信息网络安全 ›› 2019, Vol. 19 ›› Issue (12): 38-46.doi: 10.3969/j.issn.1671-1122.2019.12.005
基于蜜罐加密算法的个人隐私数据保护
- 华中师范大学计算机学院,湖北武汉 430079
-
收稿日期:2019-05-20出版日期:2019-12-10发布日期:2020-05-11 -
作者简介:作者简介:郭亚军(1965—),男,湖北,教授,博士,主要研究方向为信息安全;蒲东齐(1997—),男,海南,硕士研究生,主要研究方向为机器学习、隐私数据保护。
-
基金资助:国家自然科学基金[61772224];中央高校基本科研业务费[CCNU19ZN008]
Privacy Data Protection Based on the Honey Encryption
- School of Computer, Central China Normal University, Wuhan Hubei 430079, China
-
Received:2019-05-20Online:2019-12-10Published:2020-05-11
摘要:
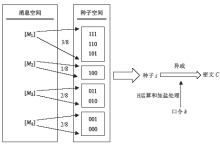
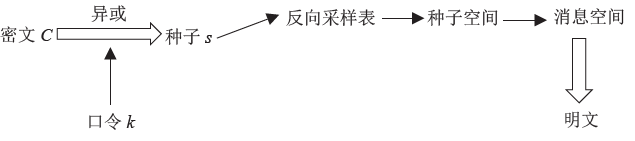
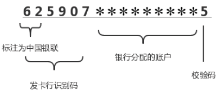
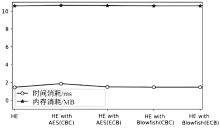
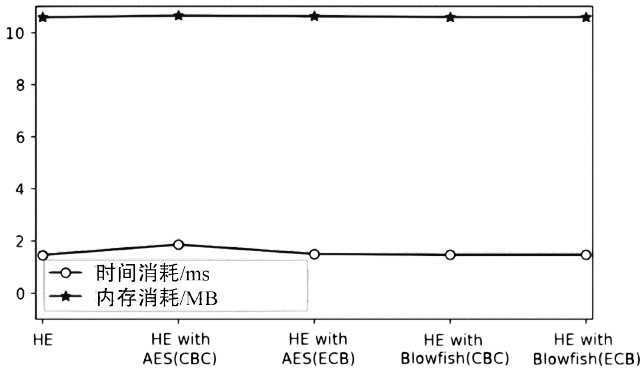
个人隐私数据的保护具有重要的意义。目前常使用基于口令的加密方法来保护个人隐私数据,该方法的安全性依赖于口令选择的强度,而用户往往会趋向于挑选简单的、易于预测的口令。当使用错误猜测的口令对消息进行解密时,该方法会输出无效的消息用以指示失败的攻击尝试,所以不能有效地抵御暴力攻击。因此,文章引入蜜罐加密算法来解决上述问题,在基于口令加密的基础上,引入分布式转换编码器的概念,当攻击者使用暴力穷举攻击对消息进行解密时,系统会提供看似有效的输出来迷惑攻击者。文章将蜜罐加密算法应用到个人电子钱包,以此来解决弱口令对于保护用户的银行卡账号及其密码的弱点问题。文章首先介绍蜜罐加密算法的基本思想;而后对该应用设计细粒度的消息空间以提供可信的引诱消息;首次引入机器学习的方法对蜜罐加密算法的安全性问题进行讨论。实验表明,蜜罐加密算法的安全性比现有基于口令加密算法的安全性更高,生成的引诱消息也足够难以区分。
中图分类号:
引用本文
郭亚军, 蒲东齐. 基于蜜罐加密算法的个人隐私数据保护[J]. 信息网络安全, 2019, 19(12): 38-46.
Yajun GUO, Dongqi PU. Privacy Data Protection Based on the Honey Encryption[J]. Netinfo Security, 2019, 19(12): 38-46.
| [1] | BONNEAU J.The Science of Guessing: Analyzing an Anonymized Corpus of 70 Million Passwords[C]//IEEE. 2012 IEEE Symposium on Security and Privacy, May 20-23, 2012, San Francisco, California, USA. New York: IEEE, 2012: 538-552. |
| [2] | KU Weichi, CHEN Shuaimin.Weaknesses and Improvements of an Efficient Password Based Remote User Authentication Scheme Using Smart Cards[J]. IEEE Transactions on Consumer Electronics, 2004, 50(1): 204-207. |
| [3] | JUELS A, RISTENPART T.Honey Encryption: Security Beyond the Brute-Force Bound[C]//Springer. 33rd Annual International Conference on the Theory and Applications of Cryptographic Techniques, May 11-15, 2014, Copenhagen, Denmark. Heidelberg: Springer, 2014: 293-310. |
| [4] | JUELS A, RIVEST R L.Honeywords: Making Password-Cracking Detectable[C]//ACM. Proceedings of the 2013 ACM SIGSAC Conference on Computer & Communications Security, November 04-08, 2013, Berlin, Germany. New York: ACM, 2013: 145-160. |
| [5] | ERGULER I.Achieving Flatness: Selecting the Honeywords from Existing User Passwords[J]. IEEE Transactions on Dependable and Secure Computing, 2015, 13(2): 284-295. |
| [6] | RAO S.Data and System Security with Failwords: U.S. Patent Application 11/039, 577[P].2006-7-20. |
| [7] | YOU Jianzhou, ZHANG Yueyang, LV Shichao, et al.Method of ICS Honeypot Identification Based on Packet-Sharding[J]. Journal of Cyber Security, 2019, 4(3):83-92. |
| 游建舟,张悦阳,吕世超,等. 基于数据包分片的工控蜜罐识别方法[J]. 信息安全学报,2019,4(3):83-92. | |
| [8] | BOJINOV H, BURSZTEIN E, BOYEN X, et al.Kamouflage: Loss-Resistant Password Management[C]// Springer. European Symposium on Research in Computer Security, September 20-22, 2010, Athens, Greece. Heidelberg: Springer, 2010: 286-302. |
| [9] | GENC Z A, KARDAŞ S, KIRAZ M S.Examination of a New Defense Mechanism: Honeywords[C]//Springer. IFIP International Conference on Information Security Theory and Practice, September 28-29, 2017, Heraklion, Crete, Greece. Heidelberg: Springer, 2017: 130-139. |
| [10] | YUILL J, ZAPPE M, DENNING D, et al.Honeyfiles: Deceptive Files for Intrusion Detection[C]//IEEE. Proceedings from the Fifth Annual IEEE SMC Information Assurance Workshop, June 10-11, 2004, West Point, NY, USA. New York: IEEE, 2004: 116-122. |
| [11] | VINAYAK P P, NAHALA M A.Avoiding Brute Force Attack in MANET Using Honey Encryption[J]. International Journal of Science and Research, 2015, 4(3): 83-85. |
| [12] | TYAGI N, WANG J, WEN K, et al. Honey Encryption Applications[EB/OL]. , 2019-4-30. |
| [13] | YIN Wei, ZHOU Hongjian, XING Guoqiang.Application of Honey Encryption Mechanism in Protection of Private Data[J]. Journal of Computer Applications, 2017, 37(12): 3406-3411. |
| 银伟,周红建,邢国强. 蜜罐加密技术在私密数据保护中的应用[J]. 计算机应用,2017,37(12):3406-3411. | |
| [14] | HUANG Z, AYDAY E, FELLAY J, et al.GenoGuard: Protecting Genomic Data Against Brute-Force Attacks[C]//IEEE. 2015 IEEE Symposium on Security and Privacy, May 17-21, 2015, San Jose, CA, USA. New York: IEEE, 2015: 447-462. |
| [15] | YOON J W, KIM H, JO H J, et al.Visual Honey Encryption: Application to Steganography[C]//ACM. Proceedings of the 3rd ACM Workshop on Information Hiding and Multimedia Security, June 17-19, 2015, Portland, Oregon, USA. New York: ACM, 2015: 65-74. |
| [16] | JAEGER J, RISTENPART T, TANG Q.Honey Encryption Beyond Message Recovery Security[C]//Springer. Annual International Conference on the Theory and Applications of Cryptographic Techniques, May 8-12, 2016, Vienna, Austria. Heidelberg: Springer, 2016: 758-788. |
| [17] | CORON J S, DODIS Y, MANDAL A, et al.A Domain Extender for the Ideal Cipher[C]//Springer. Theory of Cryptography Conference, February 9-11, 2010, Zurich, Switzerland. Heidelberg: Springer, 2010: 273-289. |
| [18] | NICK. PIN Number Analysis[EB/OL]. , 2019-4-30. |
| [19] | BELLARE M, RISTENPART T, TESSARO S.Multi-instance Security and Its Application to Password-based Cryptography[C]//Springer. Annual Cryptology Conference, August 19-23, 2012, Santa Barbara, CA, USA. Heidelberg: Springer, 2012: 312-329. |
| [1] | 赵志岩, 纪小默. 智能化网络安全威胁感知融合模型研究[J]. 信息网络安全, 2020, 20(4): 87-93. |
| [2] | 刘敏, 陈曙晖. 基于关联融合的VoLTE流量分析研究[J]. 信息网络安全, 2020, 20(4): 81-86. |
| [3] | 边玲玉, 张琳琳, 赵楷, 石飞. 基于LightGBM的以太坊恶意账户检测方法[J]. 信息网络安全, 2020, 20(4): 73-80. |
| [4] | 杜义峰, 郭渊博. 一种基于信任值的雾计算动态访问控制方法[J]. 信息网络安全, 2020, 20(4): 65-72. |
| [5] | 傅智宙, 王利明, 唐鼎, 张曙光. 基于同态加密的HBase二级密文索引方法研究[J]. 信息网络安全, 2020, 20(4): 55-64. |
| [6] | 王蓉, 马春光, 武朋. 基于联邦学习和卷积神经网络的入侵检测方法[J]. 信息网络安全, 2020, 20(4): 47-54. |
| [7] | 董晓丽, 商帅, 陈杰. 分组密码9轮Rijndael-192的不可能差分攻击[J]. 信息网络安全, 2020, 20(4): 40-46. |
| [8] | 郭春, 陈长青, 申国伟, 蒋朝惠. 一种基于可视化的勒索软件分类方法[J]. 信息网络安全, 2020, 20(4): 31-39. |
| [9] | 陈璐, 孙亚杰, 张立强, 陈云. 物联网环境下基于DICE的设备度量方案[J]. 信息网络安全, 2020, 20(4): 21-30. |
| [10] | 江金芳, 韩光洁. 无线传感器网络中信任管理机制研究综述[J]. 信息网络安全, 2020, 20(4): 12-20. |
| [11] | 刘建伟, 韩祎然, 刘斌, 余北缘. 5G网络切片安全模型研究[J]. 信息网络安全, 2020, 20(4): 1-11. |
| [12] | 刘鹏, 何倩, 刘汪洋, 程序. 支持撤销属性和外包解密的CP-ABE方案[J]. 信息网络安全, 2020, 20(3): 90-97. |
| [13] | 宋宇波, 樊明, 杨俊杰, 胡爱群. 一种基于拓扑分析的网络攻击流量分流和阻断方法[J]. 信息网络安全, 2020, 20(3): 9-17. |
| [14] | 王腾飞, 蔡满春, 芦天亮, 岳婷. 基于iTrace_v6的IPv6网络攻击溯源研究[J]. 信息网络安全, 2020, 20(3): 83-89. |
| [15] | 张艺, 刘红燕, 咸鹤群, 田呈亮. 基于授权记录的云存储加密数据去重方法[J]. 信息网络安全, 2020, 20(3): 75-82. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||