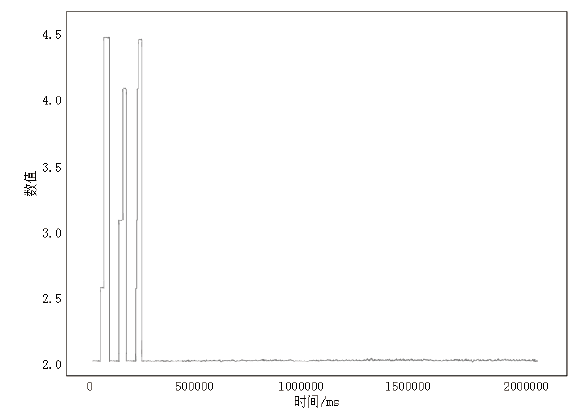
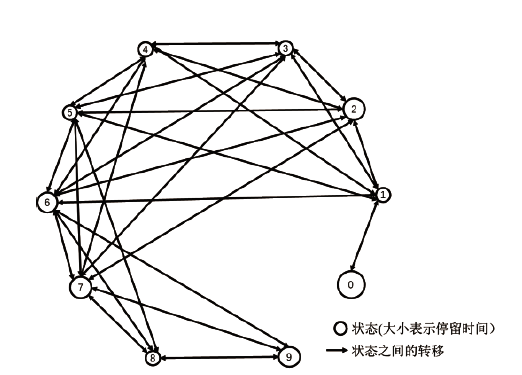
信息网络安全 ›› 2021, Vol. 21 ›› Issue (3): 53-63.doi: 10.3969/j.issn.1671-1122.2021.03.007
基于高斯混合聚类的电力工控系统异常检测研究
- 1.华北电力大学,北京 102206
2.国网北京市电力公司,北京 100031
3.全球能源互联网研究院有限公司,南京 210009
-
收稿日期:2020-12-21出版日期:2021-03-10发布日期:2021-03-16 -
通讯作者:吴克河 E-mail:wkh@ncepu.edu.cn -
作者简介:李佳玮(1989—),男,浙江,博士研究生,主要研究方向为电力信息安全|吴克河(1962—),男,江苏,教授,博士,主要研究方向为电网信息安全|张波(1985—),男,江苏,正高级工程师,博士,主要研究方向为电力信息安全、网络智能攻防 -
基金资助:国家自然科学基金(61601113)
Research on Anomaly Detection of Power Industrial Control System Based on Gaussian Mixture Clustering
LI Jiawei1,2, WU Kehe1( ), ZHANG Bo3
), ZHANG Bo3
- 1. North China Electric Power University, Beijing 102206, China
2. State Grid Beijing Electric Power Company, Beijing 100031, China
3. Global Energy Internet Research Institute Co., Ltd. Nanjing 210003, China
-
Received:2020-12-21Online:2021-03-10Published:2021-03-16 -
Contact:WU Kehe E-mail:wkh@ncepu.edu.cn
摘要:
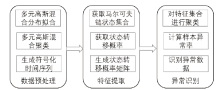
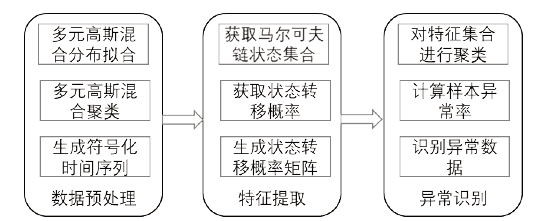
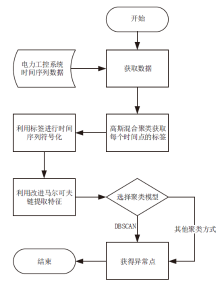
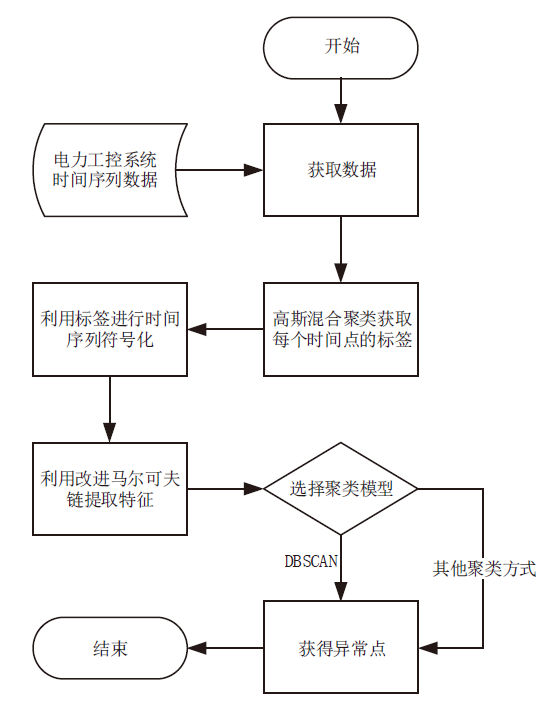
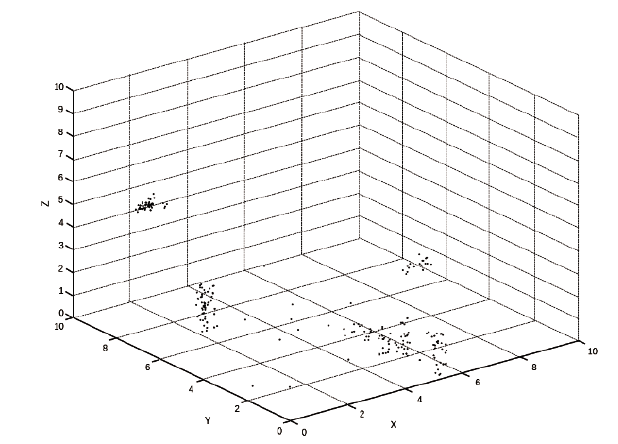
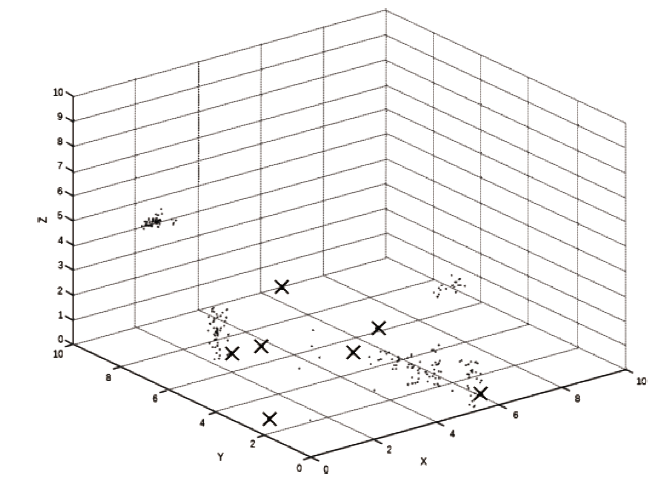
电力工控系统数据在时间维度上具有周期性,但其时间序列呈现多元高斯分布特性且周期长度不固定,这导致通过相似性度量来发现异常难以进行。针对上述问题,文章提出一种基于多元高斯聚类的电力工控系统异常时序检测方法。该方法首先获取电力工控系统流量数据,对其采用多元高斯分布混合算法实现时间序列的符号化,然后利用马尔可夫链从长度不固定的时间序列中提取出大小一致的状态转移概率矩阵作为数据特征,最后通过层次聚类方法计算样本的异常率实现异常检测。经实验分析表明,文章方法可以有效实现电力工控系统时序数据周期长度不同下的异常自动检测。
中图分类号:
引用本文
李佳玮, 吴克河, 张波. 基于高斯混合聚类的电力工控系统异常检测研究[J]. 信息网络安全, 2021, 21(3): 53-63.
LI Jiawei, WU Kehe, ZHANG Bo. Research on Anomaly Detection of Power Industrial Control System Based on Gaussian Mixture Clustering[J]. Netinfo Security, 2021, 21(3): 53-63.
使用本文
| [1] |
KEOGH E, CHAKRABARTI K, PAZZANI M, et al. Dimensionality Reduction for Fast Similarity Search in Large Time Series Databases[J]. Knowledge and Information Systems, 2001,3(3):263-286.
doi: 10.1007/PL00011669 URL |
| [2] | LIN J, KEOGH E, LONARDI S, et al. A Symbolic Representation of Time Series with Implications for Streaming Algorithms [C]//ACM. Proceedings of the 8th ACM SIGMOD Workshop on Research Issues in Data Mining and Knowledge Discovery, June 13, 2003, San Diego, CA, USA. New York: ACM, 2003: 2-11. |
| [3] | DING Xiaoou, YU Shengjian, WANG Muxian, et al. Anomaly Detection on Industrial Time Series Based on Correlation Analysis[J]. Journal of Software, 2020,31(3):726-747. |
| 丁小欧, 于晟健, 王沐贤, 等. 基于相关性分析的工业时序数据异常检测[J]. 软件学报, 2020,31(3):726-747. | |
| [4] | LI Qianmu, WANG Yinhai, PU Ziyuan, et al. Time Series Association State Analysis Method for Attacks on The Smart Internet of Electric Vehicle Charging Network[J]. Transportation Research Record, 2019,2673(4):217-228. |
| [5] | FUAD M M, MARTEAU P F. Enhancing the Symbolic Aggregate Approximation Method Using Updated Lookup Tables [C]//Springer. International Conference on Knowledge-based and Intelligent Information and Engineering Systems, September 8-10, 2010, Cardiff, UK. Berlin: Springer, 2010: 420-431. |
| [6] | BAI Xue, XIONG Yun, ZHU Yangyong, et al. Time Series Representation: A Random Shifting Perspective [C]//Springer. International Conference on Web-Age Information Management, June 14-16, Beidaihe, China. Berlin: Springer, 2013: 37-50. |
| [7] | MALINOWSKI S, GUYET T, QUINIOU R, et al. 1d-sax: A Novel Symbolic Representation for Time Series [C]//Springer. International Symposium on Intelligent Data Analysis, October 17-19, 2013, London, UK. Berlin: Springer, 2013: 273-284. |
| [8] | YIN Ning, WANG Shanshan, HONG Shenda, et al. A Segment-Wise Method for Pseudo Periodic Time Series Prediction [C]//Springer. 2014 Advanced Data Mining and Applications - 10th International Conference, December 19-21, 2014, Guilin China. Berlin, Springer, 2014: 461-474. |
| [9] | ZHAN Peng, CHEN Lin, CAO Luhui, et al. Network Traffic Anomaly Detection Based on Feature-based Symbolic Representation[J]. Journal of ZheJiang University (Engineering Science), 2020,54(7):1281-1288. |
| 展鹏, 陈琳, 曹鲁慧, 等. 基于特征符号表示的网络异常流量检测算法[J]. 浙江大学学报(工学版), 2020,54(7):1281-1288. | |
| [10] | ZHANG Chuxu, SONG Dongjin, CHEN Yuncong, et al. A Deep Neural Network for Unsupervised Anomaly Detection and Diagnosis in Multivariate Time Series Data [C]//IEEE. Proceedings of the AAAI Conference on Artificial Intelligence, February 1, 2019, Honolulu, Hawaii, USA. New York: IEEE, 2019: 1409-1416. |
| [11] | PHAM N D, LE Q L, DANG T K. Two Novel Adaptive Symbolic Representations for Similarity Search in Time Series Databases [C]//IEEE. 2010 12th International Asia-pacific Web Conference, April 6-8, 2010, Busan, Korea (South). New York: IEEE, 2010: 181-187. |
| [12] | BARNAGHI P M, BAKAR A A, OTHMAN Z A. Enhanced Symbolic Aggregate Approximation Method for Financial Time Series Data Representation [C]//IEEE. 2012 6th International Conference on New Trends in Information Science, Service Science and Data Mining (NISS2012), October 23-25, 2012, Taipei Taiwan China. New York: IEEE, 2012: 790-795. |
| [13] | PASSOS H, TEODORO F G S, DURU B M, et al. Symbolic Representations of Time Series Applied to Biometric Recognition Based on ECG Signals [C]//IEEE. 2017 International Joint Conference on Neural Networks (IJCNN), May 14, 2017, Anchorage Alaska USA. New York: IEEE, 2017: 3199-3207. |
| [14] | QI Qi, SHEN Runye, WANG Jingyu. GAD: Topology-aware Time Series Anomaly Detection[J]. Journal on Communications, 2020,41(6):152-160. |
| 戚琦, 申润业, 王敬宇. GAD:基于拓扑感知的时间序列异常检测[J]. 通信学报, 2020,41(6):152-160. | |
| [15] |
TANG Hewei, ZHANG Shang, ZHANG Feifei, et al. Time Series Data Analysis for Automatic Flow Influx Detection During Drilling[J]. Journal of Petroleum Science and Engineering, 2019,172(4):1103-1111.
doi: 10.1016/j.petrol.2018.09.018 URL |
| [16] | PHAM V, NGUYEN N, LI J, et al. Mtsad: Multivariate Time Series Abnormality Detection and Visualization [C]//IEEE. 2019 IEEE International Conference on Big Data, December 9-12, 2019, Los Angeles, CA, USA. New York: IEEE, 2019: 3267-3276. |
| [17] |
LIPPONEN J A, TARVAINEN M P. A Robust Algorithm for Heart Rate Variability Time Series Artefact Correction Using Novel Beat Classification[J]. Journal of Medical Engineering & Technology, 2019,43(3):173-181.
doi: 10.1080/03091902.2019.1640306 URL pmid: 31314618 |
| [18] | LI Dan, CHEN Dacheng, JIN Baihong, et al. MAD-GAN: Multivariate Anomaly Detection for Time Series Data With Generative Adversarial Networks [C]//Springer. International Conference on Artificial Neural Networks, September 17-19, 2019, Munich, Germany. Berlin: Springer, 2019: 703-716. |
| [19] | SU Ya, ZHAO Youjian, NIU Chenhao, et al. Robust Anomaly Detection for Multivariate Time Series Through Stochastic Recurrent Neural Network [C]//ACM. Proceedings of the 25th ACM SIGKDD International Conference on Knowledge Discovery & Data Mining, August 4-8, 2019, Anchorage AK USA. New York: ACM, 2019: 2828-2837. |
| [20] | PALPANAS T, BECKMANN V. Report on The First and Second Interdisciplinary Time Series Analysis Workshop (Itisa)[J]. ACM SIGMOD Record, 2019,48(3):36-40. |
| [1] | 陆佳丽. 基于改进时间序列模型的日志异常检测方法[J]. 信息网络安全, 2020, 20(9): 1-5. |
| [2] | 黄娜, 何泾沙, 吴亚飚, 李建国. 基于LSTM回归模型的内部威胁检测方法[J]. 信息网络安全, 2020, 20(9): 17-21. |
| [3] | 顾兆军, 任怡彤, 刘春波, 王志. 基于一致性预测算法的内网日志检测模型[J]. 信息网络安全, 2020, 20(3): 45-50. |
| [4] | 王玉娣, 刘晓洁, 王运鹏. 基于改进否定选择算法的异常检测方法研究[J]. 信息网络安全, 2020, 20(10): 75-82. |
| [5] | 王伟, 沈旭东. 基于实例的迁移时间序列异常检测算法研究[J]. 信息网络安全, 2019, 19(3): 11-18. |
| [6] | 杨威超, 郭渊博, 钟雅, 甄帅辉. 基于设备型号分类和BP神经网络的物联网流量异常检测[J]. 信息网络安全, 2019, 19(12): 53-63. |
| [7] | 朱海麒, 姜峰. 人工智能时代面向运维数据的异常检测技术研究与分析[J]. 信息网络安全, 2019, 19(11): 24-35. |
| [8] | 邓海莲, 刘宇靖, 葛一漩, 苏金树. 域间路由异常检测技术研究[J]. 信息网络安全, 2019, 19(11): 63-70. |
| [9] | 李巍, 狄晓晓, 王迪, 李云春. 基于子图的服务器网络行为建模及异常检测方法研究[J]. 信息网络安全, 2018, 18(2): 1-9. |
| [10] | 何利, 姚元辉. 基于上下文聚类的云虚拟机异常检测与识别策略[J]. 信息网络安全, 2018, 18(12): 54-65. |
| [11] | 赵刚, 姚兴仁. 基于用户画像的异常行为检测模型[J]. 信息网络安全, 2017, 17(7): 18-24. |
| [12] | 吴鑫, 严岳松, 刘晓然. 基于改进HMM的程序行为异常检测方法[J]. 信息网络安全, 2016, 16(9): 108-112. |
| [13] | 杨连群, 温晋英, 刘树发, 王峰. 一种改进的图分割算法在用户行为异常检测中的应用[J]. 信息网络安全, 2016, 16(6): 35-40. |
| [14] | 何明亮, 陈泽茂, 左进. 基于多窗口机制的聚类异常检测算法[J]. 信息网络安全, 2016, 16(11): 33-39. |
| [15] | 刘汝隽, 辛阳. 网络安全数据可视分析系统的设计与实现[J]. 信息网络安全, 2016, 16(11): 40-44. |
| 阅读次数 | ||||||||||||||||||||||||||||||||||||||||||||||||||
|
全文 183
|
|
|||||||||||||||||||||||||||||||||||||||||||||||||
|
摘要 373
|
|
|||||||||||||||||||||||||||||||||||||||||||||||||