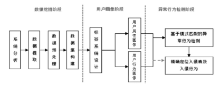
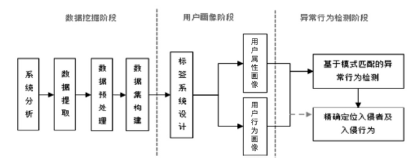
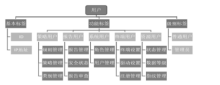
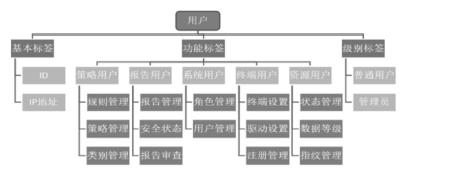
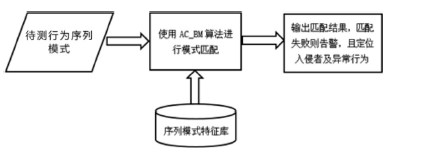
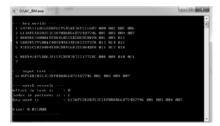
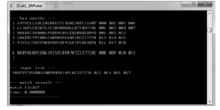
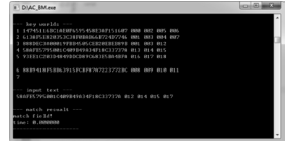
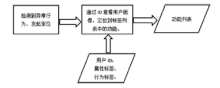
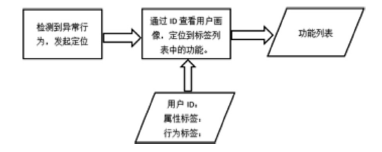
信息网络安全 ›› 2017, Vol. 17 ›› Issue (7): 18-24.doi: 10.3969/j.issn.1671-1122.2017.07.003
基于用户画像的异常行为检测模型
- 北京信息科技大学信息管理学院,北京100192
Anomaly Detection Model Based on User Portrait
- School of Information Management, Beijing Information Science & Technology University, Beijing 100192, China