信息网络安全 ›› 2018, Vol. 18 ›› Issue (5): 12-12.doi: 10.3969/j.issn.1671-1122.2018.05.002
基于马尔可夫预测的连续查询隐私保护方法
- 1. 哈尔滨工程大学计算机科学与技术学院,黑龙江哈尔滨 150001
2. 佳木斯大学信息电子技术学院,黑龙江佳木斯 154007
-
收稿日期:2017-12-22出版日期:2018-05-15发布日期:2020-05-11 -
作者简介:作者简介:张磊(1982—),男,黑龙江,博士研究生,主要研究方向为隐私保护;王斌(1979—),男,黑龙江,博士研究生,主要研究方向为机器学习、隐私保护;于莉莉(1975—),女,黑龙江,副教授,硕士,主要研究方向为信息安全、网络安全。
-
基金资助:黑龙江省自然科学基金[F2015022];黑龙江省普通本科高等学校青年创新人才培养计划[UNPYSCT-2017149,UNPYSCT-2017175]
A Markov Prediction-based Algorithm for Continuous Query Privacy Protection
Lei ZHANG1,2, Bin WANG1,2, Lili YU2( )
)
- 1. College of Computer Science and Technology, Harbin Engineering University, Harbin Heilongjiang 150001, China
2. College of Information Science and Electronic Technology, Jiamusi University, Jiamusi Heilongjiang 154007, China
-
Received:2017-12-22Online:2018-05-15Published:2020-05-11
摘要:
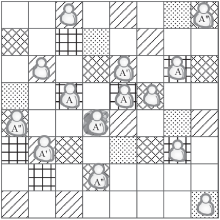
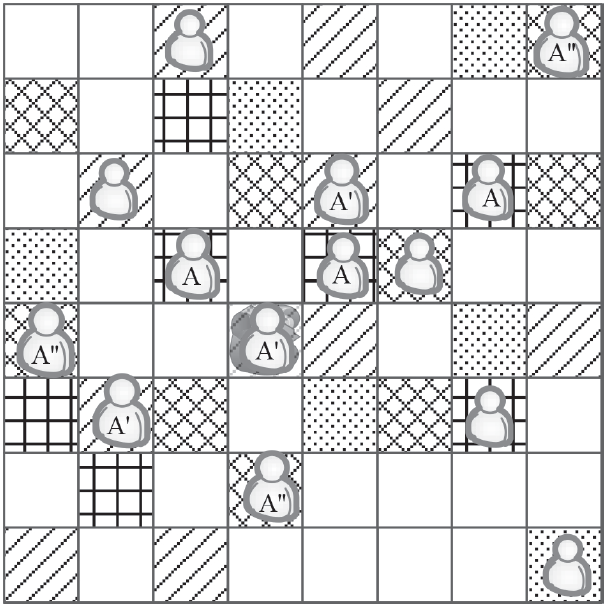
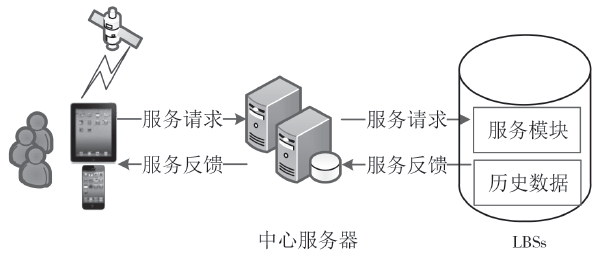
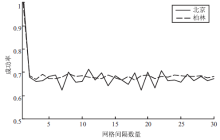
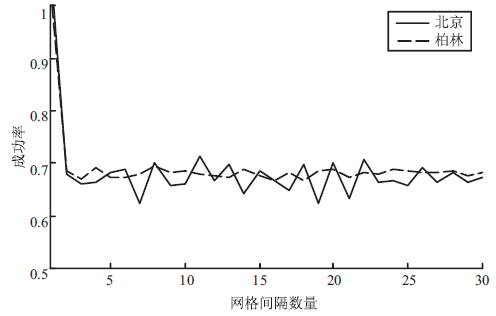
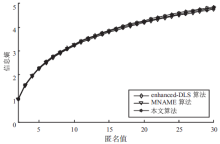
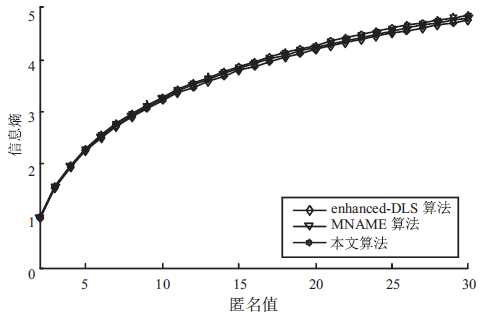
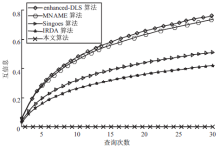
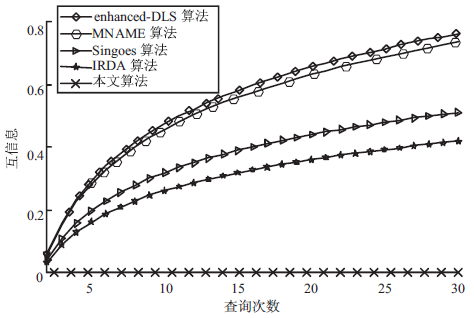
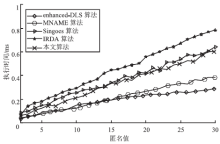
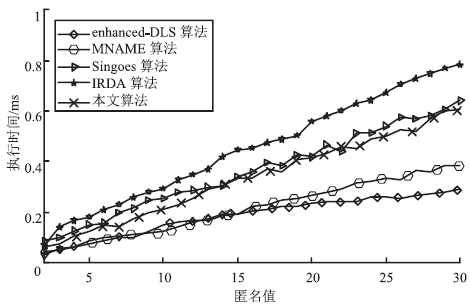
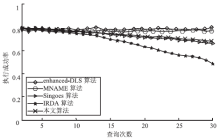
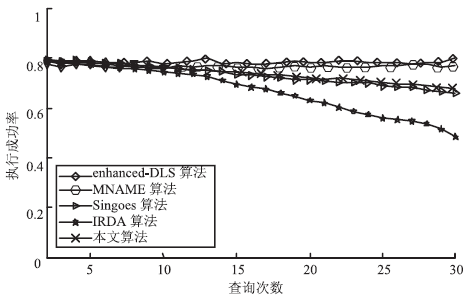
针对基于位置服务中攻击者可通过获得各匿名位置的查询概率进而识别申请者的潜在位置的问题,当前已有学者提出通过在查询过程中提交具有相同查询概率的方法进行隐私保护。这些方法虽然在快照查询下一般能够提供较好的隐私保护服务,但在连续查询时大多存在一定的局限性,且当具有相似查询概率的连续位置存在不可到达情况时,攻击者识别出用户真实位置轨迹的概率将会无限扩大。针对这一问题,文章基于马尔可夫预测提出了既能够在连续查询过程中提供查询概率泛化服务,又能够保障具有查询概率泛化能力的位置具有连续可到达性的隐私保护方法。通过该方法可实现在查询概率攻击和不可到达性分析攻击下的连续查询过程中的位置隐私保护。最后,为验证算法的隐私保护能力和执行效率,文章通过安全性分析和实验进一步加以证实,并给出了详细的验证过程和实验结果分析。
中图分类号:
引用本文
张磊, 王斌, 于莉莉. 基于马尔可夫预测的连续查询隐私保护方法[J]. 信息网络安全, 2018, 18(5): 12-12.
Lei ZHANG, Bin WANG, Lili YU. A Markov Prediction-based Algorithm for Continuous Query Privacy Protection[J]. Netinfo Security, 2018, 18(5): 12-12.
| [1] | NIU Ben, LI Qinghua, ZHU Xiaoyan, et al.Achieving k-anonymity in Privacy-aware Location-based Services[J]. Journal of Graph Algorithms & Applications, 2014, 20(2): 363-410. |
| [2] | NIU Ben, LI Qinghua, ZHU Xiaoyan, et al.Enhancing Privacy through Caching in Location-based Services[C]//IEEE. 2015 IEEE Conference on Computer Communications, April 26-May 1, 2015, Kowloon, Hong Kong, China. New Jersey: IEEE, 2015: 1017-1025. |
| [3] | SUN Yanming, CHEN Min, HU Long, et al. ASA: against Statistical Attacks for Privacy-aware Users in Location Based Service[EB/OL]. ,2017-11-20. |
| [4] | XU Yan.Research on Network Link Prediction Based on Data Mining[J]. Netinfo Security, 2017(6): 30-34. |
| 徐燕. 基于数据挖掘的网络链接预测研究[J]. 信息网络安全,2017(6):30-34. | |
| [5] | GRUTESER M, GRUNWALD D.Anonymous Usage of Location-based Services through Spatial and Temporal Cloaking[C]//ACM. 1st International Conference on Mobile Systems, Applications and Services, May 5-8, 2003, San Francisco, California. New York: ACM, 2003: 31-42. |
| [6] | GEDIK B, LIU Ling.Location Privacy in Mobile Systems: a Personalized Anonymization Model[C]//IEEE. 25th IEEE International Conference on Distributed Computing Systems, June 6-10, 2005, Columbus, OH, USA. New Jersey: IEEE, 2005: 620-629. |
| [7] | TALUKDER N, AHAMED S I.Preventing Multi-query Attack in Location-based Services[C]//ACM. 3rd ACM Conference on Wireless Network Security, March 22-24, 2010, Hoboken, New Jersey, USA. ACM: New York: 2010, 25-35. |
| [8] | XUE Jiao, LIU Xiangyu, YANG Xiaochun, et al.A Location Privacy Preserving Approach on Road Network[J]. Chinese Journal of Computers, 2011, 34(5): 865-878. |
| 薛姣,刘向宇,杨晓春,等. 一种面向公路网络的位置隐私保护方法[J]. 计算机学报,2011,34(5):865-878. | |
| [9] | SCHLEGEL R, CHOW C Y, HUANG Q, et al.User-defined Privacy Grid System for Continuous Location-based Services[J]. IEEE Transactions on Mobile Computing, 2015, 14(10): 2158-2172. |
| [10] | CHE Yanzhe, HE Qinming, HONG Xiaoyan, et al.X-Region: a Framework for Location Privacy Preservation in Mobile Peer-to-Peer Networks[J]. International Journal of Communication Systems, 2015, 28(1): 167-186. |
| [11] | YIU M L, JENSEN C S, HUANG Xuegang, et al.SpaceTwist: Managing the Trade-offs among Location Privacy, Query Performance, and Query Accuracy in Mobile Services[C]//IEEE. IEEE 24th International Conference on Data Engineering, April 7-12, 2008, Cancun, Mexico. New Jersey: IEEE, 2008: 366-375. |
| [12] | YIU M L, JENSEN C S, MOLLER J, et al.Design and Analysis of a Ranking Approach to Private Location-based Services[J]. ACM Transactions on Database Systems, 2011, 36(2): 475-486. |
| [13] | MA Chunguang, ZHOU Changli, YANG Songtao.A Voronoi-based Location Privacy-preserving Method for Continuous Query in LBS[J]. International Journal of Distributed Sensor Networks, 2015, 11(3): 1-17. |
| [14] | PENG Tao, LIU Qin, WANG Guojun.Enhanced Location Privacy Preserving Scheme in Location-based Services[J]. IEEE Systems Journal, 2017, 11(1): 219-230. |
| [15] | BAMBA B, LIU Ling, PESTI P, et al.Supporting Anonymous Location Queries in Mobile Environments with Privacygrid[C]//ACM. 17th International Conference on World Wide Web, April 21-25, 2008, Beijing, China. New York: ACM, 2008: 237-246. |
| [16] | XIAO Zheng, XU Jianliang, MENG Xiaofeng. p-Sensitivity: a Semantic Privacy-protection Model for Location-based Services[C]//IEEE. 9th International Conference on Mobile Data Management Workshops, April 27-30, 2008, Beijing, China. New Jersey: IEEE, 2008: 47-54. |
| [17] | LIU Fuyu, HUA K A, CAI Ying.Query l-diversity in Location-based Services[C]//IEEE. 10th International Conference on Mobile Data Management: Systems, Services and Middleware, May 18-20, 2009, Taiwan, China. New Jersey: IEEE, 2009: 436-442. |
| [18] | CHOW C Y, MOKBEL M F, LIU Xuan.A Peer-to-Peer Spatial Cloaking Algorithm for Anonymous Location-based Service[C]//ACM. 14th Annual ACM International Symposium on Advances in Geographic Information Systems, November 10-11, 2006, Arlington, Virginia, USA. New York: ACM, 2006: 171-178. |
| [19] | MA Chunguang, ZHANG Lei, YANG Songtao.Review on Location Trajectory Privacy Protection[J]. Netinfo Security, 2015(10): 24-31. |
| 马春光,张磊,杨松涛. 位置轨迹隐私保护综述[J]. 信息网络安全,2015(10):24-31. | |
| [20] | REBOLLO-MONEDERO D, FORNE J, DOMINGO-FERRER J.Query Profile Obfuscation by Means of Optimal Query Exchange between Users[J]. IEEE Transactions on Dependable and Secure Computing, 2012, 9(5): 641-654. |
| [21] | NIU Ben, ZHU Xiaoyan, LI Qinghua, et al. A Novel Attack to Spatial Cloaking Schemes in Location-based Services[EB/OL]. , 2017-11-20. |
| [22] | ZHANG Haichuan, ZHAO Zemao, TIAN Yujie, et al.Research on Optimization Selection of Personalized Space Anonymous Algorithm[J]. Netinfo Security, 2015(3): 23-27. |
| 张海川,赵泽茂,田玉杰,等. 基于个性化的空间匿名算法最优化选择研究[J]. 信息网络安全,2015(3):23-27. | |
| [23] | MA Chunguang, ZHANG Lei, YANG Songtao, et al.Achieve Personalized Anonymity through Query Blocks Exchanging[J]. China Communications, 2016, 13(11): 106-118. |
| [24] | MA Chunguang, ZHANG Lei, YANG Songtao, et al. Hiding Yourself Behind Collaborative Users When Using Continuous Location-based Services[EB/OL]. , 2017-11-20. |
| [25] | HWANG R H, HSUEH Y L, CHUNG H W.A Novel Time-obfuscated Algorithm for Trajectory Privacy Protection[J]. IEEE Transactions on Services Computing, 2014, 7(2): 126-139. |
| [26] | ZHANG Lei, MA Chunguang, YANG Songtao, et al.Location Privacy Protection Model and Algorithm Based on Profiles Generalization[J]. Systems Engineering and Electronics, 2016, 38(12): 2894-2900. |
| 张磊,马春光,杨松涛,等. 基于轮廓泛化的位置隐私保护模型及方法[J]. 系统工程与电子技术,2016,38(12):2894-2900. | |
| [27] | WANG Yong, GAO Shimeng, NIE Xiao, et al.A LBSs Cloaking Algorithm Based on Velocity Dynamic Variation[J]. Netinfo Security, 2015(4): 28-35. |
| 王勇,高诗梦,聂肖,等. 基于速度动态差异的位置服务匿名算法[J]. 信息网络安全,2015(4):28-35. | |
| [28] | ZHANG Lei, MA Chunguang, YANG Songtao.Location Association Similar Based Anonymus Algorithm[J]. China Sciencepaper, 2016, 11(2): 197-201, 213. |
| 张磊,马春光,杨松涛. 基于位置关联相似性的匿名算法[J]. 中国科技论文,2016,11(2):197-201,213. | |
| [29] | ZHANG Lei, MA Chunguang, YANG Songtao, et al.CP-ABE Based Users Collaborative Privacy Protection Scheme for Continuous Query[J]. Journal on Communications, 2017, 38(9): 76-85. |
| 张磊,马春光,杨松涛,等. 基于属性基加密的用户协作连续查询隐私保护策略[J]. 通信学报,2017,38(9):76-85. | |
| [30] | ANDRÉS M E, BORDENABE N E, CHATZIKOKOLAKIS K, et al. Geo-indistinguishability: Differential Privacy for Location-based Systems[C]//ACM. 2013 ACM SIGSAC Conference on Computer & Communications Security, ACM, November 4-8, 2013, Berlin, Germany. New York: ACM, 2013: 901-914. |
| [31] | BORDENABE N E, CHATZIKOKOLAKIS K, PALAMIDESSI C.Optimal Geo-indistinguishable Mechanisms for Location Privacy[C]//ACM. 2014 ACM SIGSAC Conference on Computer and Communications Security, November 3-7, 2014, Scottsdale, Arizona, USA. New York: ACM, 2014: 251-262. |
| [32] | WU Shasha, XIONG Jinbo, YE Guohua, et al.Research on Location Privacy Protection Based on Dummy Locations in Mobile Internet Environment[J]. Netinfo Security, 2016(10): 54-59. |
| 吴莎莎, 熊金波,叶帼华,等. 移动互联网环境下基于假位置的位置隐私保护研究[J]. 信息网络安全,2016(10):54-59. |
| [1] | 唐春明, 林旭慧. 隐私保护集合交集计算协议[J]. 信息网络安全, 2020, 20(1): 9-15. |
| [2] | 汪金苗, 王国威, 王梅, 朱瑞瑾. 面向雾计算的隐私保护与访问控制方法[J]. 信息网络安全, 2019, 19(9): 41-45. |
| [3] | 郝文江, 林云. 互联网企业社会责任现状与启示研究[J]. 信息网络安全, 2019, 19(9): 130-133. |
| [4] | 周权, 许舒美, 杨宁滨. 一种基于ABGS的智能电网隐私保护方案[J]. 信息网络安全, 2019, 19(7): 25-30. |
| [5] | 李怡霖, 闫峥, 谢皓萌. 车载自组织网络的隐私保护综述[J]. 信息网络安全, 2019, 19(4): 63-72. |
| [6] | 傅彦铭, 李振铎. 基于拉普拉斯机制的差分隐私保护k-means++聚类算法研究[J]. 信息网络安全, 2019, 19(2): 43-52. |
| [7] | 赵志岩, 吴剑, 康凯. 一种兼顾业务数据安全的隐私保护世系发布方法[J]. 信息网络安全, 2019, 19(12): 29-37. |
| [8] | 胡荣磊, 何艳琼, 曾萍, 范晓红. 一种大数据环境下医疗隐私保护方案设计与实现[J]. 信息网络安全, 2018, 18(9): 48-54. |
| [9] | 李佩丽, 徐海霞, 马添军, 穆永恒. 区块链技术在网络互助中的应用及用户隐私保护[J]. 信息网络安全, 2018, 18(9): 60-65. |
| [10] | 马蓉, 陈秀华, 刘慧, 熊金波. 移动群智感知中用户隐私度量与隐私保护研究[J]. 信息网络安全, 2018, 18(8): 64-72. |
| [11] | 赖成喆, 王文娟. 面向车队的安全且具备隐私保护的移动性管理框架[J]. 信息网络安全, 2018, 18(7): 36-46. |
| [12] | 王乐, 杨哲荣, 刘容京, 王祥. 基于属性加密算法的可穿戴设备系统隐私保护方法研究[J]. 信息网络安全, 2018, 18(6): 77-84. |
| [13] | 张磊, 王斌, 于莉莉. 基于Hash函数的属性泛化隐私保护方案[J]. 信息网络安全, 2018, 18(3): 14-25. |
| [14] | 李梁, 张应辉, 邓恺鑫, 张甜甜. 5G智能电网中具有隐私保护的电力注入系统[J]. 信息网络安全, 2018, 18(12): 87-92. |
| [15] | 赵娜, 龙慧, 苏金树. 一种适用于物联网环境的匿名认证与隐私保护方案[J]. 信息网络安全, 2018, 18(11): 1-7. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||