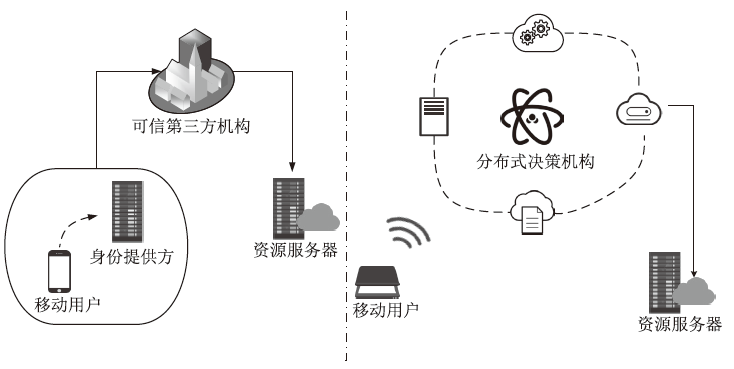
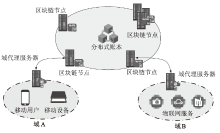
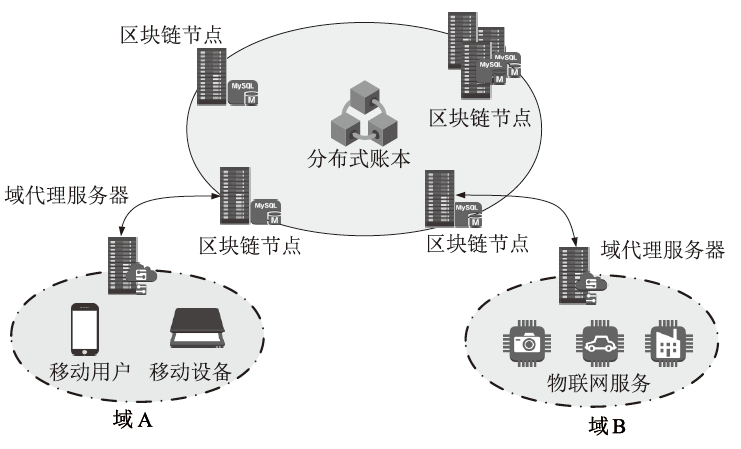
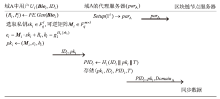
Netinfo Security ›› 2025, Vol. 25 ›› Issue (12): 1948-1960.doi: 10.3969/j.issn.1671-1122.2025.12.010
Previous Articles Next Articles
Blockchain-Based Privacy-Preserving Cross-Domain Authentication Protocol
ZHANG Guanping, WEI Fushan, CHEN Xi, GU Chunxiang( )
)
- Institute of Cyberspace Security, Information Engineering University, Zhengzhou 450001, China
-
Received:2025-02-10Online:2025-12-10Published:2026-01-06 -
Contact:GU Chunxiang E-mail:gcxiang5209@126.com
CLC Number:
Cite this article
ZHANG Guanping, WEI Fushan, CHEN Xi, GU Chunxiang. Blockchain-Based Privacy-Preserving Cross-Domain Authentication Protocol[J]. Netinfo Security, 2025, 25(12): 1948-1960.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2025.12.010
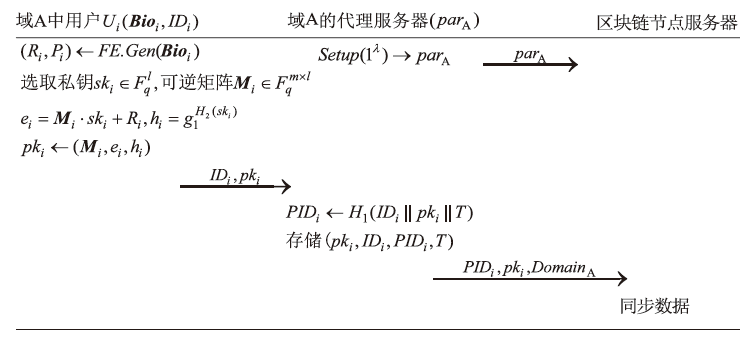
| 参数符号 | 说明 |
|---|---|
| 生物特征向量分量取值参数 | |
| 安全参数所生成的大素数 | |
| 阶为 | |
| 群 | |
| 模糊提取器输出秘密值的向量维数 | |
| 选取的随机向量维数 | |
| 哈希函数 | |
| 哈希函数 | |
| 哈希函数 | |
| 长期公钥 |
| [1] | SHAMIR A. Identity-Based Cryptosystems and Signature Schemes[C]// Springer. Advances in Cryptology-CRYPTO 1984. Heidelberg:Springer, 1984: 47-53. |
| [2] | BONEH D, FRANKLIN M. Identity-Based Encryption from the Weil Pairing[C]// Springer. Advances in Cryptology-CRYPTO 2001. Heidelberg: Springer, 2001: 213-229. |
| [3] | HORWITZ J, LYNN B. Toward Hierarchical Identity-Based Encryption[C]// Springer. Advances in Cryptology-EUROCRYPT 2002. Heidelberg: Springer, 2002: 466-481. |
| [4] | AL-RIYAMI S S, PATERSON K G. Certificateless Public Key Cryptography[C]// Springer. Advances in Cryptology -ASIACRYPT 2003. Heidelberg: Springer, 2003: 452-473. |
| [5] |
SHEN Meng, LIU Huisen, ZHU Liehuang, et al. Blockchain-Assisted Secure Device Authentication for Cross-Domain Industrial IoT[J]. IEEE Journal on Selected Areas in Communications, 2020, 38(5): 942-954.
doi: 10.1109/JSAC.49 URL |
| [6] |
CHEN Jing, ZHAN Zeyi, HE Kun, et al. XAuth: Efficient Privacy-Preserving Cross-Domain Authentication[J]. IEEE Transactions on Dependable and Secure Computing, 2021, 19(5): 3301-3311.
doi: 10.1109/TDSC.2021.3092375 URL |
| [7] |
WANG Linjie, TIAN Youliang, ZHANG Duo. Toward Cross-Domain Dynamic Accumulator Authentication Based on Blockchain in Internet of Things[J]. IEEE Transactions on Industrial Informatics, 2022, 18(4): 2858-2867.
doi: 10.1109/TII.2021.3116049 URL |
| [8] |
TONG Fei, CHEN Xing, WANG Kaiming, et al. CCAP: A Complete Cross-Domain Authentication Based on Blockchain for Internet of Things[J]. IEEE Transactions on Information Forensics and Security, 2022, 17: 3789-3800.
doi: 10.1109/TIFS.2022.3214733 URL |
| [9] |
CUI Jie, LIU Nan, ZHANG Qingyang, et al. Efficient and Anonymous Cross-Domain Authentication for IIoT Based on Blockchain[J]. IEEE Transactions on Network Science and Engineering, 2022, 10(2): 899-910.
doi: 10.1109/TNSE.2022.3224453 URL |
| [10] |
LIU Yizhong, LIU Andi, XIA Yu, et al. A Blockchain-Based Cross-Domain Authentication Management System for IoT Devices[J]. IEEE Transactions on Network Science and Engineering, 2023, 11(1): 115-127.
doi: 10.1109/TNSE.2023.3292624 URL |
| [11] |
WANG Fengqun, CUI Jie, ZHANG Qingyang, et al. Blockchain-Based Lightweight Message Authentication for Edge-Assisted Cross-Domain Industrial Internet of Things[J]. IEEE Transactions on Dependable and Secure Computing, 2023, 21(4): 1587-1604.
doi: 10.1109/TDSC.2023.3285800 URL |
| [12] |
SU Yuan, WANG Yuheng, LI Jiliang, et al. Oracle Based Privacy-Preserving Cross-Domain Authentication Scheme[J]. IEEE Transactions on Sustainable Computing, 2024, 9(4): 602-614.
doi: 10.1109/TSUSC.2024.3350343 URL |
| [13] | WANG Mei, HE Kun, CHEN Jing, et al. Biometrics-Authenticated Key Exchange for Secure Messaging[C]// ACM. 2021 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2021: 2618-2631. |
| [14] |
WU Yongdong, WENG Jian, WANG Zhengxia, et al. Attacks and Countermeasures on Privacy-Preserving Biometric Authentication Schemes[J]. IEEE Transactions on Dependable and Secure Computing, 2023, 20(2): 1744-1755.
doi: 10.1109/TDSC.2022.3162623 URL |
| [15] | NANDAKUMAR K, JAIN A K. Biometric Template Protection: Bridging the Performance Gap between Theory and Practice[J]. IEEE Signal Processing Magazine, 2015, 32(5): 88-100. |
| [16] |
DAUGMAN J. Information Theory and the IrisCode[J]. IEEE Transactions on Information Forensics and Security, 2016, 11(2): 400-409.
doi: 10.1109/TIFS.2015.2500196 URL |
| [17] | REGEV O. On Lattices, Learning with Errors, Random Linear Codes, and Cryptography[J]. Journal of the ACM, 2009, 56(6): 1-40. |
| [18] |
ALBRECHT M R, PLAYER R, SCOTT S. On the Concrete Hardness of Learning with Errors[J]. Journal of Mathematical Cryptology, 2015, 9(3): 169-203.
doi: 10.1515/jmc-2015-0016 URL |
| [19] |
BABAI L. On Lovasz Lattice Reduction and the Nearest Lattice Point Problem[J]. Combinatorica, 1986, 6(1): 1-13.
doi: 10.1007/BF02579403 URL |
| [20] | AGGARWAL D, DADUSH D, STEPHENS-DAVIDOWITZ N. Solving the Closest Vector Problem in 2n Time: The Discrete Gaussian Strikes Again![C]// IEEE. 2015 IEEE 56th Annual Symposium on Foundations of Computer Science. New York: IEEE, 2015: 563-582. |
| [21] |
DODIS Y, OSTROVSKY R, REYZIN L, et al. Fuzzy Extractors: How to Generate Strong Keys from Biometrics and Other Noisy Data[J]. SIAM Journal on Computing, 2008, 38(1): 97-139.
doi: 10.1137/060651380 URL |
| [22] |
DAUGMAN J G. High Confidence Visual Recognition of Persons by a Test of Statistical Independence[J]. IEEE Transactions on Pattern Analysis and Machine Intelligence, 1993, 15(11): 1148-1161.
doi: 10.1109/34.244676 URL |
| [23] | ABDALLA M, FOUQUE P A, POINTCHEVAL D. Password-Based Authenticated Key Exchange in The Three-Party Setting[C]// Springer. Public Key Cryptography-PKC 2005: The 8th International Workshop on Theory and Practice in Public Key Cryptography. Heidelberg: Springer, 2005: 65-84. |
| [24] | WEI Xin, WANG Xinyan, YU Zhuo, et al. Cross Domain Authentication for IoT Based on Consortium Blockchain[J]. Journal of Software, 2021, 32(8): 2613-2628. |
| 魏欣, 王心妍, 于卓, 等. 基于联盟链的物联网跨域认证[J]. 软件学报, 2021, 32(8): 2613-2628. | |
| [25] | WEI Songjie, LI Shasha, WANG Jiahe. A Cross-Domain Authentication Protocol by Identity-Based Cryptography on Consortium Blockchain[J]. Chinese Journal of Computers, 2021, 44(5): 908-920. |
| 魏松杰, 李莎莎, 王佳贺. 基于身份密码系统和区块链的跨域认证协议[J]. 计算机学报, 2021, 44(5): 908-920. |
| [1] | YANG Jianxin, WANG Xiaoding, LIN Hui. Improved Consensus Algorithm Based on HotStuff and Multi-Ary Trees [J]. Netinfo Security, 2025, 25(9): 1447-1455. |
| [2] | SHE Wei, MA Tianxiang, FENG Haige, LIU Wei. Tracing-Free Blockchain Covert Communication Method Based on RBF Mechanism [J]. Netinfo Security, 2025, 25(8): 1302-1312. |
| [3] | LIU Feng, HUANG Hao. A Decentralized Regulatory Architecture Based on Smart Contracts and Prophecy Machines with Active Sensor Networks [J]. Netinfo Security, 2025, 25(6): 898-909. |
| [4] | YE Jiajun, GAO Cuifeng, XUE Yinxing. Research on Price Oracle Manipulation Source Code Detection Method Based on Static Analysis [J]. Netinfo Security, 2025, 25(5): 732-746. |
| [5] | QIN Jinlei, KANG Yimin, LI Zheng. Lightweight Fine-Grained Multi-Dimensional Multi-Subset Privacy-Preserving Data Aggregation for Smart Grid [J]. Netinfo Security, 2025, 25(5): 747-757. |
| [6] | ZHU Xiaoqiang, ZHANG Haowen, LIN Yanzi, LIU Jiqiang. Lightweight Distributed Authentication Scheme Based on Trusted Digital Identity [J]. Netinfo Security, 2025, 25(5): 817-827. |
| [7] | YANG Yatao, DING Yucheng, LIU Peihe, SANG Peng. Research on Blockchain-Based Privacy Preservation and Digital Authentication [J]. Netinfo Security, 2025, 25(4): 640-653. |
| [8] | ZHANG Yuxuan, HUANG Cheng, LIU Rong, LENG Tao. Smart Contract Vulnerability Detection Method Combining Prompt Tuning [J]. Netinfo Security, 2025, 25(4): 664-673. |
| [9] | GUAN Zhi, HU Jianbin, LI Yue, CHEN Zhong. A Comprehensive Survey of Blockchain Technologies and Applications Based on Trusted Execution Environments [J]. Netinfo Security, 2025, 25(11): 1673-1690. |
| [10] | SHEN Haoting, PENG Zhigang, LIU Yuxuan, WANG Yafei. Hardware Authentication Mechanism for Consortium Blockchain Based on Differentiated Physical Unclonable Function Models [J]. Netinfo Security, 2025, 25(11): 1732-1744. |
| [11] | WANG Yong, WU Yifan, WAN Qiancheng. Research on Redactable Blockchain Scheme Based on the Chinese Remainder Theorem [J]. Netinfo Security, 2025, 25(1): 36-47. |
| [12] | YU Lisu, LI Biao, YAO Yuanzhi, WEN Jiajin, LI Zipeng, WANG Zhen. Performance Optimization of Blockchain-Assisted Unmanned Aerial Vehicle Mobile Edge Computing System [J]. Netinfo Security, 2024, 24(9): 1432-1443. |
| [13] | LYU Qiuyun, ZHOU Lingfei, REN Yizhi, ZHOU Shifei, SHENG Chunjie. A Lifecycle-Manageable Public Data Sharing Scheme [J]. Netinfo Security, 2024, 24(8): 1291-1305. |
| [14] | ZHANG Jiwei, WANG Wenjun, NIU Shaozhang, GUO Xiangkuo. Blockchain Scaling Solutions: ZK-Rollup Review [J]. Netinfo Security, 2024, 24(7): 1027-1037. |
| [15] | GUO Rui, YANG Xin, WANG Junming. Verifiable and Revocable Attribute Encryption Scheme Based on Blockchain [J]. Netinfo Security, 2024, 24(6): 863-878. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||