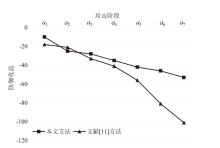
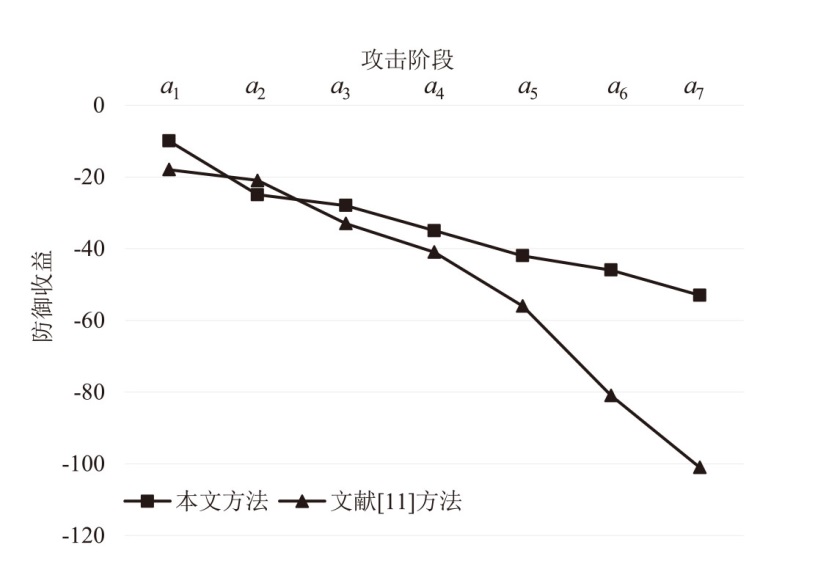
Netinfo Security ›› 2026, Vol. 26 ›› Issue (1): 59-68.doi: 10.3969/j.issn.1671-1122.2026.01.005
Previous Articles Next Articles
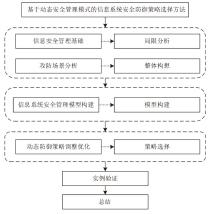
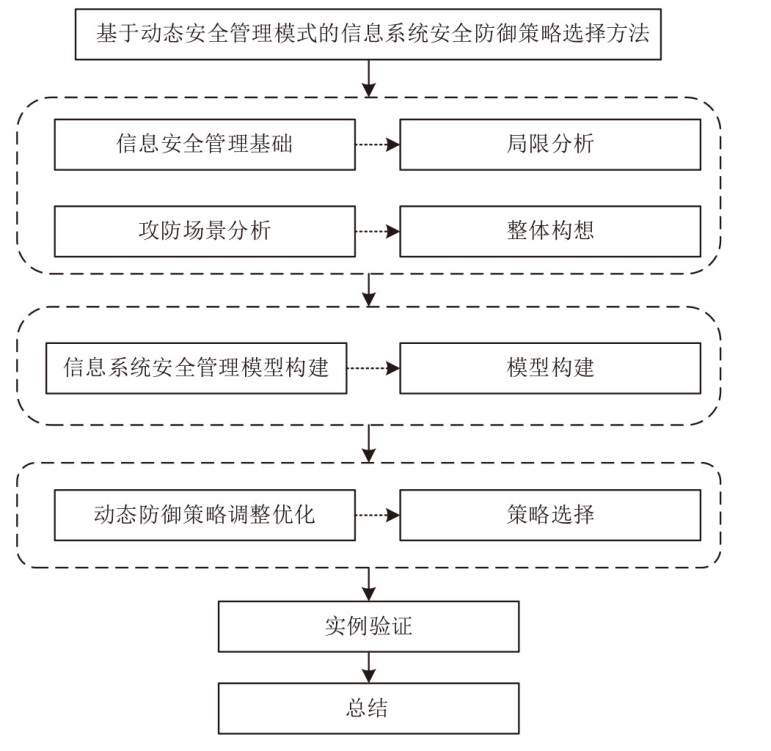
Research on Security Defense Strategy of Information System Based on Dynamic Security Management Model
WU Yue1, ZHANG Yawen2, CHENG Xiangran1,3( )
)
- 1. School of Cryptographic Engineering, Cyberspace Force Information Engineering University, Zhengzhou 450001, China
2. Unit 92330 of PLA, Qingdao 266100, China
3. Cyberspace International Governance Research Base, Fudan University, Shanghai 200433, China
-
Received:2025-03-30Online:2026-01-10Published:2026-02-13
CLC Number:
Cite this article
WU Yue, ZHANG Yawen, CHENG Xiangran. Research on Security Defense Strategy of Information System Based on Dynamic Security Management Model[J]. Netinfo Security, 2026, 26(1): 59-68.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2026.01.005
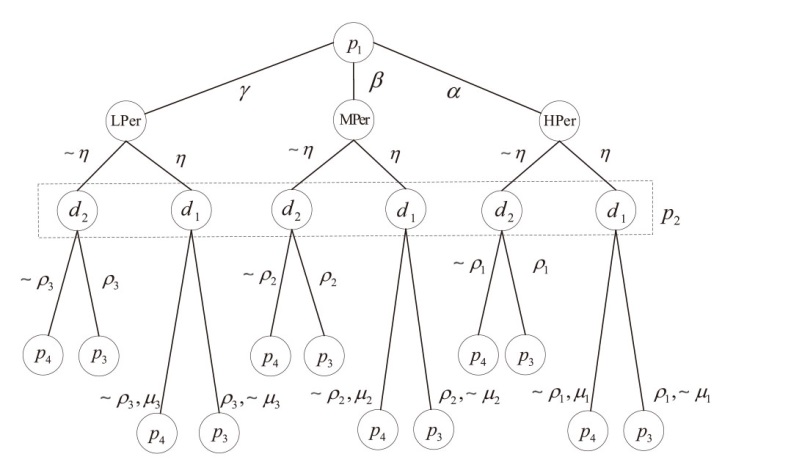
| 管理者 | ||
|---|---|---|
| 攻击者 | HPer | |
| MPer | ||
| LPer | ||
| 防御策略 | 行为描述 | 符号表示 | 变迁触发率参数 |
|---|---|---|---|
| IDS | 入侵检测 | ||
| Anti_Vul | 病毒查杀 | ||
| Block_IP | 锁定IP | ||
| Rem_Scri | 清除恶意程序 | ||
| Rem_Sniffer | 清除嗅探器 | ||
| Trace_IP | 溯源追查 | ||
| ? | 无行动 |
| [1] | MA Hhongjian, LI Yiyong, CHE Lu, et al. Research on Security Management of University Information System Based on Smart Campus[J]. Modern Information Technology, 2022, 6(8): 155-157. |
| 马鸿健, 李义勇, 车路. 等. 基于智慧校园的高校信息系统安全管理研究[J]. 现代信息科技, 2022, 6(8): 155-157. | |
| [2] | YIN Hhuantong. Analysis of Network Security and Research on Hospital Information System Security Management[J]. China New Telecommunications. 2021, 23(18): 115-116 |
| 殷焕炯. 试析网络安全及医院信息系统安全管理研究[J]. 中国新通信, 2021, 23(18): 115-116. | |
| [3] | WANG Ming. Practice in Security Management of Railway Station Anddepot Information System[J]. Railway Computer Application, 2021, 30(11): 47-53. |
| 王明. 铁路基层站段信息系统安全管理实践[J]. 铁路计算机应用, 2021, 30(11): 47-53. | |
| [4] | DING Guanghua, HAN Xuejun, ZHANG Ggangling. Analysis on the Construction Path of Information System Security Management System——From the Perspective of Provincial People's Bank Security Management[J]. FinTech Time, 2022, (9): 22-24. |
| 丁光华, 韩学军, 张刚领. 信息系统安全管理体系建设路径探析——以省域人民银行安全管理为视角[J]. 金融科技时代, 2022,(9): 22-24. | |
| [5] | ZHAO Yue, MA Yuwei, HAN Lei. Security Management Strategy of Integrated Information System[J]. Dual Use Technologies & Products. 2024, (4): 66-69. |
| 赵越, 马玉伟, 韩磊. 集团企业一体化信息系统安全管理策略研究[J]. 军民两用技术与产品, 2024,(4): 66-69. | |
| [6] | LIU Zihui, PAN Wei, WU Chao. Research on the Application of SI-SB System Security Model in the Security Management of High-Speed Railway Information System[J]. Science & Technology for Development. 2021, 17(5): 906-913. |
| 刘子慧, 潘伟, 吴超. 安全信息——安全行为系统安全模型在高铁信息系统安全管理中的应用研究[J]. 科技促进发展, 2021, 17(5): 906-913. | |
| [7] | CHEN Changmao. Research on Critical Factors AffectingInformatization Security Management in Hcompany[D]. Guangzhou: South China University of Technology, 2023. |
| 陈昌茂. H公司信息系统安全管理关键影响因素研究[D]. 广州: 华南理工大学, 2023. | |
| [8] | TANG Ronghua. Evaluation of Information System Security Management Based on Grey Relational Analysis and Synthesis[J]. Video Engineering, 2022, 46(11): 41-46. |
| 唐荣华. 基于灰色关联分析综合法的信息系统安全管理评价[J]. 电视技术, 2022, 46(11): 41-46. | |
| [9] |
GUO Ziyu, QI Jiahao, ZUO Jinxin, et al. A Security Evaluation Model for Edge Information Systems Based on Index Screening[J]. IEEE Internet of Things Journal, 2024, 11(12): 21585-21603.
doi: 10.1109/JIOT.2024.3375077 URL |
| [10] |
WANG Fei. Research on Optimization Algorithms for Artificial Intelligence Network Security Management Based on All IP Internet of Things Fusion Technology[J]. Computers and Electrical Engineering, 2024, 115: 109105.
doi: 10.1016/j.compeleceng.2024.109105 URL |
| [11] | MAO Xinyue. Research on Information System Security ManagementBased on Game Theory[D]. Guizhou: Guizhou University, 2017. |
| 毛新月. 基于博弈论的信息系统安全管理研究[D]. 贵州: 贵州大学, 2017. | |
| [12] | GAN Qingyun. Analysis of Security Risk Self-assessment of Classified Information System[J]. Cyberspace Security, 2017, 8(Z4): 51-53. |
| 甘清云. 浅析涉密信息系统安全风险自评估[J]. 网络空间安全, 2017, 8(Z4): 51-53. | |
| [13] |
LEITGEB H. The stability theory of belief[J]. Philosophical review, 2014, 123(2): 131-171.
doi: 10.1215/00318108-2400575 URL |
| [14] | Tarun Yadav, Arvind Mallari Rao. Technical Aspects of Cyber Kill Chain[C]// International symposium on security in computing and communication. Cham: Springer International Publishing, 2015: 438-452. |
| [15] | NIU Xinxin. A Study on Peirce's Theory[D]. Baoding: Hebei University, 2024. |
| 牛鑫鑫. 皮尔士信念理论研究[D]. 保定: 河北大学, 2024. | |
| [16] |
WANG Yun, ZHANG Yunbin. Belief Elicitation in Economic Experiments: Theory, Methodology and Applications[J]. South China Journal of Economics, 2020, (6): 87-104.
doi: 10.19592/j.cnki.scje.371608 |
| 王云, 张畇彬. 经济学实验中的信念诱导与测度:理论、方法与应用[J]. 南方经济, 2020,(6): 87-104. | |
| [17] | TENG Jimmy. Refining Perfect Bayesian Equilibrium by Bayesian Iterative Conjectures Algorithm[J]. Game Theory & Bargaining Theory, 2012, 10: 174-184. |
| [18] | ZHANG Hengwei, WANG Jindong, YU Dingkun, et al. Active Defense Strategy Selection Based on Static Bayesian Game[C]// Third international conference on cyberspace technology(CCT 2015). Stevenage UK: IET, 2015: 44-50. |
| [19] | YUAN Bo. Research on the Decision-Making Method of Network DefenseStrategy Based on Dynamic Game Theory[D]. Zhengzhou: Zhengzhou University of Light Industry, 2022. |
| 袁博. 基于动态博弈的网络防御策略选取方法研究[D]. 郑州: 郑州轻工业大学, 2022. |
| [1] | GUO Yi, LI Xuqing, ZHANG Zijiao, ZHANG Hongtao, ZHANG Liancheng, ZHANG Xiangli. A Review of Data Security Sharing Based on Blockchain [J]. Netinfo Security, 2026, 26(1): 1-23. |
| [2] | ZHENG Kaifa, LUO Zhenpeng, LIU Jiayi, LIU Zhiquan, WANG Ze, WU Yunkun. A Lightweight Dynamic Node Participation Scheme for Federated Learning Nodes Supporting Attribute Update [J]. Netinfo Security, 2026, 26(1): 102-114. |
| [3] | LI Dong, GAO Yuan, YU Junqing, ZENG Muhong, CHEN Junxin. Polymorphic Network Control and Security Monitor Based on P4 [J]. Netinfo Security, 2026, 26(1): 115-124. |
| [4] | DONG Jiayu, GAO Hongmin, MA Zhaofeng, LAI Guanhui. Research and Implementation of Multi-Signature Mechanism in Blockchain [J]. Netinfo Security, 2026, 26(1): 125-138. |
| [5] | NIU Ke, HU Fangmeng, LI Jun. Research on Reversible Neural Network Video Steganography Based on Nonlocal Mechanism [J]. Netinfo Security, 2026, 26(1): 139-149. |
| [6] | DENG Yuyang, LU Tianliang, LI Zhihao, MENG Haoyang, MA Yuansheng. A SQL Injection Attack Detection Model Integrating GAT and Interpretable DQN [J]. Netinfo Security, 2026, 26(1): 150-167. |
| [7] | TONG Xin, JIAO Qiang, WANG Jingya, YUAN Deyu, JIN Bo. A Survey on the Trustworthiness of Large Language Models in the Public Security Domain: Risks, Countermeasures, and Challenges [J]. Netinfo Security, 2026, 26(1): 24-37. |
| [8] | WANG Yajie, LU Jinbiao, TAN Dongli, FAN Qing, ZHU Liehuang. Member Inference Risk Assessment for Capsule Network [J]. Netinfo Security, 2026, 26(1): 38-48. |
| [9] | SHI Yinsheng, BAO Yang, PANG Jingjing. Research on a Federated Privacy Enhancement Method against GAN Attacks [J]. Netinfo Security, 2026, 26(1): 49-58. |
| [10] | ZHANG Shenming, LIANG Jinjie, XU Xinqiao, FENG Ge, ZOU Tianhua, HU Zhilin. Research on Time Strategy of IP Hopping System Based on Game Theory [J]. Netinfo Security, 2026, 26(1): 69-78. |
| [11] | XU Yifan, CHENG Guang, ZHOU Yuyang. Research on Complex LDoS Attack Detection Methods under Sampling Conditions [J]. Netinfo Security, 2026, 26(1): 79-90. |
| [12] | WANG Huanzhen, XU Hongping, LI Kuangdai, LIU Yang, YAO Linyuan. A Study on Autonomous Decision-Making for Network Defense Based on Hierarchical Reinforcement Learning [J]. Netinfo Security, 2026, 26(1): 91-101. |
| [13] | HAN Yiliang, PENG Yixuan, WU Xuguang, LI Yu. Multimodal Feature Fusion Encrypted Traffic Classification Model Based on Graph Variational Auto-Encoder [J]. Netinfo Security, 2025, 25(12): 1914-1926. |
| [14] | ZHANG Xuefeng, WANG Kehang. A Proxy Ring Signature Scheme Based on SM9 Algorithm [J]. Netinfo Security, 2025, 25(12): 1901-1913. |
| [15] | XIE Xiangpeng, SHAO Xingchen. Secure Gain-Scheduling Method for Stochastic Nonlinear CPS Based on Dual-Domain Polynomial Framework [J]. Netinfo Security, 2025, 25(12): 1889-1900. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||