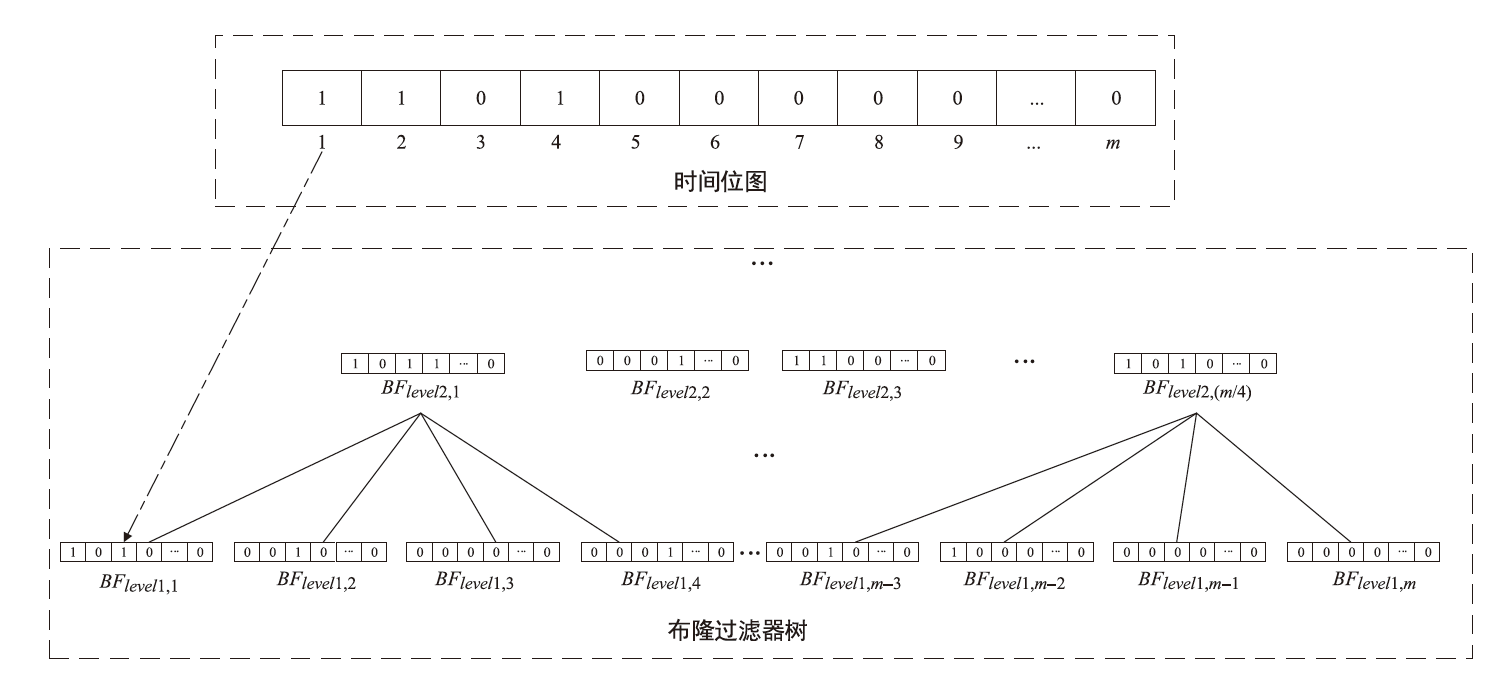
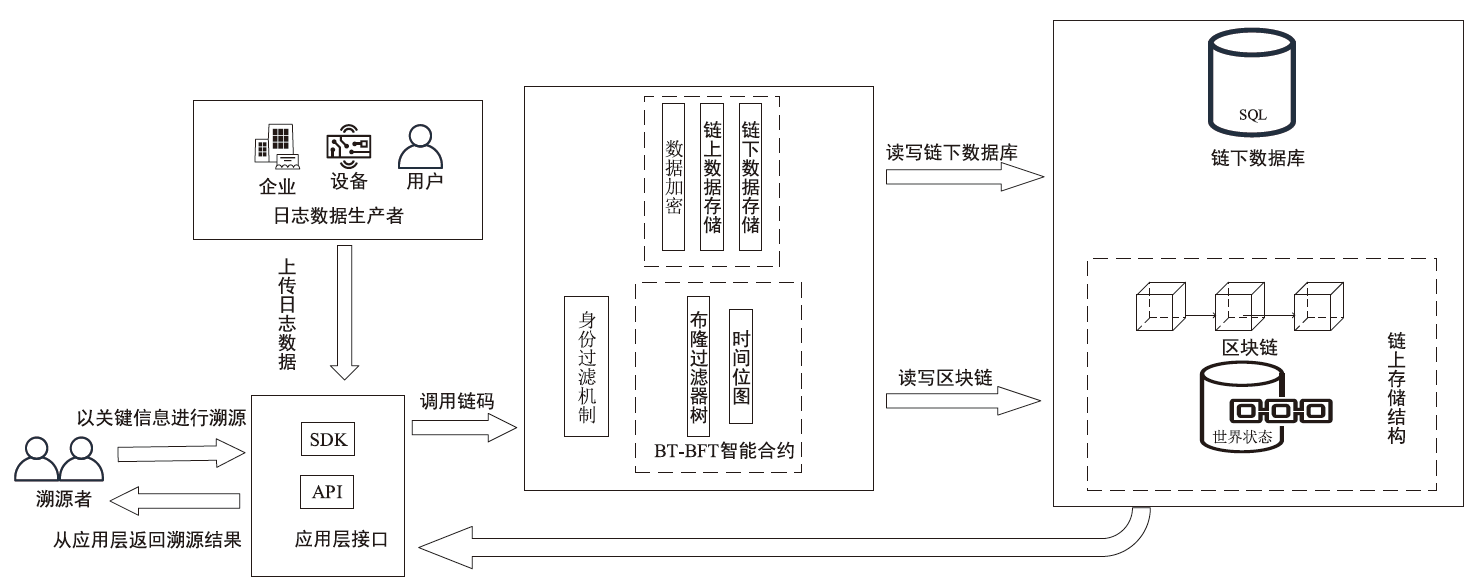
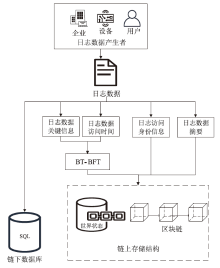
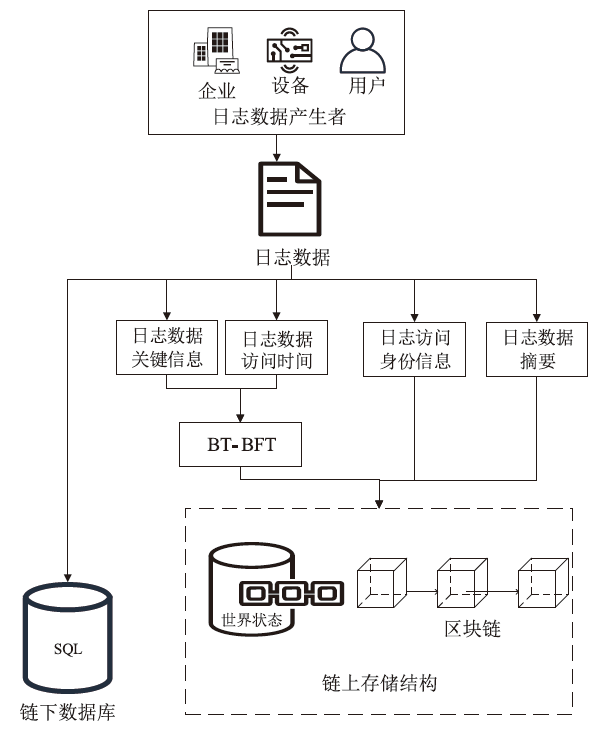
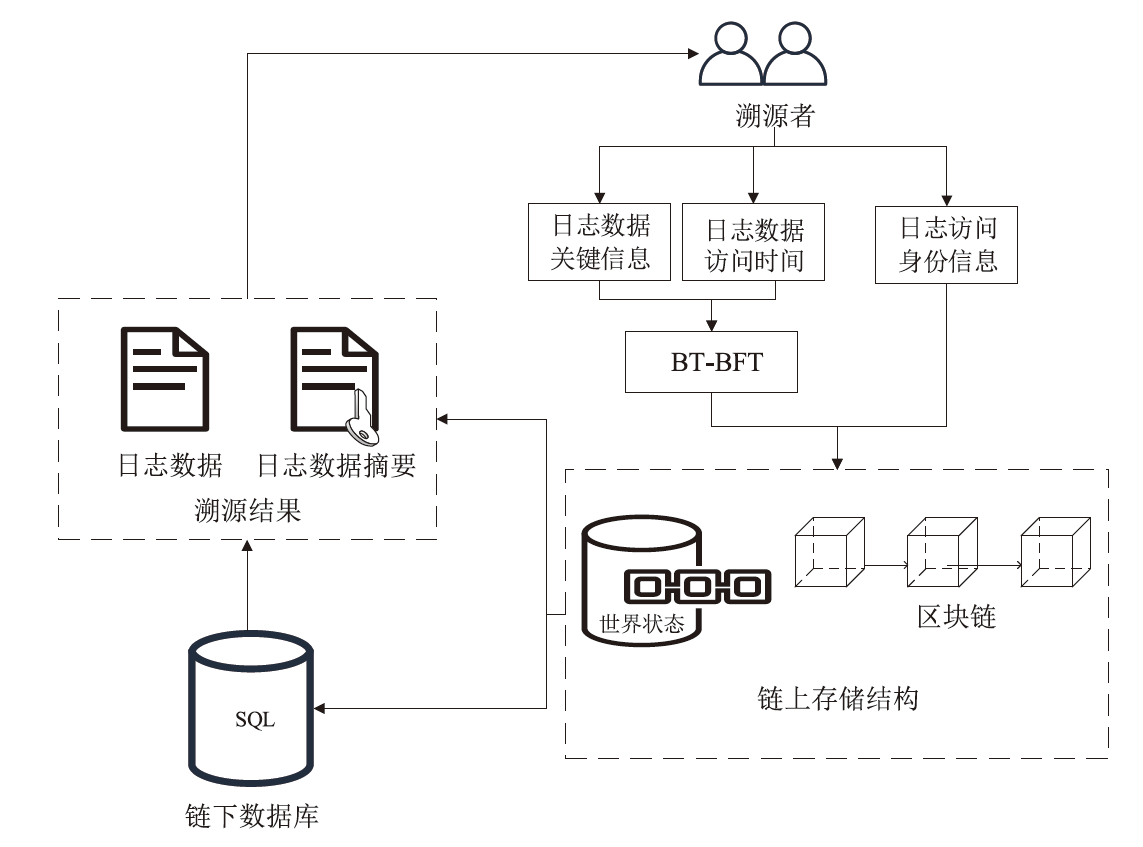
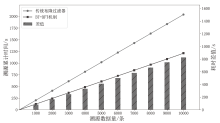
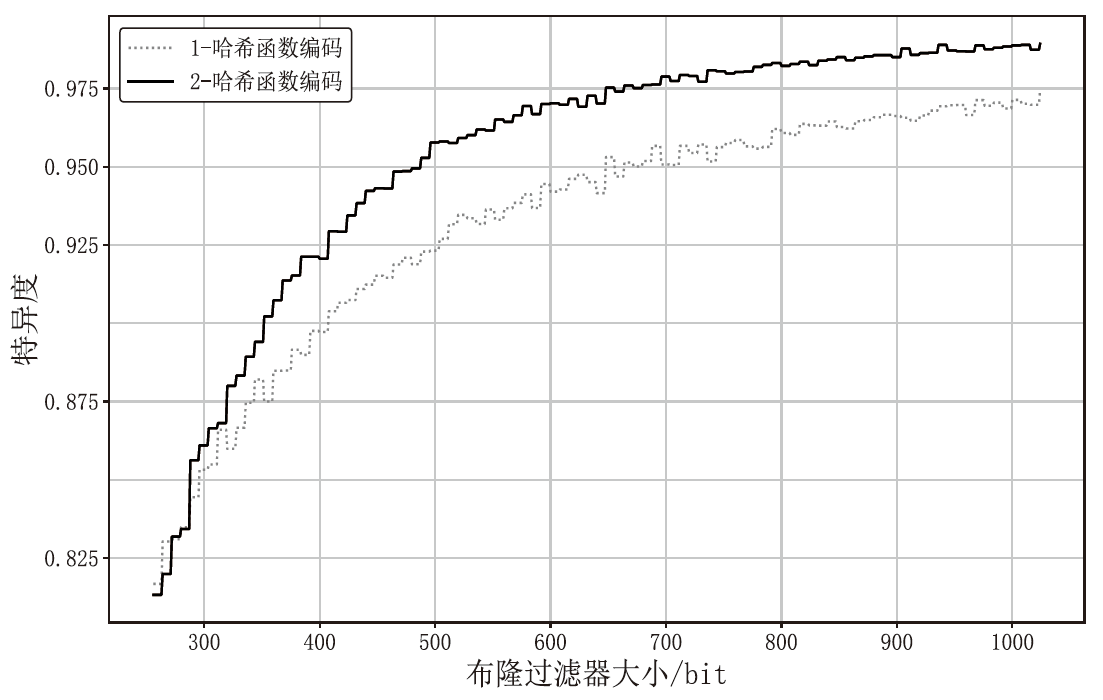
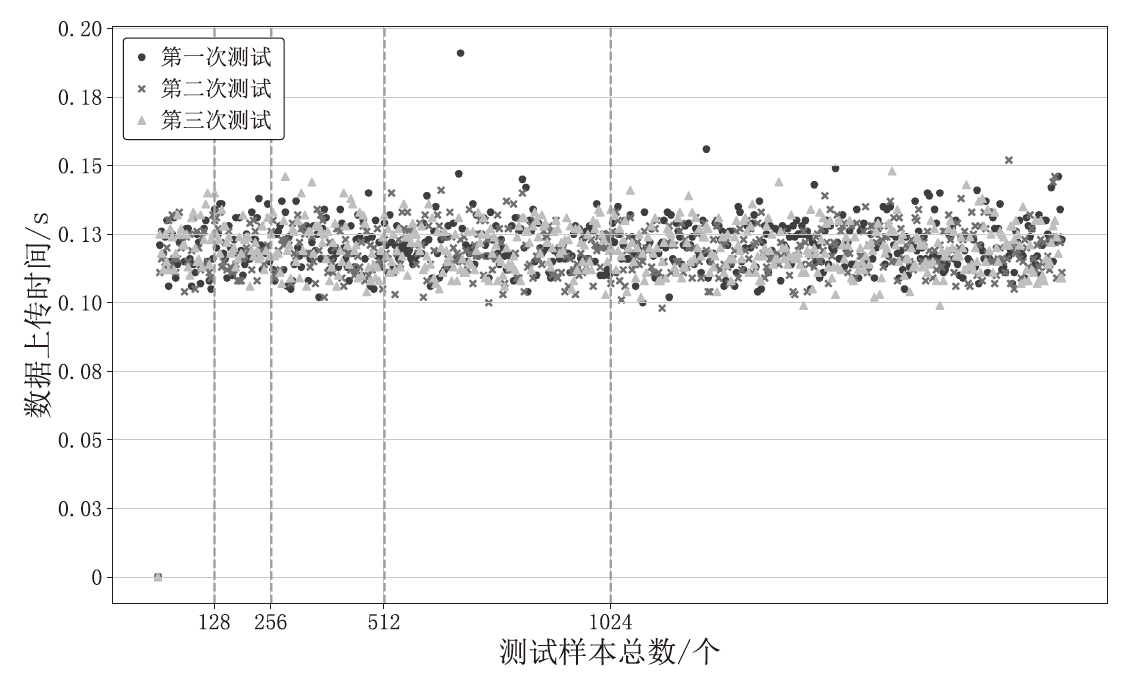
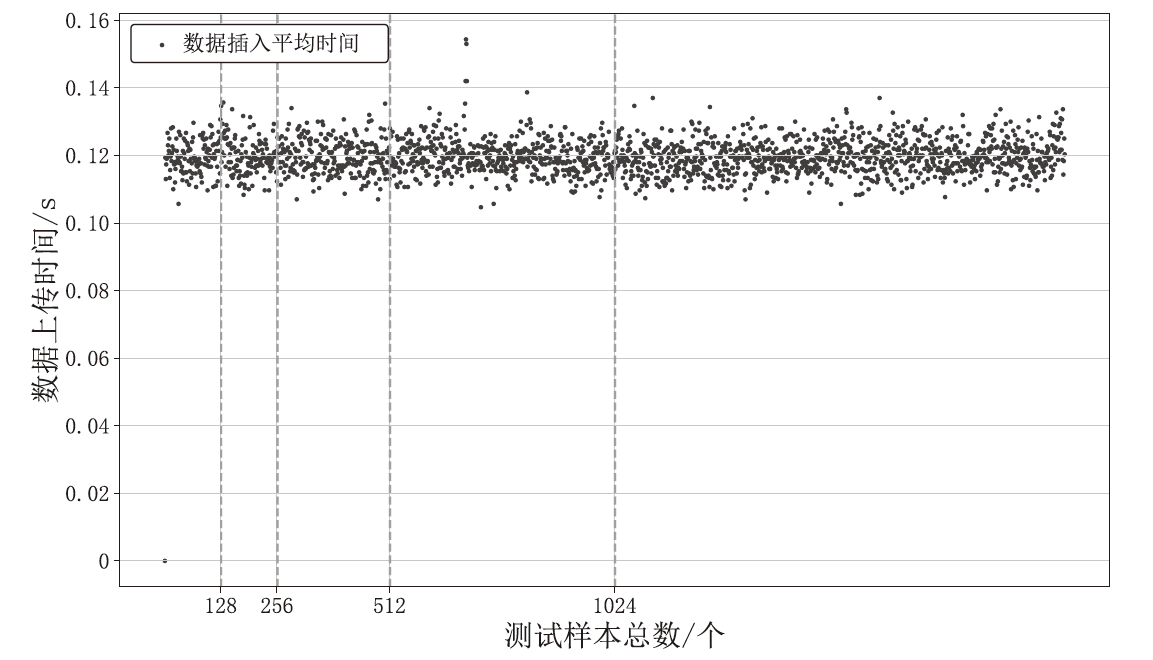
Netinfo Security ›› 2024, Vol. 24 ›› Issue (11): 1739-1748.doi: 10.3969/j.issn.1671-1122.2024.11.013
Previous Articles Next Articles
Blockchain-Based Log Data Provenance Mechanism Using Bloom Filter Search Tree
- School of Public Security Information Technology and Intelligence, Criminal Investigation Police University of China, Shenyang 110035, China
-
Received:2024-04-25Online:2024-11-10Published:2024-11-21
CLC Number:
Cite this article
ZHANG Peng, LUO Wenhua. Blockchain-Based Log Data Provenance Mechanism Using Bloom Filter Search Tree[J]. Netinfo Security, 2024, 24(11): 1739-1748.
share this article
| [1] | QI Wenhao, SUN Meng, HOSSEINI S R A. Facilitating Big-Data Management in Modern Business and Organizations Using Cloud Computing: A Comprehensive Study[J]. Journal of Management & Organization, 2023, 29(4): 697-723. |
| [2] | DUGGINENI S. Impact of Controls on Data Integrity and Information Systems[J]. Science and Technology, 2023, 13(2): 29-35. |
| [3] | SUN Nan, DING Ming, JIANG Jiaojiao, et al. Cyber Threat Intelligence Mining for Proactive Cybersecurity Defense: A Survey and New Perspectives[J]. IEEE Communications Surveys & Tutorials, 2023, 25(3): 1748-1774. |
| [4] | YANG Lisheng, LUO Wenhua. Data Poisoning Defense Based on Sample Distribution Characteristics[J]. Application Research of Computers, 2023, 40(9): 2845-2850. |
| 杨立圣, 罗文华. 基于样本分布特征的数据投毒防御[J]. 计算机应用研究, 2023, 40(9):2845-2850. | |
| [5] | SQUAREPANTS S. Bitcoin: A Peer-to-Peer Electronic Cash System[EB/OL]. (2008-10-31)[2024-03-01]. https://bitcoin.org/en/bitcoin-paper. |
| [6] | YANG Lisheng, LUO Wenhua. Tri-BERT-SENet: Multi-feature Fusion for Malicious Webpage Detection[J]. Small Micro Computer Systems, 2023, 44(4): 875-880. |
| 杨立圣, 罗文华. Tri-BERT-SENet:融合多特征的恶意网页识别[J]. 小型微型计算机系统, 2023, 44(4): 875-880. | |
| [7] | LIU Aodi, DU Xuehui, WANG Na, et al. Research Progress on Blockchain System Security Technolog[J]. Chinese Journal of Computers, 2024, 47(3): 608-646. |
| 刘敖迪, 杜学绘, 王娜, 等. 区块链系统安全防护技术研究进展[J]. 计算机学报, 2024, 47(3): 608-646. | |
| [8] | SI Honghao, NIU Baoning. Research on Blockchain Data Availability and Storage Scalability[EB/OL]. (2023-06-12)[2024-03-01]. https://doi.org/10.3390/fi15060212. |
| [9] | XU Yang, XIAO Shihao, WANG Huiling, et al. Redactable Blockchain-Based Secure and Accountable Data Management[J]. IEEE Transactions on Network and Service Management, 2024, 21(2): 1764-1776. |
| [10] | SARANYA R, MURUGAN A. A Systematic Review of Enabling Blockchain in Healthcare System: Analysis, Current Status, Challenges and Future Direction[J]. Materials Today: Proceedings, 2023, 80(3): 3010-3015. |
| [11] | RAIMUNDO R, ROSÁRIO A. Blockchain System in the Higher Education[J]. European Journal of Investigation in Health, Psychology and Education, 2021, 11(1): 276-293. |
| [12] | ZHOU Yuanjian, QIN Dongmei, LIU Yining, et al. Design of Electronic Warehouse Receipts System Based on Blockchain[J]. Netinfo Security, 2019, 19(6): 84-90. |
| 周元健, 秦冬梅, 刘忆宁, 等. 基于区块链的可信仓单系统设计[J]. 信息网络安全, 2019, 19(6): 84-90. | |
| [13] | DARAGHMI E Y, DARAGHMI Y A, YUAN S M. MedChain: A Design of Blockchain-Based System for Medical Records Access and Permissions Management[J]. IEEE Access, 2019, 7(1): 164595-164613. |
| [14] |
XIE Rongna, LI Hui, SHI Guozhen, et al. Blockchain-Based Access Control Mechanism for Data Traceability[J]. Journal on Communications, 2020, 41(12): 82-93.
doi: 10.11959/j.issn.1000-436X.2020232 |
|
谢绒娜, 李晖, 史国振, 等. 基于区块链的可溯源访问控制机制[J]. 通信学报, 2020, 41(12): 82-93.
doi: 10.11959/j.issn.1000-436X.2020232 |
|
| [15] | POURMAJIDI W, MIRANSKYY A. Logchain: Blockchain-Assisted Log Storage[C]// IEEE. 2018 IEEE 11th International Conference on Cloud Computing. New York: IEEE, 2018: 978-982. |
| [16] | YANG Xinting, LI Mengqi, YU Huajing, et al. A Trusted Blockchain-Based Traceability System for Fruit and Vegetable Agricultural Products[J]. IEEE Access, 2021, 9(1): 36282-36293. |
| [17] | SHEKHTMAN L, WAISBARD E. EngraveChain: A Blockchain-Based Tamper-Proof Distributed Log System[J]. Future Internet, 2021, 13(6): 143-157. |
| [18] | REN Hao, XU Guowen, QI Han, et al. PriFR: Privacy-Preserving Large-Scale File Retrieval System via Blockchain for Encrypted Cloud Data[C]// IEEE. 2023 IEEE 9th International Conference on Big Data Security on Cloud (BigDataSecurity), IEEE International Conference on High Performance and Smart Computing (HPSC) and IEEE International Conference on Intelligent Data and Security (IDS). New York: IEEE, 2023: 16-23. |
| [19] | YAO Zhongming, XIN Junchang, HAO Kun, et al. Learned-Index-Based Semantic Keyword Query on Blockchain[J]. Mathematics, 2023, 11(9): 1-19. |
| [20] | BLOOM B H. Space/Time Trade-Offs in Hash Coding with Allowable Errors[J]. Communications of the ACM, 1970, 13(7): 422-426. |
| [21] | AIGISSINOVA A, LE H H, YOKOTA H. Evaluation of the Performance of Secure Keyword Search Using Bit-String Signatures in the Blockchain[J]. DEIM Forum, 2020, E1(5): 1-8. |
| [22] | XU Gang, YUN Fan, XU Shiyuan, et al. A Blockchain-Based Log Storage Model with Efficient Query[J]. Soft Computing, 2023, 27(19): 13779-13787. |
| [23] |
LYU Jianfu, LAI Yingxu, LIU Jing. Log Security Storage and Retrieval Based on Combination of on-Chain and off-Chain[J]. Computer Science, 2020, 47(3): 298-303.
doi: 10.11896/jsjkx.190200298 |
|
吕建富, 赖英旭, 刘静. 基于链上链下相结合的日志安全存储与检索[J]. 计算机科学, 2020, 47(3): 298-303.
doi: 10.11896/jsjkx.190200298 |
|
| [24] | ZHU Jieming, HE Shilin, HE Pinjia, et al. Loghub: A Large Collection of System Log Datasets for AI-Driven Log Analytics[C]// IEEE. 2023 IEEE 34th International Symposium on Software Reliability Engineering (ISSRE). New York: IEEE, 2023: 355-366. |
| [1] | YU Lisu, LI Biao, YAO Yuanzhi, WEN Jiajin, LI Zipeng, WANG Zhen. Performance Optimization of Blockchain-Assisted Unmanned Aerial Vehicle Mobile Edge Computing System [J]. Netinfo Security, 2024, 24(9): 1432-1443. |
| [2] | LYU Qiuyun, ZHOU Lingfei, REN Yizhi, ZHOU Shifei, SHENG Chunjie. A Lifecycle-Manageable Public Data Sharing Scheme [J]. Netinfo Security, 2024, 24(8): 1291-1305. |
| [3] | ZHANG Jiwei, WANG Wenjun, NIU Shaozhang, GUO Xiangkuo. Blockchain Scaling Solutions: ZK-Rollup Review [J]. Netinfo Security, 2024, 24(7): 1027-1037. |
| [4] | GUO Rui, YANG Xin, WANG Junming. Verifiable and Revocable Attribute Encryption Scheme Based on Blockchain [J]. Netinfo Security, 2024, 24(6): 863-878. |
| [5] | LING Zhi, YANG Ming, YU Jiangyin. Research on Power Security Trading Platform Based on IPFS and Blockchain Technology [J]. Netinfo Security, 2024, 24(6): 968-976. |
| [6] | TIAN Zhao, NIU Yajie, SHE Wei, LIU Wei. A Reputation Evaluation Method for Vehicle Nodes in V2X [J]. Netinfo Security, 2024, 24(5): 719-731. |
| [7] | SHI Runhua, YANG Jingyi, WANG Pengbo, LIU Huawei. Online/Off line Cross-Domain Identity Authentication Scheme Based on Blockchain in Vehicle to Grid [J]. Netinfo Security, 2024, 24(4): 587-601. |
| [8] | HU Haiyang, LIU Chang, WANG Dong, WEI Xu. Clean Energy Data Traceability Mechanism Based on Blockchain [J]. Netinfo Security, 2024, 24(4): 626-639. |
| [9] | XUE Mingzhu, HU Liang, WANG Ming, WANG Feng. TAP Rule Processing System Based on Federated Learning and Blockchain Technology [J]. Netinfo Security, 2024, 24(3): 473-485. |
| [10] | ZHAI Peng, HE Jingsha, ZHANG Yu. An Identity Authentication Method Based on SM9 and Blockchain in the IoT Environment [J]. Netinfo Security, 2024, 24(2): 179-187. |
| [11] | HE Yefeng, QUAN Jiahui, LIU Yan. A Location Privacy Protection Scheme Based on Hybrid Blockchain [J]. Netinfo Security, 2024, 24(2): 229-238. |
| [12] | LAN Haoliang, WANG Qun, XU Jie, XUE Yishi, ZHANG Bo. Review of Research on Blockchain-Based Federated Learning [J]. Netinfo Security, 2024, 24(11): 1643-1654. |
| [13] | WANG Nan, YUAN Ye, YANG Haoran, WEN Zhouzhi, SU Ming, LIU Xiaoguang. Privacy Computing in Environmental Big Data on Blockchain [J]. Netinfo Security, 2024, 24(10): 1515-1527. |
| [14] | WU Haotian, LI Yifan, CUI Hongyan, DONG Lin. Federated Learning Incentive Scheme Based on Zero-Knowledge Proofs and Blockchain [J]. Netinfo Security, 2024, 24(1): 1-13. |
| [15] | ZHU Guocheng, HE Debiao, AN Haoyang, PENG Cong. The Proxy Voting Scheme Based on the Blockchain and SM9 Digital Signature [J]. Netinfo Security, 2024, 24(1): 36-47. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||