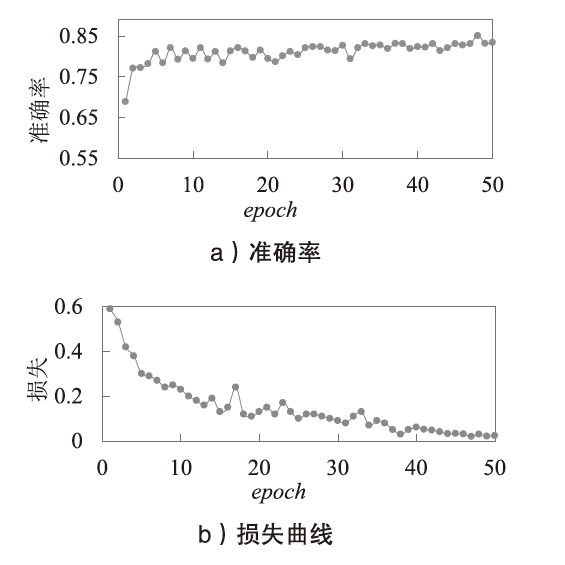
信息网络安全 ›› 2022, Vol. 22 ›› Issue (8): 1-7.doi: 10.3969/j.issn.1671-1122.2022.08.001
基于局部图匹配的智能合约重入漏洞检测方法
- 1.东南大学网络空间安全学院,南京 211189
2.江苏省泛在网络安全工程研究中心,南京 211189
-
收稿日期:2022-04-11出版日期:2022-08-10发布日期:2022-09-15 -
通讯作者:张玉健 E-mail:yjzhang@seu.edu.cn -
作者简介:张玉健(1984—),男,江苏,讲师,博士,主要研究方向为区块链和系统安全。|刘代富(1996—),男,四川,硕士研究生,主要研究方向为区块链和漏洞检测|童飞(1987—),男,安徽,副教授,博士,主要研究方向为物联网及安全 -
基金资助:国家自然科学基金(61971131);江苏省自然科学基金(BK20190346)
Reentrancy Vulnerability Detection in Smart Contracts Based on Local Graph Matching
ZHANG Yujian1,2( ), LIU Daifu1, TONG Fei1,2
), LIU Daifu1, TONG Fei1,2
- 1. School of Cyber Science and Engineering, Southeast University, Nanjing 211189, China
2. Jiangsu Province Engineering Research Center of Security for Ubiquitous Network, Nanjing 211189, China
-
Received:2022-04-11Online:2022-08-10Published:2022-09-15 -
Contact:ZHANG Yujian E-mail:yjzhang@seu.edu.cn
摘要:
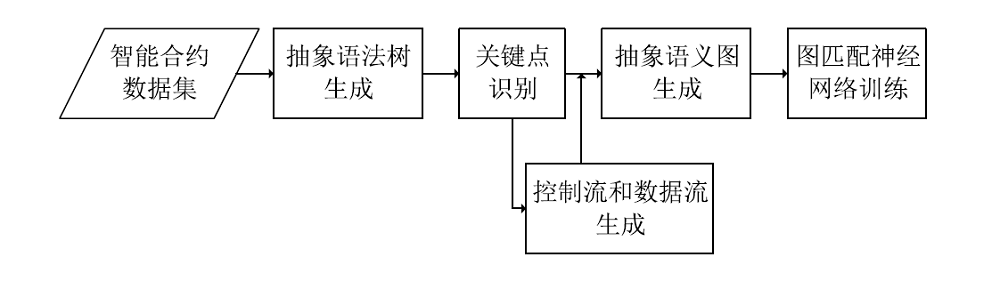
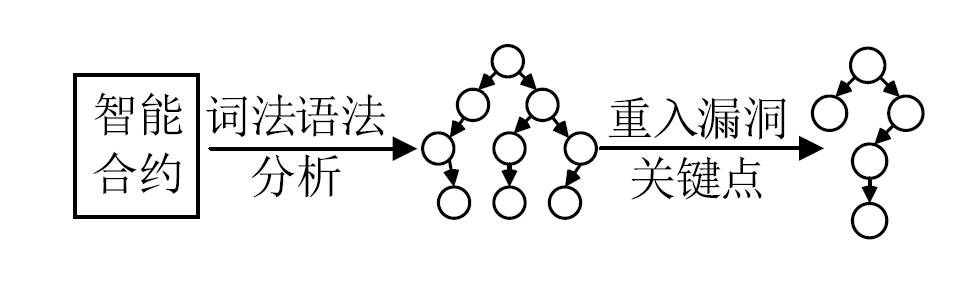
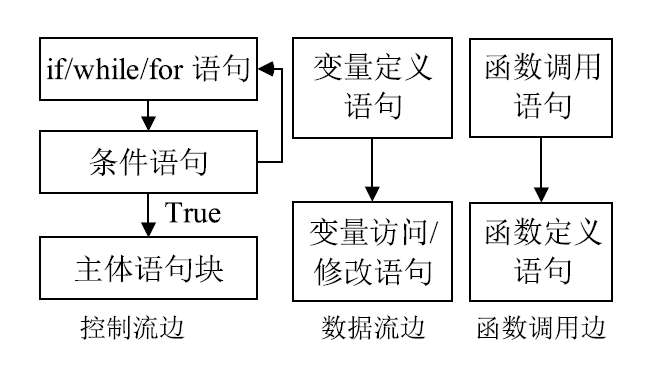
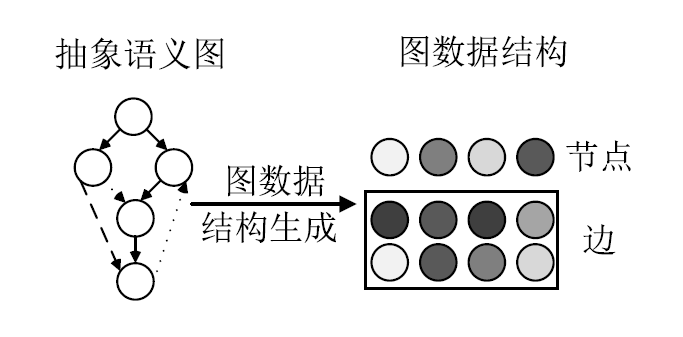
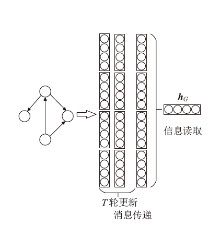
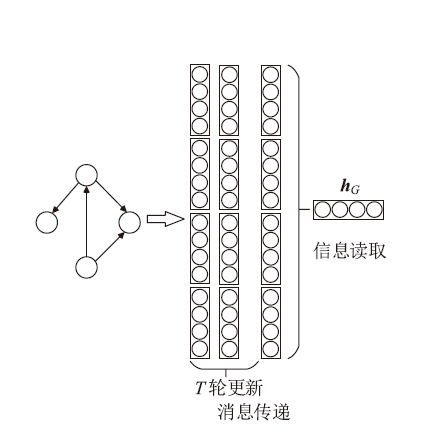
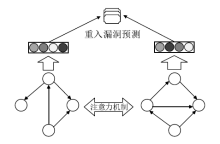
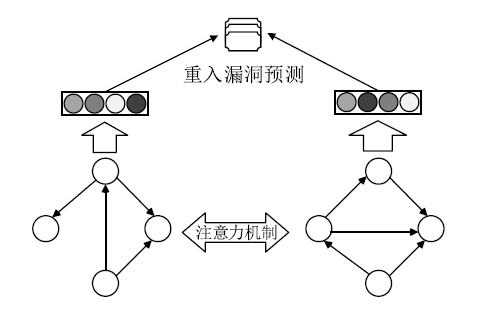
针对以太坊中智能合约遭受重入漏洞攻击的问题,文章提出一种基于局部图匹配的智能合约重入漏洞检测方法。该方法首先将智能合约源代码转化为包含基本结构信息的抽象语法树,并根据重入漏洞的特点裁剪抽象语法树;然后从抽象语法树中提取更加丰富的控制流和数据流,进而生成包含语法和语义信息的局部抽象语义图数据。文章利用图匹配神经网络对局部抽象语义图进行模型训练和测试,使用开源智能合约漏洞样本数据集生成测试数据并对方案进行评估。实验结果表明,该方法能够有效检测智能合约中的重入漏洞。
中图分类号:
引用本文
张玉健, 刘代富, 童飞. 基于局部图匹配的智能合约重入漏洞检测方法[J]. 信息网络安全, 2022, 22(8): 1-7.
ZHANG Yujian, LIU Daifu, TONG Fei. Reentrancy Vulnerability Detection in Smart Contracts Based on Local Graph Matching[J]. Netinfo Security, 2022, 22(8): 1-7.
使用本文
| [1] | SCHOLLMEIER R. A Definition of Peer-to-Peer Networking for the Classification of Peer-to-Peer Architectures and Applications[C]//IEEE. 1st International Conference on Peer-to-Peer Computing. New York: IEEE, 2001: 101-102. |
| [2] | SlowMist. The Total Amount of Money Lost[EB/OL]. (2021-07-05) [2021-08-05]. https://hacked.slowmist.io/?c=ETH%20DApp. |
| [3] | BUTERIN V. ETHEREUM: A Next-Generation Cryptocurrency and Decentralized Application Platform[EB/OL]. (2015-07-14)[2021-09-18]. https://blockchainlab.com/pdf/Ethereum_white_paper-a_next_generation_smart_contract_and_decentralized_application_platform-vitalik-buterin.pdf. |
| [4] | MEHAR M I, SHIER C L, GIAMBATTISTA A, et al. Understanding A Revolutionary and Flawed Grand Experiment in Blockchain: The DAO Attack[J]. Journal of Cases on Information Technology(JCIT), 2019, 21(1): 19-32. |
| [5] | WANG Bin, LIU Han, LIU Chao, et al. Blockeye: Hunting for Defi Attacks on Blockchain[C]//IEEE. 2021 IEEE/ACM 43rd International Conference on Software Engineering:Companion Proceedings(ICSE-Companion). New York: IEEE, 2021: 17-20. |
| [6] | JIANG Bo, LIU Ye, CHAN W K. ContractFuzzer: Fuzzing Smart Contracts for Vulnerability Detection[C]//ACM. 33rd ACM/IEEE International Conference on Automated Software Engineering. New York: ACM, 2018: 259-269. |
| [7] | ZHANG Qingzhao, WANG Yizhuo, LI Juanru, et al. Ethploit: From Fuzzing to Efficient Exploit Generation against Smart Contracts[C]//IEEE. 27th International Conference on Software Analysis, Evolution and Reengineering(SANER). New York: IEEE, 2020: 116-126. |
| [8] | LUU L, CHU D H, OLICKEL H, et al. Making Smart Contracts Smarter[C]//ACM. 2016 ACM SIGSAC Conference on Computer and Communications Security(CCS). New York: ACM, 2016: 254-269. |
| [9] | PRECHTEL D, GROS T, MÜLLER T. Evaluating Spread of ‘Gasless Send’ in Ethereum Smart Contracts[C]//IEEE. 2019 10th IFIP International Conference on New Technologies, Mobility and Security(NTMS). New York: IEEE, 2019: 1-6. |
| [10] | BHARGAVAN K, DELIGNAT-LAVAUD A, FOURNET C, et al. Formal Verification of Smart Contracts: Short Paper[C]//ACM. 2016 ACM Workshop on Programming Languages and Analysis for Security(PLAS). New York: ACM, 2016: 91-96. |
| [11] | TSANKOV P, DAN A, DRACHSLER-COHEN D, et al. Securify: Practical Security Analysis of Smart Contracts[C]//ACM. 2018 ACM SIGSAC Conference on Computer and Communications Security(CCS). New York: ACM, 2018: 67-82. |
| [12] | TIKHOMIROV S, VOSKRESENSKAYA E, IVANITSKIY I, et al. SmartCheck: Static Analysis of Ethereum Smart Contracts[C]//ACM. 1st International Workshop on Emerging Trends in Software Engineering for Blockchain. New York: ACM, 2018: 9-16. |
| [13] | FEIST J, GRIECO G, GROCE A. Slither: A Static Analysis Framework for Smart Contracts[C]//IEEE. 2019 IEEE/ACM 2nd International Workshop on Emerging Trends in Software Engineering for Blockchain(WETSEB). New York: IEEE, 2019: 8-15. |
| [14] | GORI M, MONFARDINI G, SCARSELLI F. A New Model for Learning in Graph Domains[C]//IEEE. 2005 IEEE International Joint Conference on Neural Networks. New York: IEEE, 2005: 729-734. |
| [15] |
CHANG R Y, PODGURSKI A, YANG J. Discovering Neglected Conditions in Software by Mining Dependence Graphs[J]. IEEE Transactions on Software Engineering, 2008, 34(5): 579-596.
doi: 10.1109/TSE.2008.24 URL |
| [16] | LI Yujia, GU Chenjie, DULLIEN T, et al. Graph Matching Networks for Learning the Similarity of Graph Structured Objects[EB/OL]. (2019-07-12)[2021-09-18]. http://proceedings.mlr.press/v97/li19d.html. |
| [17] | ZHUANG Yuan, LIU Zhenguang, QIAN Peng, et al. Smart Contract Vulnerability Detection Using Graph Neural Network[EB/OL]. (2020-05-08)[2021-09-18]. https://www.ijcai.org/Proceedings/2020/0454. pdf. |
| [18] | GILMER J, SCHOENHOLZ S S, RILEY P F, et al. Neural Message Passing for Quantum Chemistry[EB/OL]. (2017-09-13)[2021-09-18]. https://proceedings.mlr.press/v70/gilmer17a.html. |
| [19] | FERREIRA J F, CRUZ P, DURIEUX T, et al. SmartBugs: A Frameworkto Analyze Solidity Smart Contracts[C]//IEEE. 35th IEEE/ACM International Conference on Automated Software Engineering. New York: IEEE, 2020: 1349-1352. |
| [1] | 胡艺, 佘堃. 基于区块链和智能合约的双链车联网系统[J]. 信息网络安全, 2022, 22(8): 26-35. |
| [2] | 王健, 黄俊. 基于智能合约的日志安全存储与公平访问方法[J]. 信息网络安全, 2022, 22(7): 27-36. |
| [3] | 于克辰, 郭莉, 阴宏伟, 燕雪松. 面向数据中心场景的基于区块链与博弈论的高价值数据共享模型[J]. 信息网络安全, 2022, 22(6): 73-85. |
| [4] | 华景煜, 黄达明. 以太坊智能合约定理证明中的形式化规约研究综述[J]. 信息网络安全, 2022, 22(5): 11-20. |
| [5] | 冯景瑜, 张琪, 黄文华, 韩刚. 基于跨链交互的网络安全威胁情报共享方案[J]. 信息网络安全, 2022, 22(5): 21-29. |
| [6] | 李鹏, 郑田甜, 徐鹤, 朱枫. 基于区块链技术的RFID安全认证协议[J]. 信息网络安全, 2021, 21(5): 1-11. |
| [7] | 王健, 于航, 韩臻, 韩磊. 基于智能合约的云存储共享数据访问控制方法[J]. 信息网络安全, 2021, 21(11): 40-47. |
| [8] | 于克辰, 郭莉, 姚萌萌. 基于区块链的高价值数据共享系统设计[J]. 信息网络安全, 2021, 21(11): 75-84. |
| [9] | 姜楠, 王玮琦, 王健. 基于智能合约的个人隐私数据保护方法研究[J]. 信息网络安全, 2020, 20(11): 22-31. |
| [10] | 周元健, 秦冬梅, 刘忆宁, 吕松展. 基于区块链的可信仓单系统设计[J]. 信息网络安全, 2019, 19(6): 84-90. |
| [11] | 王文明, 施重阳, 王英豪, 危德健. 基于区块链技术的交易及其安全性研究[J]. 信息网络安全, 2019, 19(5): 1-9. |
| [12] | 黑一鸣, 刘建伟, 张宗洋, 喻辉. 基于区块链的可公开验证分布式云存储系统[J]. 信息网络安全, 2019, 19(3): 52-60. |
| [13] | 李佩丽, 徐海霞, 马添军, 穆永恒. 区块链技术在网络互助中的应用及用户隐私保护[J]. 信息网络安全, 2018, 18(9): 60-65. |
| [14] | 马春光, 安婧, 毕伟, 袁琪. 区块链中的智能合约[J]. 信息网络安全, 2018, 18(11): 8-17. |
| 阅读次数 | ||||||||||||||||||||||||||||||||||||||||||||||||||
|
全文 237
|
|
|||||||||||||||||||||||||||||||||||||||||||||||||
|
摘要 275
|
|
|||||||||||||||||||||||||||||||||||||||||||||||||