信息网络安全 ›› 2020, Vol. 20 ›› Issue (7): 60-69.doi: 10.3969/j.issn.1671-1122.2020.07.007
Android系统应用程序DEX文件保护方法研究
- 1. 北京理工大学信息系统及安全对抗实验中心,北京 100081
2. 国家计算机网络与信息安全管理中心,北京 100094
-
收稿日期:2019-09-23出版日期:2020-07-10发布日期:2020-08-13 -
通讯作者:杨鹏 E-mail:yp@cert.org.cn -
作者简介:袁晓筱(1994—),女,江苏,硕士研究生,主要研究方向为Android软件安全|罗森林(1968—),男,河北,教授,博士,主要研究方向为网络安全、文本安全、媒体安全、数据挖掘|杨鹏(1982—),男,内蒙古,高级工程师,博士,主要研究方向为信息安全、人工智能 -
基金资助:国家242信息安全专项(2019A021)
Research on Android Application DEX File Protection Method
YUAN Xiaoxiao1, LUO Senlin1, YANG Peng2( )
)
- 1. Information System & Security and Countermeasures Experiments Center, Beijing Institute of Technology, Beijing 100081, China
2. National Computer Network Emergency Response Technical Team Coordination Center of China, Beijing 100094, China
-
Received:2019-09-23Online:2020-07-10Published:2020-08-13 -
Contact:Peng YANG E-mail:yp@cert.org.cn
摘要:
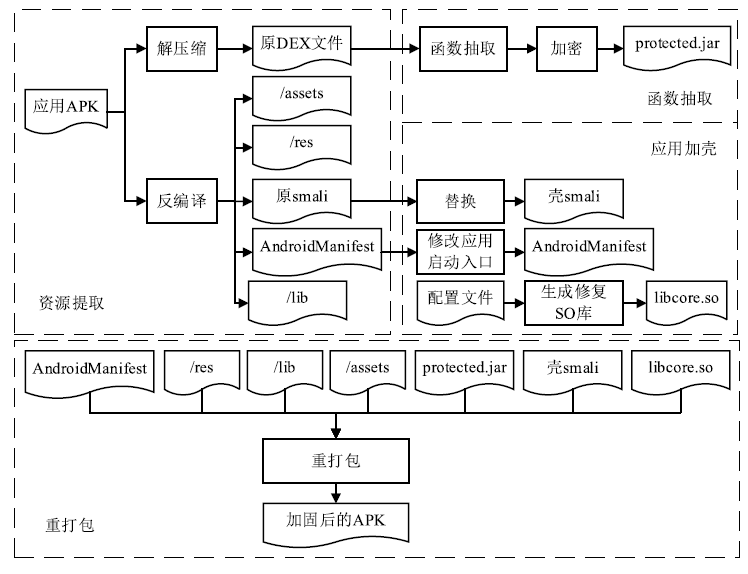
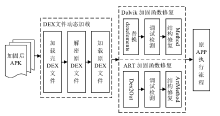
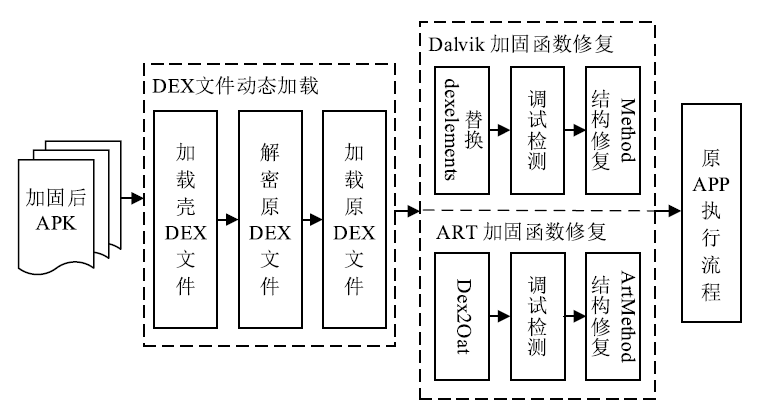
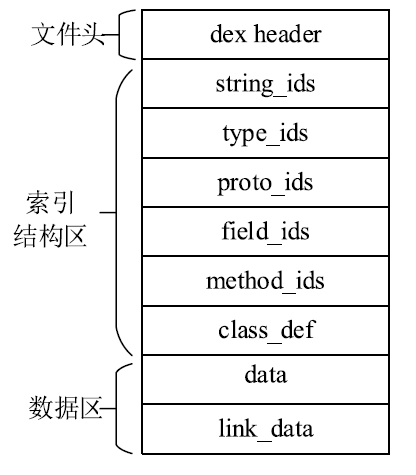
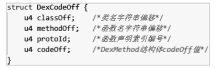
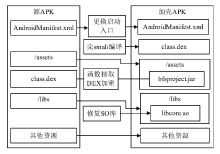
针对函数级DEX文件保护方法在函数修复过程中难以抵御动态恢复攻击且无法兼容ART虚拟机的问题,文章提出一种基于函数抽取和隐式恢复的DEX文件保护方法。该方法首先对DEX文件中的关键函数进行抽取,然后对DEX文件进行重构、整体加密、重命名和隐藏,接着通过修改APP启动入口和更换smali文件实现加壳,最后添加修复SO库完成对APK的加固。应用程序启动时,利用壳程序解密获取原DEX文件,并将原DEX解析加载到内存中,分别基于Dalvik虚拟机和ART虚拟机对加固函数进行修复,正常执行应用程序内部逻辑。以自主开发APK中的DEX文件为实验对象进行实验,结果表明,该方法能有效抵御静态分析和动态恢复攻击,同时能兼容两种虚拟机,且函数运行的时间增量为常量。
中图分类号:
引用本文
袁晓筱, 罗森林, 杨鹏. Android系统应用程序DEX文件保护方法研究[J]. 信息网络安全, 2020, 20(7): 60-69.
YUAN Xiaoxiao, LUO Senlin, YANG Peng. Research on Android Application DEX File Protection Method[J]. Netinfo Security, 2020, 20(7): 60-69.
| [1] | CHRISTIAN C, CLARK T, DOUGLAS L. A Taxonomy of Obfuscating Transformations[R]. New Zealand: University of Auckland, TR# 148, 1997. |
| [2] | SCHULZ P. Code Protection in Android[R]. Germany: Rheinische Friedrich-Wilhelms-Universitgt Bonn, TR# 110, 2012. |
| [3] | SHU Junliang, LI Juanru, ZHANG Yuanyuan, et al. Android APP Protection via Interpretation Obfuscation[C]// IEEE. 2014 IEEE 12th International Conference on Dependable, Autonomic and Secure Computing (DASC), August 20-22, 2014, Dalian, China. New York: IEEE, 2014: 63-68. |
| [4] | WANG Dejia, SONG Chao, LIU Jiajung. Deep Code Obfuscation Method for Android System Application : China, 103544414A[P]. 2014. |
| 汪德嘉, 宋超, 刘家郡. 一种Android 系统应用的深度代码混淆方法: 中国,103544414A[P]. 2014. | |
| [5] | LIU Fangyuan, MENG Xianjia, TANG Zhanyong, et al. Android Application Protection Method Based on Smali Code Obfuscation[J]. Journal of Shandong University, 2017,52(3):44-50. |
| 刘方圆, 孟宪佳, 汤战勇, 等. 基于smali代码混淆的Android应用保护方法[J]. 山东大学学报(理学版), 2017,52(3):44-50. | |
| [6] | SU Yuanqing. Research on Android-based Software Protection Based on Dynamic Loading[D]. Xi'an: Xidian University, 2014. |
| 宿元庆. Android基于动态加载的软件保护研究[D]. 西安:西安电子科技大学, 2014. | |
| [7] | DONG Hang. Research on Mobile Application Monitoring and Protection Technology[D]. Beijing: Beijing University of Posts and Telecommunications, 2014. |
| 董航. 移动应用程序检测与防护技术研究[D]. 北京:北京邮电大学, 2014. | |
| [8] | ZHU Hongjun, CHEN Yaoguang, HUA Baojian, et al. An Android Application Reinforcement Solution[J]. Computer Application and Software, 2016,11(33):297-300, 320. |
| 朱洪军, 陈耀光, 华保健, 等. 一种Android应用加固方案[J]. 计算机应用与软件, 2016,11(33):297-300,320. | |
| [9] | KIM N K, SHIM J, CHO S, et al. Android Application Protection Against Static Reverse Engineering Based on MultiDexing[J]. Journal of Internet Services and Information Security, 2016,11(6):54-64. |
| [10] | ZHOU W, WANG Z, ZHOU Y Z. et al. DIVILAR: Diversifying Intermediate Language for Anti-repacking on Android Platform[C]// SIGSAC. 4th ACM Conference on Data and Application Security and Privacy, March 15-17, 2014, San Antonio Texas USA. New York: ACM, 2014: 199-210. |
| [11] | WANG Zehua. Research and Implementation of Android Software Security Hardening Technology[D]. Chengdu: University of Electronic Science and Technology of China, 2016. |
| 王泽华. Android软件安全加固技术研究与实现[D]. 成都:电子科技大学, 2016. | |
| [12] | LIU Jiajia. Research on An Application Protection Method Based on Virtual Machine Customization[D]. Nanjing: Nanjing University of Science and Technology, 2017. |
| 刘佳佳. 一种基于虚拟机定制的应用保护方法研究[D]. 南京:南京理工大学, 2017. | |
| [13] | Tencent Cloud. Tencent Legu[EB/OL]. https://www.qcloud.com/product/cr.html, 2017-3-9. |
| 腾讯云. 腾讯乐固[EB/OL]. https://www.qcloud.com/product/cr.html, 2017-3-9. | |
| [14] | Bangbang Safety. Bangbang Reinforcement[EB/OL]. http://www.bangcle.com, 2017-11-10. |
| 梆梆安全. 梆梆加固[EB/OL]. http://www.bangcle.com, 2017-11-10. | |
| [15] | LIU Huiming. Android Application Automatic Localization and Obfuscation Sysytem[J]. Microelectronics and Computer, 2016,33(10):50-62. |
| 刘惠明. 安卓应用自动原生化及混淆系统[J]. 微电子学与计算机, 2016,33(10):50-62. | |
| [16] | MULLINER C. Android DDI: Introduction to Dynamic Dalvik Instrumentation[EB/OL]. https://github.com/crmulliner/ddi, 2019-5-11. |
| [17] | Hey-Rays . IDA[EB/OL]. https://www.hex-rays.com/products/ida/index.shtml, 2015-5-27. |
| [18] | Google. Apktool[EB/OL]. http://www.softpedia.com/get/Programming/Debuggers-Dec-ompilers-Dissase-mblers/ApkTool.html, 2017-9-22. |
| [19] | Android Open Source. Dalvik Executable File Format[EB/OL]. https://source.androi-d.google.cn/devices/tech/dalvik/dexformat?hl=zh-cn, 2017-8-23. |
| [20] | Lambdalang . DexExtractor[EB/OL]. https://github.com/lambdalang/DexExtractor, 2015-7-11. |
| [21] | Oracle. Java[EB/OL]. http://www.java.com, 2019-5-12. |
| [22] | Android Open Source Project. Dalvik and Dalvik Virtual Machine[EB/OL]. http://code.google.com/p/dalvik/, 2019-5-12. |
| [23] | Android Open Source Project. Bytecode for the Dalvik VM[EB/OL]. http://source.android.com/tech/dalvik/dalvik-bytecode.html, 2019-5-12. |
| [24] | RYSZARD W, CONNOR T. Apktool[EB/OL]. https://ibotpeaibot.github.io/Apktool/, 2019-5-3. |
| [25] | SKYLOT . Dex to Java Decompiler[EB/OL]. https://github.com/skylot/jadx, 2019-5-12. |
| [26] | SWEETSCAPE SOFTWARE. 010 Editor[EB/OL]. https://www.sweetscape.com/010editor/, 2019-4-26. |
| [1] | 侯留洋, 罗森林, 潘丽敏, 张笈. 融合多特征的Android恶意软件检测方法[J]. 信息网络安全, 2020, 20(1): 67-74. |
| [2] | 宋鑫, 赵楷, 张琳琳, 方文波. 基于随机森林的Android恶意软件检测方法研究[J]. 信息网络安全, 2019, 19(9): 1-5. |
| [3] | 丁丽萍, 刘雪花, 陈光宣, 李引. Android智能手机动态内存取证技术综述[J]. 信息网络安全, 2019, 19(2): 10-17. |
| [4] | 宋新龙, 郑东, 杨中皇. 基于AOSP与SELinux的移动设备管理系统[J]. 信息网络安全, 2017, 17(9): 103-106. |
| [5] | 陆德冰, 崔浩亮, 张文, 牛少彰. 基于Intent过滤的应用安全加固方案[J]. 信息网络安全, 2017, 17(11): 67-73. |
| [6] | 刘佳佳, 俞研, 胡恒伟, 吴家顺. 一种基于虚拟机定制的应用保护方法研究[J]. 信息网络安全, 2017, 17(1): 63-67. |
| [7] | 文伟平, 汤炀, 谌力. 一种基于Android内核的APP敏感行为检测方法及实现[J]. 信息网络安全, 2016, 16(8): 18-23. |
| [8] | 余丽芳, 杨天长, 牛少彰. 一种增强型Android组件间安全访问控制方案[J]. 信息网络安全, 2016, 16(8): 54-60. |
| [9] | 曲乐炜, 罗森林, 孙志鹏, 朱帅. Android系统数据完整性检测方法研究[J]. 信息网络安全, 2016, 16(8): 61-67. |
| [10] | 张家旺, 李燕伟. 基于N-gram算法的恶意程序检测系统研究与设计[J]. 信息网络安全, 2016, 16(8): 74-80. |
| [11] | 杨静雅, 罗森林, 朱帅, 曲乐炜. 基于多层次交叉视图分析的Android系统恶意行为监控方法研究[J]. 信息网络安全, 2016, 16(7): 40-46. |
| [12] | 李亚萌, 何泾沙. 基于Hash的YAFFS2文件各版本恢复算法研究[J]. 信息网络安全, 2016, 16(5): 51-57. |
| [13] | 文伟平, 张汉, 曹向磊. 基于Android可执行文件重组的混淆方案的设计与实现[J]. 信息网络安全, 2016, 16(5): 71-77. |
| [14] | 丁庸, 曹伟, 罗森林. 基于LKM系统调用劫持的恶意软件行为监控技术研究[J]. 信息网络安全, 2016, 16(4): 1-8. |
| [15] | 李桂芝, 韩臻, 周启惠, 王雅哲. 基于Binder信息流的Android恶意行为检测系统[J]. 信息网络安全, 2016, 16(2): 54-59. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||