系统与互联网隔离、利用公开发布的漏洞信息不能切实体现网络安全性等问题,文章提出网络架构的空管信息系统风险评估模型。该模型综合各资源组件的端口、协议、数据进行资源节点的攻击面建模,使用贝叶斯网络为资源间的相互关系建立资源图。在上述模型的基础上,融合各资源攻击面与在资源图约束下的脆弱性严重程度为系统攻击面三元组,以表征三维度的威胁程度,计算网络结构的整体风险。在空管自动化系统中进行仿真实验,量化系统在不同攻击路径、不同维度上的威胁情况,多角度、多层次分析网络结构风险情况。实验结果表明,文章提出的系统攻击面风险评估模型具有合理性和实践有效性,为空管信息系统网络安全保障提供了指导性建议,从而在有限条件下最大限度地保障系统安全。
中图分类号:
引用本文
顾兆军, 杨睿, 隋翯. 面向网络架构的系统攻击面建模方法[J]. 信息网络安全, 2022, 22(3): 29-38.
GU Zhaojun, YANG Rui, SUI He. System Attack Surface Modeling Method in Network[J]. Netinfo Security, 2022, 22(3): 29-38.
| [1] | LOVATO A V, FONTES C H, EMBIRUCU M, et al. A Fuzzy Modeling Approach to Optimize Control and Decision Making in Conflict Management in Air Traffic Control[EB/OL]. https://www.sciencedirect.com/science/article/abs/pii/S0360835217305302, 2018-01-08. |
| [2] | LYU Tao, SONG Wenbin, DU Ke. Human Factors Analysis of Air Traffic Safety Based on HFACS-BN Model[EB/OL]. https://doi.org/10.3390/app9235049, 2019-11-22. |
| [3] |
VISHNYAKOVA L V, OBUKHOV Y V. A Solution to the Problem of Assessing Aviation Safety by Simulation Modeling[J]. Journal of Computer and Systems Sciences International, 2018, 57(6):957-969.
doi: 10.1134/S1064230718060126 URL |
| [4] | SAMPIGETHAYA K, POOVENDRAN R. Cyber-physical System Framework for Future Aircraft and Air Traffic Control [C]//IEEE. 2012 IEEE Aerospace Conference, March 3-10, 2012, Big Sky, MT, USA. New York: IEEE, 2012: 1-9. |
| [5] | BATUWANGALA E, RAMASAMY S, BOGODA L, et al. Safety and Security Considerations in the Certification of Next Generation Avionics and Air Traffic Management Systems[EB/OL]. https://search.informit.org/doi/10.3316/INFORMIT.739354743285311, 2017-02-26. , 2017-02-26. |
| [6] | LYKOU G, IAKOVAKIS G, GRITZALIS D. Aviation Cybersecurity and Cyber-resilience: Assessing Risk in Air Traffic Management[M]. New York: Springer, 2019. |
| [7] | AHTO B, OLGA G, ALEKSANDR L, et al. Attribute Evaluation on Attack Trees with Incomplete Information[EB/OL]. https://www.sciencedirect.com/science/article/pii/S0167404819301774, 2020-01-18. |
| [8] | LALLIE H S, DEBATTISTA K, BAL J. A Review of Attack Graph and Attack Tree Visual Syntax in Cyber Security[J]. Computer Science Review, 2020, 35(2):6-19. |
| [9] | ENOCH S Y, LEE J S, KIM D S. Novel Security Models, Metrics and Security Assessment for Maritime Vessel Networks[J]. Computer Networks, 2021, 189(4):16-34. |
| [10] | BELLOVIN S M. Attack Surfaces[J]. IEEE Security & Privacy, 2016, 14(3):88-97. |
| [11] | HOWARD M, PINCUS J, WING J M. Measuring Relative Attack Surfaces[M]. Heidelberg: Springer, 2005. |
| [12] |
MANADHATA P K, WING J M. An Attack Surface Metric[J]. IEEE Transactions on Software Engineering, 2011, 37(3):371-386.
doi: 10.1109/TSE.2010.60 URL |
| [13] | YOUNIS A A, MALAIYA Y K. Relationship between Attack Surface and Vulnerability Density: A Case Study on Apache HTTP Server[EB/OL]. https://www.researchgate.net/publication/304675945_Relationship_between_attack_surface_and_vulnerability_density_A_case_study_on_apachehttp_server, 2012-07-15. |
| [14] | YOUNIS A A, MALAIYA Y K, RAY I. Using Attack Surface Entry Points and Reachability Analysis to Assess the Risk of Software Vulnerability Exploitability[C]//IEEE. 15th International Symposium on High-assurance Systems Engineering, January 9-11, 2014, Miami Beach, FL, USA. New York: IEEE, 2014: 1-8. |
| [15] | XIONG Xinli, ZHAO Guangsheng, XU Weiguang, et al. System Attack Surface Based MTD Effectiveness Assessment Model[J]. Journal of Tsinghua University: Science & Technology, 2019, 59(4):276-283. |
| 熊鑫立, 赵光胜, 徐伟光, 等. 基于系统攻击面的动态目标防御有效性评估方法[J]. 清华大学学报:自然科学版, 2019, 59(4):276-283. | |
| [16] | THEISEN C, HERZIG K, MURPHY B, et al. Risk-based Attack Surface Approximation: How Much Data is Enough? [C]//IEEE. 2017 IEEE/ACM 39th International Conference on Software Engineering: Software Engineering in Practice Track (ICSE-SEIP), May 20-28, 2017, Buenos Aires, Argentina. New York: IEEE, 2017: 273-282. |
| [17] | Information Work Office of the State Council. GB/T 28448-2019 Information Security Technology Network Security Level Protection Evaluation Requirements[S]. Beijing: Standards Press of China, 2019. |
| 国务院信息化工作办公室. GB/T28448-2019 信息安全技术网络安全等级保护测评要求[S]. 北京: 中国标准出版社, 2019. | |
| [18] |
ZHANG Mengyuan, WANG Lingyu, JAJODIA S. Network Attack Surface: Lifting the Concept of Attack Surface to the Network Level for Evaluating Networks’ Resilience Against Zero-day Attacks[J]. IEEE Transactions on Dependable and Secure Computing, 2021, 18(1):310-324.
doi: 10.1109/TDSC.8858 URL |
| [19] | RAMOS A, LAZAR M, HOLANDA F R, et al. Model-based Quantitative Network Security Metrics: A Survey[J]. IEEE Communications Surveys & Tutorials, 2017, 19(4):2704-2734. |
| [20] |
KHOSRAVI-FARMAD M, GHAEMI-BAFGHI A. Bayesian Decision Network-based Security Risk Management Framework[J]. Journal of Network and Systems Management, 2020, 28(4):1794-1819.
doi: 10.1007/s10922-020-09558-5 URL |
| [21] |
MUÑOZ-GONZÁLEZ L, SGANDURRA D, BARRÈRE M, et al. Exact Inference Techniques for the Analysis of Bayesian Attack Graphs[J]. IEEE Transactions on Dependable and Secure Computing, 2017, 16(2):231-244.
doi: 10.1109/TDSC.8858 URL |
| [22] |
CHATZIPOULIDIS A, MICHALOPOULOS D, MAVRIDIS I. Information Infrastructure Risk Prediction through Platform Vulnerability Analysis[J]. Journal of Systems and Software, 2015, 106(7):28-41.
doi: 10.1016/j.jss.2015.04.062 URL |
| [23] |
THEISEN C, MUNAIAH N, AL-ZYOUD M, et al. Attack Surface Definitions: A Systematic Literature Review[J]. Information and Software Technology, 2018, 104(12):94-103.
doi: 10.1016/j.infsof.2018.07.008 URL |
| [24] | MA Chunguang, WANG Chenghong, ZHANG Donghong, et al. A Dynamic Network Risk Assessment Model Based on Attacker’s Inclination[J]. Journal of Computer Research and Development, 2015, 52(9):2056-2068. |
| 马春光, 汪诚弘, 张东红, 等. 一种基于攻击意愿分析的网络风险动态评估模型[J]. 计算机研究与发展, 2015, 52(9):2056-2068. | |
| [25] | YAMAGUCHI F, LINDNER F, RIECK K. Vulnerability Extrapolation: Assisted Discovery of Vulnerabilities Using Machine Learning [C]//USENIX. Proceedings of the 5th USENIX Conference on Offensive Technologies, August 8-12, 2011, California West, USA. Berkeley: USENIX, 2011: 13-23. |
| [26] |
KHAN M A, MAHMOOD S. A Graph Based Requirements Clustering Approach for Component Selection[J]. Advances in Engineering Software, 2012, 54(12):1-16.
doi: 10.1016/j.advengsoft.2012.08.002 URL |
| [27] | ZHANG Su, ZHANG Xinwen, OU Xinming, et al. Assessing Attack Surface with Component-based Package Dependency[EB/OL]. http://citeseerx.ist.psu.edu/viewdoc/download?doi=10.1.1.706.430&rep=rep1&type=pdf, 2015-11-06. |
| [28] | WU Chensi, XIE Weiqiang, JI Yixiao, et al. Survey on Network System Security Metrics[J]. Journal on Communications, 2019, 40(6):14-31. |
| 吴晨思, 谢卫强, 姬逸潇, 等. 网络系统安全度量综述[J]. 通信学报, 2019, 40(6):14-31. | |
| [29] | FREDERIC M, Thales Canada. Identifying Key Attack Surface Resources with Dynamic Analysis[R]. Ottawa: I.T. Security R&D Specialist for the Cyber Capability Development Centre(CCDC), 2268C. 001-REP-01-DA-TA1 Rev. 02, 2015. |
| [1] | 赵佳, 高塔, 张建成. 基于改进贝叶斯网络的高维数据本地差分隐私方法[J]. 信息网络安全, 2023, 23(2): 19-25. |
| [2] | 罗文华, 张耀文. 基于贝叶斯网络的电信网络诈骗受害人特征分析[J]. 信息网络安全, 2021, 21(12): 25-30. |
| [3] | 朱容辰, 李欣, 林小暖. 基于贝叶斯网络的视频专网安全风险分析方法[J]. 信息网络安全, 2021, 21(12): 91-101. |
| [4] | 肖彪, 闫宏强, 罗海宁, 李炬成. 基于差分隐私的贝叶斯网络隐私保护算法的改进研究[J]. 信息网络安全, 2020, 20(11): 75-86. |
| [5] | 何鹏程, 方勇. 一种基于Web日志和网站参数的入侵检测和风险评估模型的研究[J]. 信息网络安全, 2015, 15(1): 61-65. |
| [6] | 何一青. 一种基于有向二分图模型和贝叶斯网络的入侵检测方法[J]. , 2012, 12(8): 0-0. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||