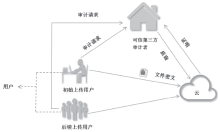
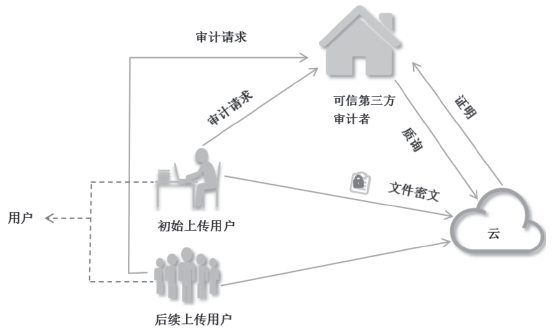
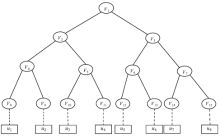
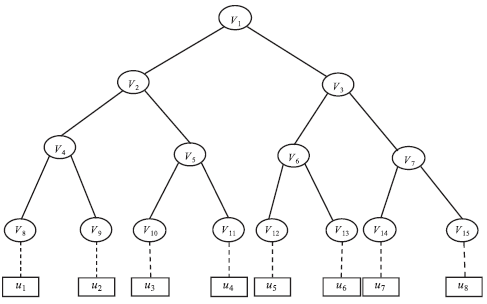
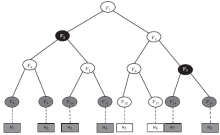
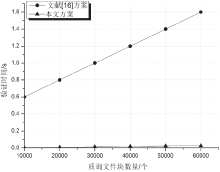
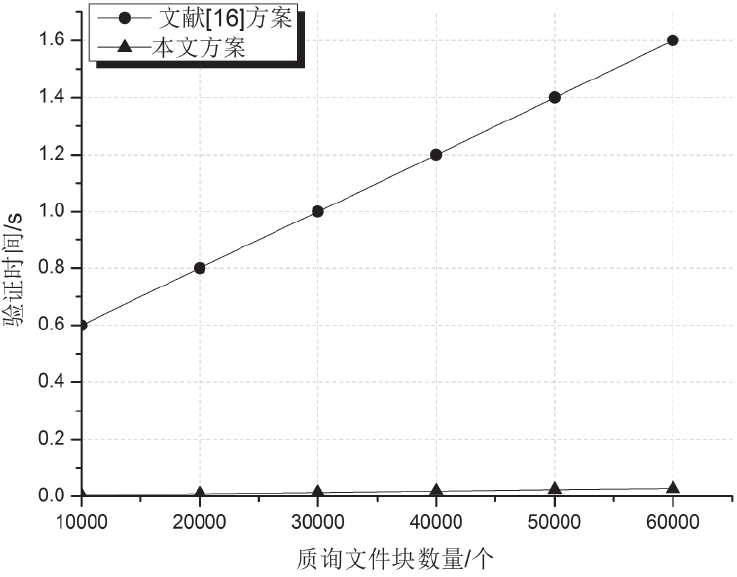
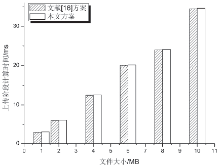
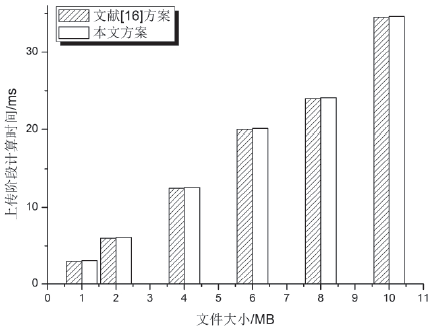
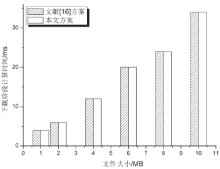
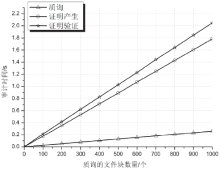
| [1] |
LIU Chang, RANJIAN R, ZHANG Xuyun, et al.Public Auditing for Big Data Storage in Cloud Computing-A Survey[C]//IEEE.2013 IEEE 16th International Conference on Computational Science and Engineering (CSE), March 6, 2014. Sydney, NSW, Australia.NJ:IEEE, 2013:1128-1135.
|
| [2] |
YU Jia., REN Kui., WANG Cong,et al.Enabling Cloud Storage Auditing with Key-Exposure Resistance[J]. IEEE Transactions on Information Forensics & Security, 2017, 10(6):1167-1179.
|
| [3] |
YU Jia, REN Kui, WANG Cong.Enabling Cloud Storage Auditing with Verifiable Outsourcing of Key Updates[J]. IEEE Transactions on Information Forensics & Security, 2016, 11(6):1362-1375.
|
| [4] |
唐春明, 郑晓龙. 云计算中一种对大群组用户的隐私保护公共审计方案[J]. 信息网络安全, 2015(2): 19-25.
|
| [5] |
YANG Guangyang, YU Jia, SHEN Wenting, et al.Enabling Public Auditing for Shared Data in Cloud Storage Supporting Identity Privacy and Traceability[J].Journal of Systems and Software, 2016(113): 130-139.
|
| [6] |
SHEN Wenting, YU Jia, XIA Hui, et al.Light-weight and Privacy-preserving Secure Cloud Auditing Scheme for Group Users via the Third Party Medium[J].Journal of Network and Computer Applications, 2017(82): 56-64.
|
| [7] |
WANG Cong, CHOW S S M, WANG Qian, et al. Privacy Preserving Public Auditing for Secure Cloud Storage[J]. IEEE Transactions on Computers, 2013(62): 362-375.
|
| [8] |
WANG Cong, WANG Qian, REN Kui, et al.Privacy-Preserving Public Auditing for Data Storage Security in Cloud Computing[C]//IEEE.Proceedings of IEEE INFOCOM 2010, March 14-19, 2010. San Diego, CA, USA.NJ:IEEE,2010:525-533.
|
| [9] |
赵洋, 任化强, 熊虎, 等. 基于更新树的动态云数据审计方案[J]. 信息网络安全, 2015 (12): 1-7.
|
| [10] |
WANG Huaqun, HE Debiao, TANG Shaohua.Identity-Based Proxy-Oriented Data Uploading and Remote Data Integrity Checking in Public Cloud[J].IEEE Transactions on Information Forensics and Security, 2016(11): 1165-1176.
|
| [11] |
YU Jia, WANG Huaqun.Strong Key-Exposure Resilient Auditing for Secure Cloud Storage[J]. IEEE Transactions on Information forensics and security, 2017(12): 1931-1940.
|
| [12] |
秦志光,吴世坤,熊虎. 云存储服务中数据完整性审计方案综述[J]. 信息网络安全, 2014(7): 1-6.
|
| [13] |
GANTZ J, REINSEL D. The Digital Universe Decade-Are You Ready?[EB/OL]. .
|
| [14] |
HALEVI S, HARNIK D, PINKAS B, et al.Proofs of Ownership in Remote Storage Systems[C]//ACM.Proceedings of the 18th ACM Conference on Computer and Communications Security, October 17 - 21, 2011. Chicago, Illinois, USA. New York: ACM,2011: 491-500.
|
| [15] |
PIETRO R D,SORNIOTTI A.Boosting Efficiency and Security in Proof of Ownership for Deduplication[C]//ACM.Proceedings of the 7th ACM Symposium on Information, Computer and Communications Security, May 2-4, 2012. Seoul, Korea. New York:ACM, 2012: 81-82.
|
| [16] |
ZHENG Qingji, XU Shouhuai.Secure and Efficient Proof of Storage with Deduplication[C]//ACM. Proceedings of the Second ACM Conference on Data and Application Security and Privacy, February 7 - 9, 2012. San Antonio, Texas, USA. New York: ACM, 2012: 1-12.
|
| [17] |
YUAN Jiawei, YU Shucheng.Secure and Constant Cost Public Cloud Storage Auditing with Deduplication[C]//IEEE.2013 IEEE Conference on Communications and Network Security (CNS), October 14-16, 2013. National Harbor, MD, USA.NJ:IEEE, 2013: 145-153.
|
| [18] |
LI Jingwei, LI Jin, XIE Dongqing, et al.Secure Auditing and Deduplicating Data in Cloud[J].IEEE Transactions on Computers, 2016, 65(8):2386-2396.
|
| [19] |
LITWIN W, SCHWARZ T.Algebraic Signatures for Scalable Distributed Data Structures[C]//IEEE.Twentieth IEEE International Conference on Data Engineering, April 2, 2004. Boston, MA, USA.NJ:IEEE, 2004: 412-423.
|
| [20] |
Pairing-Based Cryptography(PBC) Library,2017-5-20.
|
 ), Rong HAO1
), Rong HAO1