信息网络安全 ›› 2021, Vol. 21 ›› Issue (2): 53-60.doi: 10.3969/j.issn.1671-1122.2021.02.007
基于改进鲸鱼算法的工控系统入侵检测研究
- 华东理工大学化工过程先进控制和优化技术教育部重点实验室,上海 200237
-
收稿日期:2020-09-19出版日期:2021-02-10发布日期:2021-02-23 -
通讯作者:王华忠 E-mail:hzwang@ecust.edu.cn -
作者简介:王华忠(1969—),男,江苏,副教授,博士,主要研究方向为工业控制、工控信息安全|程奇(1994—),女,安徽,硕士研究生,主要研究方向为工业系统信息安全 -
基金资助:国家自然科学基金(61973119);中央高校基本科研业务费专项资金(222201917006)
Research on Intrusion Detection of Industrial Control System Based on Improved Whale Algorithm
- Key Laboratory of Advanced Control and Optimization for Chemical Processes of Ministry of Education, East China University of Science and Technology, Shanghai 200237, China
-
Received:2020-09-19Online:2021-02-10Published:2021-02-23 -
Contact:WANG Huazhong E-mail:hzwang@ecust.edu.cn
摘要:
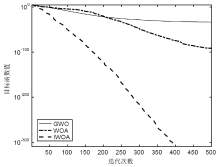
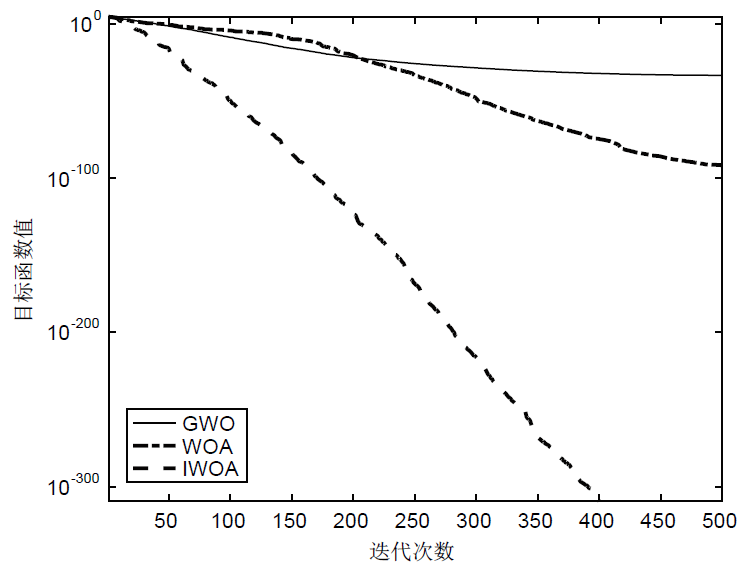
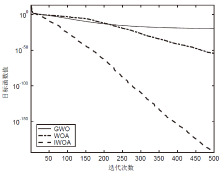
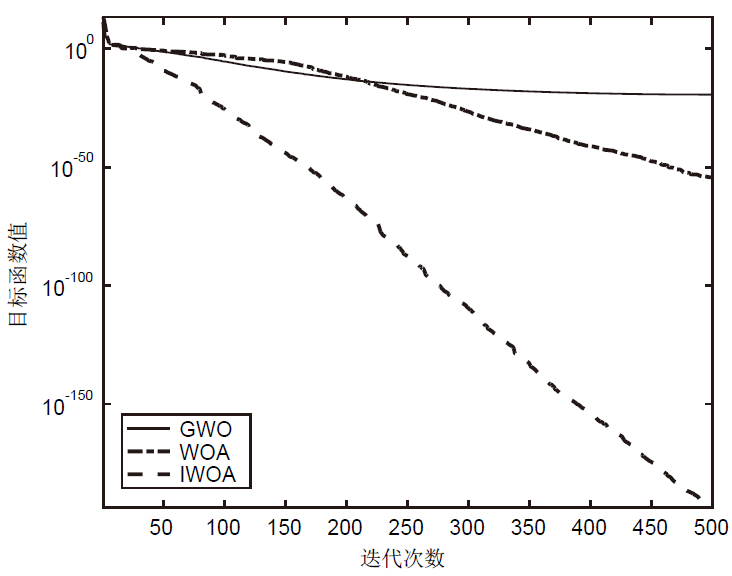
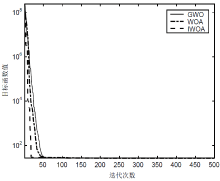
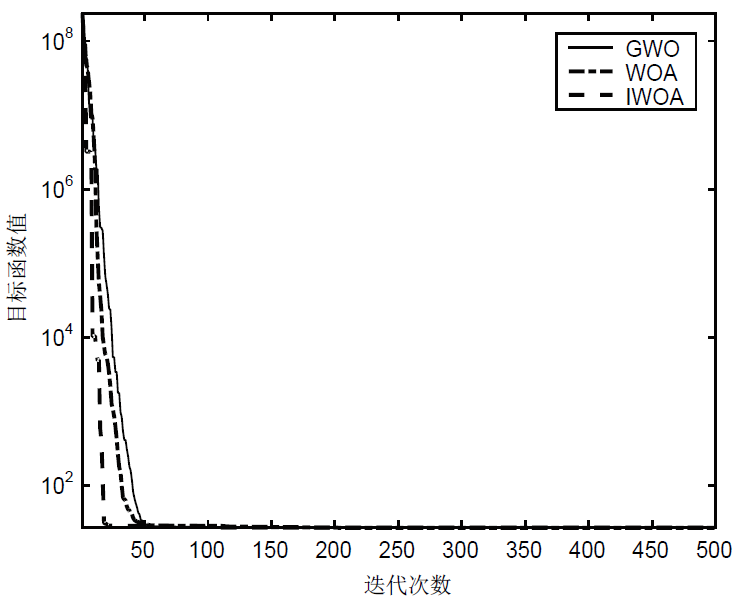
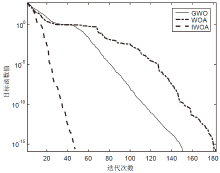
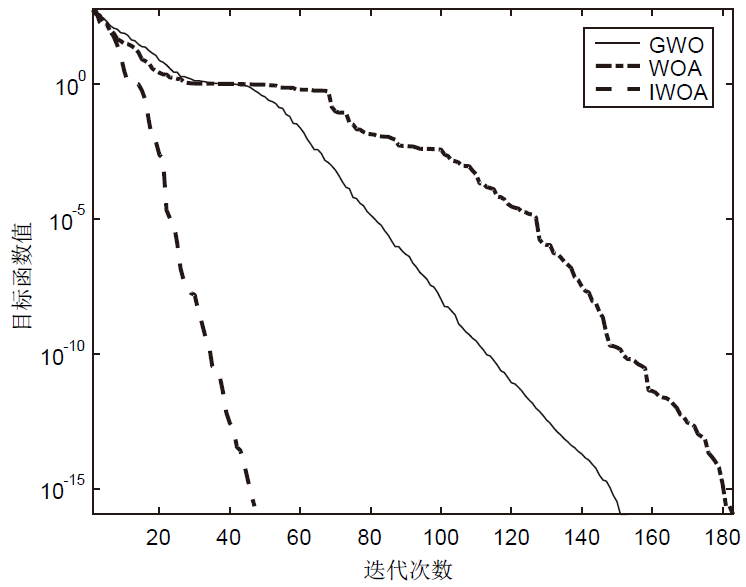
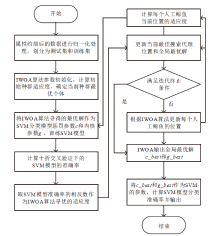
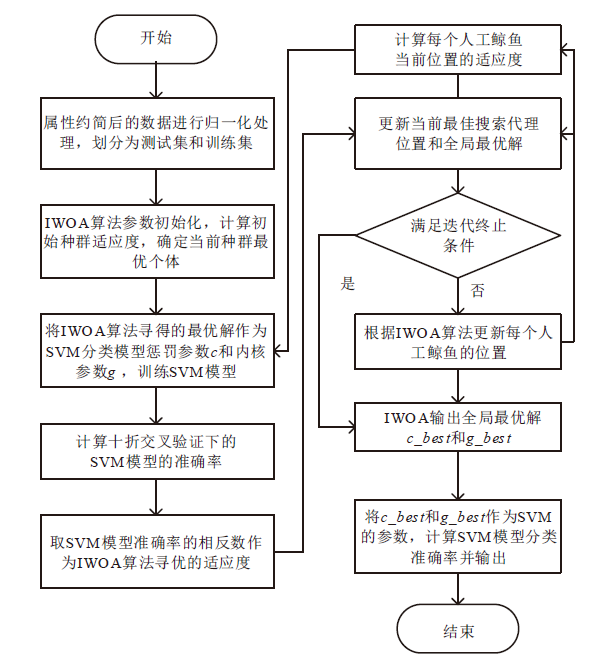
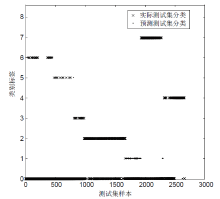
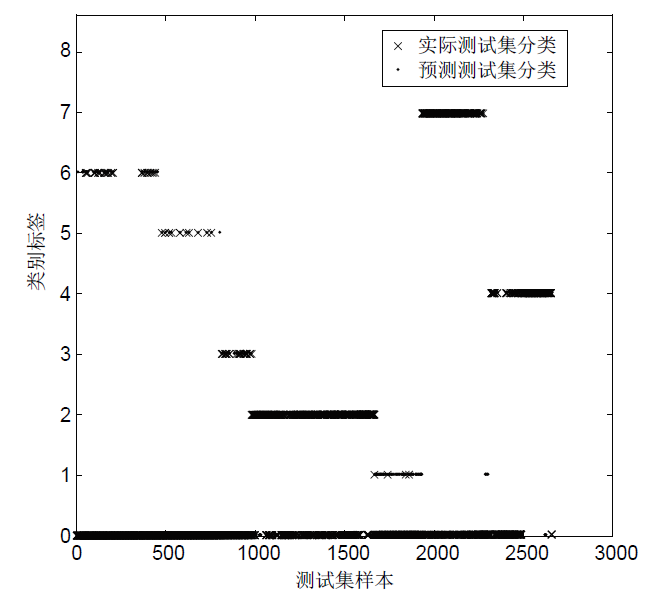
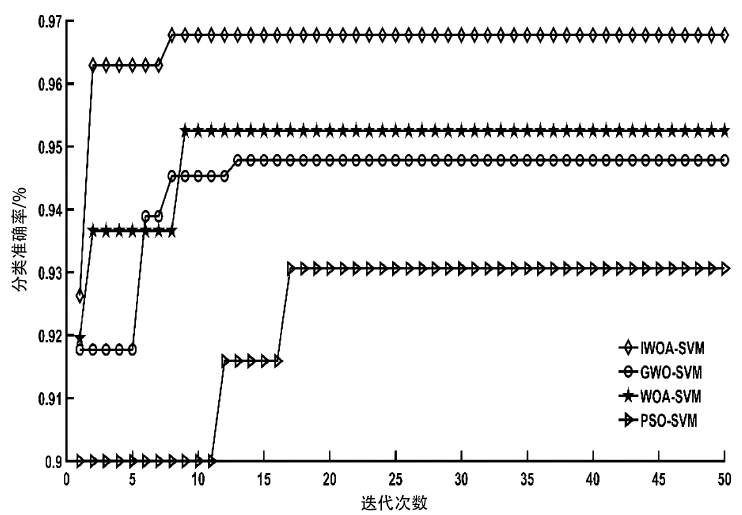
针对工控入侵检测模型训练时间长、检测率低的问题,文章提出一种改进的鲸鱼算法(IWOA)来优化SVM入侵检测模型中的参数。改进的鲸鱼算法首先引入AFSA的自适应步长和拥挤度因子,加快全局收敛速度,避免种群位置过度拥挤导致的算法早熟现象;其次,在局部搜索中加入高斯变异算子使算法跳出局部最优区域。将IWOA运用到SVM入侵检测模型参数寻优,对工控系统天然气管道数据集进行仿真,仿真结果表明,该模型检测正确率和检测速度明显提高。
中图分类号:
引用本文
王华忠, 程奇. 基于改进鲸鱼算法的工控系统入侵检测研究[J]. 信息网络安全, 2021, 21(2): 53-60.
WANG Huazhong, CHENG Qi. Research on Intrusion Detection of Industrial Control System Based on Improved Whale Algorithm[J]. Netinfo Security, 2021, 21(2): 53-60.
表1
测试函数
| 函数名 | 函数表达式 | 变量 个数 | 变量 范围 | 最小值 |
|---|---|---|---|---|
| Sphere | ${{f}_{1}}(x)=\sum\limits_{i=1}^{n}{x_{i}^{2}}$ | 30 | [-100,100] | 0 |
| Schwefel | ${{f}_{2}}(x)=\sum\limits_{i=1}^{n-1}{[100{{({{x}_{i+1}}-x_{i}^{2})}^{2}}+{{({{x}_{i}}-1)}^{2}}]}$ | 30 | [-10,10] | 0 |
| Rosenbrock | ${{f}_{3}}(x)=\sum\limits_{i=1}^{N}{[100{{({{x}_{i+1}}-x_{i}^{2})}^{2}}}+{{({{x}_{i}}-1)}^{2}}]$ | 30 | [-30,30] | 0 |
| Griewank | ${{f}_{4}}(x)=\frac{1}{4000}\sum\limits_{i=1}^{N}{x_{i}^{2}}-\prod\limits_{i=1}^{N}{\cos \left( \frac{{{x}_{i}}}{\sqrt{i}} \right)}+1$ | 30 | [-600,600] | 0 |
表1
| [1] | JIN Zhongfeng, LI Nan, LIU Chao, et al. Overview of Research on Intrusion Detection Technology of Industrial Control System[J]. Confidential Science and Technology, 2018,90(3): 20-27. |
| 金忠峰, 李楠, 刘超, 等. 工业控制系统入侵检测技术研究综述[J]. 保密科学技术, 2018,90(3): 20-27. | |
| [2] | CASELLI M, ZAMBON E, KARGL F. Sequence-aware Intrusion Detection in Industrial Control Systems[C]//I2R-ADSC. 1st ACM Workshop on Cyber-physical System Security, April 14, 2015, Singapore Republic of Singapore. New York: ACM, 2015: 13-24. |
| [3] | SONG Zhanwei, LIU Zenghui. Abnormal Detection Method of Industrial Control System Based on Behavior Model[J]. Computers and Security, 2019,84(3): 166-178. |
| [4] | QASSIM Q S, ZIN A M, AZIZ M J A. Anomalies Classification Approach for Network-based Intrusion Detection System[J]. International Journal of Network Security, 2016,18(6): 1159-1172. |
| [5] | ALJAWARNEH S, ALDWAIRI M, YASSEIN M B. Anomaly-based Intrusion Detection System Through Feature Selection Analysis and Building Hybrid Efficient Model[J]. Journal of Computational Science, 2018,25(3): 152-160. |
| [6] | WANG Linlin, LIU Jinghao, FU Xiaomei. An Intrusion Detection Method Based on Extreme Learning Machine and Modified K-means[J]. Computer Engineering and Science, 2018,40(8): 1398-1404. |
| 王琳琳, 刘敬浩, 付晓梅. 基于极限学习机与改进K-means算法的入侵检测方法[J]. 计算机工程与科学, 2018,40(8): 1398-1404. | |
| [7] | MAZINI M, SHIRAZI B, MAHDAVI I. Anomaly Network-based Intrusion Detection System Using A Reliable Hybrid Artificial Bee Colony and AdaBoost Algorithms[J]. Journal of King Saud University: Computer and Information Sciences, 2018,31(4): 541-553. |
| [8] | CHENG Dongmei, YAN Biao, WEN Hui, et al. The Design and Implement of Rule Matching-based Distributed Intrusion Detection Framework for Industry Control System[J]. Netinfo Security, 2017,17(7): 45-51. |
| [9] | CHEN Wanzhi, LIU Tianjiao, TANG Yuxu, et al. Multi-level Adaptive Coupled Method for Industrial Control Networks Safety Based on Machine Learning[J]. Safety Science, 2019,120(7): 268-275. |
| [10] | SHANG Wenli, ZENG Peng, WAN Ming, et al. Intrusion Detection Algorithm Based on OCSVM in Industrial Control System[J]. Security and Communication Networks, 2016,9(10): 1040-1049. |
| [11] | CHEN Hanyu, WANG Huazhong, YAN Bingyong. Application of SVM Based on CUDA and Cuckoo Algorithm in Industrial Control Intrusion Detection[J]. Journal of East China University of Science and Technology(Natural Science Edition), 2019,45(1): 101-109. |
| 陈汉宇, 王华忠, 颜秉勇. 基于CUDA和布谷鸟算法的SVM在工控入侵检测中的应用[J]. 华东理工大学学报(自然科学版), 2019,45(1): 101-109. | |
| [12] | YANG Zhihui, WANG Huazhong, YAN Bingyong. Research on Intrusion Detection based on Improved Particle Swarm Optimization SVM[J]. Journal of Guangxi University(Natural Science Edition), 2016,41(3): 779-785. |
| [13] | IKRAM S T, CHERUKURI A K. Improving Accuracy of Intrusion Detection Model Using PCA and Optimized SVM[J]. Journal of Computing and Information Technology, 2016,24(2): 133-148. |
| [14] | MIRJALILI S, LEWIS A. The Whale Optimization Algorithm[J]. Advances in Engineering Software, 2016,95(1): 51-67. |
| [15] | SALGOTRA R, SINGH U. Application of Mutation Operators to Flower Pollination Algorithm[J]. Expert Systems with Applications, 2017,79(2): 112-129. |
| [16] | DUAN Jie, HU Qinghua, ZHANG Lingjun, et al. Multi-label Classification Feature Selection Algorithm Based on Neighborhood Rough Set[J]. Journal of Computer Research and Development, 2015,52(1): 56-65. |
| 段洁, 胡清华, 张灵均, 等. 基于邻域粗糙集的多标记分类特征选择算法[J]. 计算机研究与发展, 2015,52(1): 56-65. | |
| [17] |
NADER P, HONEINE P, BEAUSEROY P. One-class Classification for Intrusion Detection in SCADA Systems[J]. IEEE Transactions on Industrial Informatics, 2014,10(4): 2308-2317.
doi: 10.1109/TII.2014.2330796 URL |
| [1] | 李佳玮, 吴克河, 张波. 基于高斯混合聚类的电力工控系统异常检测研究[J]. 信息网络安全, 2021, 21(3): 53-63. |
| [2] | 杜晔, 王子萌, 黎妹红. 基于优化核极限学习机的工控入侵检测方法[J]. 信息网络安全, 2021, 21(2): 1-9. |
| [3] | 沈也明, 李贝贝, 刘晓洁, 欧阳远凯. 基于主动学习的工业互联网入侵检测研究[J]. 信息网络安全, 2021, 21(1): 80-87. |
| [4] | 李桥, 龙春, 魏金侠, 赵静. 一种基于LMDR和CNN的混合入侵检测模型[J]. 信息网络安全, 2020, 20(9): 117-121. |
| [5] | 徐国天. 网络入侵检测中K近邻高速匹配算法研究[J]. 信息网络安全, 2020, 20(8): 71-80. |
| [6] | 姜楠, 崔耀辉, 王健, 吴晋超. 基于上下文特征的IDS告警日志攻击场景重建方法[J]. 信息网络安全, 2020, 20(7): 1-10. |
| [7] | 张晓宇, 王华忠. 基于改进Border-SMOTE的不平衡数据工业控制系统入侵检测[J]. 信息网络安全, 2020, 20(7): 70-76. |
| [8] | 彭中联, 万巍, 荆涛, 魏金侠. 基于改进CGANs的入侵检测方法研究[J]. 信息网络安全, 2020, 20(5): 47-56. |
| [9] | 王蓉, 马春光, 武朋. 基于联邦学习和卷积神经网络的入侵检测方法[J]. 信息网络安全, 2020, 20(4): 47-54. |
| [10] | 罗文华, 许彩滇. 基于改进MajorClust聚类的网络入侵行为检测[J]. 信息网络安全, 2020, 20(2): 14-21. |
| [11] | 何泾沙, 韩松, 朱娜斐, 葛加可. 基于改进V-detector算法的入侵检测研究与优化[J]. 信息网络安全, 2020, 20(12): 19-27. |
| [12] | 康健, 王杰, 李正旭, 张光妲. 物联网中一种基于多种特征提取策略的入侵检测模型[J]. 信息网络安全, 2019, 19(9): 21-25. |
| [13] | 冯文英, 郭晓博, 何原野, 薛聪. 基于前馈神经网络的入侵检测模型[J]. 信息网络安全, 2019, 19(9): 101-105. |
| [14] | 饶绪黎, 徐彭娜, 陈志德, 许力. 基于不完全信息的深度学习网络入侵检测[J]. 信息网络安全, 2019, 19(6): 53-60. |
| [15] | 刘敬浩, 毛思平, 付晓梅. 基于ICA算法与深度神经网络的入侵检测模型[J]. 信息网络安全, 2019, 19(3): 1-10. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||