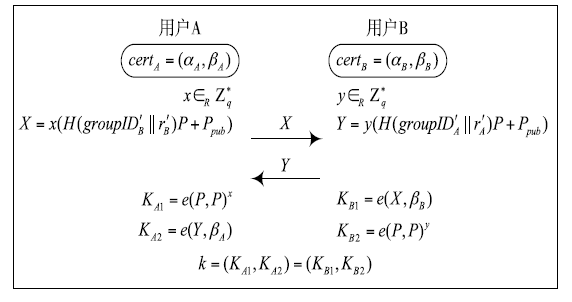
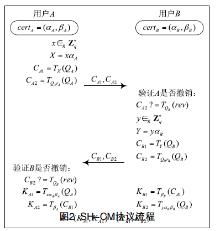
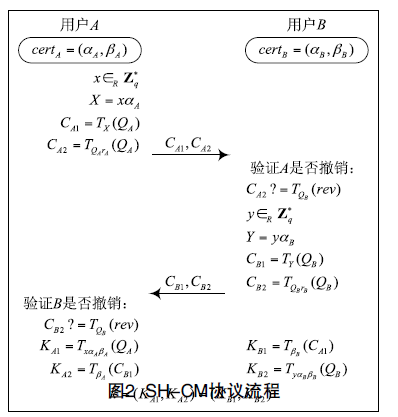
| [1] |
Balfanz D, Durfee G, Shankar N, et al.Secret handshakes from pairing-based key agreements[C]//Proceedings of the 2003 IEEE Symposium on Security and Privacy.Berkeley: IEEE Computer Society, 2003: 180-196.
|
| [2] |
Jarecki S, Kim J, Tsudik G.Beyond secret handshakes: Affiliation-hiding authenticated key exchange[C]//Malkin, T.G.(ed.) CT-RSA 2008. LNCS, vol. 4964, pp. 352-369. Springer, Heidelberg, 2008.
|
| [3] |
Shin J S, Gligor VD.A new privacy-enhanced matchmaking protocol[C]//Network and Distributed System Security Symposuim, February 2007. The Internet Society, 2007.
|
| [4] |
Xu S, Yung M.K-anonymous Secret Handshakes with Reusable Credentials[C]//Proc. of Conf. on Computer and Communications Security. Washington D. C. , USA: ACM Press, 2004.
|
| [5] |
Sorniotti A, Molva R.Secret handshakes with revocation support[C]// Proceedings of ICISC 2009. LNCS 5984. Berlin: Springer-Verlag, 2010: 274-299.
|
| [6] |
温雅敏,龚征. 一个新型不可关联秘密握手方案[J]. 计算机工程, 2013,39(3):152-156.
|
| [7] |
唐春明,郑晓龙. 云计算中一种对大群组用户的隐私保护公共审计方案[J]. 信息网络安全,2015,(2):19-25.
|
| [8] |
Pal P K A K. A New Secret Handshakes Scheme with Dynamic Matching Based on ZSS[J]. International Journal of Network Security & Its Applications (IJNSA), 2015, 7(1): 67-78.
|
| [9] |
Mason J C, Handscomb D C.Chebyshev Polynomials [M]. Chapman & Hall/CRC Press, London, 2003.
|
| [10] |
Kocarev L, Tasev Z.Public-Key Encryption Based on Chebyshev Maps[C]//Proceedings of the 2003 IEEE Symposium on Circuits and Systems (ISCAS '03) [C], IEEE Computer Society, 2003.
|
| [11] |
Bergamo P, D' Arco P, Santis A, et al. Security of Public Key Cryptosystems Based on Chebyshev Polynomials[J]. IEEE Transactions on Circuits and Systems I: Regular Papers, 2005,52(7):1382-93.
|
| [12] |
Zhang F, Safavi-Naini R, Susilo W.An efficient Signature Scheme from Bilinear Pairing and Its Application[J]. Public Key Cryptography (PKC 2004), Springer Verlag, 2004: 277-290.
|
| [13] |
Guo D, Wen Q, Li W, et al.Analysis and Improvement of ‘Chaotic Map Based Mobile Dynamic ID Authenticated Key Agreement Scheme’[J]. Wireless Personal Communications, 2015: 1-14.
|
| [14] |
Fan C, Sun W. Huang V.Provably Secure Randomized Blind Signature Scheme Based on Bilinear Pairing[J]. Computers & Mathematics with Applications, 2010, 60(2): 285-293.
|
| [15] |
Koblitz N, Menezes A, Vanstone S.The State of Elliptic Curve Cryptography[J]. Designs, Codes and Cryptography, Springer Verlag, 2000, 19(2): 173-193.
|
| [16] |
李慧智,韩广国,王沂. 一种漫游网络中可证安全的用户认证方案研究[J]. 信息网络安全,2015,(7):51-57.
|