信息网络安全 ›› 2014, Vol. 14 ›› Issue (10): 70-76.doi: 10.3969/j.issn.1671-1122.2014.10.013
基于Web应用的安全日志审计系统研究与设计
段娟1,2, 辛阳1,2, 马宇威1,2
- 1.北京邮电大学信息安全中心,北京 100876
2.灾备技术国家工程实验室,北京 100876
-
收稿日期:2014-09-01出版日期:2014-10-01发布日期:2015-08-17 -
作者简介:段娟(1986-),女,陕西,硕士研究生,主要研究方向:Web安全、Webshell;辛阳(1977-),男,北京,副教授,博士,主要研究方向:虚拟化安全、云安全、Web安全;马宇威(1988-),男,河北,硕士研究生,主要研究方向:网络攻防、移动互联网、IDS技术。
-
基金资助:国家自然科学基金[61121061、61161140320]、中央高校基本科研业务费专项资金[2012RC0215、2012RC0216]
Research and Design of Security Audit Log System Based on Web Application
DUAN Juan1,2, XIN Yang1,2, MA Yu-wei1,2
- 1. Information Security Center, Beijing University of Posts and Telecommunications, Beijing 100876, China
2. National Engineering Laboratory for Disaster Backup and Recovery, Beijing 100876, China
-
Received:2014-09-01Online:2014-10-01Published:2015-08-17
摘要:
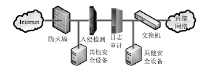
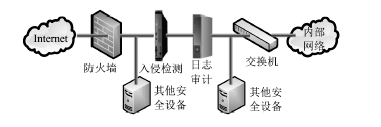
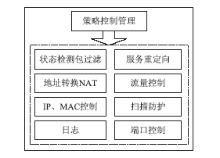
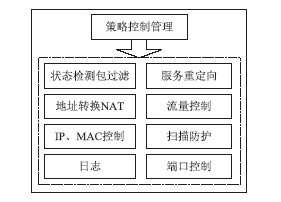
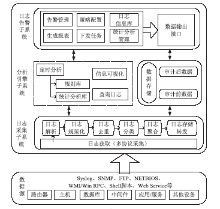
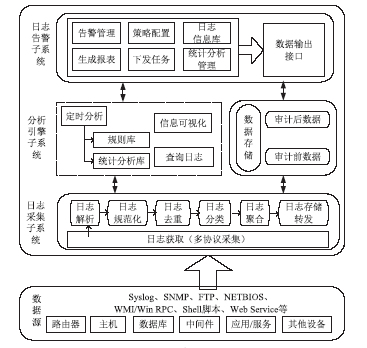
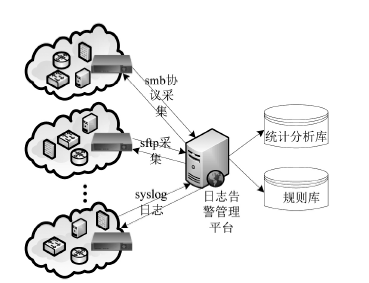
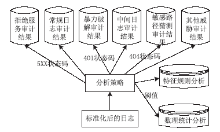
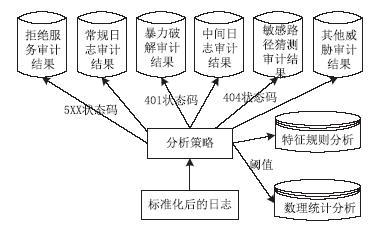
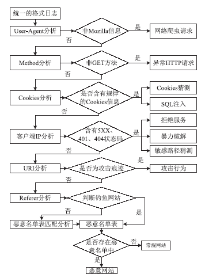
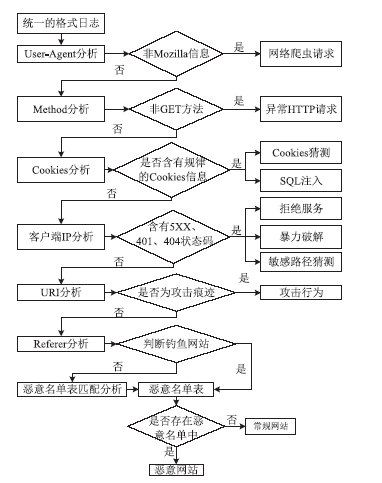
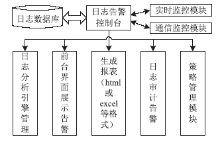
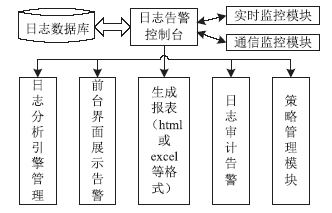
近年来随着Web应用技术的不断进步和发展,针对Web应用业务的需求越来越多,随之而来的Web应用安全攻击也呈上升趋势。目前针对网络攻击的防护技术手段也是层出不穷,但一般都是事前检测和事中防护,事后检测维护的则相应比较少。在网络中心有大量的服务器设备,Web日志文件作为服务器的一部分,详细记录设备系统每天发生的各种各样的事件,如客户端对服务器的访问请求记录、黑客对网站的入侵行为记录等,因此要想有效的管理维护设备和在攻击事件发生后及时的降低风险,分析审计日志对于事后检测和维护设备的安全是非常必要的。基于此,文章主要对基于Web应用安全日志审计系统进行研究和设计,日志审计系统主要分为三个子系统:日志采集子系统、分析引擎子系统和日志告警子系统。日志采集子系统采用多协议分析对日志进行收集,并进行相应的日志规范化和去重等处理。分析引擎子系统采用规则库和数理统计的方法,对日志特征进行提取和设置相应的统计量参数,进行比较分析。日志告警子系统则是主要配置相应策略并下发任务,对于审计结果进行界面展示或生成报告并以邮件的方式发送给用户等。
中图分类号:
引用本文
段娟, 辛阳, 马宇威. 基于Web应用的安全日志审计系统研究与设计[J]. 信息网络安全, 2014, 14(10): 70-76.
DUAN Juan, XIN Yang, MA Yu-wei. Research and Design of Security Audit Log System Based on Web Application[J]. Netinfo Security, 2014, 14(10): 70-76.
| [1] | 梁莹. 基于“WEB日志挖掘”技术的校园网络日志分析与安全审计[D]. 重庆:重庆大学,2009. |
| [2] | 熊艳. 基于网络日志的安全审计系统的研究与实现[D]. 上海:上海交通大学,2002. |
| [3] | 周琪锋. 基于网络日志的安全审计系统的研究与设计[J]. 计算机技术与发展,2009,19(11):139-142. |
| [4] | 韩松言. Windows日志审计系统的设计[D]. 沈阳:东北大学,2009. |
| [5] | 石彪,胡华平,刘利枚. 网络环境下的日志监控与安全审计系统设计与实现[J]. 福建电脑,2004,(12):43-44. |
| [6] | 宋擒豹,沈钧毅. Web日志的高效多能挖掘算法[J].计算机研究与发展,2001,38(3):328-333. |
| [7] | 施建生,伍卫国,陆丽娜,等. Web日志中挖掘用户浏览模式的研究[J]. 西安交通大学学报,2001,35(6):621-324. |
| [8] | 邢东山,沈钧毅,宋擒豹. 从Web日志中挖掘用户浏览偏爱路径[J].计算机学报,2003,26(11):1518-1523. |
| [9] | 石彪,胡华平,刘利枚. 网络环境下的日志监控与安全审计系统设计与实现[J]. 福建电脑,2004,(12):43-44. |
| [10] | 殷秦. 基于云计算服务的Web性能测试服务系统开发[D]. 北京:清华大学,2010. |
| [11] | 梁广泰,王千祥. CODAS:一个易扩展的静态代码缺陷分析服务[J]. 计算机科学,2012,39(1):14-18. |
| [12] | 王海峰,夏洪雷. 入侵检测系统的局限性分析与解决策略[J]. 临沂师范学院学报,2006,28(3):110-113. |
| [13] | Spinellis D, Louridas P.A framework for the static verification of API calls[J]. The Journal of Systems and Software, 2007, 80(07): 1156–1168. |
| [14] | Ayewah N, Pugh W.Evaluating Static Analysis Defect Warnings On Production Software[C]//Proceedings of the 7th ACM SIGPLAN-SIGSOFT workshop on Program analysis for software tools and engineering, 2007: 1-8. |
| [15] | Hovemeyer D, Pugh W.Finding More Null Pointer Bugs, But Not Too Many[C]//Proceedings of the 7th ACM SIGPLAN-SIGSOFT Workshop on Program Analysis for Software Tools and Engineering, 2007: 9-14. |
| [1] | 黄旺旺, 周骅, 王代强, 赵麒. 基于国密SM9的物联网可重构密钥安全认证协议设计[J]. 信息网络安全, 2024, 24(7): 1006-1014. |
| [2] | 张晓均, 张楠, 郝云溥, 王周阳, 薛婧婷. 工业物联网系统基于混沌映射三因素认证与密钥协商协议[J]. 信息网络安全, 2024, 24(7): 1015-1026. |
| [3] | 张继威, 王文俊, 牛少彰, 郭向阔. 区块链扩展解决方案:ZK-Rollup综述[J]. 信息网络安全, 2024, 24(7): 1027-1037. |
| [4] | 张立强, 路梦君, 严飞. 一种基于函数依赖的跨合约模糊测试方案[J]. 信息网络安全, 2024, 24(7): 1038-1049. |
| [5] | 董云云, 朱玉玲, 姚绍文. 基于改进U-Net和混合注意力机制的高质量全尺寸图像隐写方法[J]. 信息网络安全, 2024, 24(7): 1050-1061. |
| [6] | 周书丞, 李杨, 李传荣, 郭璐璐, 贾辛洪, 杨兴华. 基于上下文的异常根因算法[J]. 信息网络安全, 2024, 24(7): 1062-1075. |
| [7] | 任昌禹, 张玲, 姬航远, 杨立群. 基于预训练模型和中英文威胁情报的TTP识别方法研究[J]. 信息网络安全, 2024, 24(7): 1076-1087. |
| [8] | 蔡满春, 席荣康, 朱懿, 赵忠斌. 一种Tor网站多网页多标签指纹识别方法[J]. 信息网络安全, 2024, 24(7): 1088-1097. |
| [9] | 项慧, 薛鋆豪, 郝玲昕. 基于语言特征集成学习的大语言模型生成文本检测[J]. 信息网络安全, 2024, 24(7): 1098-1109. |
| [10] | 申秀雨, 姬伟峰. 考虑安全的边—云协同计算卸载成本优化[J]. 信息网络安全, 2024, 24(7): 1110-1121. |
| [11] | 赵新强, 范博, 张东举. 基于威胁发现的APT攻击防御体系研究[J]. 信息网络安全, 2024, 24(7): 1122-1128. |
| [12] | 问闻, 刘钦菊, 邝琳, 任雪静. 隐私保护体系下网络威胁情报共享的研究现状和方案设计[J]. 信息网络安全, 2024, 24(7): 1129-1137. |
| [13] | 刘一丹, 马永柳, 杜宜宾, 程庆丰. 一种车联网中的无证书匿名认证密钥协商协议[J]. 信息网络安全, 2024, 24(7): 983-992. |
| [14] | 罗铭, 詹骐榜, 邱敏蓉. 面向V2I通信的异构跨域条件隐私保护环签密方案[J]. 信息网络安全, 2024, 24(7): 993-1005. |
| [15] | 李增鹏, 王思旸, 王梅. 隐私保护近邻检测研究[J]. 信息网络安全, 2024, 24(6): 817-830. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||