信息网络安全 ›› 2019, Vol. 19 ›› Issue (6): 37-44.doi: 10.3969/j.issn.1671-1122.2019.06.005
不同口令组成策略下用户真实口令的安全性分析
- 华中师范大学计算机学院,湖北武汉 430079
-
收稿日期:2019-03-27出版日期:2019-06-10发布日期:2020-05-11 -
作者简介:作者简介:郭亚军(1965—),男,湖北,教授,博士,主要研究方向为信息安全;叶贝(1994—),女,湖北,硕士研究生,主要研究方向为信息安全;周伟(1980—),男,湖北,讲师,博士,主要研究方向为信息安全。
-
基金资助:国家自然科学基金[61772224];中央高校基本科研业务费资助项目 [CCNU19ZN008]
Security Analysis of User Real Password under Different Password Composition Policies
- School of Computer, Central China Normal University, Wuhan Hubei 430079, China
-
Received:2019-03-27Online:2019-06-10Published:2020-05-11
摘要:
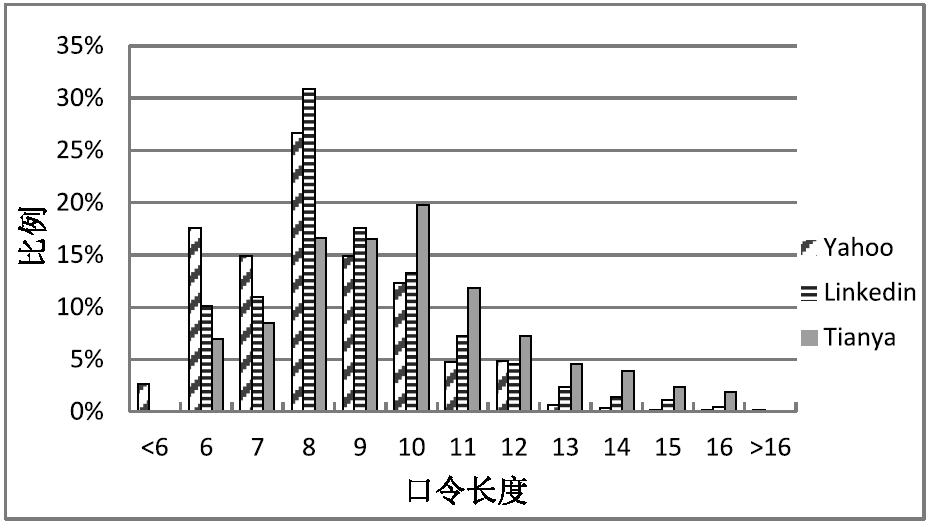
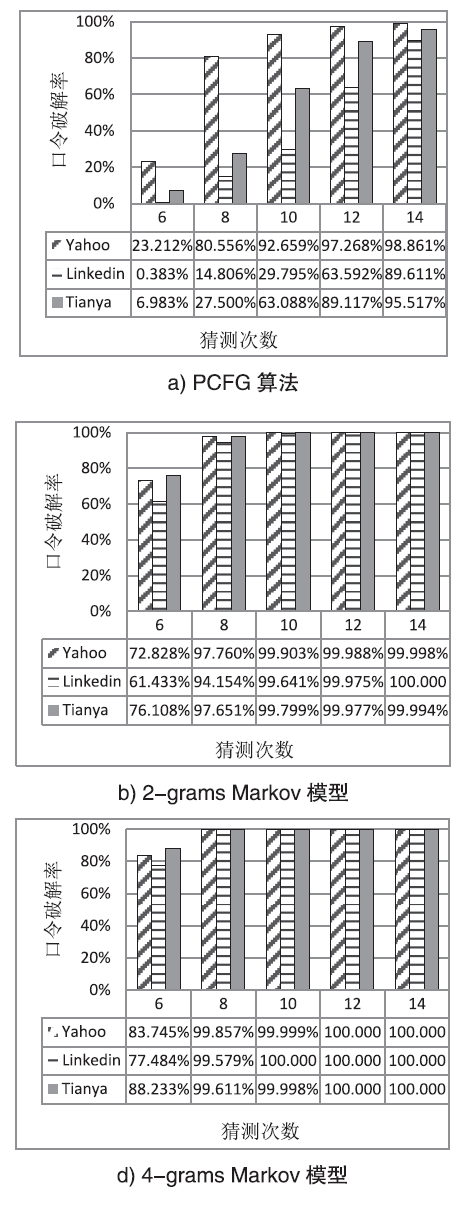
口令组成策略对用户创建口令的长度和复杂性提出了要求。目前的一些研究表明,使用口令组成策略有助于提高用户口令强度,但是这些研究主要是通过招募参与者的形式在实验室或者网络上进行,参与者被要求创建的口令并不一定出现在现实中。不同于这些研究,文章从实际出发,利用网站中泄露出来的真实口令,研究现实网站中采用较多的几种口令组成策略对用户创建口令所产生的影响。文章主要比较了没有口令组成策略、basic6策略和2class6策略这3种情形下真实口令的一些特征,分析了这些口令的安全性。研究发现,口令组成策略会对用户所选择口令的长度和字符类型造成影响,要求多字符类型的口令组成策略会增加口令的长度。此外,研究也发现,上述3类口令组成策略都不能很好地帮助用户创建强口令。
中图分类号:
引用本文
郭亚军, 叶贝, 周伟. 不同口令组成策略下用户真实口令的安全性分析[J]. 信息网络安全, 2019, 19(6): 37-44.
Yajun GUO, Bei YE, Wei ZHOU. Security Analysis of User Real Password under Different Password Composition Policies[J]. Netinfo Security, 2019, 19(6): 37-44.
表1
部分国内外网站所采用的口令组成策略
| 网站 | 口令长度要求 | 口令组成结构要求 |
|---|---|---|
| 腾讯 | 8 ~ 16位字符 | 必须包含字母、数字和符号中的至少两种;不允许有空格 |
| 淘宝 | 6 ~ 20位字符 | 只能包含字母、数字及标点符号(除空格),且至少包含其中两种 |
| 百度 | 6 ~ 14位字符 | 支持数字、大小写字母和标点符号;不允许有空格 |
| 新浪微博 | 6 ~ 16位字符 | 支持数字、大小写字母和标点符号;不允许有空格 |
| Tianya (天涯社区) | 至少6位数字 | 至少包含数字和字母 |
| 搜狐 | 8 ~ 16位字符 | 字母数字组合,可含特殊字符 |
| 网易 | 6 ~ 16位字符 | 区分大小写,无其他要求 |
| 苏宁易购 | 6 ~ 20 位字符 | 只能由字母、数字及符号组成,且必须包含其中至少两种 |
| 京东 | 6 ~ 20位字符 | 包含字母、数字和标点符号中的至少两种 |
| 搜狗 | 6 ~ 16位字符 | 可以使用字母(区分大小写)、数字、符号 |
| 爱奇艺 | 8 ~ 20位字符 | 使用字母、数字、符号中的至少两种 |
| CSDN | 11 ~ 20位字符 | 必须包含字母和数字 |
| 360 | 8 ~ 20位字符 | 至少包含数字、字母及符号中的两种;不允许有空格 |
| 12306 | 6 ~ 20位字符 | 必须且只能包含字母、数字、下划线中的至少两种 |
| Microsoft | 至少8位字符 | 至少两种字符种类 |
| Github | 至少7位字符 | 至少包含数字和字母 |
| 至少8位字符 | 混合使用字母、数字和符号 | |
| 至少6位字符 | 无其他要求 |
表3
数据集中出现次数排名前10的10个口令、它们的数量和所占比例
| Yahoo | Tianya | ||
|---|---|---|---|
| 1 | 123456 : 1673 (0.38%) | lau.guillard : 3 (0.00%) | 111222tianya : 48664 (0.63%) |
| 2 | password : 780 (0.18%) | lilll3@aol.com : 3 (0.00%) | a123456 : 20421 (0.26%) |
| 3 | welcome : 437 (0.10%) | chienquifume : 3 (0.00%) | abc123 : 14853 (0.19%) |
| 4 | ninja : 333 (0.08%) | 64binjaipark : 3 (0.00%) | 123456a : 12158 (0.16%) |
| 5 | abc123 : 250 (0.06%) | Sk@P#nk32 : 3 (0.00%) | 123qwe : 8564 (0.11%) |
| 6 | 123456789 : 226 (0.05%) | gbcllcnov212001 : 3 (0.00%) | 1qaz2wsx : 7429 (0.10%) |
| 7 | 12345678 : 208 (0.05%) | F6nt0m6SS : 3 (0.00%) | 123456abc : 5687 (0.07%) |
| 8 | sunshine : 205 (0.05%) | ornakdie.2 : 3 (0.00%) | qq123456 : 5452 (0.07%) |
| 9 | princess : 202 (0.05%) | papiCygelo : 3 (0.00%) | 123abc : 5387 (0.07%) |
| 10 | 0 : 202 (0.05%) | Eels5model : 3 (0.00%) | *123456 : 5156 (0.06%) |
表6
数据集中不同字符使用频率排列情况
| 数据集 | 字符频率降序排列 |
|---|---|
| Yahoo | aeio1rnslt2m0cd3hub9y478gp5k6wfjvzxqASMELNRTBCD!IJPOHG@- YKUW$F_*V#ZXQ.:&+%^Space=?/~,()][`|\}{ |
| aei1nrosl02tmd3cuhk947b85g6pyjfvwzxASML!@BRCTENDIPqKJGH OF$.#W*U_V-YZX&Q%+Space?/,)=(;^:’~[“]`<>\|{} | |
| Tianya | 12083956a74niylhegwxsozucjqdmbtfrkp.E+vAIHLCNGYJDBFWSZ@XQMUTOKPR_-*V!#/?=$&%~`)^([]\>;:<{}|”,’ |
表7
数据集中包含不同口令字符结构的口令分布情况
| 口令结构 | Yahoo | Tianya | |
|---|---|---|---|
| 只包含数字 | 5.82%(25760) | 3.48%(194568) | 0.00%(0) |
| 只包含大写字母 | 0.40%(1779) | 0.55%(31063) | 0.00%(0) |
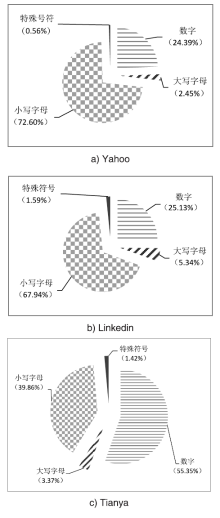
| 只包含小写字母 | 33.09%(146515) | 20.87%(1167902) | 0.00%(0) |
| 只包含特殊符号 | 0.00%(16) | 0.00%(198) | 0.00%(0) |
| 包含大小写字母 | 1.16%(5122) | 2.56%(143540) | 0.00%(0) |
| 包含大写字母和数字 | 0.77%(3401) | 1.31%(73057) | 3.02%(234179) |
| 包含大写字母和特殊符号 | 0.01%(64) | 0.04%(2508) | 0.00%(0) |
| 包含小写字母和数字 | 50.30%(222740) | 43.80%(2451521) | 82.33%(6382063) |
| 包含小写字母和特殊符号 | 0.49%(2185) | 1.32%(73684) | 0.00%(0) |
| 包含数字和特殊符号 | 0.04%(183) | 0.08%(4734) | 0.00%(0) |
| 包含大小写字母和数字 | 5.22%(23134) | 16.09%(900347) | 6.46%(500612) |
| 包含大小写字母和特殊符号 | 0.11%(492) | 0.66%(37201) | 0.00%(0) |
| 包含大写字母、数字和 特殊符号 | 0.12%(552) | 0.25%(14261) | 4.07%(315474) |
| 包含小写字母、数字和 特殊符号 | 1.37%(6074) | 4.43%(247935) | 3.82%(296019) |
| 包含所有字符类 | 1.09%(4815) | 4.55%(254780) | 0.30%(23578) |
| [1] | GUAN Zhensheng.Concerning the Electronic Payment Identity Authentication Technology[J]. Netinfo Security, 2011, 11(3): 9-11. |
| 关振胜. 论电子支付中的身份认证技术[J].信息网络安全,2011,11(3):9-11. | |
| [2] | DARWISH A A, ZAKI W M, SAAD O M, et al.Human Authenti- cation Using Face and Fingerprint Biometrics[C]//IEEE. The 2nd International Conference on Computational Intelligence, Communication Systems and Networks, July 28-30, 2010, Liverpool, UK.NJ: IEEE, 2010: 274-278. |
| [3] | WANG C J.The Solution Design Using USB Key for Network Security Authentication[C]//IEEE. Fourth International Conference on Computational Intelligence and Communication Networks, November 3-5, 2012, Mathura, India.NJ: IEEE, 2012: 766-769. |
| [4] | BONNEAU J, HERLEY C, VAN OORSCHOT P C, et al. Passwords and the Evolution of Imperfect Authentication[J]. Communications of the ACM, 2015, 58(7): 78-87. |
| [5] | BONNEAU J, HERLEY C, VAN OORSCHOT P C, et al. The Quest to Replace Passwords: A Framework for Comparative Evaluation of Web Authentication Schemes[C]//IEEE. 2012 IEEE Symposium on Security and Privacy, May 20-23, 2012, San Francisco, CA, USA.NJ: IEEE, 2012: 553-567. |
| [6] | UR B, NOMA F, BEES J, et al.I Added "!"at the End to Make It Secure: Observing Password Creation in the Lab[C]// USENIX. Symposium on Usable Privacy and Security, July 22-24, 2015, Ottawa, Canada. Berkeley: USENIX Association, 2015: 123-135. |
| [7] | WASH R, RADER E, BERMAN R, et al.Understanding Password Choices: How Frequently Entered Passwords Are Reused Across Websites[C]//USENIX. The Twelfth Symposium on Usable Privacy and Security, June 22-24, 2016, Denver, CO, USA. Berkeley: USENIX Association, 2016: 175-188. |
| [8] | KASSIM M M, SUJITHA A.ProcurePass: A User Authentication Protocol to Resist Password Stealing and Password Reuse Attack[C]//IEEE. 2013 International Symposium on Computational and Business Intelligence, August 24-26, 2013, New Delhi, India. NJ: IEEE, 2013: 31-34. |
| [9] | DAS A, BONNEAU J, CAESAR M, et al.The Tangled Web of Password Reuse[C]//NDSS. NDSS’14, February 23-26, 2014, San Diego, CA, USA. Copyright 2014 Internet Society, 2014: 23-26. |
| [10] | KOMANDURI S, SHAY R, KELLEY P G, et al.Of Passwords and People: Measuring the Effect of Password-composition Policies[C]//ACM. The SIGCHI Conference on Human Factors in Computing Systems, May 7-12, 2011, Vancouver, BC, Canada. New York: ACM, 2011: 2595-2604. |
| [11] | WANG Ding, WANG Ping.The Emperor’s New Password Creation Policies[M]// Springer. Computer Security-ESORICS 2015. Cham: Springer, Cham, 2015: 456-477. |
| [12] | GUO Yimin, ZHANG Zhenfeng.LPSE: Lightweight Password-strength Estimation for Password Meters[J]. Computers & Security, 2018, 77(3): 507-518. |
| [13] | WHEELER D L. zxcvbn: Low-Budget Password Strength Estimation[C]//USENIX. The 25th USENIX Security Symposium, August 10-12, 2016, Austin, TX, USA. Berkeley: USENIX Association, 2016: 157-173. |
| [14] | SHAY R, KOMANDURI S, KELLEY P G, et al.Encountering Stronger Password Requirements: User Attitudes and Behaviors[C]//ACM. The Sixth Symposium on Usable Privacy and Security, July 14-16, 2010, Redmond, Washington, USA . New York: ACM, 2010: 2. |
| [15] | WEIR M, AGGARWAL S, COLLINS M, et al.Testing Metrics for Password Creation Policies by Attacking Large Sets of Revealed Passwords[C]//ACM. The 17th ACM Conference on Computer and Communications Security, October 4-8, 2010, Chicago, Illinois, USA. New York: ACM, 2010: 162-175. |
| [16] | PROCTOR R W, LIEN M C, VU K P L, et al. Improving Computer Security for Authentication of Users: Influence of Proactive Password Restrictions[J]. Behavior Research Methods, Instruments, & Computers, 2002, 34(2): 163-169. |
| [17] | FLORÊNCIO D, HERLEY C, VAN OORSCHOT P C. An Administrator’s Guide to Internet Password `Research[C]///USENIX. The 28th USENIX Conference on Large Installation System Administration, November 9-14, 2014, Seattle, WA, USA. Berkeley: USENIX Association, 2014: 35-52. |
| [18] | BURR W E, DODSON D F, NEWTON E M, et al. Electronic Authentication Guideline[EB/OL]. , 2019-2-14. |
| [19] | SHAY R, KOM S, DURITY A L, et al.Can Long Passwords Be Secure and Usable?[C]//ACM. The 32nd Annual ACM Conference on Human Factors in Computing Systems, April 26-May 1, 2014, Toronto, Ontario, Canada. New York: ACM, 2014: 2927-2936. |
| [20] | VU K P L, TAI B L, BHARGAV A, et al. Promoting Memorability and Security of Passwords Through Sentence Generation[J]. Proceedings of the Human Factors and Ergonomics Society Annual Meeting, 2004, 48(13): 1478-1482. |
| [21] | YANG Weining, LI Ninghui, CHOWDHURY O, et al.An Empirical Study of Mnemonic Sentence-based Password Generation Strategies[C]//ACM. The 2016 ACM SIGSAC Conference on Computer and Communications Security, October 24-28, 2016, Vienna, Austria . New York: ACM, 2016: 1216-1229. |
| [22] | KUO C, ROMANOSKY S, CRANOR L F.Human Selection of Mnemonic Phrase-based Passwords[C]//ACM. The Second Symposium on Usable Privacy and Security, July 12-14, 2006, Pittsburgh, Pennsylvania, USA. New York: ACM, 2006: 67-78. |
| [23] | YAN J, BLACKWELL A, ANDERSON R, et al.Password Memorability and Security: Empirical Results[J]. IEEE Security & Privacy, 2004, 2(5): 25-31. |
| [24] | FORGET A, CHIASSON S, BIDDLE R.Helping Users Create Better Passwords: Is This the Right Approach?[C]//ACM. The 3rd Symposium on Usable Privacy and Security, July 18-20, 2007, Pittsburgh, Pennsylvania, USA. New York: ACM, 2007: 151-152. |
| [25] | FORGET A, CHIASSON S, VAN OORSCHOT P C, et al. Improving Text Passwords Through Persuasion[C]//ACM. The 4th Symposium on Usable Privacy and Security, July 23-25, 2008, Pittsburgh, Pennsylvania, USA. New York: ACM, 2008: 1-12. |
| [26] | HUH J H, OH S, KIM H, et al.Surpass: System-initiated User-replaceable Passwords[C]//ACM. The 22nd ACM SIGSAC Conference on Computer and Communications Security, October 12-16, 2015, Denver, Colorado, USA . New York: ACM, 2015: 170-181. |
| [27] | SEGRETI S M, MELICHER W, KOMANDURI S, et al.Diversify to Survive: Making Passwords Stronger with Adaptive Policies[C]// USENIX. The Thirteenth Symposium on Usable Privacy and Security, July 12-14, 2017, Santa Clara, California, USA. Berkeley: USENIX Association, 2017: 1-12. |
| [28] | YANG S, JI Shouling, BEYAH R.DPPG: A Dynamic Password Policy Generation System[J]. IEEE Transactions on Information Forensics and Security, 2018, 13(3): 545-558. |
| [29] | SCHECHTER S, HERLEY C, MITZENMACHER M. Popularity Is Everything: A New Approach to Protecting Passwords from Statistical-guessing Attacks[EB/OL]. , 2019-2-14. |
| [30] | LI Xiaodong, JIA Huibin.Dynamic Password Authentication System Based on Time Synchronization[J]. Netinfo Security, 2010, 10(5): 69-75. |
| 李晓东,贾慧斌.基于时间同步的动态口令认证系统[J].信息网络安全,2010,10(5):69-75. | |
| [31] | WEIR M, AGGARWAL S, DE MEDEIROS B, et al.Password Cracking Using Probabilistic Context-free Grammars[C]//IEEE. The 30th IEEE Symposium on Security and Privacy, May 17-20, 2009, Berkeley, CA, USA. NJ: IEEE, 2009: 391-405. |
| [32] | NARAYANAN A, SHMATIKOV V.Fast Dictionary Attacks on Passwords Using Time-space Tradeoff[C]//ACM. The 12th ACM conference on Computer and Communications Security, November 7-11, 2005, Alexandria, VA, USA. New York: ACM, 2005: 364-372. |
| [33] | DELL’AMICO M, FILIPPONE M. Monte Carlo Strength Evaluation: Fast and Reliable Password Checking[C]//ACM. The 22nd ACM SIGSAC Conference on Computer and Communications Security, October 12-16, 2015, Denver, Colorado, USA. New York: ACM, 2015: 158-169. |
| [34] | HABIB H, COLNAGO J, MELICHER W, et al.Password Creation in the Presence of Blacklists[C]//USEC. USEC’17, February 26, 2017, San Diego, CA, USA. Copyright 2017 Internet Society, 2017: 50-61. |
| [1] | 刘建伟, 韩祎然, 刘斌, 余北缘. 5G网络切片安全模型研究[J]. 信息网络安全, 2020, 20(4): 1-11. |
| [2] | 江金芳, 韩光洁. 无线传感器网络中信任管理机制研究综述[J]. 信息网络安全, 2020, 20(4): 12-20. |
| [3] | 傅智宙, 王利明, 唐鼎, 张曙光. 基于同态加密的HBase二级密文索引方法研究[J]. 信息网络安全, 2020, 20(4): 55-64. |
| [4] | 赵志岩, 纪小默. 智能化网络安全威胁感知融合模型研究[J]. 信息网络安全, 2020, 20(4): 87-93. |
| [5] | 马力. 网络安全等级保护测评中结论产生的定量计算方法研究[J]. 信息网络安全, 2020, 20(3): 1-8. |
| [6] | 李宁, 李柏潮. 移动互联网的通行证式统一威胁管理架构[J]. 信息网络安全, 2020, 20(3): 18-28. |
| [7] | 张兴隆, 李钰汀, 程庆丰, 郭路路. 一种防范TLS协议降级攻击的浏览器安全模型[J]. 信息网络安全, 2020, 20(3): 65-74. |
| [8] | 黎水林, 祝国邦, 范春玲, 陈广勇. 一种新的等级测评综合得分算法研究[J]. 信息网络安全, 2020, 20(2): 1-6. |
| [9] | 王晓, 赵军, 张建标. 基于可信软件基的虚拟机动态监控机制研究[J]. 信息网络安全, 2020, 20(2): 7-13. |
| [10] | 郎为民, 张汉, 赵毅丰, 姚晋芳. 一种基于区块链的物联网行为监控和活动管理方案[J]. 信息网络安全, 2020, 20(2): 22-29. |
| [11] | 姚萌萌, 唐黎, 凌永兴, 肖卫东. 基于串空间的安全协议形式化分析研究[J]. 信息网络安全, 2020, 20(2): 30-36. |
| [12] | 喻露, 罗森林. RBAC模式下数据库内部入侵检测方法研究[J]. 信息网络安全, 2020, 20(2): 83-90. |
| [13] | 唐春明, 林旭慧. 隐私保护集合交集计算协议[J]. 信息网络安全, 2020, 20(1): 9-15. |
| [14] | 荆涛, 万巍. 面向属性迁移状态的P2P网络行为分析方法研究[J]. 信息网络安全, 2020, 20(1): 16-25. |
| [15] | 胡蝶, 马东堂, 龚旻, 马召. 一种基于PUF的物理层安全认证方法[J]. 信息网络安全, 2020, 20(1): 61-66. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||