信息网络安全 ›› 2019, Vol. 19 ›› Issue (10): 16-23.doi: 10.3969/j.issn.1671-1122.2019.10.003
基于短距离无线通信的物联网智能锁安全机制研究
- 天津大学电气自动化与信息工程学院,天津 300072
-
收稿日期:2019-06-15出版日期:2019-10-10发布日期:2020-05-11 -
通讯作者:李根 E-mail:ligen@tju.edu.cn -
作者简介:作者简介:金志刚(1972—),男,上海,教授,博士,主要研究方向为水下传感器网络、网络安全、社交网络与大数据;吴桐(1997—),男,辽宁,硕士研究生,主要研究方向为区块链技术、网络安全、水下无线传感器;李根(1984—),男,天津,工程师,博士,主要研究方向为车联网、网络安全与区块链。
-
基金资助:国家自然科学基金[61571318];中国博士后科学基金[2016M601265]
Research on Internet of Things Security Mechanism Based on Short Distance Wireless Communication
Zhigang JIN, Tong WU, Gen LI( )
)
- School of Electrical and Information Engineering, Tianjin University, Tianjin 300072, China
-
Received:2019-06-15Online:2019-10-10Published:2020-05-11 -
Contact:Gen LI E-mail:ligen@tju.edu.cn
摘要:
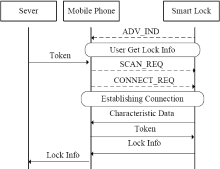
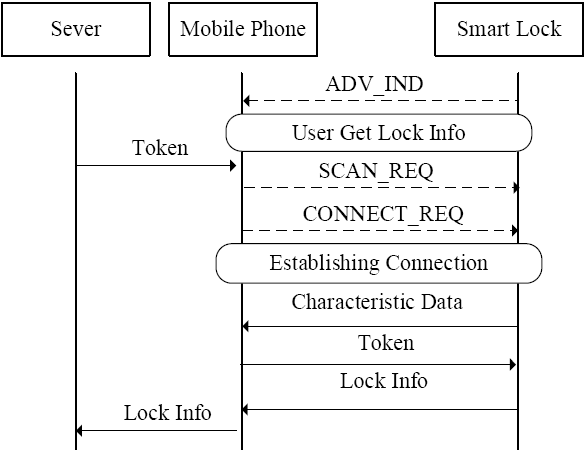
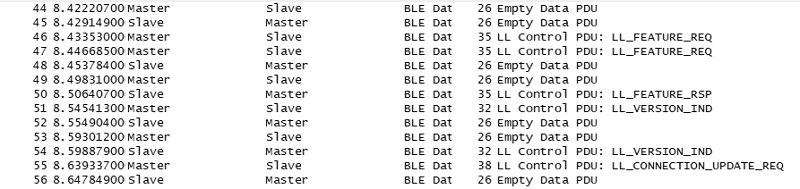
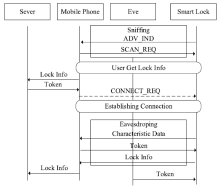
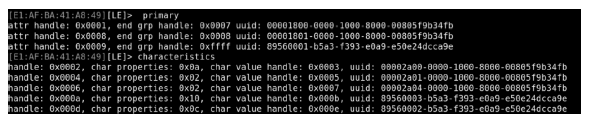
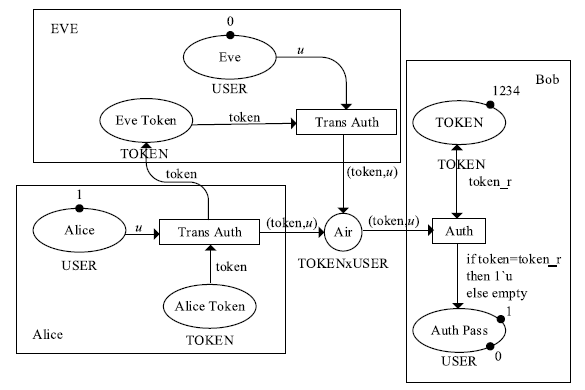
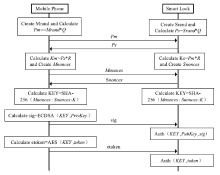
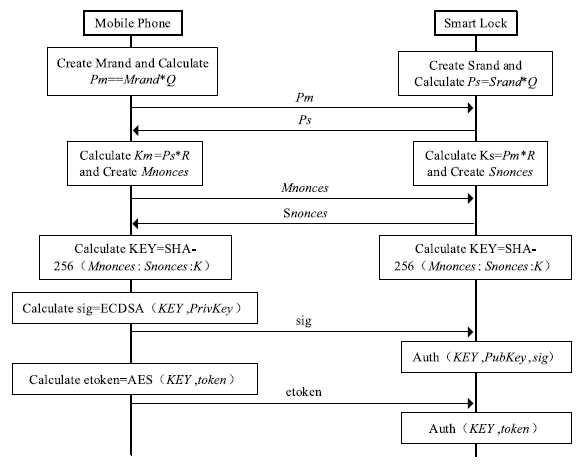
物联网领域中应用了大量的无线通信技术,由于成本等原因,其安全问题却往往被忽视。针对短距离无线通信技术在物联网设备中暴露出来的安全性问题,文章以目前物联网领域中广泛使用的智能锁为研究对象,分析了以低功耗蓝牙为例的短距离无线通信技术在物联网智能锁安全机制中的运用,使用协议分析与安全模型解析等方法研究了物联网智能锁现阶段存在的安全漏洞。同时举例描述了潜在的对物联网智能锁进行远程攻击的方法,基于CPN模型分析了物联网智能锁对非法重放攻击以及窃听攻击的抵抗性,并针对安全漏洞提出了相应的改进方法。通过利用CPN模型对加固后的通信模型进行分析,证明该模型可有效抵御非法重放攻击以及窃听攻击。
中图分类号:
引用本文
金志刚, 吴桐, 李根. 基于短距离无线通信的物联网智能锁安全机制研究[J]. 信息网络安全, 2019, 19(10): 16-23.
Zhigang JIN, Tong WU, Gen LI. Research on Internet of Things Security Mechanism Based on Short Distance Wireless Communication[J]. Netinfo Security, 2019, 19(10): 16-23.
| [1] | TANG Zejun.Future, Coming for You——“Internet of Things” Industry Research Report[EB/OL]. , 2018-11-1. |
| 唐泽俊.未来,为你而来—“物联网”行业研究报告[EB/OL]., 2018-11-1. | |
| [2] | WANG Y, ATTEBURY G, RAMAMURTHY B.A Survey of Security Issues in Wireless Sensor Networks[J]. IEEE Communications Surveys & Tutorials, 2006, 8(2): 2-23. |
| [3] | HYVONEN L, PINTO A, TROELSEN J. Near Field Pommunication: U.S. Patent 8, 212, 735[P].2012-7-3. |
| [4] | DECUIR J.Introducing Bluetooth Smart: Part 1: A look at Both Classic and New Technologies[J]. Consumer Electronics Magazine IEEE, 2014, 3(1): 12-18. |
| [5] | KAI R. Bluetooth® Low Energy, A Key Partner for Bike Sharing[EB/OL]. , 2017-4-18. |
| [6] | PALLAVI S, JORGE B. A Study of the Feasibility of Co-located App Attacks against BLE and a Large-Scale Analysis of the Current Application-Layer Security Landscape[EB/OL]. , 2018-11-1. |
| [7] | SIG D. Bluetooth Core Specification Version 4.2[EB/OL]. , 2018-11-1. |
| [8] | MINAR N B N I, TARIQUE M. Bluetooth Security Threats and Solutions: A Survey[J]. International Journal of Distributed and Parallel Systems, 2012, 3(1): 127. |
| [9] | NORDIC. nRF51 Dongle[EB/OL]., 2018-11-1. |
| [10] | OREBAUGH A, RAMIREZ G, BEALE J, et al. Wireshark & Ethereal Network Protocol Analyzer Toolkit[EB/OL]. , 2018-11-1. |
| [11] | SCARFONE K, PADGETTE J.Guide to Bluetooth Security[J]. NIST Special Publication, 2008, 800(6): 121. |
| [12] | JASEK S. GATTacking Bluetooth Smart devices, BlackHat USA 2016[EB/OL]. , 2018-11-1. |
| [13] | OLI W, FILIPPOUPOLITIS A, LOUKAS G. ImpactEvaluation and Detection of Malicious Spoofing A acks on BLE Based Occupancy Detection Systems[EB/OL]. , 2017-10-30. |
| [14] | BLUEZ, Official Linux Bluetooth Protocol Stack[EB/OL]. , 2018-11-1. |
| [15] | JENSEN K.Coloured Petri Nets: Basic Concepts, Analysis Methods and Practical Use[M]. Berlin: Springer Science & Business Media, 2013. |
| [16] | JIN Zhigang, XIE Bingshan.An Fingerprint Recognition and NFC Integrated Access Control Authentication Protocol with High Security[J]. Acta ScientiarumNaturalium Universitatis Nankaiensis, 2017, 50(5): 1-7. |
| 金志刚,解冰珊.一种高安全的融合指纹识别与NFC技术的门禁系统认证协议[J].南开大学学报(自然科学版),2017,50(5):1-7. |
| [1] | 赵志岩, 纪小默. 智能化网络安全威胁感知融合模型研究[J]. 信息网络安全, 2020, 20(4): 87-93. |
| [2] | 刘敏, 陈曙晖. 基于关联融合的VoLTE流量分析研究[J]. 信息网络安全, 2020, 20(4): 81-86. |
| [3] | 边玲玉, 张琳琳, 赵楷, 石飞. 基于LightGBM的以太坊恶意账户检测方法[J]. 信息网络安全, 2020, 20(4): 73-80. |
| [4] | 杜义峰, 郭渊博. 一种基于信任值的雾计算动态访问控制方法[J]. 信息网络安全, 2020, 20(4): 65-72. |
| [5] | 傅智宙, 王利明, 唐鼎, 张曙光. 基于同态加密的HBase二级密文索引方法研究[J]. 信息网络安全, 2020, 20(4): 55-64. |
| [6] | 王蓉, 马春光, 武朋. 基于联邦学习和卷积神经网络的入侵检测方法[J]. 信息网络安全, 2020, 20(4): 47-54. |
| [7] | 董晓丽, 商帅, 陈杰. 分组密码9轮Rijndael-192的不可能差分攻击[J]. 信息网络安全, 2020, 20(4): 40-46. |
| [8] | 郭春, 陈长青, 申国伟, 蒋朝惠. 一种基于可视化的勒索软件分类方法[J]. 信息网络安全, 2020, 20(4): 31-39. |
| [9] | 陈璐, 孙亚杰, 张立强, 陈云. 物联网环境下基于DICE的设备度量方案[J]. 信息网络安全, 2020, 20(4): 21-30. |
| [10] | 江金芳, 韩光洁. 无线传感器网络中信任管理机制研究综述[J]. 信息网络安全, 2020, 20(4): 12-20. |
| [11] | 刘建伟, 韩祎然, 刘斌, 余北缘. 5G网络切片安全模型研究[J]. 信息网络安全, 2020, 20(4): 1-11. |
| [12] | 刘鹏, 何倩, 刘汪洋, 程序. 支持撤销属性和外包解密的CP-ABE方案[J]. 信息网络安全, 2020, 20(3): 90-97. |
| [13] | 宋宇波, 樊明, 杨俊杰, 胡爱群. 一种基于拓扑分析的网络攻击流量分流和阻断方法[J]. 信息网络安全, 2020, 20(3): 9-17. |
| [14] | 王腾飞, 蔡满春, 芦天亮, 岳婷. 基于iTrace_v6的IPv6网络攻击溯源研究[J]. 信息网络安全, 2020, 20(3): 83-89. |
| [15] | 张艺, 刘红燕, 咸鹤群, 田呈亮. 基于授权记录的云存储加密数据去重方法[J]. 信息网络安全, 2020, 20(3): 75-82. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||