信息网络安全 ›› 2018, Vol. 18 ›› Issue (3): 14-25.doi: 10.3969/j.issn.1671-1122.2018.03.003
基于Hash函数的属性泛化隐私保护方案
- 1. 哈尔滨工程大学计算机科学与技术学院,黑龙江哈尔滨 150001
2. 佳木斯大学信息电子技术学院,黑龙江佳木斯 154007
-
收稿日期:2017-12-22出版日期:2018-03-15发布日期:2020-05-11 -
作者简介:作者简介:张磊(1982—),男,黑龙江,博士研究生,主要研究方向为隐私保护;王斌(1979—),男,黑龙江,博士研究生,主要研究方向为机器学习、隐私保护;于莉莉(1975—),女,黑龙江,副教授,硕士,主要研究方向为信息安全、网络安全。
-
基金资助:黑龙江省自然科学基金[F2015022];黑龙江省普通本科高等学校青年创新人才培养计划[UNPYSCT-2017149,UNPYSCT-2017175]
A Hash Function-based Attribute Generalization Privacy Protection Scheme
Lei ZHANG1,2, Bin WANG1,2, Lili YU2( )
)
- 1. College of Computer Science and Technology, Harbin Engineering University, Harbin Heilongjiang 150001, China
2. College of Information Science and Electronic Technology, Jiamusi University, Jiamusi Heilongjiang 154007, China
-
Received:2017-12-22Online:2018-03-15Published:2020-05-11
摘要:
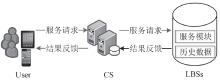
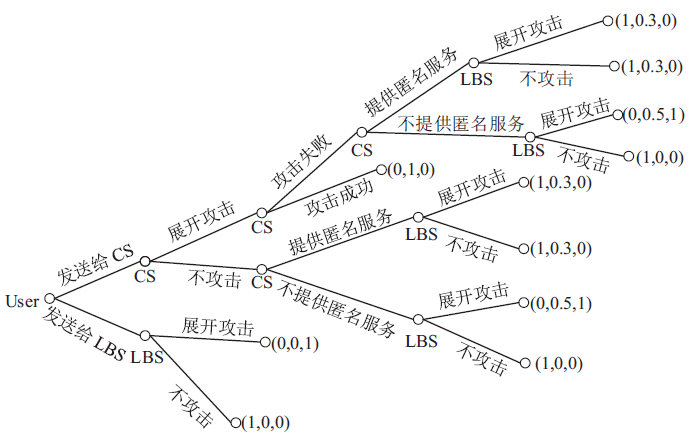
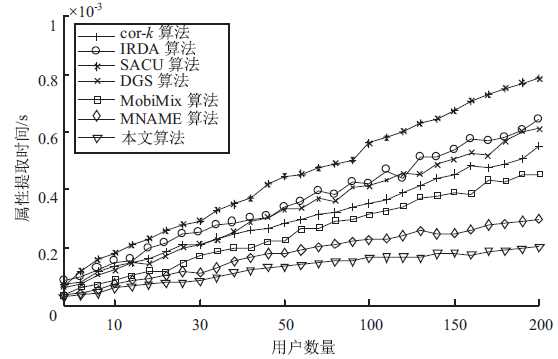
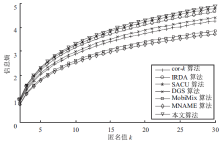
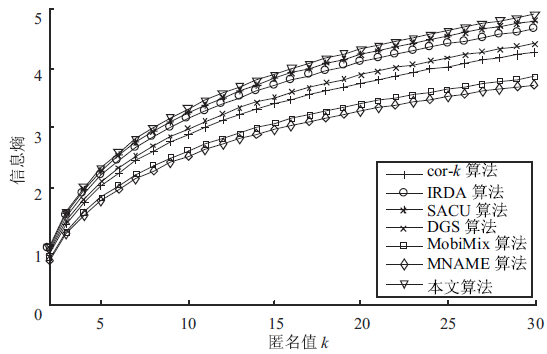
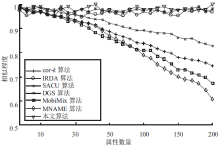
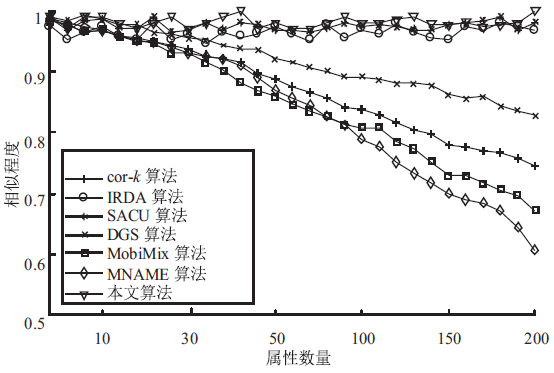
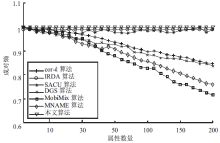
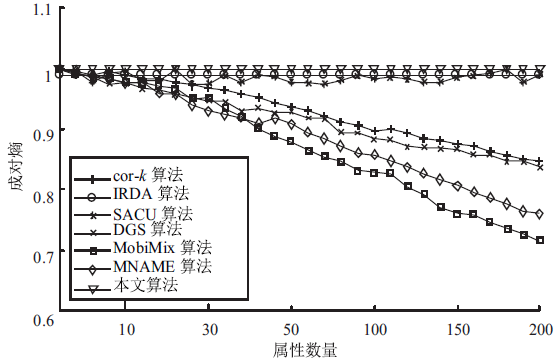
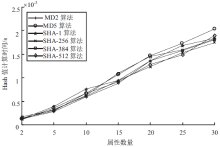
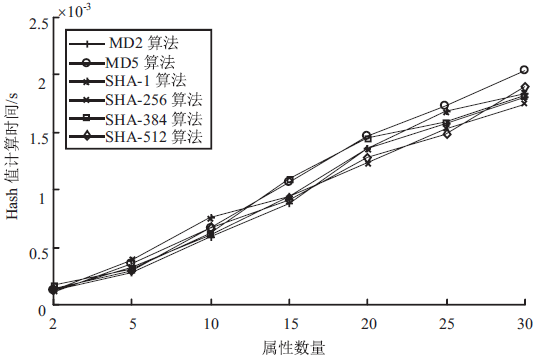
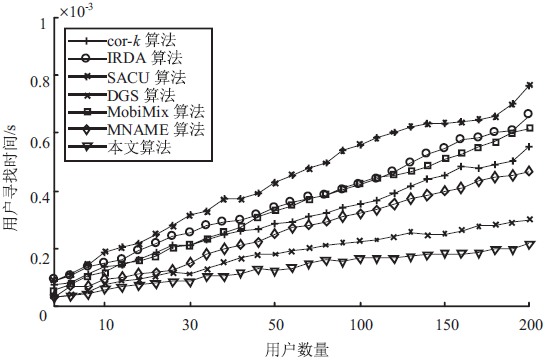
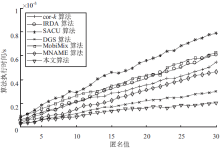
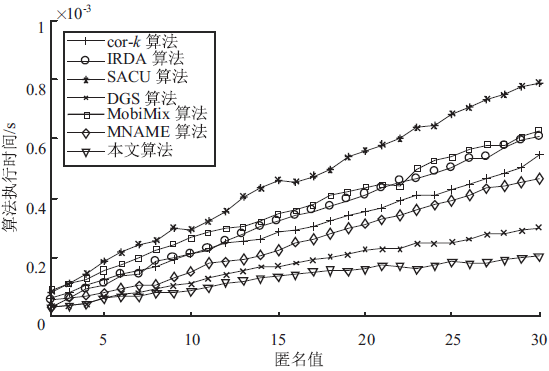
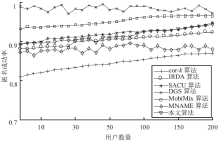
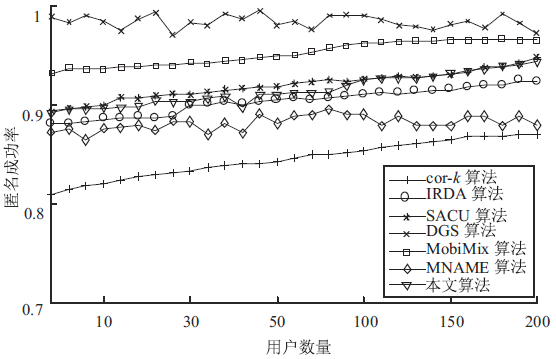
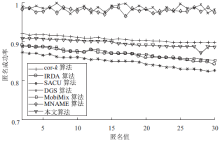
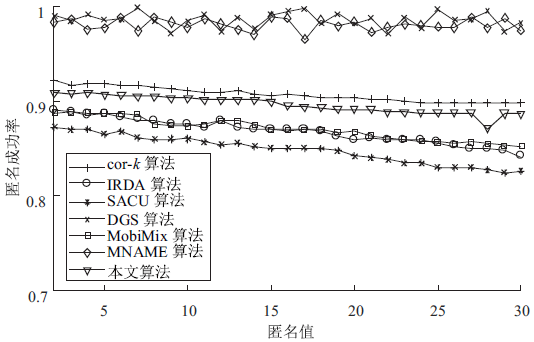
针对用户连续查询过程中属性可被关联并获得位置隐私的问题,文章基于属性泛化要求提出了一种基于Hash函数的属性泛化方法。该方法通过由属性转化的Hash值比较寻找具有相同属性的匿名用户,一方面防止具有攻击特性的中心服务器获得用户发送的隐私信息;另一方面通过这种Hash比较简化了相似属性的寻找过程,提高了算法的执行效率。同时,为了证明中心服务器具有潜在的攻击特性,利用博弈树量化的方式证明了中心服务器的不可靠性。最后,通过安全性分析和实验验证,并将文章提出的方法与其他同类算法进行比较,进一步证明了文中算法在隐私保护能力和算法执行效率方面的优势。
中图分类号:
引用本文
张磊, 王斌, 于莉莉. 基于Hash函数的属性泛化隐私保护方案[J]. 信息网络安全, 2018, 18(3): 14-25.
Lei ZHANG, Bin WANG, Lili YU. A Hash Function-based Attribute Generalization Privacy Protection Scheme[J]. Netinfo Security, 2018, 18(3): 14-25.
使用本文
| [1] | GRUTESER M, GRUNWALD D.Anonymous usage of location-based services through spatial and temporal cloaking[C]//ACM. 1st International Conference on Mobile Systems, Applications and Services, May 5-8, 2003, San Francisco, California. New York: ACM, 2003: 31-42. |
| [2] | LIU Fuyu L, HUA K A, CAI Ying.Query l-diversity in Location-based Services[C]//IEEE. 10th International Conference on Mobile Data Management: Systems, Services and Middleware, May 18-20, 2009, Taipei, China. New Jersey: IEEE, 2009: 436-442. |
| [3] | XIAO Zhen, XU Jianliang, MENG Xiaofeng. p-Sensitivity: A Semantic Privacy-protection Model for Location-based Services[C]//IEEE. 9th International Conference on Mobile Data Management Workshops, April 27-30, 2008, Beijing, China. New Jersey: IEEE, 2008: 47-54. |
| [4] | GHINITA G, KALNIS P, KHOSHGOZARAN A, et al.Private Queries in Location Based Services: Anonymizers are not Necessary[C]//ACM. 2008 ACM SIGMOD International Conference on Management of Data, June 10-12, 2008, Vancouver, Canada. New York: ACM, 2008: 121-132. |
| [5] | CHOW C Y, MOKBEL M F, LIU Xuan.A Peer-to-Peer Spatial Cloaking Algorithm for Anonymous Location-based Service[C]//ACM. 14th Annual ACM International Symposium on Advances in Geographic Information Systems, November 10-11, 2006, Arlington, Virginia, USA. New York: ACM, 2006: 171-178. |
| [6] | SCHLEGEL R, CHOW C Y, HUANG Qiong, et al.User-defined Privacy Grid System for Continuous Location-based Services[J]. IEEE Transactions on Mobile Computing, 2015, 14(10): 2158-2172. |
| [7] | NIU Ben, ZHU Xioayan, LI Qinghua, et al.A Novel Attack to Spatial Cloaking Schemes in Location-based Services[J]. Future Generation Computer Systems, 2015, 49(C): 125-132. |
| [8] | MA Chunguang, ZHANG Lei, YANG Songtao, et al.Achieve Personalized Anonymity through Query Blocks Exchanging[J]. China Communications, 2016, 13(11): 106-118. |
| [9] | SUN Yanming, CHEN Min, HU Long, et al. ASA: Against Statistical Attacks for Privacy-aware users in Location Based Service[EB/OL]. , 2017-10-12. |
| [10] | 马春光,张磊,杨松涛. 位置轨迹隐私保护综述[J]. 信息网络安全,2015(10):24-31. |
| [11] | PALANISAMY B, LIU Ling, LEE K, et al.Anonymizing Continuous Queries with Delay-tolerant Mix-zones over Road Networks[J]. Distributed and Parallel Databases, 2014, 32(1): 91-118. |
| [12] | HWANG R H, HSUEH Y L, CHUNG H W.A Novel Time-obfuscated Algorithm for Trajectory Privacy Protection[J]. IEEE Transactions on Services Computing, 2014, 7(2): 126-139. |
| [13] | ZEBERGA K, JIN R, CHO H J, et al. A Safe-region Approach to a Moving k-RNN Queries in a Directed Road Network[EB/OL]. , 2016-11-25. |
| [14] | 肖剑川,许力,叶阿勇,等. 基于Voronoi图的路网轨迹隐私保护研究[J]. 信息网络安全,2016(6):15-21. |
| [15] | 张磊,马春光,杨松涛,等. 基于轮廓泛化的位置隐私保护模型及方法[J]. 系统工程与电子技术,2016,38(12):2894-2900. |
| [16] | 王勇,高诗梦,聂肖,等. 基于速度动态差异的位置服务匿名算法[J]. 信息网络安全,2015(4):28-35. |
| [17] | 张磊,马春光,杨松涛,等. 关联概率不可区分的位置隐私保护方法[J]. 通信学报,2017,38(8):37-49. |
| [18] | 张磊,马春光,杨松涛,等. 基于属性基加密的用户协作连续查询隐私保护策略[J]. 通信学报,2017,38(9):76-85. |
| [19] | ZHANG Lei, LI Jing, YANG Songtao, et al.Privacy Preserving in Cloud Environment for Obstructed Shortest Path Query[J]. Wireless Personal Communications, 2017, 96(2): 2305-2322. |
| [20] | 周凯,彭长根,何建琼,等. 可证明安全的LBS中连续查询的轨迹隐私保护方案[J]. 信息网络安全,2017(1):43-47. |
| [21] | 张磊,马春光,杨松涛. 基于位置关联相似性的匿名算法[J]. 中国科技论文,2016,11(2):197-201. |
| [22] | PALANISAMY B, LIU Ling.Attack-Resilient Mix-zones over Road Networks: Architecture and Algorithms[J]. IEEE Transactions on Mobile Computing, 2015, 14(3): 495-508. |
| [1] | 唐春明, 林旭慧. 隐私保护集合交集计算协议[J]. 信息网络安全, 2020, 20(1): 9-15. |
| [2] | 汪金苗, 王国威, 王梅, 朱瑞瑾. 面向雾计算的隐私保护与访问控制方法[J]. 信息网络安全, 2019, 19(9): 41-45. |
| [3] | 郝文江, 林云. 互联网企业社会责任现状与启示研究[J]. 信息网络安全, 2019, 19(9): 130-133. |
| [4] | 周权, 许舒美, 杨宁滨. 一种基于ABGS的智能电网隐私保护方案[J]. 信息网络安全, 2019, 19(7): 25-30. |
| [5] | 李怡霖, 闫峥, 谢皓萌. 车载自组织网络的隐私保护综述[J]. 信息网络安全, 2019, 19(4): 63-72. |
| [6] | 傅彦铭, 李振铎. 基于拉普拉斯机制的差分隐私保护k-means++聚类算法研究[J]. 信息网络安全, 2019, 19(2): 43-52. |
| [7] | 赵志岩, 吴剑, 康凯. 一种兼顾业务数据安全的隐私保护世系发布方法[J]. 信息网络安全, 2019, 19(12): 29-37. |
| [8] | 胡荣磊, 何艳琼, 曾萍, 范晓红. 一种大数据环境下医疗隐私保护方案设计与实现[J]. 信息网络安全, 2018, 18(9): 48-54. |
| [9] | 李佩丽, 徐海霞, 马添军, 穆永恒. 区块链技术在网络互助中的应用及用户隐私保护[J]. 信息网络安全, 2018, 18(9): 60-65. |
| [10] | 马蓉, 陈秀华, 刘慧, 熊金波. 移动群智感知中用户隐私度量与隐私保护研究[J]. 信息网络安全, 2018, 18(8): 64-72. |
| [11] | 赖成喆, 王文娟. 面向车队的安全且具备隐私保护的移动性管理框架[J]. 信息网络安全, 2018, 18(7): 36-46. |
| [12] | 王乐, 杨哲荣, 刘容京, 王祥. 基于属性加密算法的可穿戴设备系统隐私保护方法研究[J]. 信息网络安全, 2018, 18(6): 77-84. |
| [13] | 张磊, 王斌, 于莉莉. 基于马尔可夫预测的连续查询隐私保护方法[J]. 信息网络安全, 2018, 0(5): 12-12. |
| [14] | 李梁, 张应辉, 邓恺鑫, 张甜甜. 5G智能电网中具有隐私保护的电力注入系统[J]. 信息网络安全, 2018, 18(12): 87-92. |
| [15] | 赵娜, 龙慧, 苏金树. 一种适用于物联网环境的匿名认证与隐私保护方案[J]. 信息网络安全, 2018, 18(11): 1-7. |
| 阅读次数 | ||||||||||||||||||||||||||||||||||||||||||||||||||
|
全文 180
|
|
|||||||||||||||||||||||||||||||||||||||||||||||||
|
摘要 473
|
|
|||||||||||||||||||||||||||||||||||||||||||||||||