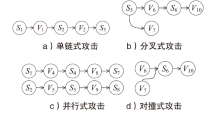
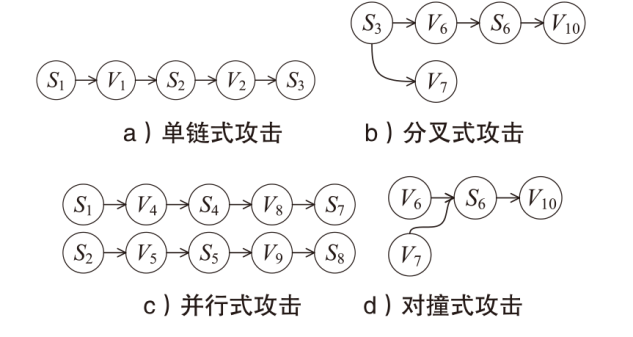
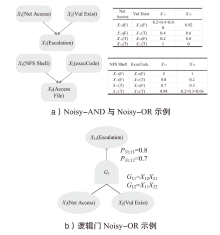
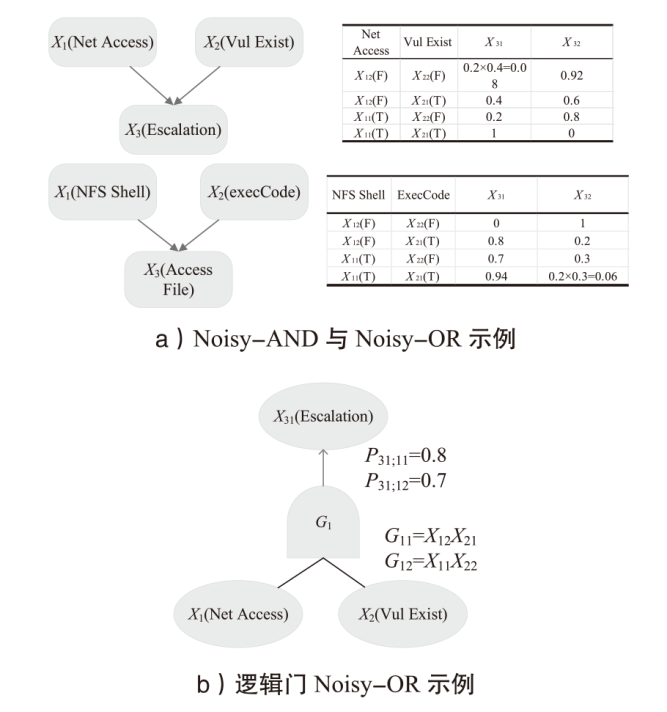
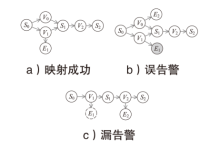
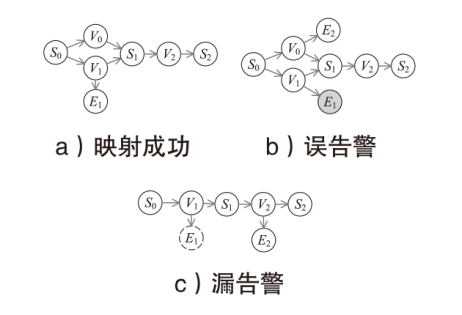
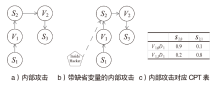
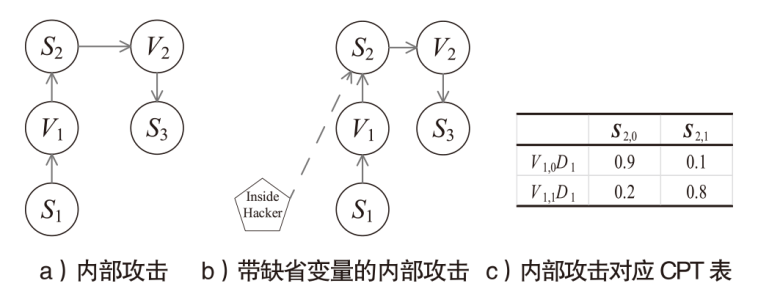
信息网络安全 ›› 2025, Vol. 25 ›› Issue (5): 778-793.doi: 10.3969/j.issn.1671-1122.2025.05.010
不确定性网络攻击场景下的多状态因果表示与推理模型
- 中国传媒大学计算机与网络空间安全学院,北京 100024
-
收稿日期:2024-12-30出版日期:2025-05-10发布日期:2025-06-10 -
通讯作者:董春玲dongchunling@cuc.edu.cn -
作者简介:董春玲(1979—),女,山东,教授,博士,CCF会员,主要研究方向为因果推断和不确定性推理|冯宇(1999—),男,云南,硕士研究生,CCF会员,主要研究方向为因果推断和网络安全攻击防御|范永开(1978—),男,山西,教授,博士,CCF会员,主要研究方向为数据安全、内容与传播安全 -
基金资助:国家自然科学基金(62176240);北京市自然科学基金(4222038)
Multi-State Causal Representation and Inference Model in Uncertain Network Attack Scenarios
DONG Chunling( ), FENG Yu, FAN Yongkai
), FENG Yu, FAN Yongkai
- School of Computer and Cyber Sciences, Communication University of China, Beijing 100024, China
-
Received:2024-12-30Online:2025-05-10Published:2025-06-10
摘要:
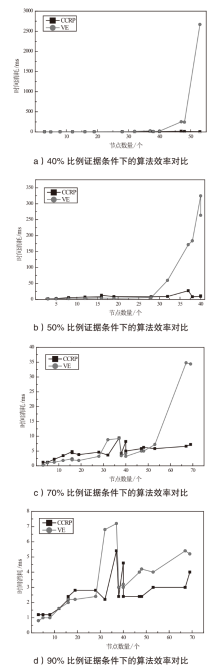
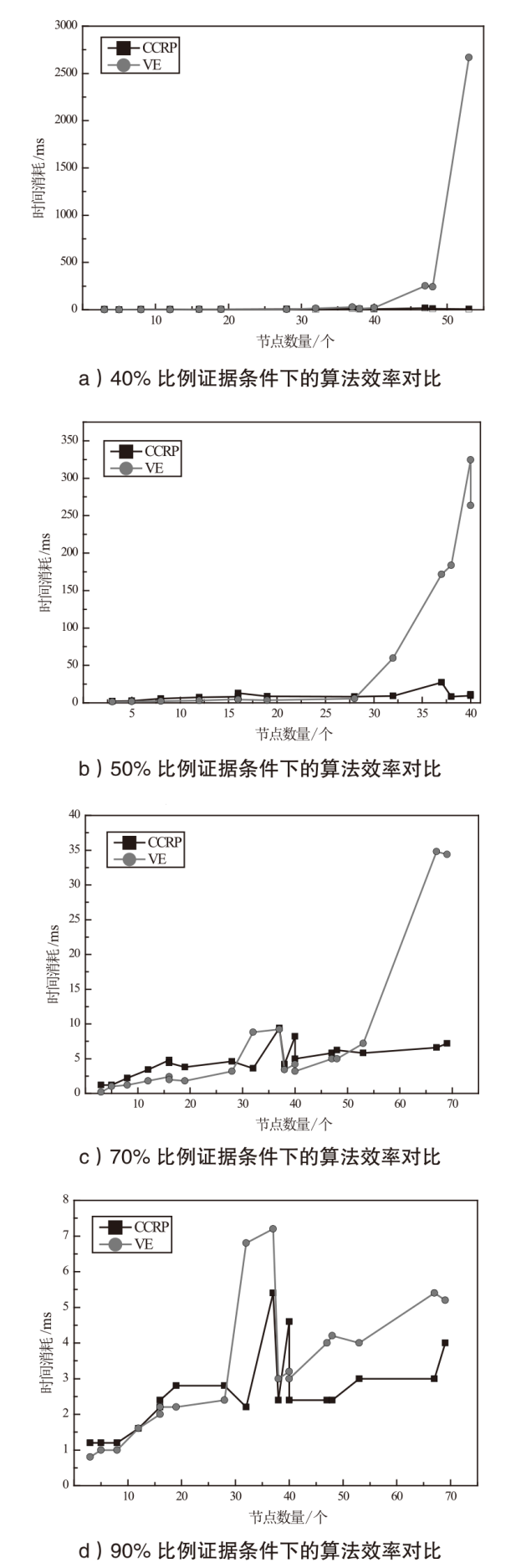
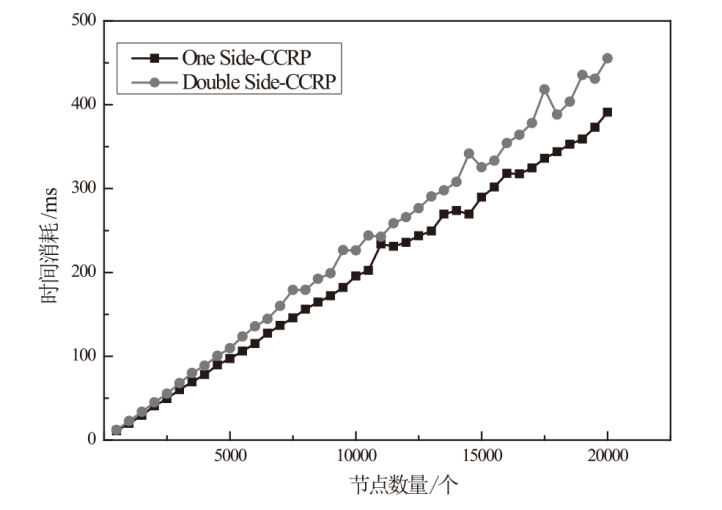
网络安全领域当前面临的挑战之一是对网络攻击的不确定性因素进行系统分析。为应对该挑战,攻击图工具被广泛应用于网络安全领域,旨在描述攻击者行为特征与构建攻击场景。然而,当前的攻击图工具,如属性攻击图、状态攻击图以及贝叶斯攻击图等,并没有全面且综合地考虑网络攻击中存在的不确定性因素,因而无法提供一个统一的网络不确定性因素描述框架。除此之外,当前攻击图中的计算节点风险概率的相关算法时间复杂度较高,难以应用实践。为解决上述问题,文章提出多状态-动态不确定性因果攻击图(M-DUCAG)模型与基于单向因果链的节点风险概率推理(One Side-CCRP)算法,以实现网络不确定性因素的表示与推理。M-DUCAG模型能够表示节点的多个状态,能够结合告警信息更加准确地描述网络攻击过程中的不确定性因素。One Side-CCRP算法通过展开节点上游因果链,有效提高推理的效率与准确性。实验结果表明,M-DUCAG模型在应对参数扰动方面具有鲁棒性,能够有效表示网络攻击过程中的不确定性因素。与变量消除法相比,One Side-CCRP算法在有限数量告警证据下具有更高的推理效率,能够满足现实推理应用需求。
中图分类号:
引用本文
董春玲, 冯宇, 范永开. 不确定性网络攻击场景下的多状态因果表示与推理模型[J]. 信息网络安全, 2025, 25(5): 778-793.
DONG Chunling, FENG Yu, FAN Yongkai. Multi-State Causal Representation and Inference Model in Uncertain Network Attack Scenarios[J]. Netinfo Security, 2025, 25(5): 778-793.
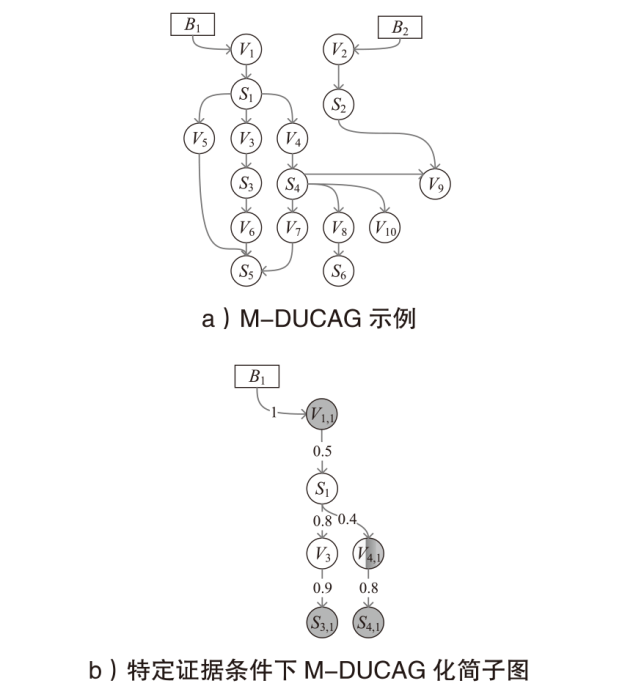
表3
应用D-CCRP算法计算节点后验风险概率
| 节点 | D-CCRP因果链 | Pr (Xv) | O-CCRP因果链 | Pr (Xv) |
|---|---|---|---|---|
| S1,1 | — | — | — | — |
| S1,2 | (AS1,2;V1,1+AV3;S1,2·AS3,1;V+ AV4;S1,2·AS4,1;V4)/3 | 0.73 | AS1,2;V1,1 | 0.5 |
| V3,0 | (AS1,2;V1,1·AV3,0;S1,2+AS3,1;V3,0)/2 | 0.5 | AS1,2;V1,1 | 0.1 |
| V3,1 | (AS1,2;V1,1·AV3,1;S1,2+AS3,1;V3,1)/2 | 0.65 | AS1,2;V1,1·AV3,1;S1,2 | 0.4 |
| V4,0 | (AS1,2;V1,1·AV4,0;S1,2+AS4,1;V4,0)/2 | 0.6 | AS1,2;V1,1·AV4,0;S1,2 | 0.4 |
| V4,1 | (AS1,2;V1,1·AV4,1;S1,2+AS4,1;V4,1)/2 | 0.45 | AS1,2;V1,1·AV4,1;S1,2 | 0.1 |
表4
模拟网络脆弱点详细信息
| ID | 描述信息 | IP地址 | 攻击行为节点 | 漏洞CVE编号 | 攻击发生概率 |
|---|---|---|---|---|---|
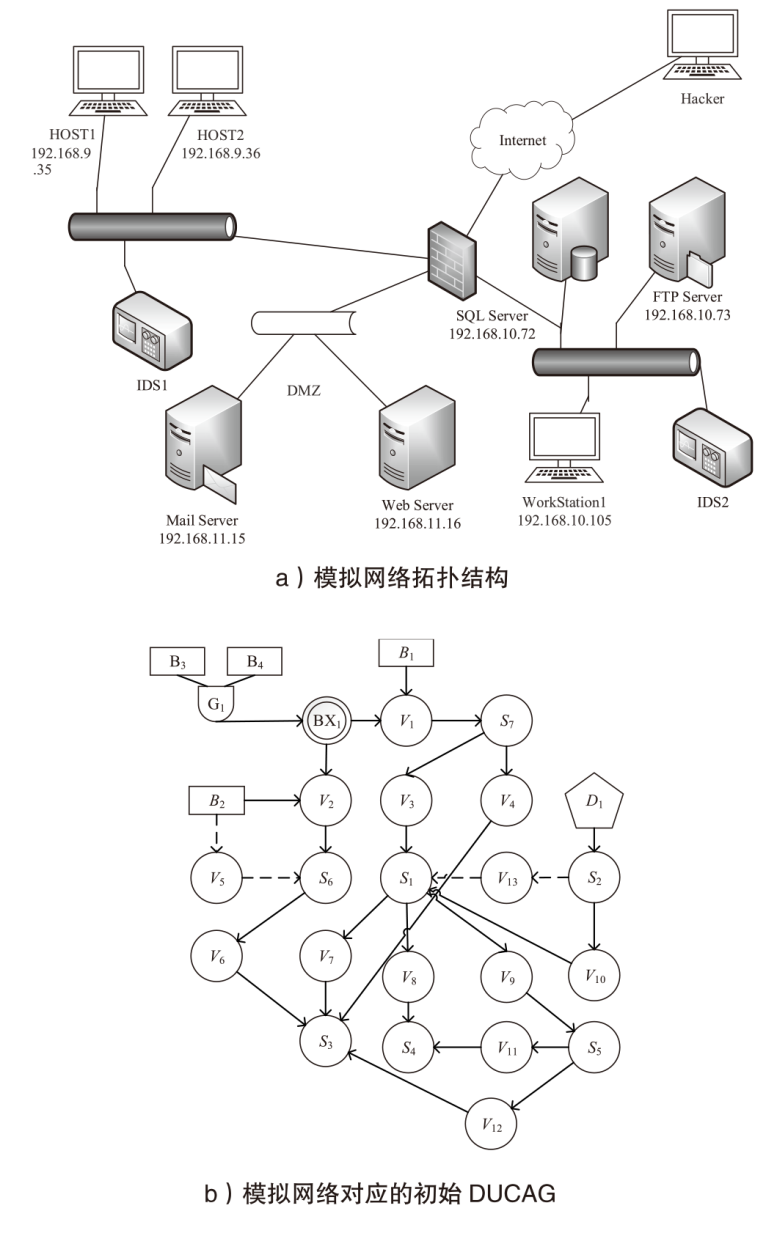
| S1 | HOST1 | 192.168.9.35 | V3, V10 | CVE-2013-3940 | 0.86 |
| CVE-2012-0002 | 0.86 | ||||
| V13 | 零日漏洞攻击 | 0.80 | |||
| S2 | HOST2 | 192.168.9.36 | D1 | Inside Attack | 1.00 |
| S3 | SQL Server | 192.168.10.72 | V4, V6, V7, V12 | CVE-2016-7253 | 0.80 |
| S4 | FTP Server | 192.168.10.73 | V8, V11 | CVE-2015-4108 | 0.86 |
| CVE-2019-10009 | 0.80 | ||||
| S5 | Workstation | 192.168.10.105 | V9 | CVE-2019-5541 | 0.80 |
| CVE-2019-5524 | 0.80 | ||||
| S6 | Mail Server | 192.168.11.15 | V2 | CVE-2020-14066 | 0.80 |
| V5 | 零日漏洞攻击 | 0.80 | |||
| S7 | Web Server | 192.168.11.16 | V1 | CVE-2017-12728 | 0.25 |
表5
不同模拟路径与对应实验结果
| 攻击序列 | 模拟攻击序列 | 攻击候选序列及其概率 |
|---|---|---|
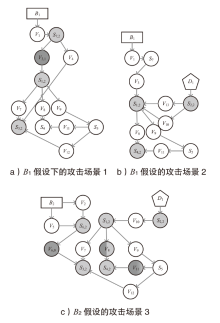
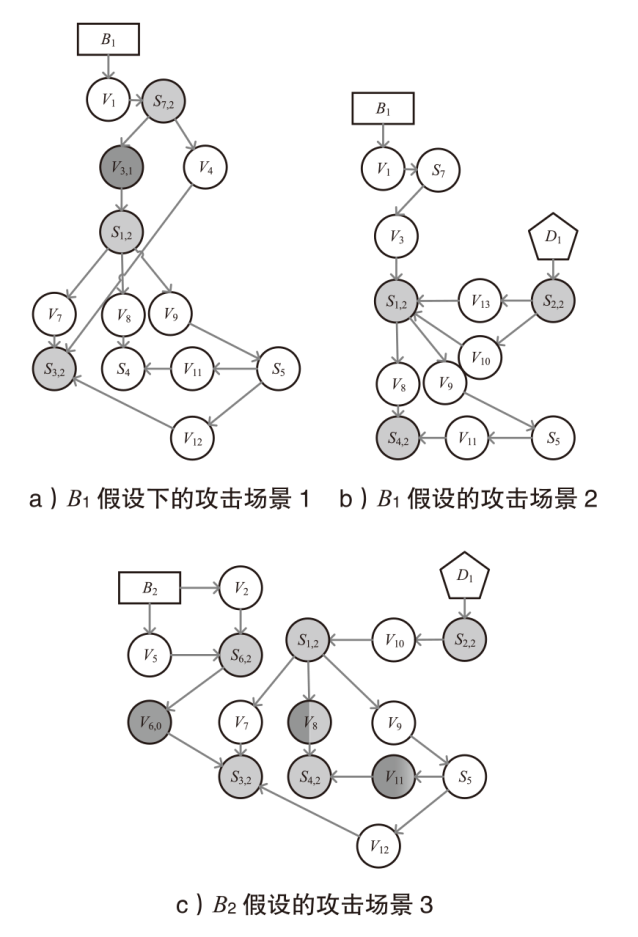
| 1 | B1→V1→S7→ V3→S1→V7→S3 | B1(BX1)→V1,0→S7,2→V3,1→S1,2→V7,0→ S3,2(0.2983) B1(BX1)→V1,0→S7,2→V4,0→S3,2(0.2983) BX1→V2,0→S6,2→V6,0→S3,2(0.3055) |
| 2 | D1→S2→V13→ S1→V8→S4 | D1→S2,2→V13,0→S1,2→V8→S4,2(0.4590) D1→S2,2→V13,0→S1,2→V9,1→S5,2→V11→ S4,2(0.1500) D1→S2,2→V10,1→S1,2→V8→S4,2(0.2870) |
| 3 | 1)B2→V5→ S6→V6→S3 2)D1→S2→V10→ S1→V8→S4 | B2(BX1)→V2,0→S6,2→V6,0→S3,2(0.3732) B2(BX1)→V5,0→S6,2→V6,0→S3,2(0.3732) D1→S2,2→V10,1→S1,2→V8,0→S4,2(0.3420) D1→S2,2→V10,1→S1,2→V8,1→S4,2(0.3690) |
| [1] | PING Guolou, YE Xiaojun. A Survey of Research on Network Attack Model[J]. Journal of Information Security Research, 2020, 6(12): 1058-1067. |
| 平国楼, 叶晓俊. 网络攻击模型研究综述[J]. 信息安全研究, 2020, 6(12): 1058-1067. | |
| [2] | KONSTA A-M, LAFUENTE A L, SPIGA B, et al. Survey: Automatic Generation of Attack Trees and Attack Graphs[J]. Computer Security, 2024, 137(C): 103660-103672. |
| [3] | GADYATSKAYA O. How to Generate Security Cameras: Towards Defence Generation for Socio-Technical Systems[C]// Springer. Proceedings of the Graphical Models for Security:Second International Workshop(GraMSec 2015). Heidelberg: Springer, 2016: 50-65. |
| [4] | IVANOVA M G, PROBST C W, HANSEN R R, et al. Transforming Graphical System Models to Graphical Attack Models[C]// Springer. Proceedings of the Graphical Models for Security:Second International Workshop(GraMSec 2015). Heidelberg: Springer, 2016: 82-96. |
| [5] | LIU Xuejiao. Research on Network Vulnerability Assessment and Intrusion Alert Analysis Technology[D]. WuHan: HuaZhong Nornal University, 2011. |
| 刘雪娇. 网络脆弱性评估及入侵报警分析技术研究[D]. 武汉: 华中师范大学, 2011. | |
| [6] |
ZHONG Shangqin, XU Guosheng, YAO Wenbin, et al. Network Security Analysis Based on Host-Security-Group[J]. Journal of Beijing University of Posts and Telecommunications, 2012, 35(1): 19-23.
doi: 10.13190/jbupt.201201.19.zhongshq |
|
钟尚勤, 徐国胜, 姚文斌, 等. 基于主机安全组划分的网络安全性分析[J]. 北京邮电大学学报, 2012, 35(1): 19-23.
doi: 10.13190/jbupt.201201.19.zhongshq |
|
| [7] | ZENITANI K. From Attack Graph Analysis to Attack Function Analysis[J]. Information Sciences, 2023, 650: 119703-119719. |
| [8] | MOHAMMADZAD M, KARIMPOUR J, MAHAN F. MAGD: Minimal Attack Graph Generation Dynamically in Cyber Security[J]. Computer Networks, 2023, 236: 110004-110019. |
| [9] | WANG Lingyu, YAO Chao, SINGHAL A, et al. Interactive Analysis of Attack Graphs Using Relational Queries[C]// Data and Applications Security XX. 20th Annual IFIP WG 113 Working Conference on Data and Applications Security. Heidelberg:Springer, 2006: 119-132. |
| [10] | WANG Shuo, TANG Guangming, KOU Guang, et al. An Attack Graph Generation Method Based on Heuristic Searching Strategy[C]// IEEE. Proceedings of the 2016 2nd IEEE International Conference on Computer and Communications (ICCC). New York: IEEE, 2016: 1180-1185. |
| [11] | KAYNAR K, SIVRIKAYA F. Distributed Attack Graph Generation[J]. IEEE Transactions on Dependable and Secure Computing, 2015, 13(5): 519-532. |
| [12] | PU Junyan, LI Yahui, ZHOU Chunjie. Cross-Domain Dynamic Security Risk Analysis Method of Industrial Control System Based on Probabilistic Attack Graph[J]. Netinfo Security, 2023, 23(9): 85-94. |
| 浦珺妍, 李亚辉, 周纯杰. 基于概率攻击图的工控系统跨域动态安全风险分析方法[J]. 信息网络安全, 2023, 23(9): 85-94. | |
| [13] | POOLSAPPASIT N, DEWRI R, RAY I. Dynamic Security Risk Management Using Bayesian Attack Graphs[J]. IEEE Transactions on Dependable and Secure Computing, 2011, 9(1): 61-74. |
| [14] | ZHANG Kai, LIU Jingju. Network Attack Path Analysis Method Based on Vulnerability Dynamic Availability[J]. Netinfo Security, 2021, 21(4): 62-72. |
| 张凯, 刘京菊. 基于漏洞动态可利用性的网络入侵路径分析方法[J]. 信息网络安全, 2021, 21(4): 62-72. | |
| [15] |
WANG Yang, WU Jianying, HUANG Jinlei, et al. Network Intrusion Intention Recognition Method Based on Bayesian Attack Graph[J]. Computer Engineering and Applications, 2019, 55(22): 73-79.
doi: 10.3778/j.issn.1002-8331.1809-0081 |
|
王洋, 吴建英, 黄金垒, 等. 基于贝叶斯攻击图的网络入侵意图识别方法[J]. 计算机工程与应用, 2019, 55(22): 73-79.
doi: 10.3778/j.issn.1002-8331.1809-0081 |
|
| [16] |
WANG Wenjuan, DU Xuehui, SHAN Dibin. Construction Method of Attack Scenario in Cloud Environment Based on Dynamic Probabilistic Attack Graph[J]. Journal on Communications, 2021, 42(1): 1-17.
doi: 10.11959/j.issn.1000-436x.2021004 |
|
王文娟, 杜学绘, 单棣斌. 基于动态概率攻击图的云环境攻击场景构建方法[J]. 通信学报, 2021, 42(1): 1-17.
doi: 10.11959/j.issn.1000-436x.2021004 |
|
| [17] | MA Chunguang, WANG Chenghong, ZHANG Donghong, et al. A Dynamic Network Risk Assessment Model Based on Attacker’s Inclination[J]. Journal of Computer Research and Development, 2015, 52(9): 2056-2068. |
| 马春光, 汪诚弘, 张东红, 等. 一种基于攻击意愿分析的网络风险动态评估模型[J]. 计算机研究与发展, 2015, 52(9): 2056-2068. | |
| [18] | GAO Qingguan, ZHANG Bo, FU Anmin. An Advanced Persistent Threat Detection Method Based on Attack Graph[J]. Netinfo Security, 2023, 23(12): 59-68. |
| 高庆官, 张博, 付安民. 一种基于攻击图的高级持续威胁检测方法[J]. 信息网络安全, 2023, 23(12): 59-68. | |
| [19] | XIE PENG, LI J H, OU Xinming, et al. Using Bayesian Networks for Cyber Security Analysis[C]// IEEE. Proceedings of the 2010 IEEE/IFIP. International Conference on Dependable Systems & Networks (DSN). New York: IEEE, 2010: 211-220. |
| [20] | CHEN Xiaojun, SHI Jinqiao, XU Fei, et al. Algorithm of Optimal Security Hardening Measures Against Insider Threat[J]. Journal of Computer Research and Development, 2014, 51(7): 1565-1577. |
| 陈小军, 时金桥, 徐菲, 等. 面向内部威胁的最优安全策略算法研究[J]. 计算机研究与发展, 2014, 51(7): 1565-1577. | |
| [21] | WANG Hui, CHEN Fuwang, WANG Zhe. Research on Internal Network Attack Graph Based on Strength Coefficient[J]. Application Research of Computers, 2018, 35(2): 515-520. |
| 王辉, 陈甫旺, 王哲. 基于强度系数的内部网络攻击图研究[J]. 计算机应用研究, 2018, 35(2): 515-520. | |
| [22] | LALLIE H S, DEBATTISTA K, BAL J. A Review of Attack Graph and Attack Tree Visual Syntax in Cyber Security[J]. Computer Science Review, 2020, 35: 100219-100260. |
| [23] | KEVIN P M. Dynamic Bayesian Networks:Representation, Inference and Learning[D]. Berkeley: University of California, 2002. |
| [24] | CAI Baoping, LIU Yu, XIE Min. A Dynamic-Bayesian-Network-Based Fault Diagnosis Methodology Considering Transient and Intermittent Faults[J]. IEEE Transactions on Automation Science and Engineering, 2017, 14(1): 276-285. |
| [25] | ZHANG Qin, DONG Chunling, CUI Yan, et al. Dynamic Uncertain Causality Graph for Knowledge Representation and Probabilistic Reasoning: Statistics Base, Matrix, and Application[J]. IEEE Transactions on Neural Networks & Learning Systems, 2014, 25(4): 645-663. |
| [26] | DONG Chunling, FENG Yu, SHANG Wenqian. A New Method of Dynamic Network Security Analysis Based on Dynamic Uncertain Causality Graph[J]. Journal of Cloud Computing, 2024, 13(1): 24-41. |
| [27] | DONG Chunling, ZHANG Qin. The Cubic Dynamic Uncertain Causality Graph: A Methodology for Temporal Process Modeling and Diagnostic Logic Inference[J]. IEEE Transactions on Neural Networks and Learning Systems, 2020, 31(10): 4239-4253. |
| [28] | DONG Chunling, ZHOU Zhenxu, ZHANG Qin. Cubic Dynamic Uncertain Causality Graph: A New Methodology for Modeling and Reasoning About Complex Faults with Negative Feedbacks[J]. IEEE Transactions on Reliability, 2018, 67(3): 920-932. |
| [29] | ISAAC M, JOHN M, SADEGH S, et al. Cyclic Bayesian Attack Graphs: A Systematic Computational Approach[C]// IEEE.Security and Privacy in Computing and Communications (TrustCom). New York: IEEE, 2020: 129-136. |
| [1] | 王建新, 许弘可, 肖超恩, 张磊. 基于重映射矩阵的Rowhammer漏洞防御方法研究[J]. 信息网络安全, 2025, 25(5): 758-766. |
| [2] | 张学旺, 卢荟, 谢昊飞. 基于节点中心性和大模型的漏洞检测数据增强方法[J]. 信息网络安全, 2025, 25(4): 550-563. |
| [3] | 张雨轩, 黄诚, 柳蓉, 冷涛. 结合提示词微调的智能合约漏洞检测方法[J]. 信息网络安全, 2025, 25(4): 664-673. |
| [4] | 王鹃, 张勃显, 张志杰, 谢海宁, 付金涛, 王洋. 基于模糊测试的Java反序列化漏洞挖掘[J]. 信息网络安全, 2025, 25(1): 1-12. |
| [5] | 张立强, 路梦君, 严飞. 一种基于函数依赖的跨合约模糊测试方案[J]. 信息网络安全, 2024, 24(7): 1038-1049. |
| [6] | 王鹃, 龚家新, 蔺子卿, 张晓娟. 多维深度导向的Java Web模糊测试方法[J]. 信息网络安全, 2024, 24(2): 282-292. |
| [7] | 李鹏超, 张全涛, 胡源. 基于双注意力机制图神经网络的智能合约漏洞检测方法[J]. 信息网络安全, 2024, 24(11): 1624-1631. |
| [8] | 沈钦涛, 梁瑞刚, 王宝林, 张倞诚, 陈恺. 基于动态执行日志和反向分析的漏洞成因分析技术[J]. 信息网络安全, 2024, 24(10): 1493-1505. |
| [9] | 张展鹏, 王鹃, 张冲, 王杰, 胡宇义. 基于图同构网络的高效Web模糊测试技术研究[J]. 信息网络安全, 2024, 24(10): 1544-1552. |
| [10] | 浦珺妍, 李亚辉, 周纯杰. 基于概率攻击图的工控系统跨域动态安全风险分析方法[J]. 信息网络安全, 2023, 23(9): 85-94. |
| [11] | 王鹃, 张冲, 龚家新, 李俊娥. 基于机器学习的模糊测试研究综述[J]. 信息网络安全, 2023, 23(8): 1-16. |
| [12] | 钟远鑫, 刘嘉勇, 贾鹏. 基于动态时间切片和高效变异的定向模糊测试[J]. 信息网络安全, 2023, 23(8): 99-108. |
| [13] | 贾凡, 康舒雅, 江为强, 王光涛. 基于NLP及特征融合的漏洞相似性算法评估[J]. 信息网络安全, 2023, 23(1): 18-27. |
| [14] | 张光华, 刘永升, 王鹤, 于乃文. 基于BiLSTM和注意力机制的智能合约漏洞检测方案[J]. 信息网络安全, 2022, 22(9): 46-54. |
| [15] | 张玉健, 刘代富, 童飞. 基于局部图匹配的智能合约重入漏洞检测方法[J]. 信息网络安全, 2022, 22(8): 1-7. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||