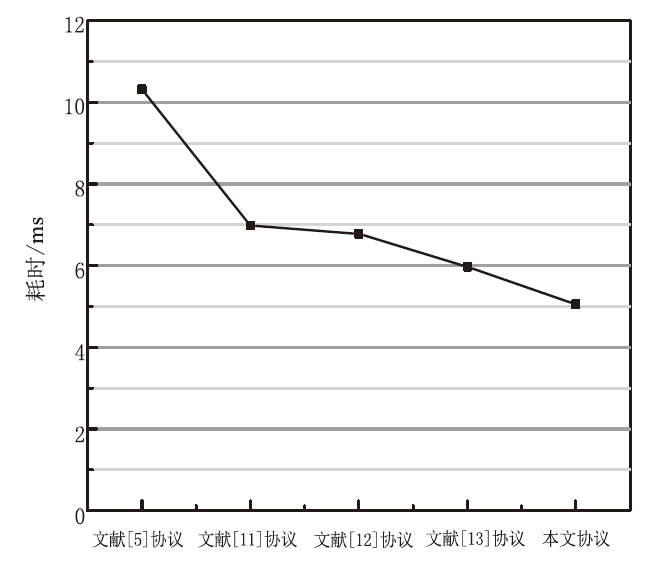
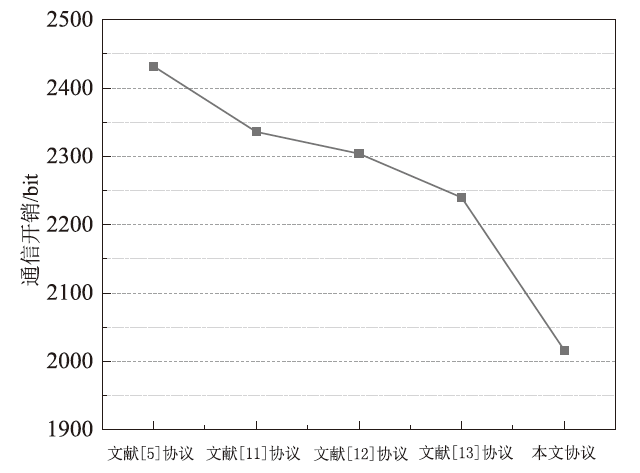
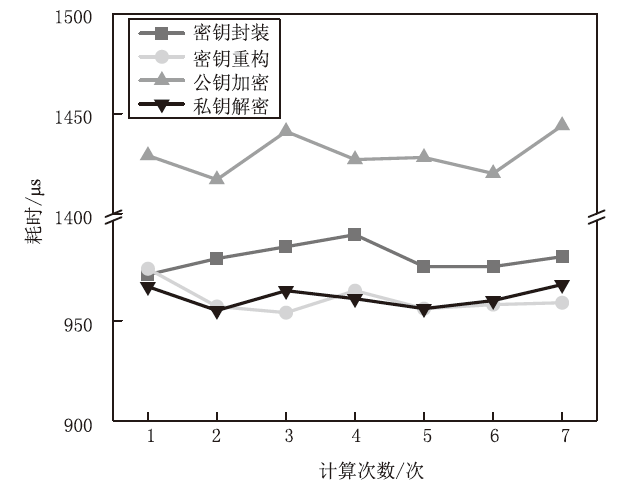
| [1] |
WU Chuankun. An Overview on the Security Techniques and Challenges of the Internet of Things[J]. Journal of Cryptologic Research, 2015, 2(1): 40-53.
|
|
武传坤. 物联网安全关键技术与挑战[J]. 密码学报, 2015, 2(1): 40-53.
doi: 10.13868/j.cnki.jcr.000059
|
| [2] |
FANG He, QI A, WANG Xianbin. Fast Authentication and Progressive Authorization in Large-Scale IoT: How to Leverage AI for Security Enhancement[J]. IEEE Network, 2020, 34(3): 24-29.
|
| [3] |
TEDESCHI P, SCIANCALEPORE S, ELIYAN A, et al. LiKe: Lightweight Certificateless Key Agreement for Secure IoT Communications[J]. IEEE Internet of Things Journal, 2020, 7(1): 621-638.
|
| [4] |
QIU Fan, HU Kaiyu, ZUO Liming, et al. Distributed Control Identity Authentication Technology Based on SM9[J]. Computer Applications and Software, 2020, 37(9): 291-295.
|
|
邱帆, 胡凯雨, 左黎明, 等. 基于国密SM9的配电网分布式控制身份认证技术[J]. 计算机应用与软件, 2020, 37(9): 291-295.
|
| [5] |
ODELU V, DAS A K, WAZID M, et al. Provably Secure Authenticated Key Agreement Scheme for Smart Grid[J]. IEEE Transactions on Smart Grid, 2018, 9(3): 1900-1910.
|
| [6] |
ABBASINEZHAD-MOOD D, NIKOOGHADAM M. Design and Hardware Implementation of a Security-Enhanced Elliptic Curve Cryptography Based Lightweight Authentication Scheme for Smart Grid Communications[J]. Future Generation Computer Systems, 2018, 84: 47-57.
|
| [7] |
GONG Xiang, FENG Tao. Lightweight Anonymous Authentication and Key Agreement Protocol Based on CoAP of Internet of Things[EB/OL]. (2022-09-22)[2024-04-21]. https://pubmed.ncbi.nlm.nih.gov/36236290/.
|
| [8] |
ABOSATA N, AL-RUBAYE S, INALHAN G. Lightweight Payload Encryption-Based Authentication Scheme for Advanced Metering Infrastructure Sensor Networks[J]. Sensors, 2022, 22(2): 534-544.
|
| [9] |
QURESHI N M F, SIDDIQUI I F, ABBAS A, et al. Stream-Based authentication Strategy Using IoT Sensor Data in Multi-Homing Sub-Aqueous Big Data Network[J]. Wireless Personal Communications, 2021, 116(2): 1217-1229.
|
| [10] |
DAS A K, WAZID M, YANNAM A R, et al. Provably Secure ECC-Based Device Access Control and Key Agreement Protocol for IoT Environment[J]. IEEE Access, 2019, 7: 55382-55397.
|
| [11] |
KHAN A A, KUMAR V, AHMAD M, et al. PALK: Password-Based Anonymous Lightweight Key Agreement Framework for Smart Grid[EB/OL]. (2020-05-14)[2024-04-21]. https://www.sciencedirect.com/science/article/abs/pii/S0142061519340621.
|
| [12] |
SAHIL G, KAUR K, KADDOUM G, et al. Secure and Lightweight Authentication Scheme for Smart Metering Infrastructure in Smart Grid[J]. IEEE Transactions on Industrial Informatics, 2020, 16(5): 3548-3557.
|
| [13] |
CHEN Yanru, YIN Fengming, HU Shunfang, et al. ECC-Based Authenticated Key Agreement Protocol for Industrial Control System[J]. IEEE Internet of Things Journal, 2023, 10(6): 4688-4697.
|
| [14] |
ZHAI Peng, HE Jingsha, ZHANG Yu. An Identity Authentication Method Based on SM9 and Blockchain in the IoT Environment[J]. Netinfo Security, 2024, 24(2): 179-187.
|
 ), WANG Daiqiang1,2, ZHAO Qi2
), WANG Daiqiang1,2, ZHAO Qi2