信息网络安全 ›› 2017, Vol. 17 ›› Issue (11): 62-66.doi: 10.3969/j.issn.1671-1122.2017.11.010
基于签名认证的DLL加载漏洞防御技术研究
- 国防科技大学计算机学院,湖南长沙 410073
-
收稿日期:2017-08-28出版日期:2017-11-20发布日期:2020-05-12 -
作者简介:作者简介: 刘峰宇(1987—), 男, 河北, 硕士研究生, 主要研究方向为操作系统和网络安全;解炜(1984—),男,湖南,助理研究员,博士,主要研究方向为物联网安全、Web安全。
-
基金资助:国家自然科学基金 [61472437]
Research on DLL Loading Vulnerability Defense Technology Based on Signature Verification
- College of Computer, National University of Defense Technology, Changsha Hunan 410073, China
-
Received:2017-08-28Online:2017-11-20Published:2020-05-12
摘要:
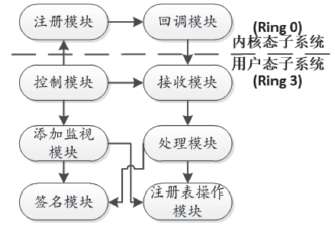
动态链接库(Dynamic Link Library,DLL)是Windows操作系统中共享函数库概念的一种实现方式,其中包含可供多个程序同时使用的代码和数据。动态链接库虽然为操作系统提供模块化的共享机制,但由于其加载机制不完善,衍生出DLL劫持等安全漏洞。文章首先提出一种利用操作系统回调机制进行DLL加载认证以抵御DLL加载漏洞攻击的技术方案;然后在Windows 7操作系统平台上实现和验证;最后分析评述该方法的实用性、稳定性和扩展性。仿真实验结果证明,文章提出的防御机制能够有效监控DLL文件的加载过程,并在近实时环境条件下监测到恶意文件加载行为。
中图分类号:
引用本文
刘峰宇, 解炜. 基于签名认证的DLL加载漏洞防御技术研究[J]. 信息网络安全, 2017, 17(11): 62-66.
Fengyu LIU, Wei XIE. Research on DLL Loading Vulnerability Defense Technology Based on Signature Verification[J]. Netinfo Security, 2017, 17(11): 62-66.
| [1] | 梅瑞,孟正,霍玮. 典型文档类CVE漏洞检测工具的研究与实现[J]. 信息网络安全,2014(6):18-22. |
| [2] | HARITHA U, NAIDU V L.A Survey on Windows Component Loading Vulnerabilities[J]. International Journal of Advanced Research in Computer Engineering & Technology (IJARCET), 2013, 2(5): 1780-1783. |
| [3] | LUK C K, COHN R, MUTH R, et al.Pin: Building Customized Program Analysis Tools with Dynamic Instrumentation[C]//ACM. Proceedings of the 2005 ACM SIGPLAN Conference on Programming Language Design and Implementation, June 12 - 15, 2005. Chicago, IL, USA.New York: ACM, 2005: 190-200. |
| [4] | 杜雷,辛阳. 基于规则库和网络爬虫的漏洞检测技术研究与实现[J]. 信息网络安全,2014(10):38-43. |
| [5] | KWON T, SU Zhendong.Automatic Detection of Unsafe Dynamic Component Loadings[J]. IEEE Transactions on Software Engineering, 2012, 38(2): 293-313. |
| [6] | 傅建明, 彭碧琛, 杜浩. 一种组件加载漏洞的动态检测[J].清华大学学报: 自然科学版, 2012, 52(10): 1356-1363. |
| [7] | KWON T, SU Zhendong.Static Detection of Unsafe Component Loadings[A]// Compiler Construction[M]. Heidelberg :Springer Berlin Heidelberg, 2012: 122-143. |
| [8] | MIN B, VARADHARAJAN V.Secure Dynamic Software Loading and Execution Using Cross Component Verification[C]//IEEE. 2015 45th Annual IEEE/IFIP International Conference on Dependable Systems and Networks (DSN), June 22-25, 2015. Rio de Janeiro, Brazil .NJ:IEEE, 2015: 113-124. |
| [9] | 关通,任馥荔,文伟平,等. 基于Windows的软件安全典型漏洞利用策略探索与实践[J]. 信息网络安全,2014(11):59-65. |
| [1] | 赵志岩, 纪小默. 智能化网络安全威胁感知融合模型研究[J]. 信息网络安全, 2020, 20(4): 87-93. |
| [2] | 刘敏, 陈曙晖. 基于关联融合的VoLTE流量分析研究[J]. 信息网络安全, 2020, 20(4): 81-86. |
| [3] | 边玲玉, 张琳琳, 赵楷, 石飞. 基于LightGBM的以太坊恶意账户检测方法[J]. 信息网络安全, 2020, 20(4): 73-80. |
| [4] | 杜义峰, 郭渊博. 一种基于信任值的雾计算动态访问控制方法[J]. 信息网络安全, 2020, 20(4): 65-72. |
| [5] | 傅智宙, 王利明, 唐鼎, 张曙光. 基于同态加密的HBase二级密文索引方法研究[J]. 信息网络安全, 2020, 20(4): 55-64. |
| [6] | 王蓉, 马春光, 武朋. 基于联邦学习和卷积神经网络的入侵检测方法[J]. 信息网络安全, 2020, 20(4): 47-54. |
| [7] | 董晓丽, 商帅, 陈杰. 分组密码9轮Rijndael-192的不可能差分攻击[J]. 信息网络安全, 2020, 20(4): 40-46. |
| [8] | 郭春, 陈长青, 申国伟, 蒋朝惠. 一种基于可视化的勒索软件分类方法[J]. 信息网络安全, 2020, 20(4): 31-39. |
| [9] | 陈璐, 孙亚杰, 张立强, 陈云. 物联网环境下基于DICE的设备度量方案[J]. 信息网络安全, 2020, 20(4): 21-30. |
| [10] | 江金芳, 韩光洁. 无线传感器网络中信任管理机制研究综述[J]. 信息网络安全, 2020, 20(4): 12-20. |
| [11] | 刘建伟, 韩祎然, 刘斌, 余北缘. 5G网络切片安全模型研究[J]. 信息网络安全, 2020, 20(4): 1-11. |
| [12] | 刘鹏, 何倩, 刘汪洋, 程序. 支持撤销属性和外包解密的CP-ABE方案[J]. 信息网络安全, 2020, 20(3): 90-97. |
| [13] | 宋宇波, 樊明, 杨俊杰, 胡爱群. 一种基于拓扑分析的网络攻击流量分流和阻断方法[J]. 信息网络安全, 2020, 20(3): 9-17. |
| [14] | 王腾飞, 蔡满春, 芦天亮, 岳婷. 基于iTrace_v6的IPv6网络攻击溯源研究[J]. 信息网络安全, 2020, 20(3): 83-89. |
| [15] | 张艺, 刘红燕, 咸鹤群, 田呈亮. 基于授权记录的云存储加密数据去重方法[J]. 信息网络安全, 2020, 20(3): 75-82. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||