信息网络安全 ›› 2019, Vol. 19 ›› Issue (3): 1-10.doi: 10.3969/j.issn.1671-1122.2019.03.001
• • 下一篇
基于ICA算法与深度神经网络的入侵检测模型
刘敬浩1, 毛思平1, 付晓梅2
- 1. 天津大学电气自动化与信息工程学院,天津300072
2.天津大学海洋科学与技术学院,天津300072
-
收稿日期:2018-08-15出版日期:2019-03-19发布日期:2020-05-11 -
作者简介:作者简介:刘敬浩(1963—),男,天津,副教授,硕士,主要研究方向为网络安全、网络虚拟环境、无线网络通信;毛思平(1995—),男,浙江,硕士研究生,主要研究方向为网络安全、机器学习;付晓梅(1968—),女,重庆,副教授,博士,主要研究方向为无线通信、海洋通信、信息安全。
-
基金资助:国家自然科学基金[61571323]
Intrusion Detection Model Based on ICA Algorithm and Deep Neural Network
Jinghao LIU1, Siping MAO1, Xiaomei FU2
- 1. School of Electrical and Information Engineering, Tianjin University, Tianjin 300072, China
2. School of Marine Science and Technology, Tianjin University, Tianjin 300072, China
-
Received:2018-08-15Online:2019-03-19Published:2020-05-11
摘要:
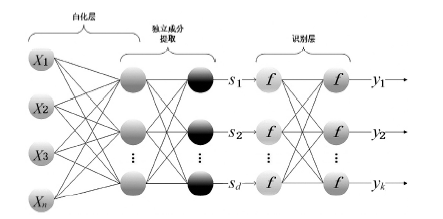
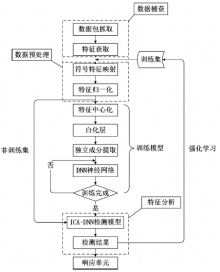
针对网络数据的特征维数高、非线性可分等问题,文章提出了一种基于独立成分分析ICA与深度神经网络DNN的入侵检测模型ICA-DNN。首先,利用ICA算法将网络连接数据基于极大非高斯性进行特征提取,并将数据从高维特征空间映射到低维空间,消除特征冗余性。然后使用深度神经网络进行分类,深度神经网络采用ReLU激活函数和交叉熵损失函数以及adam优化算法。ICA-DNN模型不仅能减少特征冗余性,还能抓取特征之间的内部结构。实验表明,基于ICA-DNN的入侵检测模型与一些浅层机器学习模型比较具有更好的特征学习能力和更精确的分类能力。
中图分类号:
引用本文
刘敬浩, 毛思平, 付晓梅. 基于ICA算法与深度神经网络的入侵检测模型[J]. 信息网络安全, 2019, 19(3): 1-10.
Jinghao LIU, Siping MAO, Xiaomei FU. Intrusion Detection Model Based on ICA Algorithm and Deep Neural Network[J]. Netinfo Security, 2019, 19(3): 1-10.
表2
10个样本子集数据分布
| 项目 | U2R | R2L | pobe | normal | DoS | sum |
|---|---|---|---|---|---|---|
| Tr0 | 42 | 215 | 870 | 19786 | 79119 | 100032 |
| Te0 | 10 | 23 | 78 | 1927 | 7969 | 10007 |
| Tr1 | 42 | 241 | 883 | 21812 | 87054 | 110032 |
| Te1 | 10 | 19 | 90 | 2142 | 8745 | 11006 |
| Tr2 | 42 | 269 | 990 | 23595 | 95131 | 120027 |
| Te2 | 10 | 28 | 112 | 2283 | 9577 | 12010 |
| Tr3 | 42 | 292 | 1117 | 25707 | 102868 | 130026 |
| Te3 | 10 | 28 | 92 | 2578 | 10301 | 13009 |
| Tr4 | 42 | 358 | 1160 | 27397 | 111065 | 140022 |
| Te4 | 10 | 26 | 133 | 2815 | 11025 | 14009 |
| Tr5 | 42 | 371 | 1231 | 29521 | 118855 | 150020 |
| Te5 | 10 | 32 | 125 | 2955 | 11885 | 15007 |
| Tr6 | 42 | 355 | 1361 | 31470 | 126794 | 160022 |
| Te6 | 10 | 32 | 125 | 3239 | 12602 | 16008 |
| Tr7 | 42 | 372 | 1419 | 33394 | 134795 | 170022 |
| Te7 | 10 | 39 | 137 | 3294 | 13530 | 17010 |
| Tr8 | 42 | 387 | 1515 | 35573 | 142500 | 180017 |
| Te8 | 10 | 50 | 138 | 3552 | 14257 | 18007 |
| Tr9 | 42 | 468 | 1624 | 37506 | 150390 | 190030 |
| Te9 | 10 | 44 | 164 | 3605 | 15185 | 19008 |
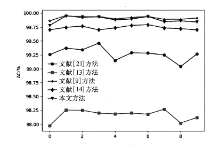
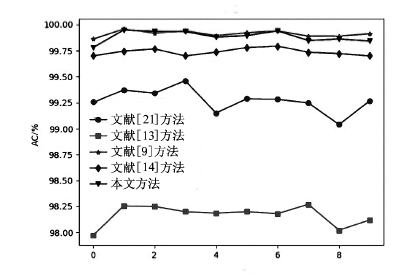
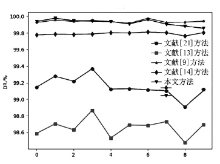
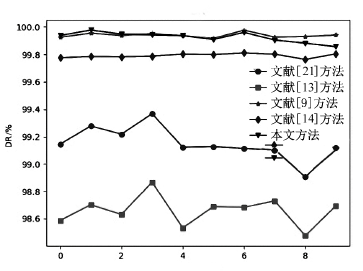
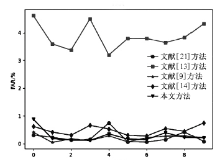
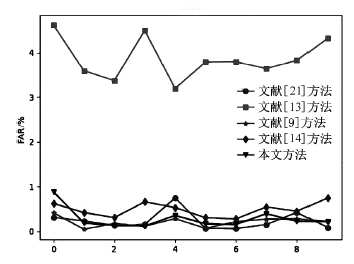
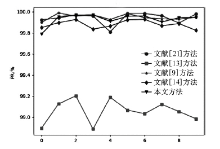
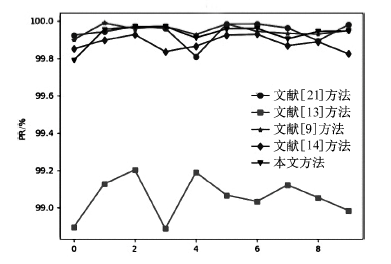
表5
所有攻击类型的检测性能对比
| 入侵类型 | 项目 | 文献[ | 文献[ | 文献[ | 文献[ | 本文 方法/% |
|---|---|---|---|---|---|---|
| U2R | DR | 0.0 | 46.0 | 50.0 | 50.0 | 53.0 |
| FAR | 0.0 | 0.000714 | 0.000714 | 0.000714 | 0.002381 | |
| PR | 0.0 | 97.5 | 98.0 | 98.3333 | 95.0833 | |
| R2L | DR | 40.5749 | 25.8345 | 88.4129 | 85.2031 | 87.6079 |
| FAR | 0.0683 | 0.0546 | 0.0338 | 0.0417 | 0.0304 | |
| PR | 54.1291 | 51.8648 | 86.0219 | 82.1050 | 87.3424 | |
| Probe | DR | 94.2930 | 60.6635 | 98.3743 | 91.3207 | 98.0866 |
| FAR | 0.0205 | 5.2973 | 0.0059 | 0.0210 | 0.0191 | |
| PR | 97.3859 | 8.6734 | 99.2979 | 97.2964 | 97.7086 | |
| Normal | DR | 99.7395 | 91.1490 | 99.8172 | 99.6618 | 99.7630 |
| FAR | 0.8460 | 1.1389 | 0.0863 | 0.1722 | 0.1011 | |
| PR | 96.6281 | 95.1134 | 99.6447 | 99.2928 | 99.5822 | |
| DoS | DR | 99.3782 | 94.1923 | 99.9890 | 99.9729 | 99.9741 |
| FAR | 0.0951 | 3.0902 | 0.0522 | 0.1365 | 0.0548 | |
| PR | 99.9750 | 99.1521 | 99.9864 | 99.9643 | 99.9857 | |
| ALL | DR | 99.1539 | 98.8610 | 99.9136 | 99.8277 | 99.8988 |
| FAR | 0.2604 | 8.8509 | 0.18276 | 0.3381 | 0.2369 | |
| PR | 99.9363 | 97.8693 | 99.9557 | 99.9176 | 99.9425 |
| [1] | ALMSEIDIN M, ALZUBI M, KOVACS S, et al.Evaluation of Machine Learning Algorithms for Intrusion Detection System[C]//IEEE.15th IEEE International Symposium on Intelligent Systems and Informatics, September 14-16, 2017, Subotica, Serbia. New York: IEEE, 2017: 277-282. |
| [2] | AMUDHA P, KARTHIK S, SIVAKUMARI S.Classification Techniques for Intrusion Detection-An Overview[J]. International Journal of Computer Applications, 2014, 76(16): 33-40. |
| [3] | HINTON G E.Rectified Linear Units Improve Restricted Boltzmann Machines Vinod Nair[C]//IMLS.27th International Conference on Machine Learning(ICML-10), June 21-24, 2010, Haifa, Israel.Madison:Omnipress, 2010:807-814. |
| [4] | MUDA Z, YASSIN W, SULAIMAN M N, et al.Intrusion Detection Based on K-Means Clustering and Naïve Bayes Classification[C]// IEEE.17th International Conference on Information Technology in Asia, July 12-13, 2011, Kuching, Sarawak, Malaysia. New York:IEEE, 2011:192-197. |
| [5] | KLINE D M, BERARDI V L.Revisiting Squared-error and Cross-entropy Functions for Training Neural Network Classifiers[J]. Neural Computing&Applications, 2005, 14(4): 310-318. |
| [6] | MUKKAMALA S, JANOSKI G, SUNG A.Intrusion Detection Using Neural Networks and Support Vector Machines[C]// IEEE.International Joint Conference on Neural Networks, May 12-17, 2002, Honolulu, HI, USA. New York:IEEE, 2002:1702-1707. |
| [7] | LECUN Y, BENGIO Y, HINTON G.Deep learning[J]. Nature, 2015, 521(7553):436-444. |
| [8] | HOQUE M S, MUKIT M A, BIKAS M A N. An Implementation of Intrusion Detection System Using Genetic Algorithm[J]. International Journal of Network Security & Its Applications, 2012, 4(2):109-120. |
| [9] | LAKHINA S, JOSEPH S, VERMA B.Feature Reduction using Principal Component Analysis for Effective Anomaly-Based Intrusion Detection on NSL-KDD[J]. International Journal of Engineering Science & Technology, 2010, 2(6):3175-3180. |
| [10] | KDD.KDD Cup 1999 Data[EB/OL]. |
| [11] | HYVARINENA. Fast and Robust Fixed-point Algorithms for Independent Component Analysis[J]. IEEE Transactions on Neural Networks, 1999, 10(3):626-634. |
| [12] | KINGMA D P.Adam: A Method for Stochastic Optimization[J]. Computer Science, 2014, 1412(6980):1-15. |
| [13] | MUKHERJEE S, SHARMA N.Intrusion Detection Using Naive Bayes Classifier with Feature Reduction[J]. Procedia Technology, 2012, 4(11):119-128. |
| [14] | SUBBA B, BISWASS, KARMAKAR S.Intrusion Detection Systems Using Linear Discriminant Analysis and Logistic Regression[C]// IEEE.2015 Annual IEEE India Conference (INDICON), December 17-20, 2015, New Delhi, India. New York:IEEE, 2016:1-6. |
| [15] | MOORE B.Principal Component Analysis in Linear Systems: Controllability, Observability, and Model Reduction[J]. IEEE Transactions on Automatic Control, 2003, 26(1):17-32. |
| [16] | PHAM D T, GARAT P.Blind Separation of Mixture of Independent Sources Through a Quasi-maximum Likelihood Approach[J]. IEEE Transactions on Signal Processing, 1997, 45(7):1712-1725. |
| [17] | MALOUCHE Z, MACCHI O.Adaptive Unsupervised Extraction of One Component of ALinear Mixture with A Single Neuron[J]. IEEE Transactions on Neural Networks, 1998, 9(1):123-138. |
| [18] | RIO, RENNER R, et al.The Thermodynamic Meaning of Negative Entropy[J]. Nature, 2011, 474(7349):61-63. |
| [19] | GLOROT X, BENGIO Y.Understanding the Difficulty of Training Deep Feedforward Neural Networks[J]. Journal of Machine Learning Research, 2010, 9(1):249-256. |
| [20] | QI Mingyu, LIU Ming, FU Yanming.Research on Network Intrusion Detection Using Machines Based on Principal ComponentSupport Vector Analysis[J]. Netinfo Security, 2015, 15(2):15-18 |
| 戚名钰,刘铭,傅彦铭.基于PCA的SVM网络入侵检测研究[J].信息网络安全,2015,15(2):15-18. | |
| [21] | GAO Ni, GAO Ling, HE Yiyue, et al.A Lightweight Intrusion Detection Model Based on Autoencoder Network with Feature REduction[J].Acta Electronica Sinica, 2017, 45(3):730-739. |
| 高妮,高岭,贺毅岳,等.基于自编码网络特征降维的轻量级入侵检测模型[J].电子学报,2017,45(3):730-739. | |
| [22] | ZHANG Xuebo, LIU Jinghao, FU Xiaomei.Design and Implementation of Anti Web DDoS Attack Model Based on Improved Logistic Regression Algorithm[J]. Netinfo Security, 2017, 17(6):62-67 |
| 张雪博,刘敬浩,付晓梅.基于改进Logistic回归算法的抗WebDDoS攻击模型的设计与实现[J].信息网络安全,2017,17(6):62-67. | |
| [23] | WANG Jianxiong, ZHANG Limin, ZHONG Zhaogen.Blind Source Separation Based on FastICA Algorithm[J]. Computer Technology and Development, 2011, 21(12):93-96. |
| 王建雄,张立民,钟兆根.基于FastICA算法的盲源分离[J].计算机技术与发展, 2011,21(12):93-96. | |
| [24] | GUO Chonghui, JIA Hongfeng, ZHANG Na.Time Series Clustering Based on ICA for Stock Data Analysis[J]. Operations Researchand Management Science, 2008, 17(5):120-124. |
| 郭崇慧,贾宏峰,张娜.基于ICA的时间序列聚类方法及其在股票数据分析中的应用[J].运筹与管理,2008,17(5):120-124. | |
| [25] | LAN Rongwei, SUN Huaijiang.Style Analysis and Human Locomotion Synthesis Based on Inverse Kinematics and Reconstructive ICA[J]. Acta Automatica Sinica, 2014, 40(6):1135-1147. |
| 蓝荣祎,孙怀江.基于逆运动学和重构式ICA的人体运动风格分析与合成[J].自动化学报,2014,40(6):1135-1147. | |
| [26] | MA Chenxi.Chinese Event Detection Based on Recurrent Neural Network[J]. Netinfo Security,2018, 18(5):75-81. |
| 马晨曦. 基于递归神经网络的中文事件检测[J].信息网络安全,2018,18(5):75-81. |
| [1] | 王蓉, 马春光, 武朋. 基于联邦学习和卷积神经网络的入侵检测方法[J]. 信息网络安全, 2020, 20(4): 47-54. |
| [2] | 罗文华, 许彩滇. 基于改进MajorClust聚类的网络入侵行为检测[J]. 信息网络安全, 2020, 20(2): 14-21. |
| [3] | 康健, 王杰, 李正旭, 张光妲. 物联网中一种基于多种特征提取策略的入侵检测模型[J]. 信息网络安全, 2019, 19(9): 21-25. |
| [4] | 冯文英, 郭晓博, 何原野, 薛聪. 基于前馈神经网络的入侵检测模型[J]. 信息网络安全, 2019, 19(9): 101-105. |
| [5] | 饶绪黎, 徐彭娜, 陈志德, 许力. 基于不完全信息的深度学习网络入侵检测[J]. 信息网络安全, 2019, 19(6): 53-60. |
| [6] | 陈虹, 肖越, 肖成龙, 陈建虎. 融合最大相异系数密度的SMOTE算法的入侵检测方法[J]. 信息网络安全, 2019, 19(3): 61-71. |
| [7] | 田峥, 李树, 孙毅臻, 黎曦. 一种面向S7协议的工控系统入侵检测模型[J]. 信息网络安全, 2019, 19(11): 8-13. |
| [8] | 张阳, 姚原岗. 基于Xgboost算法的网络入侵检测研究[J]. 信息网络安全, 2018, 18(9): 102-105. |
| [9] | 张戈琳, 李勇. 非负矩阵分解算法优化及其在入侵检测中的应用[J]. 信息网络安全, 2018, 18(8): 73-78. |
| [10] | 魏书宁, 陈幸如, 焦永, 王进. AR-OSELM算法在网络入侵检测中的应用研究[J]. 信息网络安全, 2018, 18(6): 1-6. |
| [11] | 和湘, 刘晟, 姜吉国. 基于机器学习的入侵检测方法对比研究[J]. 信息网络安全, 2018, 18(5): 1-11. |
| [12] | 刘超玲, 张棪, 杨慧然, 吴宏晶. 基于DPDK的虚拟化网络入侵防御系统设计与实现[J]. 信息网络安全, 2018, 18(5): 41-51. |
| [13] | 陈红松, 王钢, 宋建林. 基于云计算入侵检测数据集的内网用户异常行为分类算法研究[J]. 信息网络安全, 2018, 18(3): 1-7. |
| [14] | 翟继强, 肖亚军, 杨海陆, 王健. 改进的人工蜂群结合优化的随机森林的U2R攻击检测研究[J]. 信息网络安全, 2018, 18(12): 38-45. |
| [15] | 赵旭, 黄光球, 崔艳鹏, 王明明. 基于改进选择算子的NIDS多媒体包多线程择危处理模型[J]. 信息网络安全, 2018, 18(10): 45-50. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||