信息网络安全 ›› 2018, Vol. 18 ›› Issue (6): 77-84.doi: 10.3969/j.issn.1671-1122.2018.06.010
基于属性加密算法的可穿戴设备系统隐私保护方法研究
- 1. 中国电子科技集团公司第二十研究所,陕西西安 710068
2. 西安石油大学计算机学院, 陕西西安 710300
3. 西安电子科技大学通信工程学院,陕西西安 710071
-
收稿日期:2018-01-15出版日期:2018-06-15发布日期:2020-05-11 -
作者简介:作者简介:王乐(1988—),男,陕西,工程师,硕士,主要研究方向为数据链研发;杨哲荣(1996—),男,山西,本科,主要研究方向为可穿戴设备的隐私保护;刘容京(1983—),男,四川,硕士研究生,主要研究方向为可穿戴设备的隐私保护;王祥(1984—),男,山东,副教授,博士,主要研究方向为数字图像/视频内容保护等。
-
基金资助:国家自然科学基金[61373170];国家自然科学基金青年科学基金[61602358,61402352];陕西省重点研发计划[2014JQ8308]
A CP-ABE Privacy Preserving Method for Wearable Devices
Le WANG1( ), Zherong YANG2, Rongjing LIU3, Xiang WANG3
), Zherong YANG2, Rongjing LIU3, Xiang WANG3
- 1. China Electronic Technology Group Corporation No.20 Institute, Xi’an Shaanxi 710068, China;
2. School of Computer and Technology, Xi’an Shiyou University, Xi’an Shaanxi 710300, China;
3. School of Telecommunications Engineering, Xidian University, Xi’an Shaanxi 710071, China;
-
Received:2018-01-15Online:2018-06-15Published:2020-05-11
摘要:
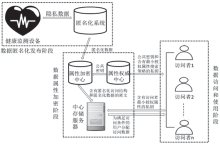
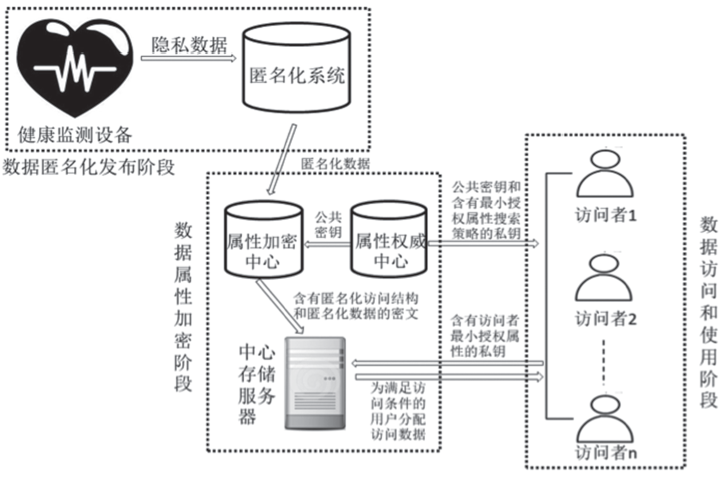
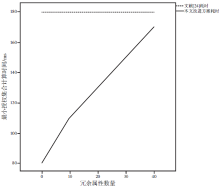
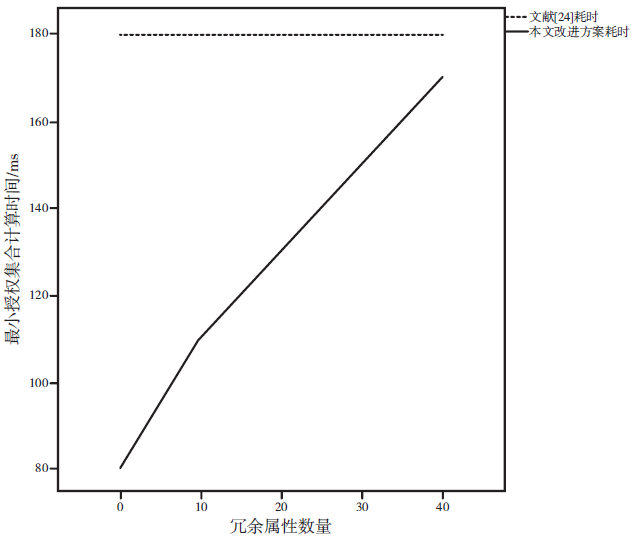
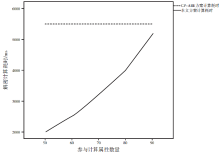
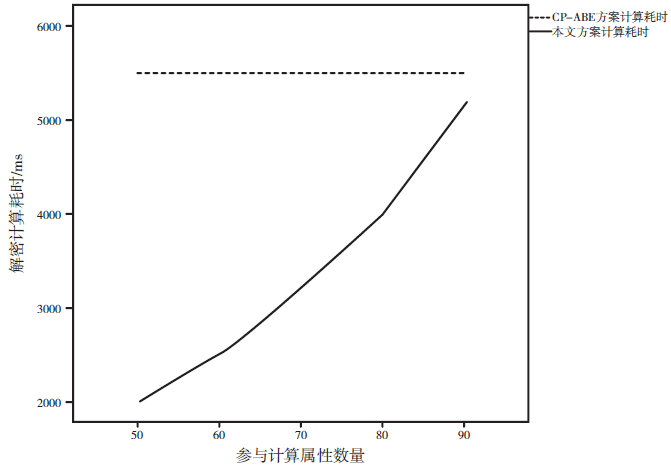
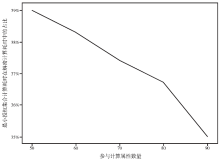
基于无线传感器网络的可穿戴健康监测设备正改变着传统的数据监测方式,其开放式的使用环境和高效便捷的数据传输网络为人们带来更加便捷的数据监测方式和海量监测数据,但是监测数据的再利用却给用户带来了担忧。文章在传统数据加密方法的基础上改善可穿戴健康监测系统的隐私保护效率,以传统的CP-ABE方案为基础,使用数据属性和用户属性对数据访问行为加以过滤,在减少密文大小、消除冗余属性、提高加解密效率等方面,进行了两点改进:1)在LSSS矩阵生成过程中只生成授权属性相关的行,剔除其他冗余属性,减少LSSS矩阵大小;2)取得只含有授权属性集的LSSS矩阵后,结合最小授权属性搜索策略寻找最小授权集合,提出一种匿名化算法与属性基加密相融合的隐私保护模型。实验证明,文章所提方案能够一定程度上抑制冗余属性参与加解密计算,对加解密计算效率有一定的提升,而且匿名化后的访问结构并不影响最终解密过程,能够有效保护用户隐私信息。
中图分类号:
引用本文
王乐, 杨哲荣, 刘容京, 王祥. 基于属性加密算法的可穿戴设备系统隐私保护方法研究[J]. 信息网络安全, 2018, 18(6): 77-84.
Le WANG, Zherong YANG, Rongjing LIU, Xiang WANG. A CP-ABE Privacy Preserving Method for Wearable Devices[J]. Netinfo Security, 2018, 18(6): 77-84.
| [1] | CAMPBELL A T, EISENMAN S B, LANE N D, et al.The Rise of People-Centric Sensing[J]. IEEE Internet Computing, 2008, 12(4): 12-21. |
| [2] | CAO Lei.Cloud Outsourcing Attribute Base Encryption for Hidden Structure in Mobile Medical Service [D]. Xi’an: Xidian University, 2015. |
| 曹磊. 移动医疗中隐藏访问结构的云外包属性基加密[D]. 西安: 西安电子科技大学, 2015. | |
| [3] | QIU Yue.Information Security Analysis in Wearable Devices[J]. Netinfo Security, 2016, 16(9): 79-83. |
| 裘玥. 智能可穿戴设备信息安全分析[J]. 信息网络安全, 2016,16(9):79-83. | |
| [4] | SWEENEY L.Uniqueness of Simple Demographics in the US Population[J]. Computers & Security, 2001, 30(2-3): 88-97. |
| [5] | SAMARATI P, SWEENEY L.Generalizing Data to Provide Anonymity when Disclosing Information[C]// ACM. Special Interest Group on Algorithms and Computation Theory, Proceedings of the 17th ACM Sigact-Sigmod-Sigart Symposiumon Principles of Database System, June1-3, 1998, Seattle, Washington, USA.New York: ACM, 1998:188. |
| [6] | ZHANG Dajun, LI Yunfa, ZHENG Zhou.The Mechanism of Data Resources Secure Sharing in Cloud Computing[J]. Netinfo Security, 2012, 12(8): 79-82. |
| 张大军, 李运发, 郑周. 云计算中数据资源的安全共享机制[J]. 信息网络安全, 2012,12(8):79-82. | |
| [7] | GATES C.Access Control Requirements for Web 2.0 Security and Privacy[C]// ACM. Workshop on Web 2.0 Security & Privacy, ACM Symposium on Information, Computer and Communications Security, August 23-25, 2007,Incheon, Korea. New York:ACM, 2007:27-42. |
| [8] | CARMINATI B, FERRARI E, HEATHERLY R.Semantic Web-based Social Network Access Control[J]. Computers & Security, 2011, 30(2): 108-115. |
| [9] | FONG P, ANWAR M, ZHAO Z.A Privacy Preservation Model for Facebook-Style Social Network Systems[J]. Computers & Security, 2009, 5789(12):303-320. |
| [10] | FONG P W L, SIAHAAN I. Relationship-based Access Control Policies and Their Policy Languages[C]// ACM. Special Interest Group on Security, Audit, and Control, ACM Symposium on Access Control MODELS and Technologies, June 15-17, 2011, Shanghai, China. New York: ACM, 2011: 51-60. |
| [11] | NIN J, TORRA V.Possibilistic Reasoning for Trust-Based Access Control Enforcement in Social Networks[C]// IEEE.International Conference on Fuzzy Systems, July 18-23, 2010, Barcelona, Spain. New York: IEEE, 2011: 1-6. |
| [12] | CRAMPTON J, SELLWOOD J.Inter-ReBAC: Inter-Operation of Relationship-Based Access Control Model Instances[C]// IFIP, International Conference on Data and Applications Security and Privacy, May 30 - June 1, 2016, Ghent, Belgium. Laxenburg: IFIP, 2016: 1-10. |
| [13] | LOU Jiapeng, ZHANG Shutian, ZHANG Yi, et al.Design and Implementation of Privacy Preserving System on the Internet[J]. Netinfo Security, 2013, 13(9): 35-40. |
| 娄嘉鹏, 张曙天, 张怡,等. 互联网安全隐私保护系统设计与实现[J]. 信息网络安全, 2013,13(9): 35-40. | |
| [14] | PARK J, SANDHU R, GHANTA S.RBAC on the Web by Secure Cookies[C]// IFIP. International Conference on Database Security: Research Advances in Database and Information Systems Security, May 21-24, Kluwer. Laxenburg: IFIP, 1999: 1-10. |
| [15] | PANG J, ZHANG Y.A New Access Control Scheme for Facebook-Style Social Networks[C]// IEEE, International Conference on Availability, Reliability and Security,September 8-12, 2014, University of Fribourg, Switzerland. New York: IEEE. 2014: 1-6. |
| [16] | BETHENCOURT J, SAHAI A, WATERS B.Ciphertext-policy attribute-based encryption[C]// IEEE, Symposium on Security and Privacy, May 20-23, 2007, Oakland, USA. New York: IEEE, 2007: 1-29. |
| [17] | GOYAL V, PANDEY O, SAHAI A, et al.Attribute-Based Encryption for Fine-grained Access Control of Encrypted Data[C]// ACM. Conference on Computer and Communications Security, October 30-November 3, 2006, Alexandria, USA. New York: ACM, 2006: 1-28. |
| [18] | ATTRAPADUNG N, IMAI H.Dual-policy Attribute Based Encryption[C]// Springer. International Conference on Applied Cryptography and Network Security, June 2-5, 2009, Paris, France. Berlin: Springer, 2009: 168-185. |
| [19] | LEWKO A B, OKAMOTO T, SAHAI A, et al.Fully Secure Functional Encryption: Attribute-Based Encryption and (Hierarchical) Inner Product Encryption[C]// Springer. Annual International Conference on the Theory and Applications of Cryptographic Techniques, May 30-June 3, French, Riviera. Berlin: Springer, 2010: 62-91. |
| [20] | BETHENCOURT J, SAHAI A, WATERS B.Ciphertext-Policy Attribute-Based Encryption[C] // IEEE. Symposium on Security and Privacy, May 20-23, 2007, Oakland, USA. New York: IEEE, 2007: 1-29. |
| [21] | XIAO L, LIU M.Linear Multi-secret Sharing Schemes[J]. Science in China Series F: Information Sciences, 2005, 48(1): 125-136. |
| [22] | NIKOV V, NIKOVA S.New Monotone Span Programs from Old[J]. Iacr Cryptology Eprint Archive, 2004,2(1):56-70. |
| [23] | LIAO Jingxue, CHEN Fuzhen, CHENG Jiujun, et al.Privacy Protection System for Innovative Service Platform of Community Internet of Things[J]. Netinfo Security, 2016, 16(12): 60-67. |
| 廖竞学, 陈福臻, 程久军,等. 面向社区物联网创新服务平台的隐私保护系统[J]. 信息网络安全, 2016,16(12):60-67. | |
| [24] | SHERIDAN D.The Optimality of a Fast CNF Conversion and Its Use with SAT[J]. Proc. of SAT, 2004, 4(3):32-47. |
| [1] | 唐春明, 林旭慧. 隐私保护集合交集计算协议[J]. 信息网络安全, 2020, 20(1): 9-15. |
| [2] | 汪金苗, 王国威, 王梅, 朱瑞瑾. 面向雾计算的隐私保护与访问控制方法[J]. 信息网络安全, 2019, 19(9): 41-45. |
| [3] | 王生玉, 汪金苗, 董清风, 朱瑞瑾. 基于属性加密技术研究综述[J]. 信息网络安全, 2019, 19(9): 76-80. |
| [4] | 郝文江, 林云. 互联网企业社会责任现状与启示研究[J]. 信息网络安全, 2019, 19(9): 130-133. |
| [5] | 周权, 许舒美, 杨宁滨. 一种基于ABGS的智能电网隐私保护方案[J]. 信息网络安全, 2019, 19(7): 25-30. |
| [6] | 刘建华, 郑晓坤, 郑东, 敖章衡. 基于属性加密且支持密文检索的安全云存储系统[J]. 信息网络安全, 2019, 19(7): 50-58. |
| [7] | 李怡霖, 闫峥, 谢皓萌. 车载自组织网络的隐私保护综述[J]. 信息网络安全, 2019, 19(4): 63-72. |
| [8] | 傅彦铭, 李振铎. 基于拉普拉斯机制的差分隐私保护k-means++聚类算法研究[J]. 信息网络安全, 2019, 19(2): 43-52. |
| [9] | 赵志岩, 吴剑, 康凯. 一种兼顾业务数据安全的隐私保护世系发布方法[J]. 信息网络安全, 2019, 19(12): 29-37. |
| [10] | 胡荣磊, 何艳琼, 曾萍, 范晓红. 一种大数据环境下医疗隐私保护方案设计与实现[J]. 信息网络安全, 2018, 18(9): 48-54. |
| [11] | 李佩丽, 徐海霞, 马添军, 穆永恒. 区块链技术在网络互助中的应用及用户隐私保护[J]. 信息网络安全, 2018, 18(9): 60-65. |
| [12] | 马蓉, 陈秀华, 刘慧, 熊金波. 移动群智感知中用户隐私度量与隐私保护研究[J]. 信息网络安全, 2018, 18(8): 64-72. |
| [13] | 赖成喆, 王文娟. 面向车队的安全且具备隐私保护的移动性管理框架[J]. 信息网络安全, 2018, 18(7): 36-46. |
| [14] | 张磊, 王斌, 于莉莉. 基于马尔可夫预测的连续查询隐私保护方法[J]. 信息网络安全, 2018, 18(5): 12-12. |
| [15] | 张磊, 王斌, 于莉莉. 基于Hash函数的属性泛化隐私保护方案[J]. 信息网络安全, 2018, 18(3): 14-25. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||