信息网络安全 ›› 2020, Vol. 20 ›› Issue (4): 47-54.doi: 10.3969/j.issn.1671-1122.2020.04.006
基于联邦学习和卷积神经网络的入侵检测方法
- 1.哈尔滨工程大学计算机科学与技术学院,哈尔滨 150001
2.山东科技大学计算机科学与工程学院,青岛 266590
-
收稿日期:2019-12-29出版日期:2020-04-10发布日期:2020-05-11 -
通讯作者:马春光 E-mail:machunguang@sdust.edu.cn -
作者简介:作者简介:王蓉(1995—),女,山西,硕士研究生,主要研究方向为人工智能安全;马春光(1974—),男,黑龙江,教授,博士,主要研究方向为智能计算安全与隐私、密码学、区块链、数据安全与隐私等;武朋(1974—),女,河北,实验师,硕士,主要研究方向为为数据安全与隐私。
-
基金资助:国家自然科学基金[61932005];黑龙江省自然科学基金[JJ2019LH1770];信息安全国家重点实验室开发课题[2019-ZD-05]
An Intrusion Detection Method Based on Federated Learning and Convolutional Neural Network
WANG Rong1, MA Chunguang2( ), WU Peng2
), WU Peng2
- 1. College of Computer Science and Technology, Harbin Engineering University, Harbin 150001, China
2. College of Computer Science and Engineering, Shandong University of Science and Technology,Qingdao 266590, China
-
Received:2019-12-29Online:2020-04-10Published:2020-05-11 -
Contact:Chunguang MA E-mail:machunguang@sdust.edu.cn
摘要:
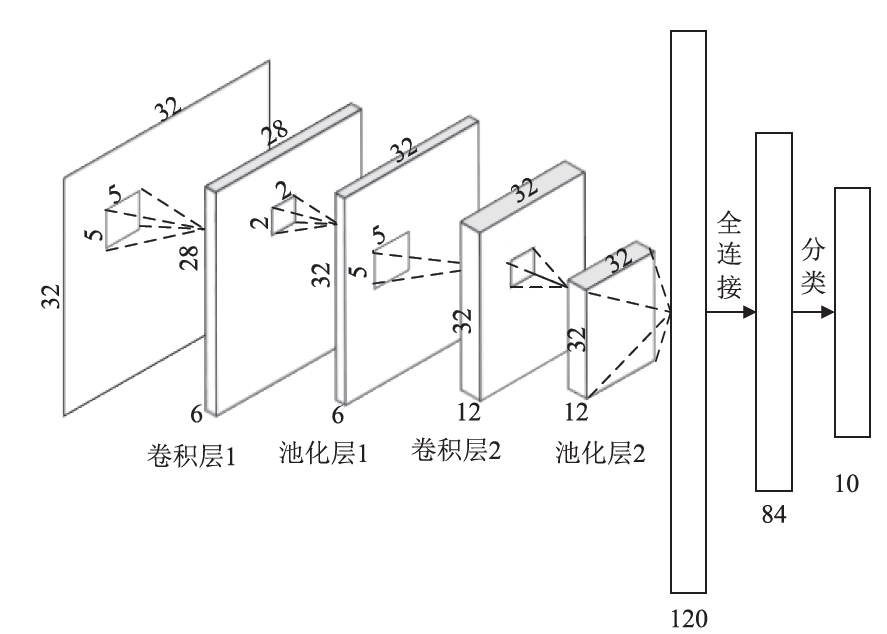
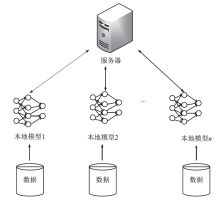
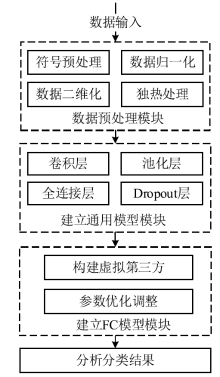
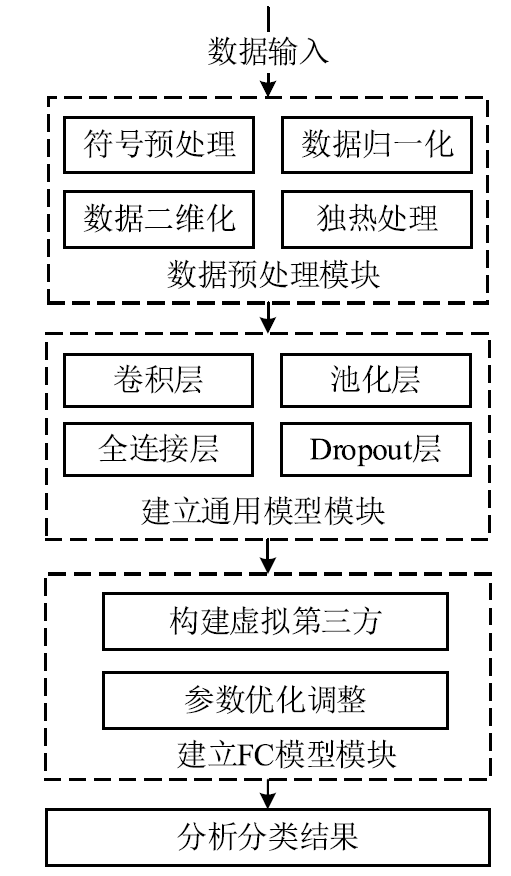
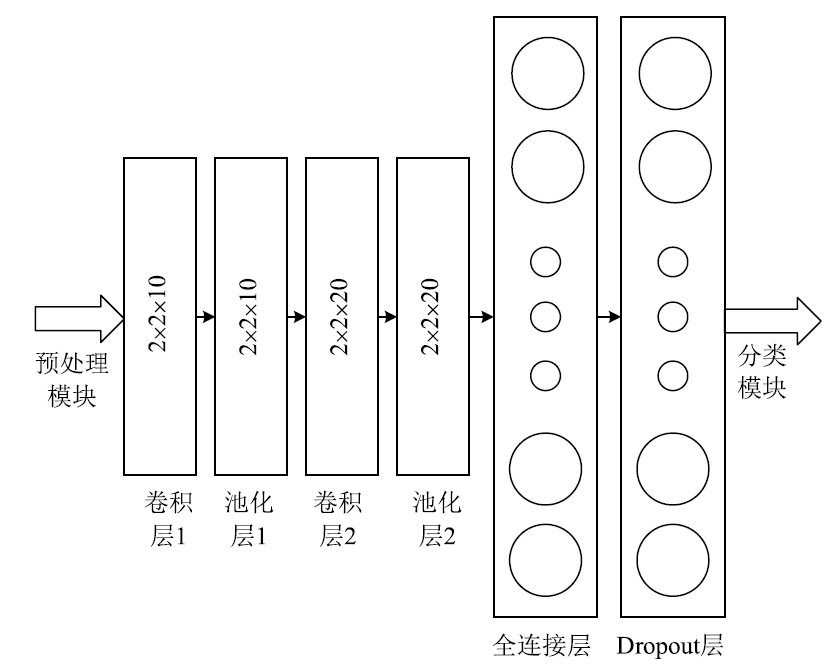
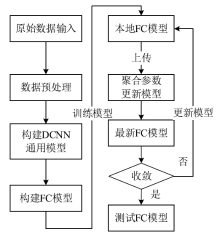
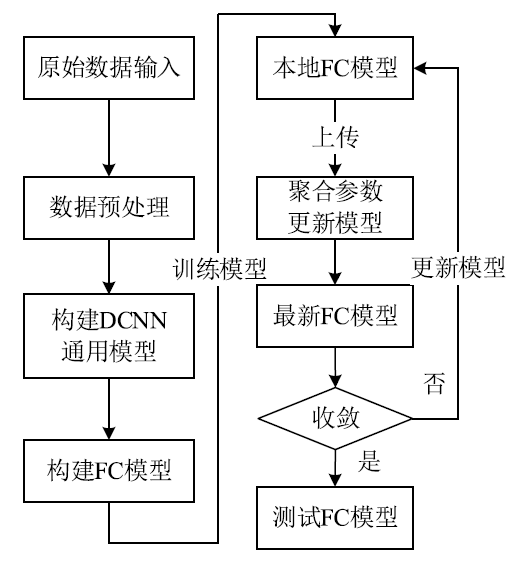
目前基于深度学习的入侵检测算法是入侵检测研究领域的研究热点,但是大多数研究的重点集中在如何改进算法来提高入侵检测的准确率,而忽视了实际中单个机构所产生的有限的标签数据不足以训练出一个高准确率的深度模型的问题。文章提出一种基于联邦学习和卷积神经网络的入侵检测方法,可以通过多个参与方的数据集联合训练模型达到扩充数据量的目的。该方法利用联邦学习框架,设计了基于深度学习的入侵检测模型。首先通过数据填充进行数据维度重构,形成二维数据,然后在联邦学习的机制下利用DCNN网络进行特征提取学习,最后结合Softmax分类器训练模型进行检测。实验结果表明,该方法很大程度上减少了训练时间并保持较高的检测率。另外,与一般的入侵检测模型相比,该模型还保证了数据安全隐私。
中图分类号:
引用本文
王蓉, 马春光, 武朋. 基于联邦学习和卷积神经网络的入侵检测方法[J]. 信息网络安全, 2020, 20(4): 47-54.
WANG Rong, MA Chunguang, WU Peng. An Intrusion Detection Method Based on Federated Learning and Convolutional Neural Network[J]. Netinfo Security, 2020, 20(4): 47-54.
| [1] | YIN Chuanlong, ZHU Yuefei, FEI Jinlong, et al.A Deep Learning Approach for Intrusion Detection Using Recurrent Neural Networks[J]. IEEE Access, 2017(5): 21954-21961. |
| [2] | LI Zhipeng, QIN Zheng, HUANG Kai, et al.Intrusion Detection Using Convolutional Neural Networks for Representation Learning[C]//Springer. International Conference on Neural Information Processing, November 14-18, 2017, Guangzhou, China. Heidelberg: Springer, 2017: 858-866. |
| [3] | WANG Wei, SHENG Yiqiang, WANG Jinlin, et al.HAST-IDS: Learning Hierarchical Spatial-temporal Features Using Deep Neural Networks to Improve Intrusion Detection[J]. IEEE Access, 2017(6): 1792-1806. |
| [4] | ZHANG Hongpo, WU C Q, GAO Shan, et al.An Effective Deep Learning Based Scheme for Network Intrusion Detection[C]//IEEE. 24th International Conference on Pattern Recognition(ICPR), Auguest 20-24, 2018, Beijing, China. New Jersey: IEEE, 2018: 682-687. |
| [5] | AL-QATF M, YU Lasheng, AL-HABIB M, et al.Deep Learning Approach Combining Sparse Autoencoder With SVM for Network Intrusion Detection[J]. IEEE Access, 2018(6): 52843-52856. |
| [6] | NGUYEN T D, MARCHAL S, MIETTINEN M, et al.DÏoT: A Federated Self-learning Anomaly Detection System for IoT[C]//IEEE. 39th International Conference on Distributed Computing Systems(ICDCS), July 17-10, 2019, Dallas, TX, USA. New Jersey: IEEE, 2019: 756-767. |
| [7] | AVALLAEE M, BAGHERIE , LU W, et al. NSL-KDD[EB/OL]. , 2018-5-3. |
| [8] | GAO Yazhi, RONG Wenge, SHEN Yikang, et al.Convolutional Neural Network Based Sentiment Analysis Using Adaboost Combination[C]//IEEE. 2016 International Joint Conference on Neural Networks(IJCNN), July 24-29, 2016, Vancouver, BC, Canada. New Jersey: IEEE, 2016: 1333-1338. |
| [9] | YU Dingjun, WANG Hanli, CHEN Peiqiu, et al.Mixed Pooling for Convolutional Neural Networks[C]//Springer. International Conference on Rough Sets and Knowledge Technology, October 24-26, 2014, Shanghai, China. Heidelberg: Springer, 2014: 364-375. |
| [10] | YANG Qiang, LIU Yang, CHEN Tianjian, et al.Federated Machine Learning: Concept and Applications[J]. ACM Transactions on Intelligent Systems and Technology(TIST), 2019, 10(2): 1-19. |
| [11] | KONEČNÝ J, MCMAHAN H B, YU F X, et al. Federated Learning: Strategies for Improving Communication Efficiency[EB/OL]. , 2019-12-21. |
| [12] | TAVALLAEE M, BAGHERI E, LU W, et al.A Detailed Analysis of the KDD CUP 99 Data Set[C]//IEEE. 2009 IEEE Symposium on Computational Intelligence for Security and Defense Applications, July 8-10, 2009, Ottawa, ON, Canada. New Jersey: IEEE, 2009: 1-6. |
| [13] | ZHANG Sicong, XIE Xiaoyao, XU Yang.Intrusion Detection Method Based on a Deep Convolutional Neural Network[J]. Journal of Tsinghua University(Science and Technology), 2019, 59(1): 46-54. |
| 张思聪,谢晓尧,徐洋. 基于dCNN的入侵检测方法[J]. 清华大学学报(自然科学版),2019,59(1):46-54. | |
| [14] | LIANG Jie, CHEN Jiahao, ZHANG Xueqin.One-hot Encoding and Convolutional Neural Network Based Anomaly Detection[J]. Journal of Tsinghua University(Science and Technology), 2019, 59(7): 523-529. |
| 梁杰,陈嘉豪,张雪芹. 基于独热编码和卷积神经网络的异常检测[J]. 清华大学学报(自然科学版),2019,59(7):523-529. | |
| [15] | WU Kehe, CHEN Zuge, LI Wei.A Novel Intrusion Detection Model for a Massive Network Using Convolutional Neural Networks[J]. IEEE Access, 2018(6): 50850-50859. |
| [16] | VINAYAKUMAR R, SOMAN K P, POORNACHANDRAN P.Applying Convolutional Neural Network for Network Intrusion Detection[C]//IEEE. 2017 International Conference on Advances in Computing, Communications and Informatics, September 13-16, 2017, Udupi, India. New Jersey: IEEE, 2017: 1222-1228. |
| [17] | KWON D, NATARAJAN K, SUH S C, et al.An Empirical Study on Network Anomaly Detection Using Convolutional Neural Networks[C]//IEEE. 2018 IEEE 38th International Conference on Distributed Computing Systems, July 2-6, Vienna, Austria. New Jersey: IEEE, 2018: 1595-1598. |
| [18] | CHOONG A C H, LEE N K. Evaluation of Convolutionary Neural Networks Modeling of DNA Sequences Using Ordinal Versus One-hot Encoding Method[C]//IEEE. 2017 International Conference on Computer and Drone Applications, November 9-11, Kuching, Malaysia. New Jersey: IEEE, 2017: 60-65. |
| [19] | SHONE N, NGOC T N, PHAI V D, et al.A Deep Learning Approach to Network Intrusion Detection[J]. IEEE Transactions on Emerging Topics in Computational Intelligence, 2018, 2(1): 41-50. |
| [1] | 李桥, 龙春, 魏金侠, 赵静. 一种基于LMDR和CNN的混合入侵检测模型[J]. 信息网络安全, 2020, 20(9): 117-121. |
| [2] | 吴警, 芦天亮, 杜彦辉. 基于Char-RNN改进模型的恶意域名训练数据生成技术[J]. 信息网络安全, 2020, 20(9): 6-11. |
| [3] | 王文华, 郝新, 刘焱, 王洋. AI系统的安全测评和防御加固方案[J]. 信息网络安全, 2020, 20(9): 87-91. |
| [4] | 王湘懿, 张健. 基于图像和机器学习的虚拟化平台异常检测[J]. 信息网络安全, 2020, 20(9): 92-96. |
| [5] | 姜楠, 崔耀辉, 王健, 吴晋超. 基于上下文特征的IDS告警日志攻击场景重建方法[J]. 信息网络安全, 2020, 20(7): 1-10. |
| [6] | 张晓宇, 王华忠. 基于改进Border-SMOTE的不平衡数据工业控制系统入侵检测[J]. 信息网络安全, 2020, 20(7): 70-76. |
| [7] | 刘静, 张学谦, 刘全明. 混合Gabor的轻量级卷积神经网络的验证码识别研究[J]. 信息网络安全, 2020, 20(7): 77-84. |
| [8] | 彭中联, 万巍, 荆涛, 魏金侠. 基于改进CGANs的入侵检测方法研究[J]. 信息网络安全, 2020, 20(5): 47-56. |
| [9] | 张蕾华, 黄进, 张涛, 王生玉. 视频侦查中人像智能分析应用及算法优化[J]. 信息网络安全, 2020, 20(5): 88-93. |
| [10] | 罗文华, 许彩滇. 基于改进MajorClust聚类的网络入侵行为检测[J]. 信息网络安全, 2020, 20(2): 14-21. |
| [11] | 康健, 王杰, 李正旭, 张光妲. 物联网中一种基于多种特征提取策略的入侵检测模型[J]. 信息网络安全, 2019, 19(9): 21-25. |
| [12] | 谢永恒, 冯宇波, 董清风, 王梅. 基于深度学习的数据接入方法研究[J]. 信息网络安全, 2019, 19(9): 36-40. |
| [13] | 冯文英, 郭晓博, 何原野, 薛聪. 基于前馈神经网络的入侵检测模型[J]. 信息网络安全, 2019, 19(9): 101-105. |
| [14] | 饶绪黎, 徐彭娜, 陈志德, 许力. 基于不完全信息的深度学习网络入侵检测[J]. 信息网络安全, 2019, 19(6): 53-60. |
| [15] | 马春光, 郭瑶瑶, 武朋, 刘海波. 生成式对抗网络图像增强研究综述[J]. 信息网络安全, 2019, 19(5): 10-12. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||