信息网络安全 ›› 2024, Vol. 24 ›› Issue (10): 1544-1552.doi: 10.3969/j.issn.1671-1122.2024.10.008
基于图同构网络的高效Web模糊测试技术研究
张展鹏1,2, 王鹃1,2( ), 张冲1,2, 王杰1,2, 胡宇义1,2
), 张冲1,2, 王杰1,2, 胡宇义1,2
- 1.武汉大学国家网络安全学院,武汉 430072
2.武汉大学空天信息安全与可信计算教育部重点实验室,武汉 430072
-
收稿日期:2024-05-08出版日期:2024-10-10发布日期:2024-09-27 -
通讯作者:王鹃,jwang@whu.edu.cn -
作者简介:张展鹏(2000—),男,河北,硕士研究生,主要研究方向为漏洞挖掘、系统安全|王鹃(1976—),女,湖北,教授,博士,CCF会员,主要研究方向为网络安全、可信计算、系统安全、人工智能安全|张冲(1998—),男,山东,硕士,主要研究方向为漏洞挖掘、二进制安全|王杰(1995—),男,山东,博士研究生,主要研究方向为可信计算、机密计算|胡宇义(2001—),男,四川,硕士研究生,主要研究方向为系统安全、硬件安全、漏洞挖掘 -
基金资助:国家自然科学基金(61872430);科技部科技创新2030—“新一代人工智能”重大项目(2020AA0107700);国家电网科学技术项目(520940210009)
The Research on Efficient Web Fuzzing Technology Based on Graph Isomorphic Network
ZHANG Zhanpeng1,2, WANG Juan1,2( ), ZHANG Chong1,2, WANG Jie1,2, HU Yuyi1,2
), ZHANG Chong1,2, WANG Jie1,2, HU Yuyi1,2
- 1. School of Cyber Science and Engineering, Wuhan University, Wuhan 430072, China
2. Key Laboratory of Aerospace Information Security and Trusted Computing of Ministry of Education, Wuhan University, Wuhan 430072, China
-
Received:2024-05-08Online:2024-10-10Published:2024-09-27
摘要:
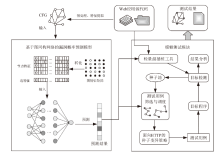
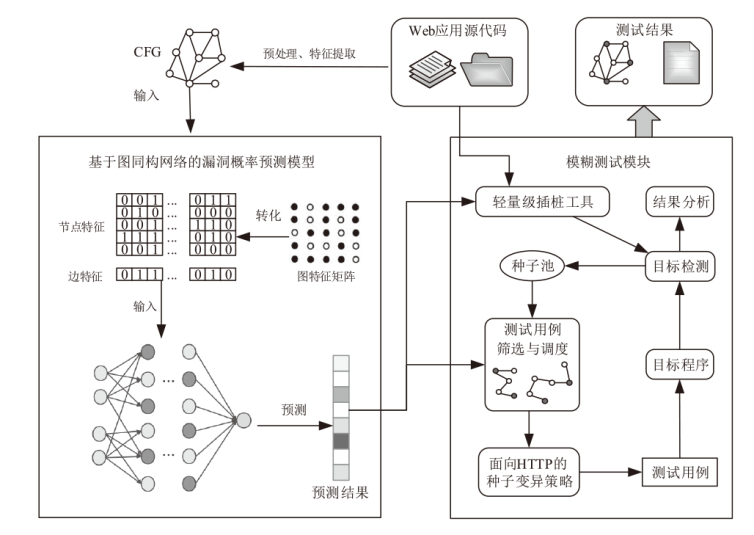
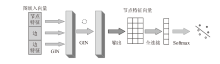
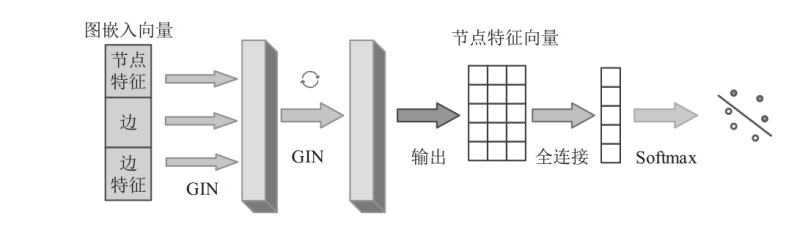
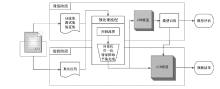
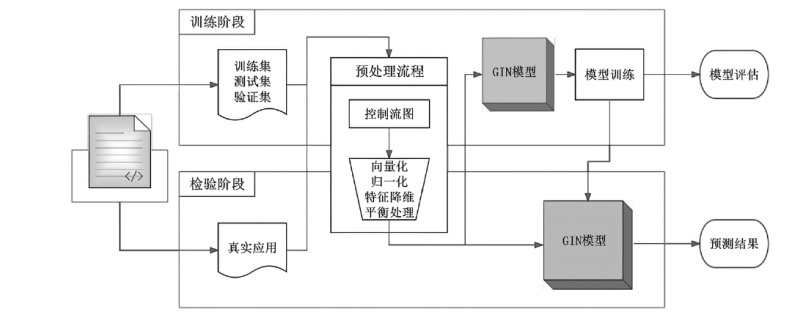
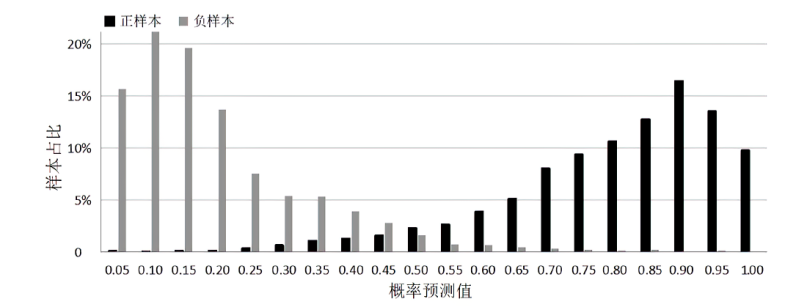
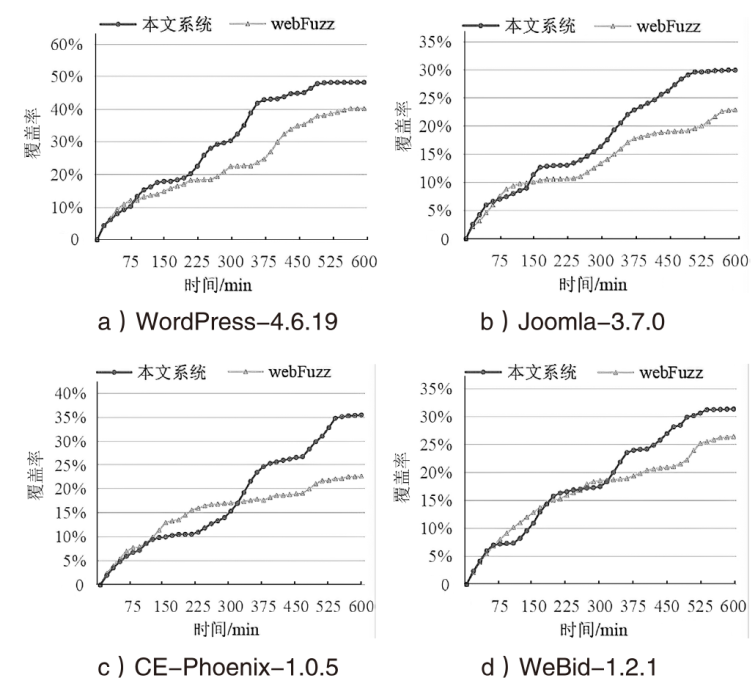
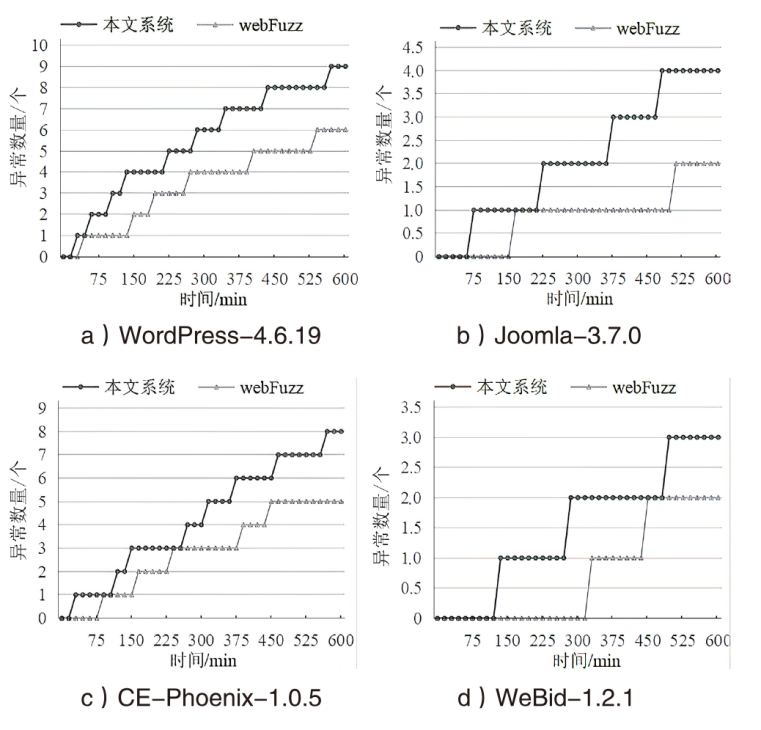
现有的Web模糊测试方法主要包括基于字典的黑盒测试方法和借鉴二进制模糊测试的灰盒测试方法,这些方法存在随机性大、效率低的缺点。针对上述问题,文章提出了一种基于图同构网络的高效Web模糊测试方法。首先,利用图同构网络在图表示和图结构学习方面的强大能力,在代码的控制流图上学习漏洞语义和结构特征,并进行基本块漏洞概率预测;然后,基于漏洞预测结果提出了漏洞概率和覆盖率双导向的Web应用模糊测试指导策略,在不降低覆盖率的同时优先探索含漏洞概率更高的程序位置,有效解决了现有Web应用模糊测试工具随机性大、效率低的问题;最后,基于以上方法实现了原型系统并进行实验评估。实验结果表明,与webFuzz相比,该原型系统的漏洞挖掘效率提高了40%,覆盖率扩大了5%。
中图分类号:
引用本文
张展鹏, 王鹃, 张冲, 王杰, 胡宇义. 基于图同构网络的高效Web模糊测试技术研究[J]. 信息网络安全, 2024, 24(10): 1544-1552.
ZHANG Zhanpeng, WANG Juan, ZHANG Chong, WANG Jie, HU Yuyi. The Research on Efficient Web Fuzzing Technology Based on Graph Isomorphic Network[J]. Netinfo Security, 2024, 24(10): 1544-1552.
| [1] | MILLER B P, FREDRIKSEN L, SO B. An Empirical Study of the Reliability of UNIX Utilities[J]. Communications of the ACM, 1990, 33(12): 32-44. |
| [2] |
TU Ling, MA Yue, CHENG Cheng, et al. Hybrid Protocol Deformation Based Web Security Fuzzy Testing and Utility Evaluation Approach[J]. Computer Science, 2017, 44(5): 141-145.
doi: 10.11896/j.issn.1002-137X.2017.05.025 |
|
涂玲, 马跃, 程诚, 等. 基于协议混合变形的Web安全模糊测试与效用评估方法[J]. 计算机科学, 2017, 44(5): 141-145.
doi: 10.11896/j.issn.1002-137X.2017.05.025 |
|
| [3] | ZHOU Xinshi. Research and Implementation of Web Vulnerability Mining Technology Based on Fuzzy Testing[D]. Beijing: Beijing University of Posts and Telecommunications, 2020. |
| 周心实. 基于模糊测试的Web漏洞挖掘技术研究与实现[D]. 北京: 北京邮电大学, 2020. | |
| [4] | VAN R O, CHARALAMBOUS M A, KAIZER D, et al. WebFuzz: Grey-Box Fuzzing for Web Applications[C]// Springer. 26th European Symposium on Research in Computer Security (ESORICS 2021). Heidelberg: Springer, 2021: 152-172. |
| [5] | GAUTHIER F, HASSANSHAHI B, SELWYN-SMITH B, et al. BackREST: A Model-Based Feedback-Driven Greybox Fuzzer for Web Applications[EB/OL]. (2021-08-19)[2024-03-05]. https://arxiv.org/abs/2108.08455v1. |
| [6] | ZHAO Jiazhen, LU Yuliang, ZHU Kailong, et al. Cefuzz: An Directed Fuzzing Framework for PHP RCE Vulnerability[EB/OL]. (2022-03-01)[2024-03-05]. https://doi.org/10.3390/electronics11050758. |
| [7] | Google. American Fuzzy Lop[EB/OL]. (2023-04-01)[2024-03-05]. http://lcamtuf.coredump.cx/afl/. |
| [8] | BÖHME M, PHAM V T, ROYCHOUDHURY A. Coverage-Based Greybox Fuzzing as Markov Chain[C]// ACM. Proceedings of the 2016 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2016: 1032-1043. |
| [9] | BÖHME M, PHAM V T, NGUYEN M D, et al. Directed Greybox Fuzzing[C]// ACM. Proceedings of the 2017 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2017: 2329-2344. |
| [10] | CHEN Hongxu, XUE Yinxing, LI Yuekang, et al. Hawkeye: Towards a Desired Directed Grey-Box Fuzzer[C]// ACM. Proceedings of the 2018 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2018: 2095-2108. |
| [11] | PortSwigger. Burp Suite[EB/OL]. (2023-03-23)[2024-03-05]. https://portswigger.net/burp. |
| [12] | Acunetix. Acunetix Web Vulnerability Scanner[EB/OL]. (2023-03-23)[2024-03-05]. https://www.acunetix.com/. |
| [13] | HCLSoftware. AppScan[EB/OL]. (2023-03-23)[2024-03-05]. https://www.hcltechsw.com/appscan. |
| [14] | ZAP Dev Team. OWASP Zed Attack Proxy[EB/OL]. (2023-03-23)[2024-03-05]. https://www.zaproxy.org/. |
| [15] | Vulners Inc. w3af-Open Source Web Application Security Scanner[EB/OL]. (2023-03-23)[2024-03-05]. http://w3af.org/. |
| [16] | LI Yuwei, JI Shouling, LYU Chenyang, et al. V-Fuzz: Vulnerability Prediction-Assisted Evolutionary Fuzzing for Binary Programs[J]. IEEE Transactions on Cybernetics, 2022, 52(5): 3745-3756. |
| [17] | ZHAO Yuyue, LI Yangyang, YANG Tengfei, et al. Suzzer: A Vulnerability-Guided Fuzzer Based on Deep Learning[C]// Springer. International Conference on Information Security and Cryptology. Heidelberg: Springer, 2020: 134-153. |
| [18] | WANG Yan, JIA Peng, LIU Luping, et al. A Systematic Review of Fuzzing Based on Machine Learning Techniques[EB/OL]. (2020-08-18)[2024-03-05]. https://arxiv.org/abs/1908.01262. |
| [19] | Nikic. A PHP Parser Written in PHP[EB/OL]. (2018-03-15)[2024-03-05]. https://github.com/nikic/PHP-Parser. |
| [20] | XU K, HU Weihua, LESKOVEC J, et al. How Powerful are Graph Neural Networks?[EB/OL]. (2018-10-01)[2024-03-05]. https://arxiv.org/abs/1810.00826. |
| [21] | Wikipedia. Weisfeiler Leman Graph Isomorphism Test[EB/OL]. (2023-03-23)[2024-03-05]. https://en.wikipedia.org/wiki/Weisfeiler_Leman_graph_isomorphism_test. |
| [22] | NIST. PHP Vulnerability Test Suite[EB/OL]. (2023-03-23)[2024-03-05]. https://samate.nist.gov/SARD/test-suites/103. |
| [1] | 陈昊然, 刘宇, 陈平. 基于大语言模型的内生安全异构体生成方法[J]. 信息网络安全, 2024, 24(8): 1231-1240. |
| [2] | 张立强, 路梦君, 严飞. 一种基于函数依赖的跨合约模糊测试方案[J]. 信息网络安全, 2024, 24(7): 1038-1049. |
| [3] | 王鹃, 龚家新, 蔺子卿, 张晓娟. 多维深度导向的Java Web模糊测试方法[J]. 信息网络安全, 2024, 24(2): 282-292. |
| [4] | 张子涵, 赖清楠, 周昌令. 深度学习框架模糊测试研究综述[J]. 信息网络安全, 2024, 24(10): 1528-1536. |
| [5] | 洪玄泉, 贾鹏, 刘嘉勇. AFLNeTrans:状态间关系感知的网络协议模糊测试[J]. 信息网络安全, 2024, 24(1): 121-132. |
| [6] | 王鹃, 张冲, 龚家新, 李俊娥. 基于机器学习的模糊测试研究综述[J]. 信息网络安全, 2023, 23(8): 1-16. |
| [7] | 钟远鑫, 刘嘉勇, 贾鹏. 基于动态时间切片和高效变异的定向模糊测试[J]. 信息网络安全, 2023, 23(8): 99-108. |
| [8] | 吴佳明, 熊焰, 黄文超, 武建双. 一种基于距离导向的模糊测试变异方法[J]. 信息网络安全, 2021, 21(10): 63-68. |
| [9] | 杜笑宇, 叶何, 文伟平. 基于字节码搜索的Java反序列化漏洞调用链挖掘方法[J]. 信息网络安全, 2020, 20(7): 19-29. |
| [10] | 李明磊, 黄晖, 陆余良. 面向漏洞挖掘的基于符号分治区的测试用例生成技术[J]. 信息网络安全, 2020, 20(5): 39-46. |
| [11] | 段斌, 李兰, 赖俊, 詹俊. 基于动态污点分析的工控设备硬件漏洞挖掘方法研究[J]. 信息网络安全, 2019, 19(4): 47-54. |
| [12] | 胡建伟, 赵伟, 闫峥, 章芮. 基于机器学习的SQL注入漏洞挖掘技术的分析与实现[J]. 信息网络安全, 2019, 19(11): 36-42. |
| [13] | 王夏菁, 胡昌振, 马锐, 高欣竺. 二进制程序漏洞挖掘关键技术研究综述[J]. 信息网络安全, 2017, 17(8): 1-13. |
| [14] | 郭亮, 罗森林, 潘丽敏. 编码函数交叉定位网络协议测试数据生成方法研究[J]. 信息网络安全, 2016, 16(3): 8-14. |
| [15] | . 基于模糊测试的网络协议自动化漏洞挖掘工具设计与实现[J]. , 2014, 14(6): 23-. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||