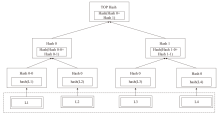
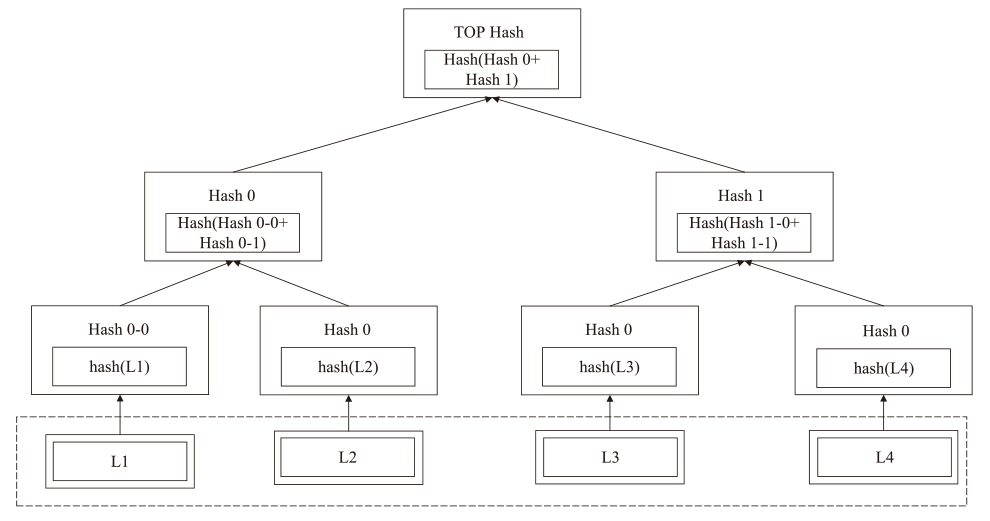
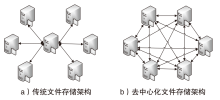
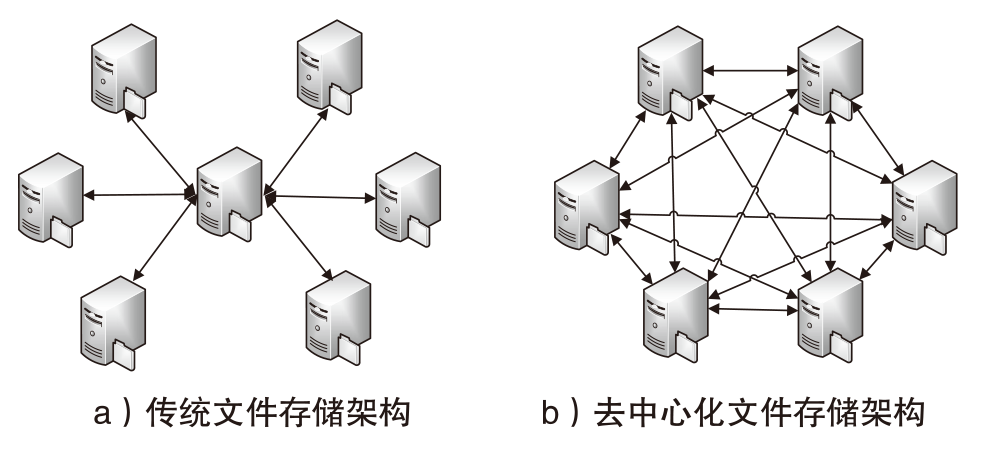
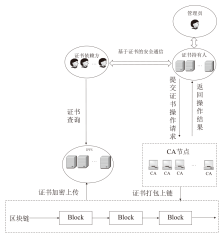
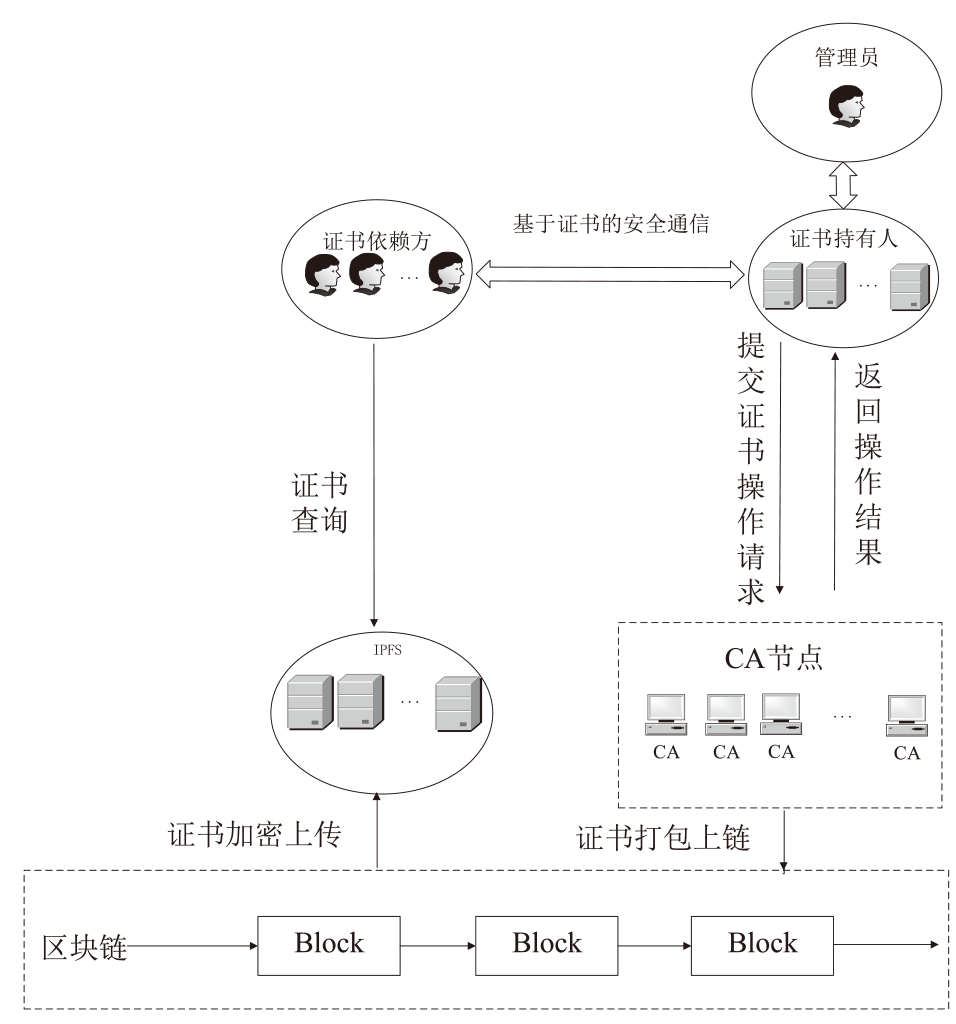
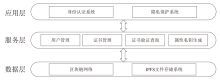
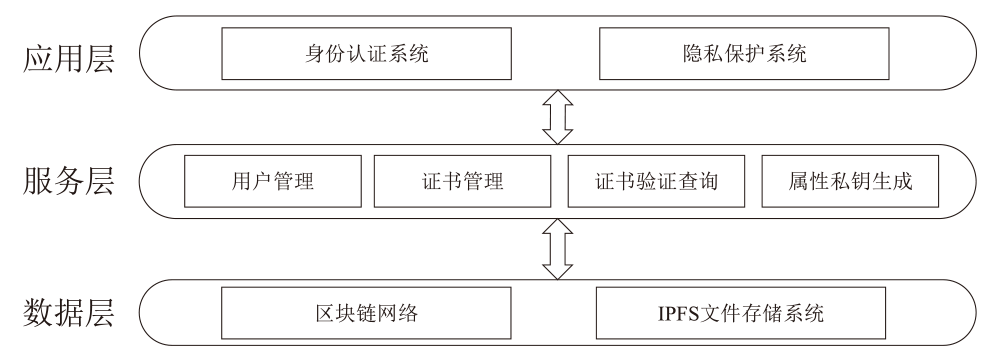
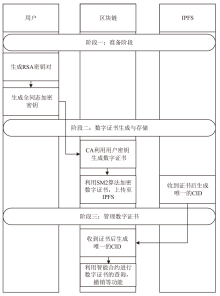
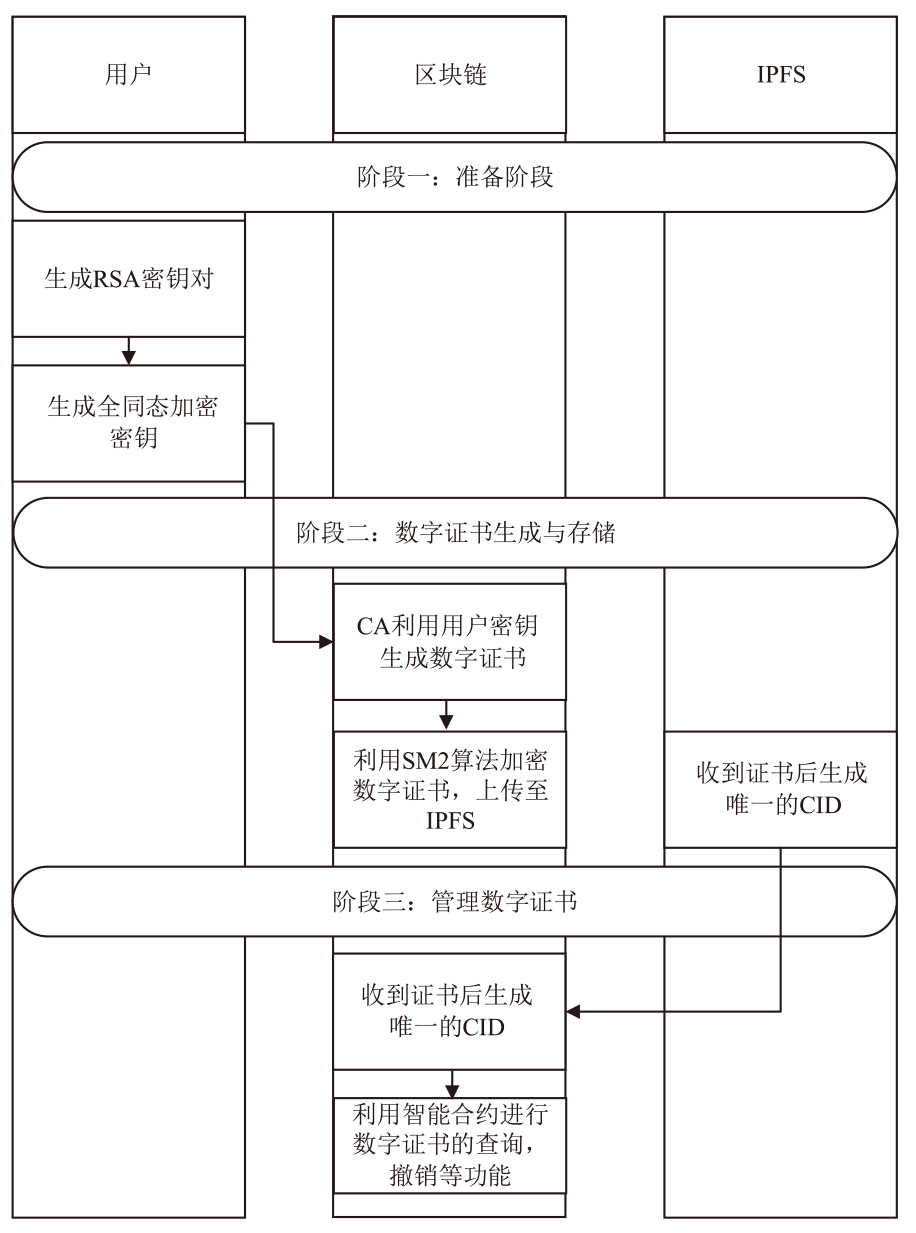
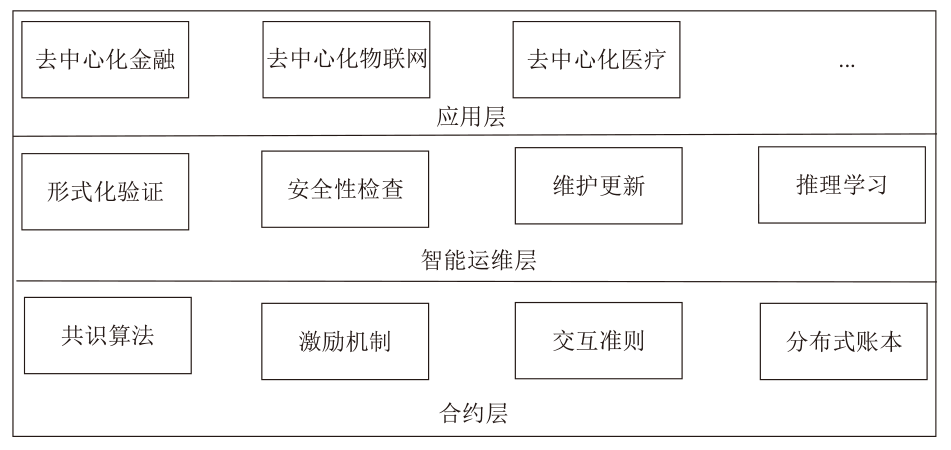
Netinfo Security ›› 2025, Vol. 25 ›› Issue (4): 640-653.doi: 10.3969/j.issn.1671-1122.2025.04.012
Previous Articles Next Articles
Research on Blockchain-Based Privacy Preservation and Digital Authentication
YANG Yatao1,2( ), DING Yucheng1, LIU Peihe1, SANG Peng1
), DING Yucheng1, LIU Peihe1, SANG Peng1
- 1. Department of Electronic and Communication Engineering, Beijing Electronic Science and Technology Institute, Beijing 100070, China
2. School of Telecommunications Engineering, Xidian University, Xi’an 710071, China
-
Received:2024-10-20Online:2025-04-10Published:2025-04-25
CLC Number:
Cite this article
YANG Yatao, DING Yucheng, LIU Peihe, SANG Peng. Research on Blockchain-Based Privacy Preservation and Digital Authentication[J]. Netinfo Security, 2025, 25(4): 640-653.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2025.04.012
| [1] | NAKAMOTO S. Bitcoin: A Peer-To-Peer Electronic Cash System[EB/OL]. (2008-10-31)[2024-09-06]. https://bitcoin.org/bitcoin.pdf. |
| [2] | TEWARI H. Blockchain Research Beyond Cryptocurrencies[J]. IEEE Communications Standards Magazine, 2019, 3(4): 21-25. |
| [3] | XIAO Ling, LI Zhitang. Public Key Infrastructure (PKI) Architecture[J]. Computer Engineering and Applications, 2002, 38(10): 137-139. |
| 肖凌, 李之棠. 公开密钥基础设施(PKI)结构[J]. 计算机工程与应用, 2002, 38(10):137-139. | |
| [4] | LIN Jingqiang, JIN Jiwu, ZHANG Qionglu, et al. Recent Research on PKI Technology: A Review[J]. Journal of Cryptography, 2015, 2(6): 487-496. |
|
林璟锵, 荆继武, 张琼露, 等. PKI技术的近年研究综述[J]. 密码学报, 2015, 2(6):487-496.
doi: 10.13868/j.cnki.jcr.000095 |
|
| [5] |
YANG Yatao, LIU Deli, LIU Peihe, et al. BFV-Blockchainvoting: A Blockchain-Based Electronic Voting System Supporting BFV Fully Homomorphic Encryption[J]. Journal on Communications, 2022, 43(9): 100-111.
doi: 10.11959/j.issn.1000-436x.2022172 |
|
杨亚涛, 刘德莉, 刘培鹤, 等. BFV-Blockchainvoting:支持BFV全同态加密的区块链电子投票系统[J]. 通信学报, 2022, 43(9):100-111.
doi: 10.11959/j.issn.1000-436x.2022172 |
|
| [6] | YANG Yatao, LIN Tianxiang, CHENG Jianyuan. Design of Fully Homomorphic Encryption Smart Contracts Under Edge Computing Model[J]. Journal of Information Security, 2022, 7(2): 150-162. |
| 杨亚涛, 林天祥, 陈剑源. 边缘计算模式下全同态加密智能合约设计[J]. 信息安全学报, 2022, 7(2):150-162. | |
| [7] | NASRULIN B, DE V M, ISHMAEV G, et al. Gromit: Benchmarking the Performance and Scalability of Blockchain Systems[C]// IEEE. 2022 IEEE International Conference on Decentralized Applications and Infrastructures (DAPPS). New York: IEEE, 2022: 56-63. |
| [8] | CHIU W Y, MENG Weizhi, JENSEN C D. ChainPKI-Towards Ethash-Based Decentralized PKI with Privacy Enhancement[C]// IEEE. 2021 IEEE Conference on Dependable and Secure Computing(DSC). New York: IEEE, 2021: 1-8. |
| [9] | BERBECARU D G, LIOY A. An Evaluation of X. 509 Certificate Revocation and Related Privacy Issues in the Web PKI Ecosystem[J]. IEEE Access, 2023, 11: 79156-79175. |
| [10] | FROMKNECHT C, VELICANU D, YAKOUBOV S. Certcoin: A Namecoin Based Decentralized Authentication System[EB/OL]. (2014-05-14)[2024-09-06]. https://courses.csail.mit.edu/6.857/2014/files/19-fromknecht-velicann-yakoubov-certcoin.pdf?source=post_page. |
| [11] | ZOU Bangqi, ZHAO Gansen, TANG Hua, et al. Archiveschain: Distributed PKI Archives System[C]// IEEE. 2021 4th International Conference on Advanced Electronic Materials, Computers and Software Engineering (AEMCSE). New York: IEEE, 2021: 1009-1013. |
| [12] | FAN Wenjun, CHANG S, KUMAR S, et al. Blockchain-Based Secure Coordination for Distributed SDN Control Plane[C]// IEEE. 2021 IEEE 7th International Conference on Network Softwarization (NetSoft). New York: IEEE, 2021: 253-257. |
| [13] | OBIRI I A, YANG Jian, GAO Jun, et al. A Sovereign PKI for IoT Devices Based on the Blockchain Technology[C]// IEEE. 2021 18th International Computer Conference on Wavelet Active Media Technology and Information Processing (ICCWAMTIP). New York: IEEE, 2021: 110-115. |
| [14] | SUZUKI N, YOSHIOKA T, HASEGAWA A, et al. Implementation and Evaluation of Spectrum Sharing Technology Using Smart Contracts[C]// IEEE. 2022 IEEE 12th Annual Computing and Communication Workshop and Conference (CCWC). New York: IEEE, 2022: 922-928. |
| [15] | GUPTA N, NEGI S, RAWAT K, et al. Decentralized and Permission-Aware Blockchain for Certificate Security: An Exploratory Analysis[C]// IEEE. 2024 2nd International Conference on Sustainable Computing and Smart Systems (ICSCSS). New York: IEEE, 2024: 558-562. |
| [16] | DASH S P, JENA A K. An Efficient Approach for Optimizing the CA Selection Search Space in a Blockchain Network[C]// IEEE. 2024 International Conference on Emerging Systems and Intelligent Computing (ESIC). New York: IEEE, 2024: 685-690. |
| [17] | WANG Miaomiao, RUI Lanlan, YANG Yang, et al. A Blockchain-Based Multi-CA Cross-Domain Authentication Scheme in Decentralized Autonomous Network[J]. IEEE Transactions on Network and Service Management, 2022, 19(3): 2664-2676. |
| [18] | MOUSSAOUI D, KADRI B, FEHAM M, et al. A Distributed Blockchain Based PKI (BCPKI)Architecture to Enhance Privacy in VANET[C]// IEEE. 2020 2nd International Workshop on Human-Centric Smart Environments for Health and Well-Being (IHSH). New York: IEEE, 2021: 75-79. |
| [19] | AGURU A D, ERUKALA S B, KAVATI I. Smart Contract Based Next-Generation Public KeyInfrastructure (PKI) Using Permissionless Blockchain[C]// Springer. Hybrid Intelligent Systems (HIS). International Conference on Hybrid Intelligent Systems(HIS). Heidelberg: Springer, 2022: 625-635. |
| [20] | TRAN E, SEN S, ERGUN T. A Semi-Decentralized PKI Based on Blockchain with a Stake-Based Reward-Punishment Mechanism[J]. IEEE Access, 2024, 12: 60705-60721. |
| [21] | GARBA A, HU Qinwen, CHEN Zhong, et al. BB-PKI: Blockchain-Based Public Key Infrastructure Certificate Management[C]// IEEE. 2020 IEEE 22nd International Conference on High Performance Computing and Communications; IEEE 18th International Conference on Smart City(HPCC/SmartCity/DSS). New York: IEEE, 2020: 824-829. |
| [22] | GARBA A, CHEN Zhong, GUAN Zhi, et al. Lightledger: A Novel Blockchain-Based Domain Certificate Authentication and Validation Scheme[J]. IEEE Transactions on Network Science and Engineering, 2021, 8(2): 1698-1710. |
| [23] | RASHID A, MASOOD A, ABBAS H, et al. Blockchain-Based Public Key Infrastructure: A Transparent Digital Certification Mechanism for Secure Communication[J]. IEEE Network, 2021, 35(5): 220-225. |
| [24] | WANG Ze, LIN Jinqiang, CAI Quanwei, et al. Blockchain-Based Certificate Transparency and Revocation Transparency[J]. IEEE Transactions on Dependable and Secure Computing, 2020, 19(1): 681-697. |
| [25] | PENNINO D, PIZZONIA M, VITALETTI A, et al. Efficient Certification of Endpoint Control on Blockchain[J]. IEEE Access, 2021, 9(1): 133309-133334. |
| [26] | KUBILAY M, KIRAZ M S, MANTAR H. CERTLEDGER: A New PKI Model With Certificate Transparency Based on Blockchain[J]. Computers & Security, 2019, 85(1): 333-352. |
| [27] | CHEN Jing, YAO Shixiong, YUAN Quan, et al. CertChain: Public and Efficient Certificate Audit Based on Blockchain for TLS Connections[C]// IEEE. IEEE INFOCOM 2018 - IEEE Conference on Computer Communications(IEEE INFOCOM 2018). New York: IEEE, 2018: 2060-2068. |
| [28] | KHAN S, ZHANG Zijian J, ZHU Liehuang, et al. SCM: Secure and Accountable TLS Certificate Management[EB/OL]. (2020-07-31)[2024-09-24]. https://onlinelibrary.wiley.com/doi/full/10.1002/dac.4503. |
| [29] | YE H, PARK S. Reliable Vehicle Data Storage Using Blockchain and IPFS[J]. Electronics, 2021, 10(10): 1130-1145. |
| [30] | CHEN Yongle, LI Hui, LI Kejiao, et al. An Improved P2P File System Scheme Based on IPFS and Blockchain[C]// IEEE. 2017 IEEE International Conference on Big Data (Big Data). New York: IEEE, 2017: 2652-2657. |
| [31] | FAN Junfeng, VERCAUTEREN F. Somewhat Practical Fully Homomorphic Encryption[EB/OL]. (2012-03-22) [2024-09-24]. https://eprint.iacr.org/2012/144. |
| [32] | BRAKERSKI Z, VAIKUNTANATHAN V. Efficient Fully Homomorphic Encryption from (Standard) LWE[EB/OL]. (2011-08-04) [2024-09-24]. https://eprint.iacr.org/2011/344. |
| [33] | QIN Bo, HUANG Jikun, WANG Qin, et al. Cecoin: A Decentralized PKI Mitigating MitM Attacks[J]. Future Generation Computer Systems, 2017,107:805-815. |
| [34] | DYKCIK L, CHUAT L, SZALACHOWSKI P, et al. BlockPKI:An Automated, Resilient, and Transparent Public-Key Infrastructure[C]// IEEE. 2018 IEEE International Conference on Data Mining Workshops (ICDMW). New York: IEEE, 2018:105-114. |
| [35] | WANG Rong, HE Juan, LIU Can, et al. A Privacy-Aware PKI System Based on Permissioned Blockchains[C]// IEEE. 2018 IEEE 9th International Conference on Software Engineering and Service Science (ICSESS). New York: IEEE, 2018: 928-931. |
| [1] | ZHANG Yuxuan, HUANG Cheng, LIU Rong, LENG Tao. Smart Contract Vulnerability Detection Method Combining Prompt Tuning [J]. Netinfo Security, 2025, 25(4): 664-673. |
| [2] | WANG Yong, WU Yifan, WAN Qiancheng. Research on Redactable Blockchain Scheme Based on the Chinese Remainder Theorem [J]. Netinfo Security, 2025, 25(1): 36-47. |
| [3] | YU Lisu, LI Biao, YAO Yuanzhi, WEN Jiajin, LI Zipeng, WANG Zhen. Performance Optimization of Blockchain-Assisted Unmanned Aerial Vehicle Mobile Edge Computing System [J]. Netinfo Security, 2024, 24(9): 1432-1443. |
| [4] | LYU Qiuyun, ZHOU Lingfei, REN Yizhi, ZHOU Shifei, SHENG Chunjie. A Lifecycle-Manageable Public Data Sharing Scheme [J]. Netinfo Security, 2024, 24(8): 1291-1305. |
| [5] | ZHANG Jiwei, WANG Wenjun, NIU Shaozhang, GUO Xiangkuo. Blockchain Scaling Solutions: ZK-Rollup Review [J]. Netinfo Security, 2024, 24(7): 1027-1037. |
| [6] | GUO Rui, YANG Xin, WANG Junming. Verifiable and Revocable Attribute Encryption Scheme Based on Blockchain [J]. Netinfo Security, 2024, 24(6): 863-878. |
| [7] | LING Zhi, YANG Ming, YU Jiangyin. Research on Power Security Trading Platform Based on IPFS and Blockchain Technology [J]. Netinfo Security, 2024, 24(6): 968-976. |
| [8] | TIAN Zhao, NIU Yajie, SHE Wei, LIU Wei. A Reputation Evaluation Method for Vehicle Nodes in V2X [J]. Netinfo Security, 2024, 24(5): 719-731. |
| [9] | SHI Runhua, YANG Jingyi, WANG Pengbo, LIU Huawei. Online/Off line Cross-Domain Identity Authentication Scheme Based on Blockchain in Vehicle to Grid [J]. Netinfo Security, 2024, 24(4): 587-601. |
| [10] | HU Haiyang, LIU Chang, WANG Dong, WEI Xu. Clean Energy Data Traceability Mechanism Based on Blockchain [J]. Netinfo Security, 2024, 24(4): 626-639. |
| [11] | XUE Mingzhu, HU Liang, WANG Ming, WANG Feng. TAP Rule Processing System Based on Federated Learning and Blockchain Technology [J]. Netinfo Security, 2024, 24(3): 473-485. |
| [12] | ZHAI Peng, HE Jingsha, ZHANG Yu. An Identity Authentication Method Based on SM9 and Blockchain in the IoT Environment [J]. Netinfo Security, 2024, 24(2): 179-187. |
| [13] | HE Yefeng, QUAN Jiahui, LIU Yan. A Location Privacy Protection Scheme Based on Hybrid Blockchain [J]. Netinfo Security, 2024, 24(2): 229-238. |
| [14] | LAN Haoliang, WANG Qun, XU Jie, XUE Yishi, ZHANG Bo. Review of Research on Blockchain-Based Federated Learning [J]. Netinfo Security, 2024, 24(11): 1643-1654. |
| [15] | ZHANG Peng, LUO Wenhua. Blockchain-Based Log Data Provenance Mechanism Using Bloom Filter Search Tree [J]. Netinfo Security, 2024, 24(11): 1739-1748. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||