信息网络安全 ›› 2014, Vol. 14 ›› Issue (10): 64-69.doi: 10.3969/j.issn.1671-1122.2014.10.012
基于改进策略树的防火墙策略审计方案设计与实现
卢云龙1, 罗守山1, 郭玉鹏2
- 1.北京邮电大学信息安全中心,北京 100876
2.北京林业大学信息学院,北京 100083
The Design and Implementation of Firewall Policy Audit Plan Based on Improved Strategy Tree
LU Yun-long1, LUO Shou-shan1, GUO Yu-peng2
- 1. Information Security Center, Beijing University of Posts and Telecommunications, Beijing 100876, China
2. School of Information Science & Technology, Beijing Forestry University, Beijing 100083, China
摘要:
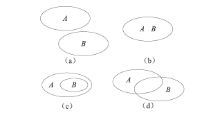
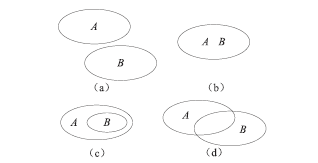
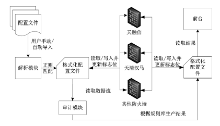
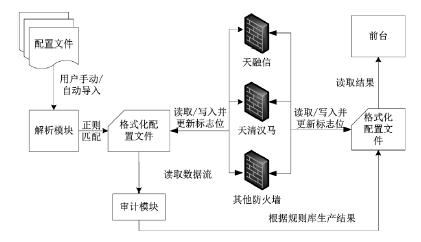
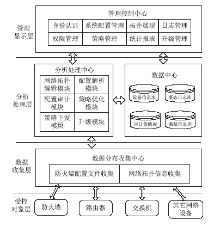
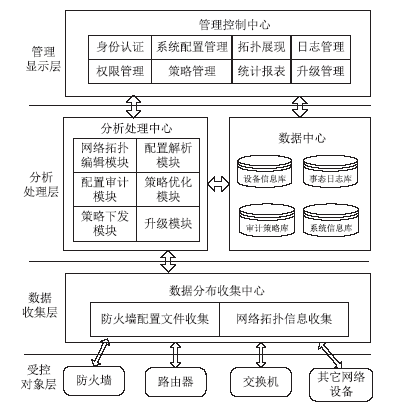
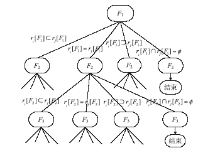
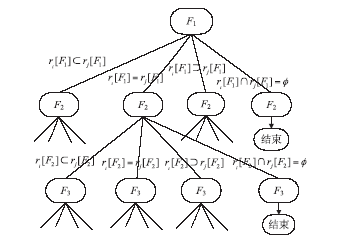
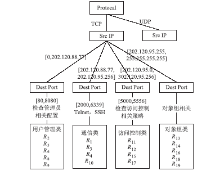
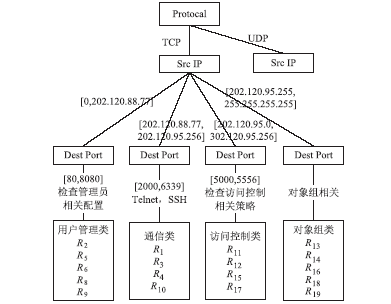
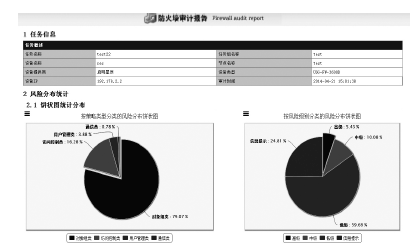
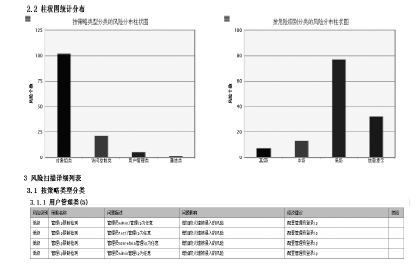
防火墙在当今网络中起着不可或缺的作用,防火墙规则配置的合理与否直接关系到网络环境的安全。随着网络规模日益增大,防火墙配置也日趋复杂,为了更好的发挥防火墙的防护性能,防火墙策略审计应需而生。文章首先对防火墙规则之间的关系进行了详细研究,总结并分析了一些常见的规则异常种类,并对现有的策略审计方案进行了综述研究。其次,论述了防火墙策略审计系统整体的工作流程,层次化的分析了系统总体架构设计,对防火墙策略审计系统的配置规则审计模块进行了重点研究论述。再次,论述了传统的策略判定树审计方案,详细阐述了该方案的实现流程,分析并指出了该方案的优点以及所存在的不足。接下来提出一种以树形结构为基础改进后的策略审计方案,详细论述了该方案的审计流程并实现了改进的审计方案。最后结合该实现展示了系统的图形化报表以及详细审计结果,对改进后审计方案的审计结果与传统策略树进行了对比分析验证。
中图分类号: