信息网络安全 ›› 2022, Vol. 22 ›› Issue (8): 8-18.doi: 10.3969/j.issn.1671-1122.2022.08.002
基于混沌和改进广义Feistel结构的轻量级密码算法
- 1.哈尔滨工业大学(威海)计算机科学与技术学院,威海 264209
2.哈尔滨工业大学(威海)信息科学与工程学院,威海 264209
-
收稿日期:2022-04-15出版日期:2022-08-10发布日期:2022-09-15 -
通讯作者:苏煜粤 E-mail:suyuyue2000@163.com -
作者简介:佟晓筠(1963—),女,辽宁,教授,博士,主要研究方向为信息安全|苏煜粤(2000—),女,江西,硕士研究生,主要研究方向为信息安全和混沌密码学。|张淼(1979—),女,内蒙古,教授,博士,主要研究方向为混沌密码学|王翥(1963—),男,辽宁,教授,博士,主要研究方向为无线传感网络与安全 -
基金资助:国家自然科学基金(61902091);山东省自然科学基金(ZR2019MF054)
Lightweight Cipher Algorithm Based on Chaos and Improved Generalized Feistel Structure
TONG Xiaojun1, SU Yuyue1( ), ZHANG Miao1, WANG Zhu2
), ZHANG Miao1, WANG Zhu2
- 1. Department of Computer Science and Technology, Harbin Institute of Technology at Weihai, Weihai 264209, China
2. Department of Information science and Engineering, Harbin Institute of Technology at Weihai, Weihai 264209, China
-
Received:2022-04-15Online:2022-08-10Published:2022-09-15 -
Contact:SU Yuyue E-mail:suyuyue2000@163.com
摘要:
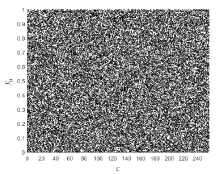
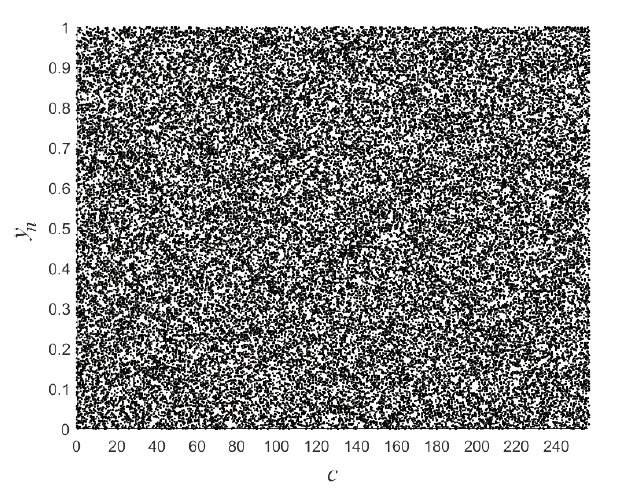
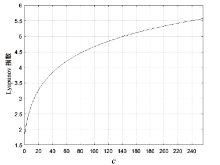
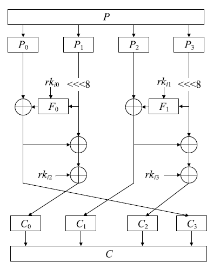
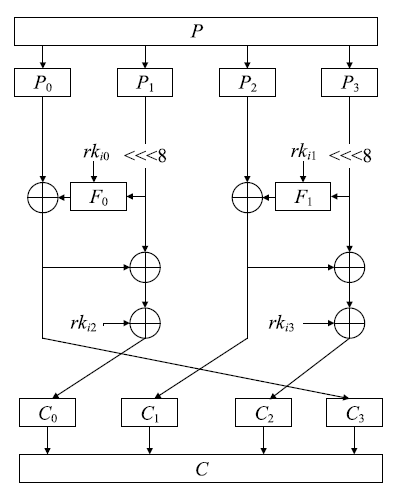
随着物联网的快速发展,无线网络传感器、射频识别标签以及工业控制器等被广泛部署,这些资源受限设备的安全同样需要保障,而传统的密码算法需要消耗大量的资源,不适用于资源受限设备。针对以上问题,文章提出一种轻量级分组密码。S盒是分组密码的关键性组件,通过应用两个混沌映射和跳跃蜘蛛优化算法构成的多目标优化算法生成并优化得到非线性度平均值为110,线性逼近概率为0.1172,差分逼近概率为0.0391的S盒。文章对广义Feistel结构进行相应改进,改进后的结构一次能够处理所有的中间状态,不存在未处理的分支,并结合构造的S盒、密钥扩展算法等,组成分组长度为64位、种子密钥长度为80位、迭代轮数为12轮的轻量级分组密码算法。该算法的等效门电路数量符合轻量级的标准,并且有良好的性能。
中图分类号:
引用本文
佟晓筠, 苏煜粤, 张淼, 王翥. 基于混沌和改进广义Feistel结构的轻量级密码算法[J]. 信息网络安全, 2022, 22(8): 8-18.
TONG Xiaojun, SU Yuyue, ZHANG Miao, WANG Zhu. Lightweight Cipher Algorithm Based on Chaos and Improved Generalized Feistel Structure[J]. Netinfo Security, 2022, 22(8): 8-18.
表1
优化后得到的性能较好的S盒
| 列 行 | 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | 9 | 10 | 11 | 12 | 13 | 14 | 15 | 16 |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1 | 181 | 21 | 208 | 152 | 204 | 42 | 156 | 189 | 253 | 132 | 170 | 77 | 177 | 216 | 149 | 230 |
| 2 | 237 | 11 | 235 | 83 | 255 | 120 | 188 | 62 | 88 | 236 | 183 | 191 | 114 | 107 | 175 | 136 |
| 3 | 140 | 252 | 65 | 59 | 76 | 12 | 124 | 47 | 145 | 64 | 49 | 6 | 54 | 171 | 222 | 43 |
| 4 | 79 | 106 | 75 | 246 | 81 | 217 | 98 | 27 | 102 | 39 | 127 | 192 | 199 | 133 | 160 | 220 |
| 5 | 240 | 166 | 67 | 159 | 84 | 155 | 111 | 167 | 56 | 94 | 61 | 148 | 226 | 125 | 60 | 151 |
| 6 | 71 | 165 | 168 | 198 | 231 | 5 | 182 | 146 | 38 | 150 | 31 | 210 | 195 | 214 | 154 | 24 |
| 7 | 57 | 26 | 122 | 203 | 44 | 95 | 239 | 193 | 130 | 23 | 110 | 224 | 20 | 249 | 2 | 90 |
| 8 | 7 | 55 | 131 | 13 | 248 | 4 | 22 | 135 | 89 | 173 | 126 | 128 | 254 | 123 | 218 | 116 |
| 9 | 223 | 174 | 63 | 238 | 105 | 134 | 18 | 129 | 206 | 121 | 143 | 32 | 138 | 153 | 85 | 241 |
| 10 | 15 | 45 | 51 | 161 | 41 | 178 | 86 | 0 | 103 | 197 | 70 | 30 | 50 | 118 | 139 | 225 |
| 11 | 207 | 9 | 250 | 247 | 10 | 40 | 69 | 179 | 119 | 187 | 112 | 53 | 92 | 93 | 137 | 87 |
| 12 | 232 | 215 | 3 | 244 | 1 | 158 | 176 | 172 | 48 | 46 | 109 | 99 | 104 | 37 | 142 | 184 |
| 13 | 14 | 96 | 97 | 33 | 16 | 17 | 190 | 163 | 78 | 28 | 8 | 209 | 113 | 202 | 227 | 157 |
| 14 | 200 | 162 | 242 | 91 | 82 | 251 | 74 | 234 | 211 | 34 | 219 | 35 | 194 | 144 | 221 | 72 |
| 15 | 243 | 66 | 80 | 19 | 117 | 25 | 196 | 185 | 205 | 58 | 108 | 212 | 100 | 233 | 52 | 68 |
| 16 | 115 | 201 | 36 | 186 | 180 | 141 | 164 | 228 | 169 | 147 | 29 | 101 | 245 | 73 | 229 | 213 |
表3
${{S}_{1}}$的差分分布
| 列 行 | 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | 9 | 10 | 11 | 12 | 13 | 14 | 15 | 16 |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1 | — | 6 | 6 | 6 | 6 | 8 | 8 | 6 | 6 | 8 | 8 | 8 | 8 | 6 | 6 | 10 |
| 2 | 8 | 8 | 8 | 6 | 10 | 8 | 8 | 10 | 6 | 6 | 8 | 10 | 6 | 6 | 8 | 6 |
| 3 | 6 | 6 | 6 | 6 | 6 | 6 | 10 | 6 | 6 | 8 | 6 | 6 | 8 | 6 | 8 | 8 |
| 4 | 8 | 6 | 6 | 6 | 8 | 6 | 8 | 8 | 8 | 4 | 6 | 6 | 6 | 6 | 6 | 6 |
| 5 | 6 | 6 | 6 | 6 | 8 | 6 | 6 | 8 | 6 | 8 | 6 | 6 | 6 | 8 | 6 | 6 |
| 6 | 6 | 8 | 6 | 8 | 6 | 6 | 6 | 8 | 6 | 8 | 6 | 8 | 6 | 6 | 6 | 6 |
| 7 | 8 | 8 | 8 | 6 | 6 | 6 | 6 | 6 | 6 | 6 | 6 | 8 | 8 | 8 | 6 | 6 |
| 8 | 8 | 6 | 6 | 6 | 8 | 6 | 8 | 8 | 6 | 10 | 6 | 6 | 6 | 6 | 6 | 6 |
| 9 | 6 | 10 | 6 | 8 | 6 | 8 | 6 | 8 | 6 | 8 | 6 | 6 | 6 | 6 | 6 | 6 |
| 10 | 6 | 6 | 8 | 6 | 8 | 8 | 6 | 8 | 8 | 6 | 6 | 6 | 10 | 6 | 8 | 6 |
| 11 | 6 | 6 | 6 | 10 | 6 | 10 | 6 | 8 | 8 | 6 | 6 | 6 | 6 | 6 | 6 | 8 |
| 12 | 6 | 8 | 6 | 8 | 6 | 6 | 10 | 6 | 8 | 6 | 6 | 6 | 6 | 6 | 6 | 6 |
| 13 | 6 | 10 | 6 | 6 | 8 | 6 | 8 | 8 | 8 | 4 | 6 | 6 | 6 | 8 | 8 | 6 |
| 14 | 4 | 8 | 6 | 6 | 10 | 8 | 6 | 6 | 6 | 6 | 6 | 6 | 6 | 8 | 10 | 6 |
| 15 | 6 | 6 | 6 | 6 | 8 | 8 | 8 | 6 | 10 | 6 | 6 | 10 | 6 | 6 | 8 | 6 |
| 16 | 6 | 8 | 8 | 8 | 6 | 8 | 4 | 8 | 8 | 6 | 6 | 8 | 6 | 6 | 6 | 8 |
表4
${{S}_{1}}$的SAC相关矩阵
| 列 行 | 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 |
|---|---|---|---|---|---|---|---|---|
| 1 | 0.4688 | 0.4688 | 0.4844 | 0.4844 | 0.5313 | 0.5625 | 0.4844 | 0.5156 |
| 2 | 0.5781 | 0.5156 | 0.4844 | 0.4531 | 0.4844 | 0.4531 | 0.5000 | 0.4688 |
| 3 | 0.5156 | 0.4844 | 0.5000 | 0.5000 | 0.5000 | 0.5156 | 0.4688 | 0.5156 |
| 4 | 0.4844 | 0.4531 | 0.4844 | 0.5156 | 0.6094 | 0.5313 | 0.5313 | 0.4844 |
| 5 | 0.5000 | 0.5469 | 0.4688 | 0.4688 | 0.5469 | 0.4688 | 0.5000 | 0.5313 |
| 6 | 0.5156 | 0.5000 | 0.5000 | 0.4531 | 0.4688 | 0.5469 | 0.5156 | 0.4688 |
| 7 | 0.5469 | 0.4688 | 0.4688 | 0.5313 | 0.5781 | 0.5313 | 0.4844 | 0.5313 |
| 8 | 0.4531 | 0.5469 | 0.5313 | 0.4375 | 0.5000 | 0.5781 | 0.5156 | 0.4375 |
表6
${{S}_{1}}$的BIC-SAC
| 列 行 | 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 |
|---|---|---|---|---|---|---|---|---|
| 1 | 0.5000 | 0.4961 | 0.4961 | 0.5098 | 0.4824 | 0.5000 | 0.5234 | 0.4805 |
| 2 | 0.4961 | 0.5000 | 0.4902 | 0.5020 | 0.4863 | 0.4863 | 0.5039 | 0.5098 |
| 3 | 0.4961 | 0.4902 | 0.5000 | 0.5078 | 0.5020 | 0.5078 | 0.5117 | 0.4922 |
| 4 | 0.5098 | 0.5020 | 0.5078 | 0.5000 | 0.5078 | 0.5020 | 0.4883 | 0.5137 |
| 5 | 0.4824 | 0.4863 | 0.5020 | 0.5078 | 0.5000 | 0.5137 | 0.4961 | 0.4941 |
| 6 | 0.5000 | 0.4863 | 0.5078 | 0.5020 | 0.5137 | 0.5000 | 0.5000 | 0.5078 |
| 7 | 0.5234 | 0.5039 | 0.5117 | 0.4883 | 0.4961 | 0.5000 | 0.5000 | 0.5254 |
| 8 | 0.4805 | 0.5098 | 0.4922 | 0.5137 | 0.4941 | 0.5078 | 0.5254 | 0.5000 |
| [1] |
SMID M E, BRANSTAD D K. The Data Encryption Standard: Past and Future[J]. Proceedings of the IEEE, 1988, 76(5): 550-559.
doi: 10.1109/5.4441 URL |
| [2] | DAEMEN J, RIJMEN V. The Design of Rijndael: AES—The Advanced Encryption Standard[M]. Berlin: Springer, 2002. |
| [3] | SCHNEIER B. The IDEA Encryption Algorithm[J]. Dr Dobb’s Journal-Software Tools for the Professional Programmer, 1993, 18(13): 50-57. |
| [4] |
LI Lang, LIU Botao, WANG Hui. QTL: A New Ultra-Lightweight Block Cipher-Science Direct[J]. Microprocessors and Microsystems, 2016, 45(1): 45-55.
doi: 10.1016/j.micpro.2016.03.011 URL |
| [5] |
LI Lang, LI Kenli, HE Weiwei, et al. Magpie: A High Security Lightweight Block Cipher Algorithm[J]. Acta Electronica Sinica, 2017, 45(10): 2521-2527.
doi: 10.3969/j.issn.0372-2112.2017.10.029 |
|
李浪, 李肯立, 贺位位, 等. Magpie:一种高安全的轻量级分组密码算法[J]. 电子学报, 2017, 45(10):2521-2527.
doi: 10.3969/j.issn.0372-2112.2017.10.029 |
|
| [6] | BISWAS A, MAJUMDAR A, NATH S, et al. LRBC: A Lightweight Block Cipher Design for Resource Constrained IoT Devices[EB/OL]. (2020-01-11)[2022-04-11]. https://doi.org/10.1007/s12652-020-01694-9. |
| [7] | LI Lang, LIU Botao. Surge: A New Low-Resource and Efficient Lightweight Block Cipher Algorithm[J]. Computer Science, 2018, 45(2): 236-240. |
| 李浪, 刘波涛. Surge:一种新型、低资源、高效的轻量级分组密码算法[J]. 计算机科学, 2018, 45(2):236-240. | |
| [8] |
LI Lang, LIU Botao, ZHOU Yimeng, et al. SFN: A New Lightweight Block Cipher[J]. Microprocessors and Microsystems, 2018, 60: 138-150.
doi: 10.1016/j.micpro.2018.04.009 URL |
| [9] | FENG Jingya, LI Lang. SCENERY: A Lightweight Block Cipher Based on Feistel Structure[J]. Frontiers of Computer Science, 2022, 16(3): 1-10. |
| [10] | SHI Guodong, KANG Fei, GU Haiwen. Research on Unified Description Model of Block Cipher[J]. Computer Engineering, 2010, 36(1): 154-156. |
| 师国栋, 康绯, 顾海文. 分组密码统一描述模型研究[J]. 计算机工程, 2010, 36(1): 154-156. | |
| [11] | DWIVEDI A D. BRISK: Dynamic Encryption Based Cipher for Long Term Security[EB/OL]. (2021-08-26)[2022-04-13]. https://doi.org/10.3390/s21175744. |
| [12] | TONG Xiaojun, LIU Xudong, LIU Jing, et al. A Novel Lightweight Block Encryption Algorithm Based on Combined Chaotic S-Box[EB/OL]. (2021-09-18)[2022-04-13]. https://doi.org/10.1142/S0218127421501522. |
| [13] | ZHANG Xiaofeng, LIU Yonggui. Lightweight Block Cipher Algorithm Based on the Improved Generalized Feistel Structure[EB/OL]. (2021-08-26)[2022-04-13]. . |
| 张晓枫, 刘永桂. 改进的广义Feistel结构轻量级分组密码算法[EB/OL]. (2021-08-26)[2022-04-13]. http://kns.cnki.net/kcms/detail/44.1240. TP.20210825.1338.020. html. | |
| [14] | MASSEY J L. SAFER K-64: A Byte-Oriented Block-Ciphering Algorithm[C]//Springer. International Workshop on Fast Software Encryption. Berlin: Springer, 1993: 1-17. |
| [15] |
LAMBIC D. A Novel Method of S-Box Design Based on Discrete Chaotic Map[J]. Nonlinear Dynamics, 2017, 87(4): 1-7.
doi: 10.1007/s11071-016-2940-9 URL |
| [16] |
HEMATPOUR N, AHADPOUR S. Execution Examination of Chaotic S-Box Dependent on Improved PSO Algorithm[J]. Neural Computing and Applications, 2021, 33(10): 5111-5133.
doi: 10.1007/s00521-020-05304-9 URL |
| [17] |
WANG Yong, ZHANG Zhiqiang, ZHANG L Y, et al. A Genetic Algorithm for Constructing Bijective Substitution Boxes with High Nonlinearity[J]. Information Sciences, 2020, 523: 152-166.
doi: 10.1016/j.ins.2020.03.025 URL |
| [18] |
IBRAHIM S, ABBAS A M. A Novel Optimization Method for Constructing Cryptographically Strong Dynamic S-Boxes[J]. IEEE Access, 2020, 8: 225004-225017.
doi: 10.1109/ACCESS.2020.3045260 URL |
| [19] | ZHANG Xuefeng, WEI Kaili, JIANG Wen. The Nonlinearity Optimization Algorithm of S-Box Based on TD-ERCS Sequence[J]. Netinfo Security, 2021, 21(1): 10-18. |
| 张雪锋, 卫凯莉, 姜文. 基于TD-ERCS序列的S盒非线性度优化算法[J]. 信息网络安全, 2021, 21(1): 10-18. | |
| [20] | WANG Xingyuan, CHEN Xuan. An Image Encryption Algorithm Based on Dynamic Row Scrambling and Zigzag Transformation[EB/OL]. (2021-06-27)[2022-04-13]. https://doi.org/10.1016/j.chaos.2021.110962. |
| [21] | PERAZA V H, PENA D A, RANJAN P, et al. A Bio-Inspired Method for Mathematical Optimization Inspired by Arachnida Salticidade[EB/OL]. (2021-12-29)[2022-04-14]. https://doi.org/10.3390/math10010102. |
| [22] | WANG Xingyuan, GUAN Nana, YANG Jingjing. Image Encryption Algorithm with Random Scrambling Based on One-Dimensional Logistic Self-Embedding Chaotic Map[J]. Chaos Solitons and Fractals, 2021, 150(3): 111-117. |
| [23] | NARUEI I, KEYNIA F. A New Optimization Method Based on Coot Bird Natural Life Model[EB/OL]. (2021-11-15)[2022-04-13]. https://doi.org/10.1016/j.eswa.2021.115352. |
| [24] |
TALATAHARI S, AZIZI M. Chaos Game Optimization: A Novel Metaheuristic Algorithm[J]. Artificial Intelligence Review, 2021, 54(2): 917-1004.
doi: 10.1007/s10462-020-09867-w URL |
| [25] | VILLUENDAS R Y, VELAZQUEZ R J L, ALANIS T M D, et al. Mexican Axolotl Optimization: A Novel Bioinspired Heuristic[EB/OL]. (2021-04-03)[2022-04-13].https://doi.org/10.3390/math9070781. |
| [26] | CHOU J S, TROUNG D N. A Novel Metaheuristic Optimizer Inspired by Behavior of Jellyfish in Ocean[EB/OL]. (2021-01-15)[2022-04-13]. https://doi.org/10.1016/j.amc.2020.125535. |
| [27] |
BELAZI A, KHAN M, ABD E L A A, et al. Efficient Cryptosystem Approaches: S-Boxes and Permutation-Substitution-Based Encryption[J]. Nonlinear Dynamics, 2017, 87(1): 337-361.
doi: 10.1007/s11071-016-3046-0 URL |
| [28] |
ULLAH A, JAMAL S S, SHAH T. A Novel Construction of Substitution Box Using a Combination of Chaotic Maps with Improved Chaotic Range[J]. Nonlinear Dynamics, 2017, 88(4): 2757-2769.
doi: 10.1007/s11071-017-3409-1 URL |
| [29] |
HUA Zhongyun, LI Jiaxin, CHEN Yongyong, et al. Design and Application of an S-Box Using Complete Latin Square[J]. Nonlinear Dynamics, 2021, 104(1): 807-825.
doi: 10.1007/s11071-021-06308-3 URL |
| [30] | BOGDANOV A, KNUDSEN L R, LEANDER G, et al. PRESENT: An Ultra-Lightweight Block Cipher[C]//Springer. Cryptographic Hardware and Embedded Systems-CHES 2007, 9th International Workshop. Berlin: Springer, 2007: 450-466. |
| [31] | SHIRAI T, SHIBUTANI K, AKISHITA T, et al. The 128-bit Blockcipher CLEFIA (Extended Abstract)[M]. Berlin: Lecture Notes in Computer Science, 2007. |
| [1] | 陈柏沩, 夏璇, 钟卫东, 吴立强. 基于秘密共享的LBlock的S盒防御方案[J]. 信息网络安全, 2021, 21(7): 80-86. |
| [2] | 孟庆全, 杨晓元, 钟卫东, 张帅伟. 抵抗差分功耗攻击的秘密共享S盒实现与优化[J]. 信息网络安全, 2018, 18(2): 71-77. |
| [3] | 王闻博, 程庆丰, 陆思奇, 赵进华. 一种基于混沌映射的秘密握手协议[J]. 信息网络安全, 2015, 15(11): 40-46. |
| [4] | . 基于混沌和比特级置乱的并行图像加密算法[J]. , 2014, 14(4): 40-. |
| [5] | 杨佳;鲁青远. C2密码防攻击技术研究[J]. , 2011, 11(5): 0-0. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||