信息网络安全 ›› 2015, Vol. 15 ›› Issue (2): 26-32.doi: 10.3969/j.issn.1671-1122.2015.02.005
基于OpenFlow的SDN网络安全分析与研究
- 国防信息学院,湖北武汉 430010
-
收稿日期:2014-11-13出版日期:2015-02-10发布日期:2015-07-05 -
作者简介:作者简介: 左青云(1986-),男,湖北,讲师,博士,主要研究方向:软件定义网络、信息资源管理;张海粟(1982-),男,安徽,讲师,博士,主要研究方向:数据挖掘。
-
基金资助:国家自然科学基金[61379149]
Analysis and Research on Network Security for OpenFlow-based SDN
- PLA Academy of National Defense Information, Wuhan Hubei 430010, China
-
Received:2014-11-13Online:2015-02-10Published:2015-07-05
摘要:
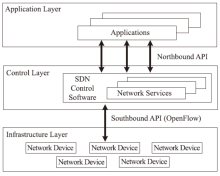
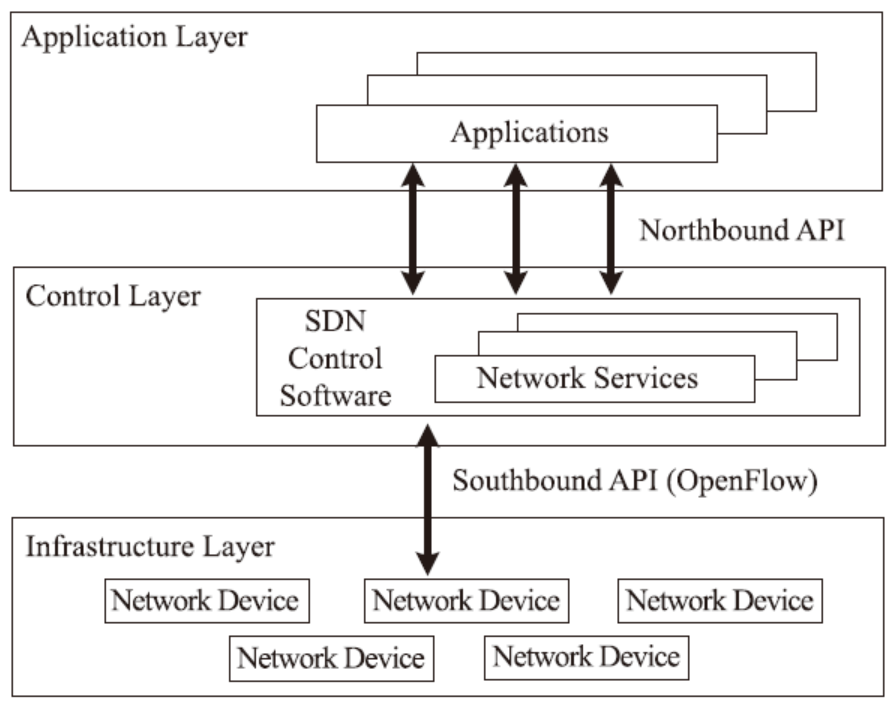
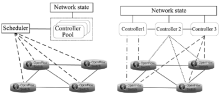
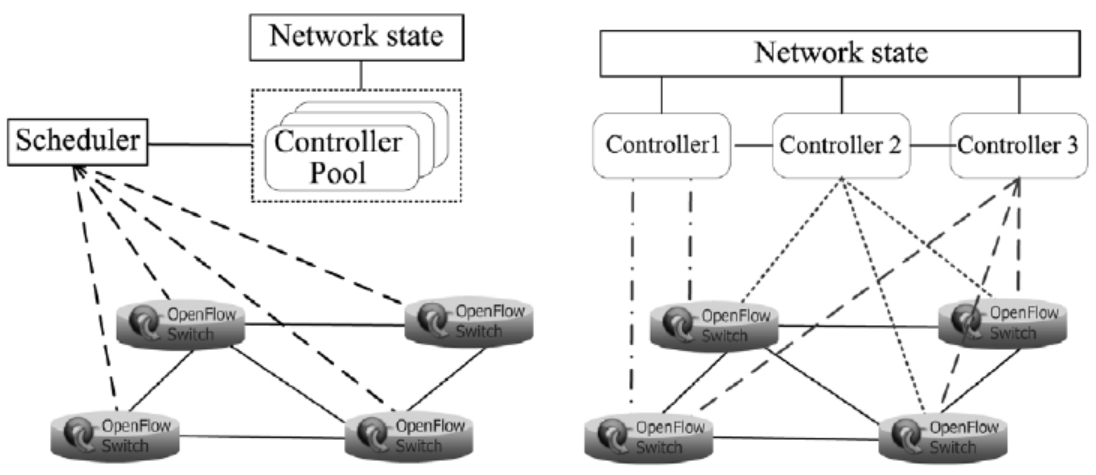
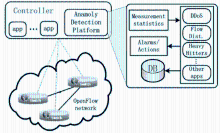
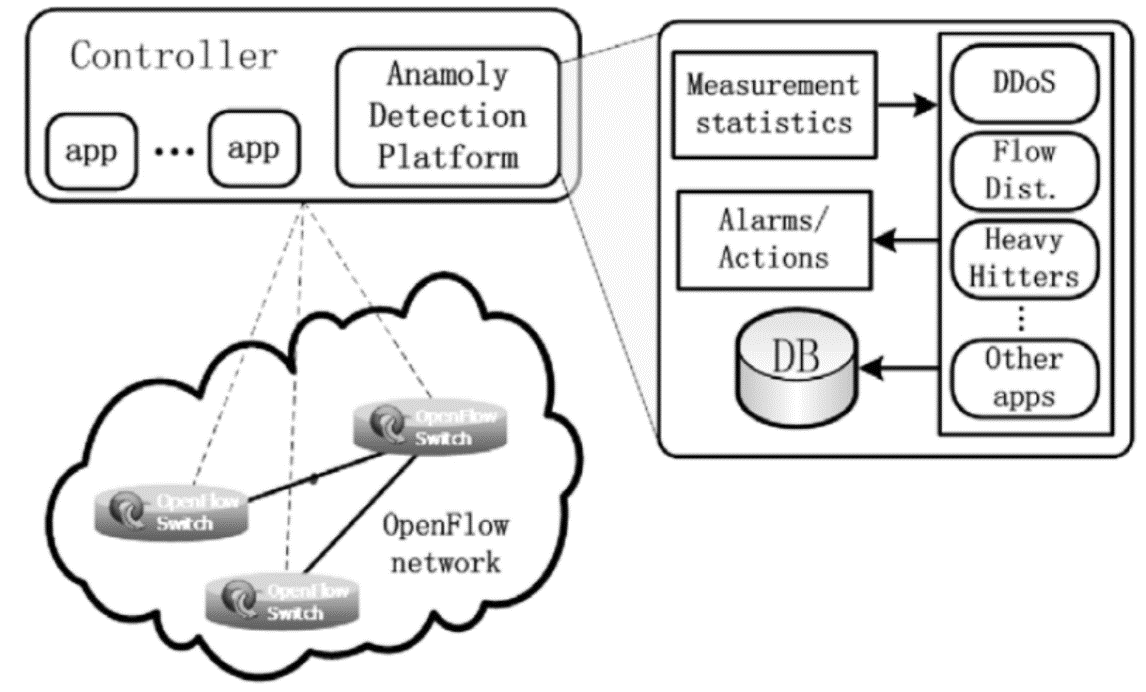
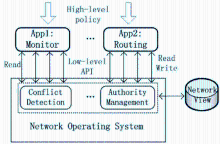
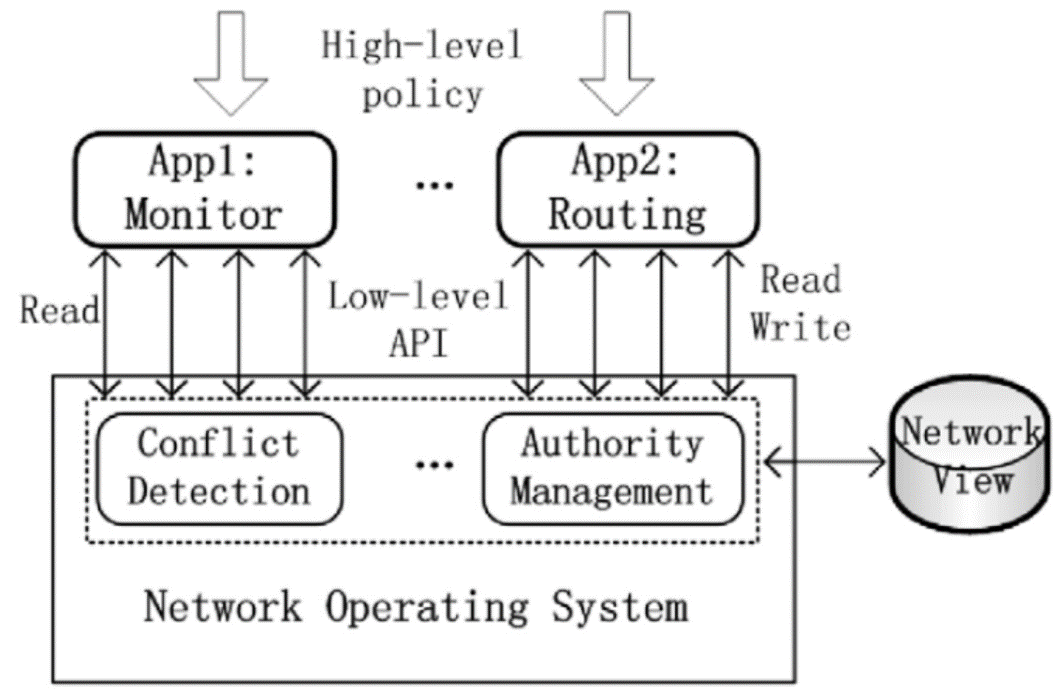
基于OpenFlow的SDN技术将网络的数据平面和控制平面相分离,通过部署中央控制器来实现对网络的管控,为未来网络的发展提供了一种新的解决思路。然而,这种新型网络管控方法与传统网络在分布式控制平面上通过封闭网络设备进行管控的方法有着根本区别,因而在实现集中化管理的同时将引入新的管理和安全问题。文章首先介绍了其三层架构的自身缺陷和可能存在的安全问题,并从SDN架构的基础设施层、南向接口、控制层、北向接口和应用层等几个方面分别进行分析,总结出SDN不同层次存在安全问题的原因;随后,文章从认证机制、控制层的备份和恢复、网络异常识别和防御机制、应用隔离和权限管理等四个方面总结了当前的相关研究进展和研究思路,并提出了可行的解决方案;最后,对全文进行总结和展望。
中图分类号:
引用本文
左青云, 张海粟. 基于OpenFlow的SDN网络安全分析与研究[J]. 信息网络安全, 2015, 15(2): 26-32.
ZUO Qing-yun, ZHANG Hai-su. Analysis and Research on Network Security for OpenFlow-based SDN[J]. Netinfo Security, 2015, 15(2): 26-32.
| [1] | Mckeown N, Anderson T, Balakrishnan H, et al.OpenFlow: Enabling Innovation in Campus Networks[J]. ACM SIGCOMM Computer Communication Review 2008, 38(2): 69-74. |
| [2] | Kreutz D, Ramos F, Verissimo P.Towards Secure and Dependable Software-Defined Networks[C]// HotSDN. 2013: 55-60. |
| [3] | Benton K, Camp L, Small C.OpenFlow Vulnerability Assessment[C]// HotSDN. 2013: 151-152. |
| [4] | Shin S, Gu G.Attacking Software-Defined Networks: A First Feasibility Study[C]//HotSDN. 2013: 165-166. |
| [5] | Koponen T, Casado M, Gude N, et al.Onix: A Distributed Control Platform for Large-scale Production Networks[C]//Proc. of the 9th USENIX conference on Operating Systems Design and Implementation (OSDI). Vancouver: USENIX Association, 2010: 1-6. |
| [6] | Open Networking Foundation[EB/OL]., 2014-03-10. |
| [7] | Gude N, Koponen T, Pettit J, et al.Nox: Towards an operating system for networks[J]. ACM Computer Communication Review, 2008, 38(3):105-110. |
| [8] | Sharma S, Staessens D, Colle D, et al.OpenFlow: Meeting carrier-grade recovery requirements[J]. Computer communications. 2012, 36(6):656-665. |
| [9] | Kuzniar M, Peresini P, Vasic N, et al.Automatic Failure Recovery for Software-Defined Networks[C]//HotSDN. 2013:159-160. |
| [10] | Kozat U, Liang G, Kokten K.Verifying Forwarding Plane Connectivity and Locating Link Failures using Static Rules in Software Defined Networks[C]//HotSDN. 2013:157-158. |
| [11] | Tootoonchian A, Ganjali Y.HyperFlow:A Distributed Control Plane for OpenFlow[C] //Proceeding of Internet Network Management Workshop/Workshop on Research on Enterprise Networking (INM/WREN), 2010:3-3. |
| [12] | Yeganeh S, Ganjali Y.Kandoo: A Framework for Efficient and Scalable Offloading of Control Applications[C]//HotSDN, 2012: 19-24. |
| [13] | Dixit A, Hao F, Mukherjee S, et al.Towards an Elastic Distributed SDN Controller[C]//HotSDN. 2013:7-12. |
| [14] | Pfaff B, Pettit J, Koponen T, Amidon K, Casado M, Shenker S.Extending Networking into the Virtualization Layer[C]//Proc. of the 7th ACM SIGCOMM Workshop on Hot Topics in Networks (HotNets), 2009. |
| [15] | Mehdi S, Khalid J, Khayam S. Revisiting Traffic Anomaly Detection Using Software Defined Networking[C]//Proc of the 14th International Conference on Recent Advances in Intrusion Detection (RAID), 2011:161-180. |
| [16] | Shin S, Porras P, Yegneswaran V, et al.FRESCO: Modular Composable Security Services for Software-Defined Networks[C]// NDSS, 2013. |
| [17] | Jose L, Yu M, Rexford J.Online Measurement of Large Traffic Aggregates on Commodity Switches[C]//Proc of the 11th USENIX Conference on Hot Topics in Management of Internet, Cloud, and Enterprise Networks and Services (Hot-ICE), 2011:13-13. |
| [18] | Braga R, Mota E, Passito A. Lightweight DDoS Flooding Attack Detection Using NOX/OpenFlow[C]//IEEE 35th Conference on Local Computer Networks (LCN), 2010:408-415. |
| [19] | Shahreza S, Ganjali Y.FleXam: Flexible Sampling Extension for Monitoring and Security Applications in OpenFlow[C]//HotSDN. 2013:167-168. |
| [20] | Canini M, Venzano D, Peresini P, et al.A NICE way to test OpenFlow applications[C]//Proc. of the 9th USENIX Symp. on Networked Systems Design and Implementation (NSDI), 2012:10. |
| [21] | Sherwood R, Gibb G, Yap K, et al.Can the production network be the testbed?[C] //Proc. of the 9th USENIX Conf.on Operating Systems Design and Implementation (OSDI), 2010:1-6. |
| [22] | Porras P, Shin S, Yegneswaran V.A Security Enforcement Kernel for OpenFlow Networks[C]//HotSDN, 2012:121-126. |
| [23] | Wen X, Chen Y, Hu C.Towards a Secure Controller Platform for OpenFlow Applications[C]//HotSDN, 2013:171-172. |
| [24] | Foster N, Guha A, Reitblatt M, et al.Languages for Software-Defined Networks[J]. IEEE communications magazine. 2013, 51(2):128-134. |
| [1] | 黄旺旺, 周骅, 王代强, 赵麒. 基于国密SM9的物联网可重构密钥安全认证协议设计[J]. 信息网络安全, 2024, 24(7): 1006-1014. |
| [2] | 张晓均, 张楠, 郝云溥, 王周阳, 薛婧婷. 工业物联网系统基于混沌映射三因素认证与密钥协商协议[J]. 信息网络安全, 2024, 24(7): 1015-1026. |
| [3] | 胡丞聪, 胡红钢. 基于格的最优轮数口令认证秘密共享协议[J]. 信息网络安全, 2024, 24(6): 937-947. |
| [4] | 沈卓炜, 汪仁博, 孙贤军. 基于Merkle树和哈希链的层次化轻量认证方案[J]. 信息网络安全, 2024, 24(5): 709-718. |
| [5] | 石润华, 杨婧怡, 王鹏博, 刘华伟. V2G中基于区块链的在线/离线跨域身份认证方案[J]. 信息网络安全, 2024, 24(4): 587-601. |
| [6] | 翟鹏, 何泾沙, 张昱. 物联网环境下基于SM9算法和区块链技术的身份认证方法[J]. 信息网络安全, 2024, 24(2): 179-187. |
| [7] | 赵鹏程, 于俊清, 李冬. 一种基于深度学习的SRv6网络流量调度优化算法[J]. 信息网络安全, 2024, 24(2): 272-281. |
| [8] | 张敏, 冯永强, 许春香, 张建华. 智能家居网络下基于多因子的认证密钥协商方案[J]. 信息网络安全, 2024, 24(1): 133-142. |
| [9] | 戴玉, 周非, 薛丹. 基于中国剩余定理秘密共享的切换认证协议[J]. 信息网络安全, 2023, 23(9): 118-128. |
| [10] | 张伟, 李子轩, 徐晓瑀, 黄海平. SDP-CoAP:基于软件定义边界的安全增强CoAP通信框架设计[J]. 信息网络安全, 2023, 23(8): 17-31. |
| [11] | 黄杰, 何城鋆. 基于软件定义边界的服务保护方案[J]. 信息网络安全, 2023, 23(6): 1-10. |
| [12] | 谭伟杰, 杨雨婷, 牛坤, 彭长根. 基于MI-PUF的V2X车联网通信安全认证协议[J]. 信息网络安全, 2023, 23(12): 38-48. |
| [13] | 王智, 张浩, 顾建军. SDN网络中基于联合熵与多重聚类的DDoS攻击检测[J]. 信息网络安全, 2023, 23(10): 1-7. |
| [14] | 张敏, 许春香, 张建华. 无人机网络中基于多因子的认证密钥协商协议研究[J]. 信息网络安全, 2022, 22(9): 21-30. |
| [15] | 张学旺, 刘宇帆. 可追踪身份的物联网感知层节点匿名认证方案[J]. 信息网络安全, 2022, 22(9): 55-62. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||