信息网络安全 ›› 2020, Vol. 20 ›› Issue (7): 70-76.doi: 10.3969/j.issn.1671-1122.2020.07.008
基于改进Border-SMOTE的不平衡数据工业控制系统入侵检测
- 华东理工大学化工过程先进控制和优化技术教育部重点实验室,上海 200237
-
收稿日期:2020-05-13出版日期:2020-07-10发布日期:2020-08-13 -
通讯作者:王华忠 E-mail:hzwang@ecust.edu.cn -
作者简介:张晓宇(1996—),男,安徽,硕士研究生,主要研究方向为工业系统信息安全|王华忠(1969—),男,江苏,副教授,博士,主要研究方向为工业控制、工控信息安全 -
基金资助:国家自然科学基金(61973119);中央高校基本科研业务费专项资金(222201917006)
Intrusion Detection of ICS Based on Improved Border-SMOTE for Unbalance Data
- Key Laboratory of Advanced Control and Optimization for Chemical Processes of Ministry of Education, East China University of Science and Technology, Shanghai 200237, China
-
Received:2020-05-13Online:2020-07-10Published:2020-08-13 -
Contact:Huazhong WANG E-mail:hzwang@ecust.edu.cn
摘要:
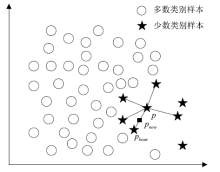
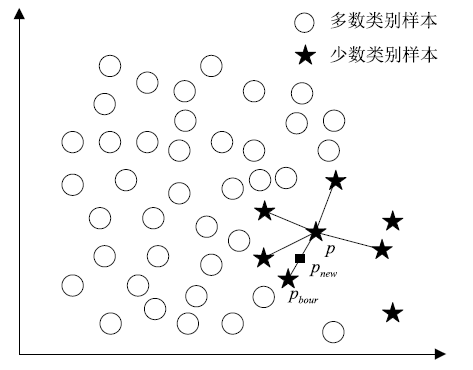
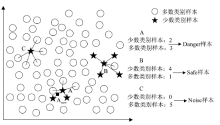
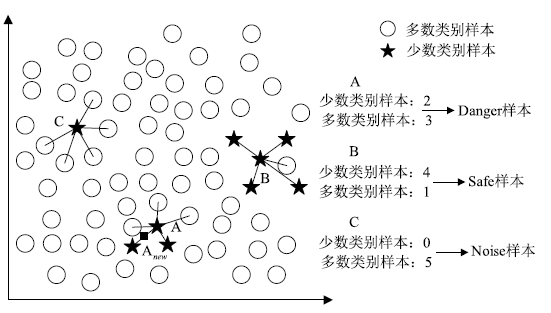
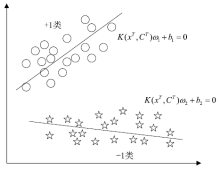
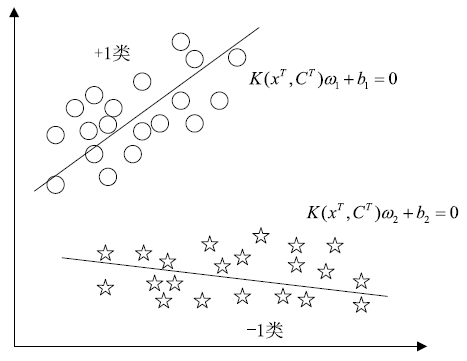
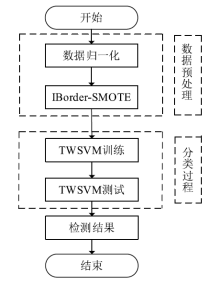
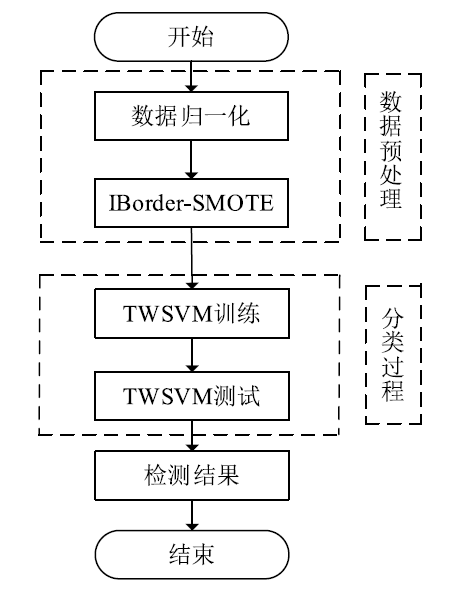
工业环境中正常与异常样本间的不平衡特点导致入侵检测模型在进行分类时对少数异常样本识别率较低。然而,工控入侵检测模型尤其注重对异常样本的检测成功率,因此文章引入具有自适应思想的边界SMOTE算法,在边界区域根据样本分布情况合理生成少数样本以降低样本的不平衡性。UCI不平衡数据集上的结果证明了该算法的有效性。然后改进边界SMOTE对原始不平衡工控入侵检测数据集SWaT进行数据预处理,在合成合理攻击数据后使用孪生支持向量机(TWSVM)作为分类器构建入侵检测模型。实验结果表明,该方法提高了对攻击样本的识别能力。
中图分类号:
引用本文
张晓宇, 王华忠. 基于改进Border-SMOTE的不平衡数据工业控制系统入侵检测[J]. 信息网络安全, 2020, 20(7): 70-76.
ZHANG Xiaoyu, WANG Huazhong. Intrusion Detection of ICS Based on Improved Border-SMOTE for Unbalance Data[J]. Netinfo Security, 2020, 20(7): 70-76.
表2
不同算法的AUC值
| 数据集 | 方法 | SMOTE/% | Border-SMOTE/% | SLSMOTE/% | IBorder-SMOTE/% |
|---|---|---|---|---|---|
| Ecoli | KNN | 85.34 | 87.14 | 87.25 | 88.56 |
| NB | 89.01 | 88.32 | 88.65 | 90.74 | |
| SVM | 88.25 | 87.68 | 89.18 | 90.96 | |
| Abalone | KNN | 70.31 | 71.67 | 70.91 | 72.41 |
| NB | 77.32 | 76.34 | 77.48 | 78.82 | |
| SVM | 75.31 | 77.04 | 76.61 | 76.92 | |
| CarEvaluation | KNN | 89.53 | 89.91 | 87.93 | 90.12 |
| NB | 86.67 | 84.58 | 84.97 | 88.64 | |
| SVM | 91.71 | 93.15 | 91.12 | 96.82 | |
| Yeast | KNN | 74.30 | 78.58 | 76.21 | 79.05 |
| NB | 79.20 | 80.45 | 77.82 | 80.91 | |
| SVM | 75.56 | 80.10 | 79.61 | 81.35 |
表2
| [1] | RUBIO J E, ALCARAZ C, ROMAN R, et al. Analysis of Intrusion Detection Systems in Industrial Ecosystems[C]// INSTICC. 14th International Conference on Security and Cryptography, July 26-28, 2017, Madrid, Spain. Madrid: INSTICC, 2017: 116-128. |
| [2] | FAN Xiaohe, FAN Kefeng, WANG Yong, et al. Overview of Cyber-security of Industrial Control System[C]// IEEE. 2015 International Conference on Cyber Security of Smart Cities, August 5-7, 2015, Shanghai, China. New Jersey: IEEE, 2015: 1-7. |
| [3] | YU Bangbing, WANG Huazhong, YAN Bingyong, Intrusion Detection of Industrial Control System Based on Grey Wolf Algorithm and Case-based Reasoning[J]. Journal of East China University of Science and Technology(Natural Science Edition), 2018,44(2):239-245. |
| 於帮兵, 王华忠, 颜秉勇. 基于灰狼算法和案例推理的工控系统入侵检测[J]. 华东理工大学学报(自然科学版), 2018,44(2):239-245. | |
| [4] | TRAUTMAN L J, ORMEROD P C. Industrial Cyber Vulnerabilities: Lessons from Stuxnet and the Internet of Things[J]. University of Miami Law Review, 2017,72(3):761. |
| [5] | DI P A, DRAGONI Y, CARCANO A. TRITON. The First ICS Cyber Attack on Safety Instrument Systems[C]// Black Hat. Black Hat USA 2018, August 4-6, 2018, Las Vegas, USA. Las Vegas: BLACK HAT, 2018: 1-26. |
| [6] | CHENG Dongmei, YAN Biao, WEN Hui, SUN Limin. The Design and Implement of Rule Matching-based Distributed Intrusion Detection Framework for Industry Control System[J]. Netinfo Security, 2017,17(7):45-51. |
| [7] | WU Yali, LI Guoting, FU Yulong, et al. A New Intrusion Detection Model Based on Adaptability and Robustness[J]. Control and Decision, 2019,34(11):2330-2336. |
| 吴亚丽, 李国婷, 付玉龙, 等. 基于自适应鲁棒性的入侵检测模型[J]. 控制与决策, 2019,34(11):2330-2336. | |
| [8] | KHALILI A, SAMI A. SysDetect: A Systematic Approach to Critical State Determination for Industrial Intrusion Detection Systems Using Apriori Algorithm[J]. Journal of Process Control, 2015,32(C):154-160. |
| [9] | MIRZA B, LIN Zhiping, LIU Nan. Ensemble of Subset Online Sequential Extreme Learning Machine for Class Imbalance and Concept Drift[J]. Neurocomputing, 2015,149(A):316-329. |
| [10] | HU Ji, YAN Chenggang, LIU Xin, et al. Truncated Gradient Confidence-Weighted Based Online Learning for Imbalance Streaming Data[C]// IEEE. 2019 IEEE International Conference on Multimedia and Expo(ICME), July 8-12, 2019, Shanghai, China. New Jersey: IEEE, 2019: 133-138. |
| [11] | CHAWLA N V, BOWYER K W, HALL L O, et al. SMOTE: Synthetic Minority Over-sampling Technique[J]. Journal of Artificial Intelligence Research, 2002,16(1):321-357. |
| [12] | HUANG Jianming, LI Xiaoming, QU Hezuo, et al. Method for Fault Type Identification of Transmission Line Considering Wavelet Singular Information and Unbalanced Dataset[J]. Proceedings of the CSEE, 2017,37(11):3099-3107, 3365. |
| 黄建明, 李晓明, 瞿合祚, 等. 考虑小波奇异信息与不平衡数据集的输电线路故障识别方法[J]. 中国电机工程学报, 2017,37(11):3099-3107,3365. | |
| [13] | LIU Chao, WU Shen, ZHENG Yichao, et al. Classification of Cancer Based on DeepForest and DNA Methylation[J]. Computer Engineering and Applications. 2020,56(13):189-193. |
| 刘超, 吴申, 郑一超, 等. 基于深度森林和DNA甲基化的癌症分类研究[J]. 计算机工程与应用, 2020,56(13):189-193. | |
| [14] | HAN Hui, WANG Wenyuan, MAO Binghuan. Borderline-SMOTE: A New Over-sampling Method in Imbalanced Data Sets Learning[C]// Springer. International Conference on Intelligent Computing, August 22-26, 2005, Hefei, China. Berlin: Springer, 2005: 878-887. |
| [15] |
KHEMCHANDANI R, CHANDRA S. Twin Support Vector Machines for Pattern Classification[J]. IEEE Transactions on Pattern Analysis and Machine Intelligence, 2007,29(5):905-910.
doi: 10.1109/tpami.2007.1068 URL pmid: 17469239 |
| [16] | MATHUR A P, TIPPENHAUER N O. SWaT: A Water Treatment Testbed for Research and Training on ICS Security[C]// IEEE. 2016 International Workshop on Cyber-physical Systems for Smart Water Networks(CySWater), April 11, 2016, Vienna, Austria. New Jersey: IEEE, 2016: 31-36. |
| [1] | 李桥, 龙春, 魏金侠, 赵静. 一种基于LMDR和CNN的混合入侵检测模型[J]. 信息网络安全, 2020, 20(9): 117-121. |
| [2] | 李世斌, 李婧, 唐刚, 李艺. 基于HMM的工业控制系统网络安全状态预测与风险评估方法[J]. 信息网络安全, 2020, 20(9): 57-61. |
| [3] | 姜楠, 崔耀辉, 王健, 吴晋超. 基于上下文特征的IDS告警日志攻击场景重建方法[J]. 信息网络安全, 2020, 20(7): 1-10. |
| [4] | 彭中联, 万巍, 荆涛, 魏金侠. 基于改进CGANs的入侵检测方法研究[J]. 信息网络安全, 2020, 20(5): 47-56. |
| [5] | 王蓉, 马春光, 武朋. 基于联邦学习和卷积神经网络的入侵检测方法[J]. 信息网络安全, 2020, 20(4): 47-54. |
| [6] | 罗文华, 许彩滇. 基于改进MajorClust聚类的网络入侵行为检测[J]. 信息网络安全, 2020, 20(2): 14-21. |
| [7] | 康健, 王杰, 李正旭, 张光妲. 物联网中一种基于多种特征提取策略的入侵检测模型[J]. 信息网络安全, 2019, 19(9): 21-25. |
| [8] | 冯文英, 郭晓博, 何原野, 薛聪. 基于前馈神经网络的入侵检测模型[J]. 信息网络安全, 2019, 19(9): 101-105. |
| [9] | 尚文利, 尹隆, 刘贤达, 赵剑明. 工业控制系统安全可信环境构建技术及应用[J]. 信息网络安全, 2019, 19(6): 1-10. |
| [10] | 饶绪黎, 徐彭娜, 陈志德, 许力. 基于不完全信息的深度学习网络入侵检测[J]. 信息网络安全, 2019, 19(6): 53-60. |
| [11] | 尚文利, 张修乐, 刘贤达, 尹隆. 工控网络局域可信计算环境构建方法与验证[J]. 信息网络安全, 2019, 19(4): 1-10. |
| [12] | 刘敬浩, 毛思平, 付晓梅. 基于ICA算法与深度神经网络的入侵检测模型[J]. 信息网络安全, 2019, 19(3): 1-10. |
| [13] | 陈虹, 肖越, 肖成龙, 陈建虎. 融合最大相异系数密度的SMOTE算法的入侵检测方法[J]. 信息网络安全, 2019, 19(3): 61-71. |
| [14] | 陈瑞滢, 陈泽茂, 王浩. 工业控制系统安全监控协议的设计与优化研究[J]. 信息网络安全, 2019, 19(2): 60-69. |
| [15] | 田峥, 李树, 孙毅臻, 黎曦. 一种面向S7协议的工控系统入侵检测模型[J]. 信息网络安全, 2019, 19(11): 8-13. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||