信息网络安全 ›› 2021, Vol. 21 ›› Issue (12): 109-117.doi: 10.3969/j.issn.1671-1122.2021.12.015
一种基于改进的Xception网络的深度伪造视频检测模型
- 中国人民公安大学信息网络安全学院,北京 100038
-
收稿日期:2021-11-05出版日期:2021-12-10发布日期:2022-01-11 -
通讯作者:蔡满春 E-mail:caimanchun@ppsuc.edu.cn -
作者简介:马瑞(1997—),男,江苏,硕士研究生,主要研究方向为信息网络安全|蔡满春(1972—),男,河北,副教授,博士,主要研究方向为密码学与通信保密|彭舒凡(1998—),男,江苏,硕士研究生,主要研究方向为信息网络安全 -
基金资助:“十三五”国家密码发展基金密码理论研究重点课题(MMJJ20180108);中国人民公安大学2020年基本科研业务费(2020JKF101)
A Deep Forgery Video Detection Model Based on Improved Xception Network
MA Rui, CAI Manchun( ), PENG Shufan
), PENG Shufan
- College of Information Network Security, People’s Public University of China, Beijing 100038, China
-
Received:2021-11-05Online:2021-12-10Published:2022-01-11 -
Contact:CAI Manchun E-mail:caimanchun@ppsuc.edu.cn
摘要:
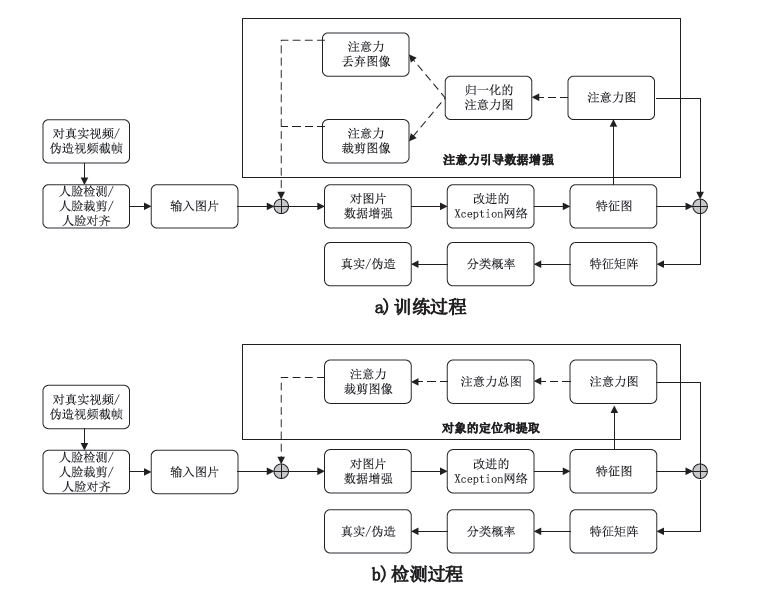
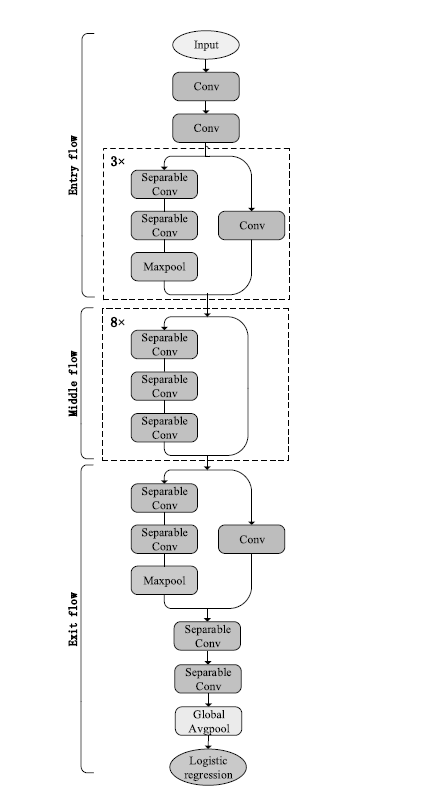
近年来,随着深度伪造技术的发展,深度伪造的内容变得更加难以识别,这给信息网络的安全带来了严峻的挑战。文章针对深度伪造篡改的内容不易识别以及现有深度伪造检测方法存在的面部特征提取不充分、参数量过大等问题,提出了一种融合Xception网络、SENet与WSDAN的深度伪造检测模型i_Xception。该模型将SE模块嵌入Xception网络中用来提取特征,再利用WSDAN模块对输入图片用注意力引导数据增强,把增强后的图像反馈回网络进行训练,以提高模型的检测精度。在此基础上,文章通过合理减小Xception网络的深度和宽度,设计了一个轻量级的网络模型i_miniXception,大大减少模型的参数。在目前深度伪造检测领域广泛使用的数据集FaceForensics++的两类子数据集FaceSwap和DeepFakes上验证,i_Xception检测的准确率分别达到99.50%和98.83%,i_miniXception检测的准确率分别达到99.17%和98.50%,优于现有的主流算法。
中图分类号:
引用本文
马瑞, 蔡满春, 彭舒凡. 一种基于改进的Xception网络的深度伪造视频检测模型[J]. 信息网络安全, 2021, 21(12): 109-117.
MA Rui, CAI Manchun, PENG Shufan. A Deep Forgery Video Detection Model Based on Improved Xception Network[J]. Netinfo Security, 2021, 21(12): 109-117.
使用本文
表1
改进策略产生性能增益对比
| Model | Acc | CrossEntropy Loss | Param-eters/MB | |||||
|---|---|---|---|---|---|---|---|---|
| Xception | Mini_Xception | SENet | WSDAN | FS | DP | FS | DP | |
| √ | — | — | — | 98.17% | 97.50% | 0.0863 | 0.1027 | 21.80 |
| √ | — | √ | — | 99.17% | 98.33% | 0.0752 | 0.0863 | 22.30 |
| √ | — | √ | √ | 99.50% | 98.83% | 0.0628 | 0.0786 | 20.53 |
| — | √ | — | — | 97.67% | 97.16% | 0.0893 | 0.1063 | 1.96 |
| — | √ | √ | — | 98.50% | 98.16% | 0.0796 | 0.0886 | 2.37 |
| — | √ | √ | √ | 99.17% | 98.50% | 0.0746 | 0.0832 | 2.05 |
| [1] |
SHU Kai, SLIVA A, WANG Suhang, et al. Fake News Detection on Social Media: A Data Mining Perspective[J]. ACM SIGKDD Explorations Newsletter, 2017, 19(1):22-36.
doi: 10.1145/3137597.3137600 URL |
| [2] | KINGMA D P, WELLING M. Auto-encoding Variational Bayes[EB/OL]. https://arxiv.org/abs/1312.6114, 2013-12-20. |
| [3] | REZENDE D J, MOHAMED S, WIERSTRA D. Stochastic Backpropagation and Approximate Inference in Deep Generative Models[C]// ICML. International Conference on Machine Learning, June 21-26,2014, Beijing, China. New York: PMLR, 2014: 1278-1286. |
| [4] |
GOODFELLOW I, POUGET-ABADIE J, MIRZA M, et al. Generative Adversarial Networks[J]. Communications of the ACM, 2020, 63(11):139-144.
doi: 10.1145/3422622 URL |
| [5] | AGARWAL S, FARID H, GU Y, et al. Protecting World Leaders against Deep Fakes[C] // IEEE. In: Proc. of the IEEE Conf. on Computer Vision and Pattern Recognition Workshops, June 16-20, 2019, Long Beach, CA, USA. New York: IEEE, 2019: 38-45. |
| [6] | WANG Run, MA Lei, JUEFEI-XU F, et al. Fakespotter: A Simple Yet Robust Baseline for Spotting Ai-synthesized Fake Faces[EB/OL]. https://arxiv.org/abs/1909.06122, 2019-09-13. |
| [7] | AMOS B, LUDWICZUK B, SATYANARAYANAN M. Openface: A General-purpose Face Recognition Library with Mobile Applications[EB/OL]. http://reports-archive.adm.cs.cmu.edu/anon/anon/usr0/ftp/2016/CMU-CS-16-118.pdf, 2021-10-06. |
| [8] | SCHROFF F, KALENICHENKO D, PHILBIN J. Facenet: A Unified Embedding for Face Recognition and Clustering[C]// IEEE. Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition, June 7-12, 2015, Boston, MA, USA. New York: IEEE, 2015: 815-823. |
| [9] | AMERINI I, GALTERI L, CALDELLI R, et al. Deepfake Video Detection through Optical Flow Based CNN[C]// IEEE. In: Proc. of the IEEE International Conference. on Computer Vision Workshops, October 27-28, 2019, Seoul, Korea (South). New York: IEEE, 2019: 1205-1207. |
| [10] | SABIR E, CHENG Jiaxin, JAISWAL A, et al. Recurrent Convolutional Strategies for Face Manipulation Detection in Videos[J]. Interfaces (GUI), 2019, 3(1):80-87. |
| [11] | MITTAL T, BHATTACHARYA U, CHANDRA R, et al. Emotions Don’t Lie: An Audio-uisual Deepfake Detection Method Using Affective Cues[C]// ACM. Proceedings of the 28th ACM International Conference on Multimedia, October 12-16, 2020, Seattle, WA, USA. New York: ACM, 2020: 2823-2832. |
| [12] | LIMA O D, FRANKLIN S, BASU S, et al. Deepfake Detection Using Spatiotemporal Convolutional Networks[EB/OL]. https://arxiv.org/abs/2006.14749, 2020-06-26. |
| [13] | AFCHAR D, NOZICK V, YAMAGISHI J, et al. Mesonet: A Compact Facial Video Forgery Detection Network[C]// IEEE. In: Proc. of the IEEE Int’l Workshop on Information Forensics and Security (WIFS), December 11-13, 2018, Hong Kong, China. New York: IEEE, 2018: 1-7. |
| [14] | NGUYEN HH, YAMAGISHI J, ECHIZEN I. Capsule-forensics: Using Capsule Networks to Detect Forged Images and Videos[C]// IEEE. In: Proc. Of the IEEE Int’l Conf. on Acoustics, Speech and Signal Processing (ICASSP 2019), May 12-17, 2019, Brighton, United Kingdom. New York: IEEE, 2019: 2307-2311. |
| [15] | DANG Hao, LIU Feng, STEHOUWER J, et al. On the Detection of Digital Face Manipulation[C]// IEEE. In:Proc. of the IEEE Conference. on Computer Vision and Pattern Recognition (CVPR), May 12-17, 2019, Brighton, United Kingdom. New York: IEEE, 2020: 5780-5789. |
| [16] | TAN Mingxing, LE Q. Efficientnet: Rethinking Model Scaling for Convolutional Neural Networks[C]// ICML. International Conference on Machine Learning. June 9-15, 2019, Long Beach, California, USA. New York: PMLR, 2019: 6105-6114. |
| [17] | ZHU Xintong, TANG Yunqi, GENG Pengzhi. Detection Algorithm of Tamper and Deepfake Image Based on Feature Fusion[J]. Netinfo Security, 2021, 21(8):70-81. |
| 朱新同, 唐云祁, 耿鹏志. 基于特征融合的篡改与深度伪造图像检测算法[J]. 信息网络安全, 2021, 21(8):70-81. | |
| [18] | CHOLLET F. Xception: Deep Learning with Depthwise Separable Convolutions[C]// IEEE. Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition, July 21-26, 2017, Honolulu, HI, USA. NewYork: IEEE, 2017: 1251-1258. |
| [19] | CHEN Shuping, CHEN Bingcai. Research on Image Classification Method Based on Improved Xception Model[M]// LIANG Qilian,WANG Wei, MU Jiasong,et al.Artificial Intelligence in China. Singapore: Springer, 2021: 538-547. |
| [20] | WOO S, PARK J, LEE J Y, et al. Cbam: Convolutional Block Attention Module[C]// ICAIS. Proceedings of the European Conference on Computer Vision (ECCV), July 26-28, 2019, New York, NY, USA. New York: Springer, 2019: 3-19. |
| [21] | LIN Hao, LUO Weiqi, WEI Kangkang, et al. Improved Xception with Dual Attention Mechanism and Feature Fusion for Face Forgery Detection[EB/OL]. https://arxiv.org/abs/2109.14136, 2021-9-29. |
| [22] | HU Jie, SHEN Li, SUN Gang. Squeeze-and-excitation networks[C]// IEEE. Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition, July 26-28, 2019, New York, USA. New York: IEEE, 2018: 7132-7141. |
| [23] | HU Tao, QI Honggang, HUANG Qingming, et al. See Better Before Looking Closer: Weakly Supervised Data Augmentation Network for Fine-grained Visual Classification[EB/OL]. https://arxiv.org/abs/1901.09891, 2019-01-26. |
| [24] | DENG Jiankang, GUO Jia, ZHOU Yuxiang, et al. Retinaface: Single-stage Dense Face Localisation in the Wild[EB/OL]. https://arxiv.org/abs/1905.00641, 2019-05-02. |
| [25] |
SHORTEN C, KHOSHGOFTAAR T M. A Survey on Image Data Augmentation for Deep Learning[J]. Journal of Big Data, 2019, 6(1):1-48.
doi: 10.1186/s40537-018-0162-3 URL |
| [26] | CUBUK E D, ZOPH B, MANE D, et al. Autoaugment: Learning Augmentation Policies from Data[EB/OL]. https://arxiv.org/abs/1805.09501, 2018-05-24. |
| [27] | ROSSLER A, COZZOLINO D, VERDOLIVA L, et al. Faceforensics++: Learning to Detect Manipulated Facial Images[C]// IEEE. Proceedings of the IEEE/CVF International Conference on Computer Vision, October 27-November 2, 2019, Seoul, Korea (South). New York: IEEE, 2019: 1-11. |
| [1] | 朱新同, 唐云祁, 耿鹏志. 基于特征融合的篡改与深度伪造图像检测算法[J]. 信息网络安全, 2021, 21(8): 70-81. |
| [2] | 路宏琳, 王利明. 面向用户的支持用户掉线的联邦学习数据隐私保护方法[J]. 信息网络安全, 2021, 21(3): 64-71. |
| [3] | 潘孝勤, 杜彦辉. 基于混合特征和多通道GRU的伪造语音鉴别方法[J]. 信息网络安全, 2021, 21(10): 1-7. |
| [4] | 徐国天, 盛振威. 基于融合CNN与LSTM的DGA恶意域名检测方法[J]. 信息网络安全, 2021, 21(10): 41-47. |
| [5] | 吴警, 芦天亮, 杜彦辉. 基于Char-RNN改进模型的恶意域名训练数据生成技术[J]. 信息网络安全, 2020, 20(9): 6-11. |
| [6] | 王文华, 郝新, 刘焱, 王洋. AI系统的安全测评和防御加固方案[J]. 信息网络安全, 2020, 20(9): 87-91. |
| [7] | 张蕾华, 黄进, 张涛, 王生玉. 视频侦查中人像智能分析应用及算法优化[J]. 信息网络安全, 2020, 20(5): 88-93. |
| [8] | 王蓉, 马春光, 武朋. 基于联邦学习和卷积神经网络的入侵检测方法[J]. 信息网络安全, 2020, 20(4): 47-54. |
| [9] | 毕新亮, 杨海滨, 杨晓元, 黄思远. 基于StarGAN的生成式图像隐写方案[J]. 信息网络安全, 2020, 20(12): 64-71. |
| [10] | 程洋, 雷敏, 罗群. 基于深度学习的物联网终端设备接入认证方法[J]. 信息网络安全, 2020, 20(11): 67-74. |
| [11] | 谢永恒, 冯宇波, 董清风, 王梅. 基于深度学习的数据接入方法研究[J]. 信息网络安全, 2019, 19(9): 36-40. |
| [12] | 马春光, 郭瑶瑶, 武朋, 刘海波. 生成式对抗网络图像增强研究综述[J]. 信息网络安全, 2019, 19(5): 10-12. |
| [13] | 方勇, 朱光夏天, 刘露平, 贾鹏. 基于深度学习的浏览器Fuzz样本生成技术研究[J]. 信息网络安全, 2019, 19(3): 26-33. |
| [14] | 朱海麒, 姜峰. 人工智能时代面向运维数据的异常检测技术研究与分析[J]. 信息网络安全, 2019, 19(11): 24-35. |
| [15] | 段大高, 谢永恒, 盖新新, 刘占斌. 基于神经网络的微博虚假消息识别模型[J]. 信息网络安全, 2017, 17(9): 134-137. |
| 阅读次数 | ||||||||||||||||||||||||||||||||||||||||||||||||||
|
全文 296
|
|
|||||||||||||||||||||||||||||||||||||||||||||||||
|
摘要 808
|
|
|||||||||||||||||||||||||||||||||||||||||||||||||