信息网络安全 ›› 2015, Vol. 15 ›› Issue (2): 33-39.doi: 10.3969/j.issn.1671-1122.2015.02.006
星际骨干网的轻量级密码体制研究
- 1.上海大学特种光纤与光接入网省部共建重点实验室 上海 200072
2.上海市信息安全测评中心,上海 200011
-
收稿日期:2015-01-15出版日期:2015-02-10发布日期:2015-07-05 -
作者简介:作者简介: 侯玉灵(1989-),女,河南,硕士研究生,主要研究方向:量子人工智能算法与密码学;卞阳东(1993-),男,上海,本科,主要研究方向:跳频通信编码;胡广跃(1987-),男,江苏,硕士,主要研究方向:网络信息安全;王潮(1971-),男,山东,教授,博士,主要研究方向:无线传感器网络、网络信息安全与椭圆曲线密码学、量子计算密码。
-
基金资助:国家自然科学基金[61272096,6097006,61332019];上海市教委创新基金重点项目[14ZZ089]
Research on Lightweight Cryptography of Interplanetary Backbone Networks
HOU Yu-ling1, BIAN Yang-dong1, HU Guang-yue2, WANG Chao1( )
)
- 1. Key Lab of Specialty Fiber Optics and Optical Access Network, Shanghai University, Shanghai 200072, China
2. Information Security Assessment Center of Shanghai, Shanghai 200011, China
-
Received:2015-01-15Online:2015-02-10Published:2015-07-05
摘要:
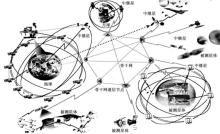
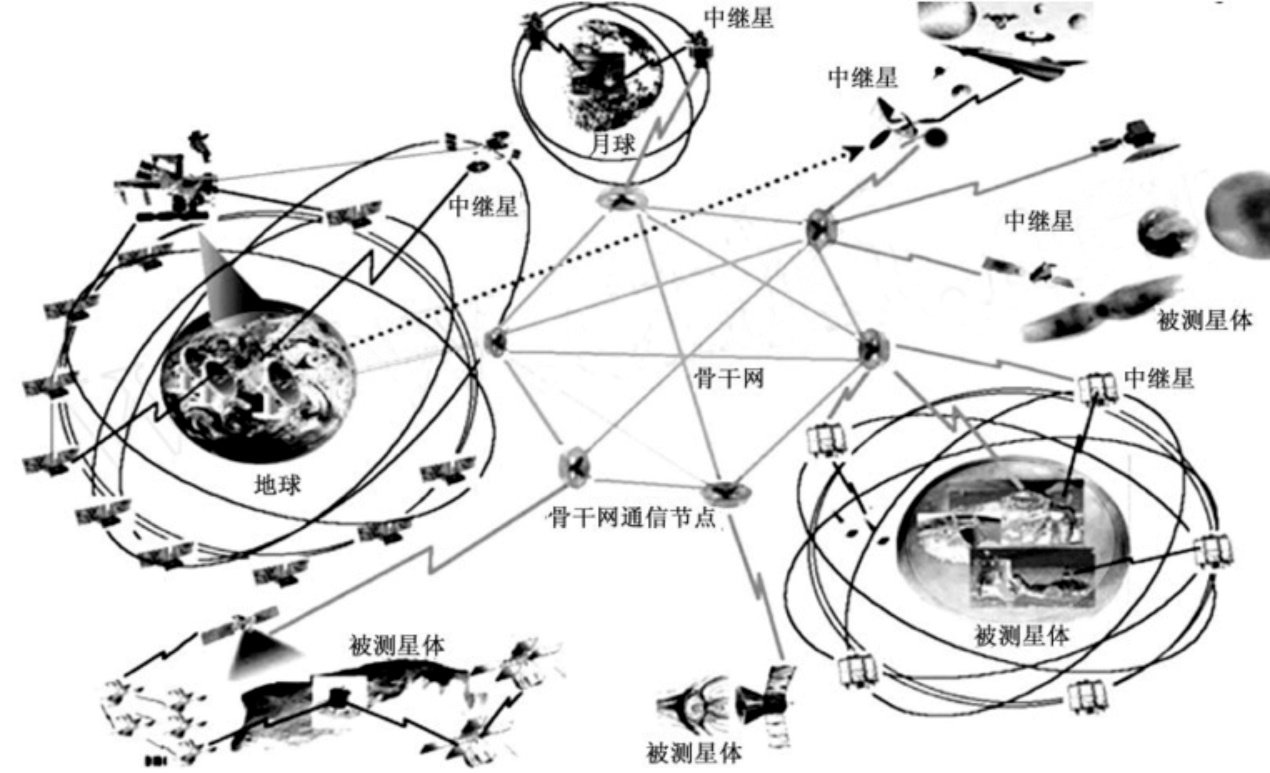
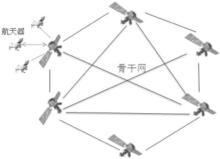
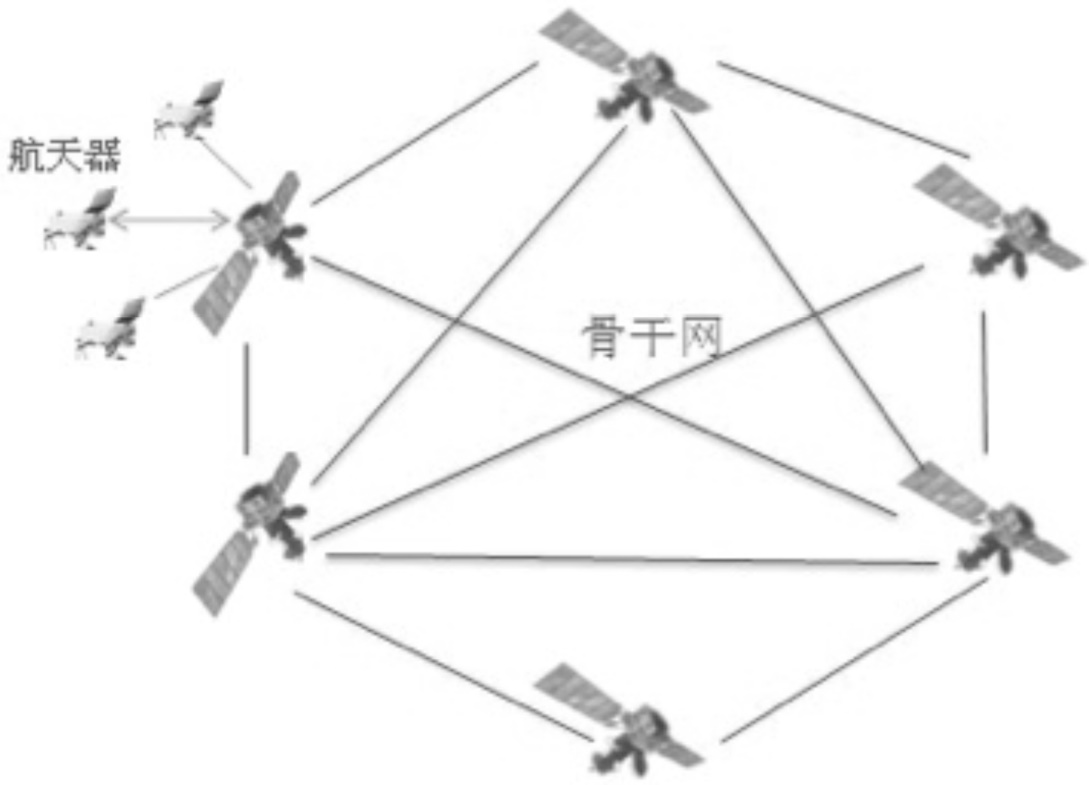
现有的空间网络安全方案存在缺乏对星际骨干网组网安全的考虑、缺乏对星际骨干网的节点特别是中继站的双向认证以及密钥管理和认证效率不高、密码计算复杂度较高等问题而不适合星际骨干网。文章结合深空通信的特点,提出了星际骨干网的轻量级密码体制和安全算法。为了解决遭遇恶意节点的问题,文章提出了基于门限秘密共享机制的思想;为了保证普通航天器与卫星间的通信安全,采用了双向认证的方式,由于认证过程简单高效,加上使用轻量化ECC算法设计,从而加速了点乘运算,减少了认证过程中的计算开销和通信开销;采用基于ECC的CPK体制的思想,在无需第三方的参与下,即可实现高效的认证过程,安全性依赖于椭圆离散对数分解的指数级破译计算复杂度;利用少量的公/私钥矩阵,生成大规模的公/私钥对;采用双向认证的方式,保证普通航天器与卫星间的通信安全,抵御中间人攻击。
中图分类号:
引用本文
侯玉灵, 卞阳东, 胡广跃, 王潮. 星际骨干网的轻量级密码体制研究[J]. 信息网络安全, 2015, 15(2): 33-39.
HOU Yu-ling, BIAN Yang-dong, HU Guang-yue, WANG Chao. Research on Lightweight Cryptography of Interplanetary Backbone Networks[J]. Netinfo Security, 2015, 15(2): 33-39.
使用本文
| [1] | 马强,辛爽.互联网的起源与未来[J].中国计算机学会通讯,2013,9(12):6-10. |
| [2] | OUYANG Z Y, LI C L, ZOU Y L, et al.Evolvement of deep space exploration and strategy of our country's deep space exploration[J]. Aerospace China, 2002, (12): 28-32. |
| [3] | LUAN E J.Shenzhou-5 and strategy of China's astronautic developments[C]//Forum of China&s Science and Humanities, 2003, 11. |
| [4] | 甘仲民. 深空通信[J]. 数字通信世界,2005,(6):36-42. |
| [5] | 沈荣骏. 我国天地一体化航天互联网构想[J].中国工程科学,2006,8(10):1930. |
| [6] | 张乃通,李晖,张钦宇. 深空探测通信技术发展趋势及思考[J]. 宇航学报,2007,(4):786-493. |
| [7] | BURLEIGH S, HOOKE A, TORGERSON, et al. Delay-tolerant networking: An approach to interplanetary internet[J].IEEE Communications Magazine, 2003, 41(6): 128-136. |
| [8] | RFC 4838 Delay-Tolerant Network Architecture[S]. IETF, 2007. |
| [9] | RFC 5050 Bundle Protocol Specification[S]. IETF, 2007. |
| [10] | WOOD L, IVANCICL W.Use of the delay-tolerant networking bundle protocol from space[C]//59th International Astronautical Congress. Glasgrow, Britain, 2008: 1-11. |
| [11] | LINDGREN A, DORIA A.Networking in the Land of Northern Lights-Two Years of Experiences from DTN System Deployments [C]//Proceedings of the 2008 ACM Workshop on Wireless Networks and Systems for Developing Regions. San Francisco, California, USA: ACM, 2008: 1-7. |
| [12] | BALASUBRAMANIAN A, MAHAJAN R.Interactive WiFi Connectivity for Moving Vehicles[C]//Proceedings of SIGCOMM’08. Seattle, WaShington, USA: ACM, 2008: 427-438. |
| [13] | LIU T, CHRISTOPHER M S, ZHANG P.Implementing software on resource-constrained mobile sensors: experiences with Impala and ZebraNet[C]//Proceedings of 2nd International Conference on Mobile system, Application, and Services, Boston, USA: ACM, 2004: 256-269. |
| [14] | HAAS Z J, SMALL T.A New Networking Model for Biological Applications of Ad Hoc Sensor Networks[J]. IEEE Transactions on Networking, 2006, 14(1): 27-40. |
| [15] | HOOKE A.The interplanetary internet[J]. Communication of the ACM, 2001, 44(9): 38-40. |
| [16] | 陈垣毅,郑增威. 星际网络通信协议研究进展综述[J]. 计算机应用研究,2011,28(2):406-412. |
| [17] | DELRE E, PIERUCCI L.Next-generation mobile satellite networks[J]. IEEE Communications Magazine, 2002, 40(9): 150-159. |
| [18] | BHASIN K, HAYDEN J L.Space Internet Architectures and Technologies for NASA Enterprises[J]. International Journal of Satellite Communications, 2002, 20(5): 311-332. |
| [19] | BALASUBRAMANIANL A, MISHRA S.Secure Key Management for NASA Space Communication[C]//ICNS Conference, 2005. |
| [20] | 罗长远,李伟,霍士伟. 基于身份的空间网络组密钥管理方案[J]. 通信学报,2010,31(12):104-110. |
| [21] | FANTACCI R, CHITI F, MACCARI L.Fast Distributed Bi-Directional Authentication for Wireless Sensor Networks[J]. Security and Communication Networks, 2008, 1(1): 17-24. |
| [22] | HAN K, SHON T, KIM K.Efficient Mobile Sensor Authentication in Smart Home and WPAN[J]. IEEE Transactions on Consumer Electronics, 2010, 56(2). 591-596. |
| [23] | HAN K, KIM K, SHON T.Untraceable Mobile Node Authentication in WSN[J]. Sensors, 2010, 10(5): 4410-4429. |
| [24] | 南湘浩. 组合公钥(CPK)体制标准(v5.0)[J]. 计算机安全,2010,(10):1-2. |
| [25] | 王潮,时向勇,牛志华. 基于Montgomery 曲线改进ECDSA算法的研究[J]. 通信学报,2010,31(1):9-13. |
| [26] | 王潮,时向勇,朱美丽.基于ECC的CBTC无线接入安全认证架构研究[C]//第十三届全国容错计算学术会议论文集,2009. |
| [27] | OKEYA K, SAKURAI K.A scalar multiplication algorithm with recovery of y-coordinate on the Montgomery form and analysis of efficiency for elliptic curve cryptosystem[J]. IEICE Trans Fundamental, 2002, 85(1): 84-93. |
| [28] | FUTA Y, OHMORI M.Efficient scalar Multiplication on Montgomery-form elliptic curves[J]. IEICE Transactions on Fundamentals of Electronics, Communications and Computer Sciences, 2004, 87(8): 2126-2136. |
| [29] | LIU D, DAI Y Q.The algorithm of computing kP+mQ+lR on a Montgomery-form elliptic curve[C]//Chinese National Conference of Computer 2003, Beijing: Tsinghua University Press, 2003. |
| [1] | 黄旺旺, 周骅, 王代强, 赵麒. 基于国密SM9的物联网可重构密钥安全认证协议设计[J]. 信息网络安全, 2024, 24(7): 1006-1014. |
| [2] | 张晓均, 张楠, 郝云溥, 王周阳, 薛婧婷. 工业物联网系统基于混沌映射三因素认证与密钥协商协议[J]. 信息网络安全, 2024, 24(7): 1015-1026. |
| [3] | 胡丞聪, 胡红钢. 基于格的最优轮数口令认证秘密共享协议[J]. 信息网络安全, 2024, 24(6): 937-947. |
| [4] | 沈卓炜, 汪仁博, 孙贤军. 基于Merkle树和哈希链的层次化轻量认证方案[J]. 信息网络安全, 2024, 24(5): 709-718. |
| [5] | 石润华, 杨婧怡, 王鹏博, 刘华伟. V2G中基于区块链的在线/离线跨域身份认证方案[J]. 信息网络安全, 2024, 24(4): 587-601. |
| [6] | 杨杰超, 胡汉平, 帅燕, 邓宇昕. 基于时变互耦合双混沌系统的轻量级序列密码[J]. 信息网络安全, 2024, 24(3): 385-397. |
| [7] | 翟鹏, 何泾沙, 张昱. 物联网环境下基于SM9算法和区块链技术的身份认证方法[J]. 信息网络安全, 2024, 24(2): 179-187. |
| [8] | 张敏, 冯永强, 许春香, 张建华. 智能家居网络下基于多因子的认证密钥协商方案[J]. 信息网络安全, 2024, 24(1): 133-142. |
| [9] | 戴玉, 周非, 薛丹. 基于中国剩余定理秘密共享的切换认证协议[J]. 信息网络安全, 2023, 23(9): 118-128. |
| [10] | 张伟, 李子轩, 徐晓瑀, 黄海平. SDP-CoAP:基于软件定义边界的安全增强CoAP通信框架设计[J]. 信息网络安全, 2023, 23(8): 17-31. |
| [11] | 黄杰, 何城鋆. 基于软件定义边界的服务保护方案[J]. 信息网络安全, 2023, 23(6): 1-10. |
| [12] | 秦宝东, ,陈从正, ,何俊杰, 郑东. 基于可验证秘密共享的多关键词可搜索加密方案[J]. 信息网络安全, 2023, 23(5): 32-40. |
| [13] | 谭伟杰, 杨雨婷, 牛坤, 彭长根. 基于MI-PUF的V2X车联网通信安全认证协议[J]. 信息网络安全, 2023, 23(12): 38-48. |
| [14] | 张敏, 许春香, 张建华. 无人机网络中基于多因子的认证密钥协商协议研究[J]. 信息网络安全, 2022, 22(9): 21-30. |
| [15] | 张学旺, 刘宇帆. 可追踪身份的物联网感知层节点匿名认证方案[J]. 信息网络安全, 2022, 22(9): 55-62. |
| 阅读次数 | ||||||||||||||||||||||||||||||||||||||||||||||||||
|
全文 31
|
|
|||||||||||||||||||||||||||||||||||||||||||||||||
|
摘要 536
|
|
|||||||||||||||||||||||||||||||||||||||||||||||||