Netinfo Security ›› 2025, Vol. 25 ›› Issue (7): 1092-1102.doi: 10.3969/j.issn.1671-1122.2025.07.008
Previous Articles Next Articles
General Construction and Instantiation for Query Request Bandwidth Optimization in Homomorphic Encryption-Based PIR
TIAN Haibo1,2, LI Yitong1, DU Yusong1,2( )
)
- 1. School of Computer Science and Engineering, Sun Yat-sen University, Guangzhou 510006, China
2. Guangdong Provincial Key Laboratory of Information Security Technology, Guangzhou 510006, China
-
Received:2025-04-28Online:2025-07-10Published:2025-08-07 -
Contact:DU Yusong E-mail:duyusong@mail.sysu.edu.cn
CLC Number:
Cite this article
TIAN Haibo, LI Yitong, DU Yusong. General Construction and Instantiation for Query Request Bandwidth Optimization in Homomorphic Encryption-Based PIR[J]. Netinfo Security, 2025, 25(7): 1092-1102.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2025.07.008
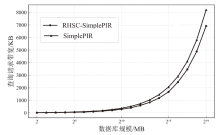
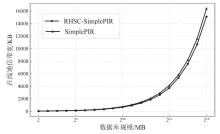
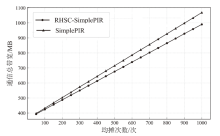
| 数据库 规模 | 指标 | RHSC-SimplePIR | SimplePIR | DoublePIR | Spiral | KsPIR | YPIR |
|---|---|---|---|---|---|---|---|
| 4 MB (225×1) | 离线提示 通信量/MB | 22.6 | 22.6 | 16 | 0 | 0 | 0 |
| 在线上传 通信量/KB | 16 | 22 | 256 | 14 | 140 | 486 | |
| 在线下载 通信量/KB | 22 | 22 | 32 | 14 | 26 | 12 | |
| 吞吐量 (MB/s) | 4455 | 4749 | 3467 | 13 | 30 | 74 | |
| 16 MB (227×1) | 离线提示 通信量/MB | 45.2 | 45.2 | 16 | 0 | 0 | 0 |
| 在线上传 通信量/KB | 33 | 45 | 264 | 14 | 140 | 510 | |
| 在线下载 通信量/KB | 45 | 45 | 32 | 20 | 26 | 12 | |
| 吞吐量 (MB/s) | 4976 | 5107 | 4144 | 35 | 49 | 281 | |
| 64 MB (229×1) | 离线提示 通信量/MB | 90.5 | 90.5 | 16 | 0 | 0 | 0 |
| 在线上传 通信量/KB | 57 | 90 | 288 | 14 | 140 | 558 | |
| 在线下载 通信量/KB | 90 | 90 | 32 | 20 | 26 | 12 | |
| 吞吐量 (MB/s) | 7762 | 7810 | 5125 | 76 | 97 | 969 |
| [1] | CHOR B, KUSHILEVITZ E, GOLDREICH O, et al. Private Information Retrieval[C]// IEEE. IEEE 36th Annual Foundations of Computer Science. New York: IEEE, 1995: 41-50. |
| [2] | KUSHILEVITZ E, OSTROVSKY R. Replication is Not Needed: Single Database, Computationally-Private Information Retrieval[C]// IEEE. 38th Annual Symposium on Foundations of Computer Science. New York: IEEE, 1997: 364-373. |
| [3] | MENON S J, WU D J. YPIR: High-Throughput Single-Server PIR with Silent Preprocessing[C]// USENIX. 33rd USENIX Security Symposium(USENIX Security ’24). Berkeley: USENIX, 2024: 5985-6002. |
| [4] | HENZINGER A, HONG M M, CORRIGAN-GIBBS H, et al. One Server for the Price of Two: Simple and Fast Single-Server Private Information Retrieval[C]// USENIX. 32nd USENIX Security Symposium (USENIX Security ’23). Berkeley: USENIX, 2023: 3889-3905. |
| [5] | GE Yifei, ZHENG Yanbin. Private Information Retrieval Schemes with Erasure-Correcting or Error-Correcting Properties[J]. Journal of Guangxi Teachers Education University(Philosophy and Social Sciences Edition), 2020, 38(3): 33-44. |
| 葛奕飞, 郑彦斌. 带有纠删或纠错性质的隐私保护信息检索方案[J]. 广西师范大学学报(自然科学版), 2020, 38(3):33-44. | |
| [6] | ZHANG Xiaoqing, ZHANG Shuli, LEI Shumei, et al. Analysis and Comparison of Private Information Retrieval Techniques[J]. Communications Technology, 2023, 56(2): 198-206. |
| 张小青, 张舒黎, 雷术梅, 等. 私有信息检索技术分析对比研究[J]. 通信技术, 2023, 56(2):198-206. | |
| [7] | CHI Jialin, FENG Dengguo, ZHANG Min, et al. Advances in Privacy-Preserving Ciphertext Retrieval[J]. Journal of Electronics & Information Technology, 2024, 46(5): 1546-1569. |
| 迟佳琳, 冯登国, 张敏, 等. 隐私保护密文检索技术研究进展[J]. 电子与信息学报, 2024, 46(5):1546-1569. | |
| [8] | AGUILAR-MELCHOR C, BARRIER J, FOUSSE L, et al. XPIR: Private Information Retrieval for Everyone[J]. Proceedings on Privacy Enhancing Technologies, 2016(2): 155-174. |
| [9] | ANGEL S, CHEN Hao, LAINE K, et al. PIR with Compressed Queries and Amortized Query Processing[C]// IEEE. 2018 IEEE Symposium on Security and Privacy (SP). New York: IEEE, 2018: 962-979. |
| [10] | MUGHEES M H, CHEN Hao, REN Ling. OnionPIR: Response Efficient Single-Server PIR[C]// ACM. Proceedings of the 2021 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2021: 2292-2306. |
| [11] | MENON S J, WU D J. Spiral:Fast, High-Rate Single-Server PIR via FHE Composition[C]// IEEE. 2022 IEEE Symposium on Security and Privacy (SP). New York: IEEE, 2022: 930-947. |
| [12] | LUO Ming, LIU Fenghao, WANG Han. Faster FHE-Based Single-Server Private Information Retrieval[C]// ACM. Proceedings of the 2024 on ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2024: 1405-1419. |
| [13] | PARK J, TIBOUCHI M. SHECS-PIR: Somewhat Homomorphic Encryption-Based Compact and Scalable Private Information Retrieval[C]// Springer. Computer Security-ESORICS 2020-25th European Symposium on Research in Computer Security. Heidelberg: Springer, 2020: 86-106. |
| [14] | TIAN Haibo, LIN Yini. An Efficient Private Information Retrieval Protocol Based on TFHE[C]// Springer. EAI SecureComm 2023-19th EAI International Conference on Security and Privacy in Communication Networks. Heidelberg: Springer, 2023: 476-495. |
| [15] | HENZINGER A, DAUTERMAN E, CORRIGAN-GIBBS H, et al. Private Web Search with Tiptoe[C]// ACM. Proceedings of the 29th Symposium on Operating Systems Principles. New York: ACM, 2023: 396-416. |
| [16] | LI Baiyu, MICCIANCIO D, RAYKOVA M, et al. Hintless Single-Server Private Information Retrieval[C]// Springer. Advances in Cryptology-CRYPTO 2024-44th Annual International Cryptology Conference. Heidelberg: Springer, 2024: 183-217. |
| [17] | BECK M. Randomized Decryption (RD) Mode of Operation for Homomorphic Cryptography-Increasing Encryption, Communication and Storage Efficiency[C]// IEEE. 2015 IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS). New York: IEEE, 2015: 220-226. |
| [18] | REGEV O. On Lattices, Learning with Errors, Random Linear Codes, and Cryptography[C]// ACM. The Thirty-Seventh Annual ACM Symposium on Theory of Computing. New York: ACM, 2005: 84-93. |
| [19] | CHILLOTTI I, GAMA N, GEORGIEVA M, et al. TFHE: Fast Fully Homomorphic Encryption over the Torus[J]. Journal of Cryptology, 2020, 33(1): 34-91. |
| [20] | LINDNER R, PEIKERT C. Better Key Sizes (and Attacks) for LWE-Based Encryption[C]// Springer. Topics in Cryptology-CT-RSA 2011: The Cryptographers’ Track at the RSA Conference 2011. Heidelberg: Springer, 2011: 319-339. |
| [1] | CHEN Ping, LUO Mingyu. Research on Large Model Analysis Methods for Kernel Race Vulnerabilities in Cloud-Edge-Device Scenarios [J]. Netinfo Security, 2025, 25(7): 1007-1020. |
| [2] | ZHANG Quanxin, LI Ke, SHAO Yujie, TAN Yu’an. An FPGA-Based Heterogeneous Acceleration System for SM4 Algorithm [J]. Netinfo Security, 2025, 25(7): 1021-1031. |
| [3] | WANG Mei, YANG Xiaoran, LI Zengpeng. Research on Simple and Low Interaction Authentication Protocols for IoT Devices [J]. Netinfo Security, 2025, 25(7): 1032-1043. |
| [4] | LIU Yujing, WANG Zhilin, LI Pengfei, WANG Chengxiao. Analysis Method of Inter-Domain Routing Propagation Characteristics Based on Routing Temporal Betweenness [J]. Netinfo Security, 2025, 25(7): 1044-1052. |
| [5] | ZHANG Guanghua, CHANG Jiyou, CHEN Fang, MAO Bomin, WANG He, ZHANG Jianyan. Firmware Simulation Scheme of IoT Devices Based on Dynamic Substitution of Library Functions [J]. Netinfo Security, 2025, 25(7): 1053-1062. |
| [6] | YANG Wang, MA Mingyu, BIAN Junjing. A Multidimensional Cyber Range Attribute Characterization Model and Similarity Algorithm Based on ATT&CK [J]. Netinfo Security, 2025, 25(7): 1063-1073. |
| [7] | YAN Yukun, TANG Peng, CHEN Rui, DU Ruochen, HAN Qilong. A Randomness Enhanced Bi-Level Optimization Defense Method against Data Poisoning Backdoor Attacks [J]. Netinfo Security, 2025, 25(7): 1074-1091. |
| [8] | LENG Yongqing, AO Tianyong, QIU Xin, CUI Xingli, LI Shaoshi. Design and Implementation of Automatic Assessment System for Cryptographic Criteria of S-Box [J]. Netinfo Security, 2025, 25(7): 1103-1110. |
| [9] | GAO Yang, ZHANG Qi, WANG Chen, XU Jian. Research on New Composable Authenticated Distributed Data Structure Model [J]. Netinfo Security, 2025, 25(7): 1111-1125. |
| [10] |
ZHAO Haixia, LIU Dexiong.
A Multi-Indicator Search Method for RSBF Based on the Matrix |
| [11] | WANG Zhengyang, LIU Xiaolu, SHEN Zhuowei, WEI Mengli. Review of Security Protection Technologies for Multi-Agent Systems [J]. Netinfo Security, 2025, 25(7): 1138-1152. |
| [12] | ZHANG Xuefeng, MIAO Kai. A Progressive Focusing-Based Scheme for Low-Quality Fingerprint Pose Estimation [J]. Netinfo Security, 2025, 25(7): 1153-1162. |
| [13] | FENG Wei, XIAO Wenming, TIAN Zheng, LIANG Zhongjun, JIANG Bin. Research on Semantic Intelligent Recognition Algorithms for Meteorological Data Based on Large Language Models [J]. Netinfo Security, 2025, 25(7): 1163-1171. |
| [14] | ZHAO Bo, PENG Junru, WANG Yixuan. Network Security Situation Assessment Method Based on Threat Propagation [J]. Netinfo Security, 2025, 25(6): 843-858. |
| [15] | SUN Jianwen, ZHANG Bin, SI Nianwen, FAN Ying. Lightweight Malicious Traffic Detection Method Based on Knowledge Distillation [J]. Netinfo Security, 2025, 25(6): 859-871. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||