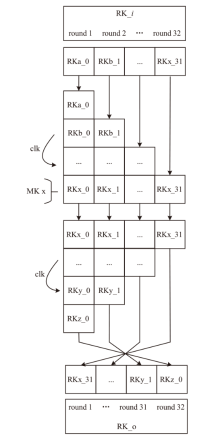
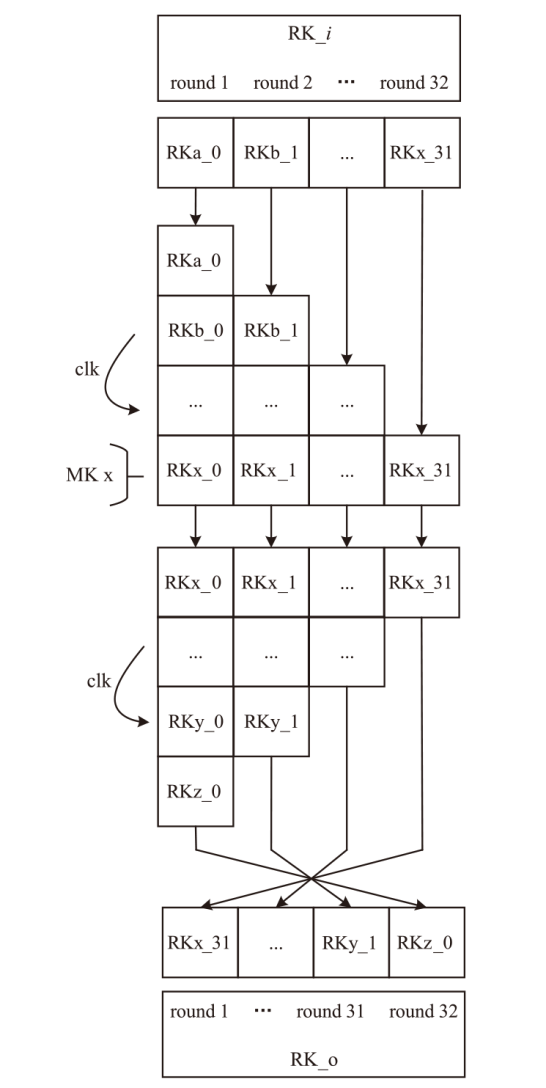
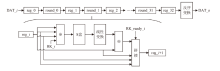
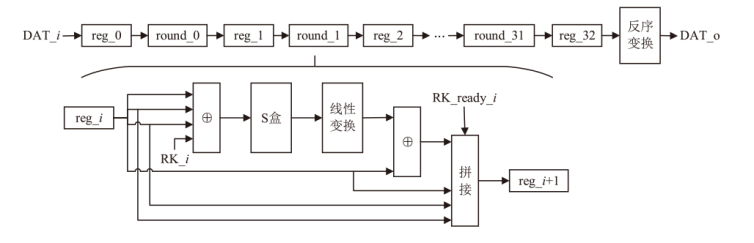
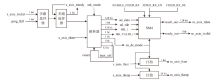
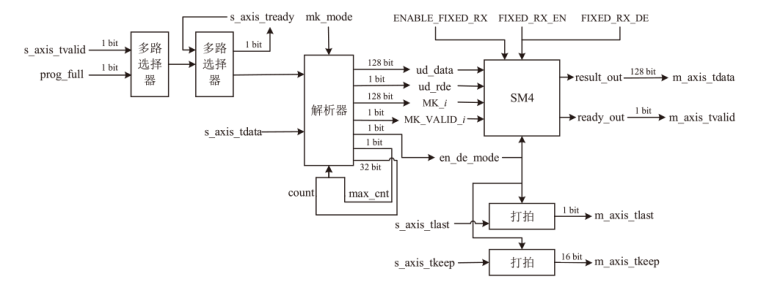
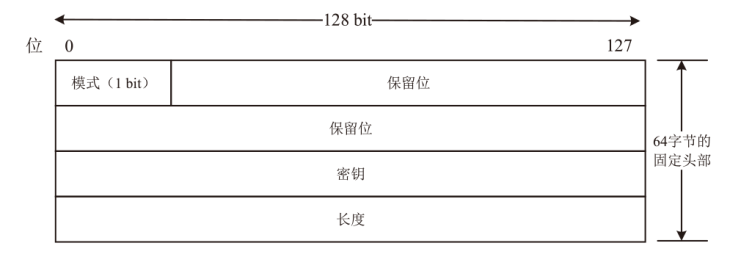
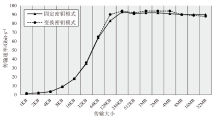
Netinfo Security ›› 2025, Vol. 25 ›› Issue (7): 1021-1031.doi: 10.3969/j.issn.1671-1122.2025.07.002
Previous Articles Next Articles
An FPGA-Based Heterogeneous Acceleration System for SM4 Algorithm
ZHANG Quanxin1, LI Ke1, SHAO Yujie1, TAN Yu’an2( )
)
- 1. School of Computer Science and Technology, Beijing Institute of Technology, Beijing 100081, China
2. School of Cyberspace Science and Technology, Beijing Institute of Technology, Beijing 100081, China
-
Received:2023-07-13Online:2025-07-10Published:2025-08-07 -
Contact:TAN Yu’an E-mail:tan2008@bit.edu.cn
CLC Number:
Cite this article
ZHANG Quanxin, LI Ke, SHAO Yujie, TAN Yu’an. An FPGA-Based Heterogeneous Acceleration System for SM4 Algorithm[J]. Netinfo Security, 2025, 25(7): 1021-1031.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2025.07.002
| [1] | AHMAD S, ARIF M, AHMAD J, et al. Convergent Encryption Enabled Secure Data Deduplication Algorithm for Cloud Environment[EB/OL]. (2022-12-9) [2023-03-16]. https://doi.org/10.1002/cpe.8205. |
| [2] | SEBASTIAN G. Cyber Kill Chain Analysis of Five Major US Data Breaches: Lessons Learnt and Prevention Plan[J]. International Journal of Cyber Warfare and Terrorism (IJCWT), 2022, 12(1): 1-15. |
| [3] | AIVAZPOUR Z, VALECHA R, CHAKRABORTY R. Data Breaches: An Empirical Study of the Effect of Monitoring Services[J]. ACM SIGMIS Database: The DATABASE for Advances in Information Systems, 2022, 53(4): 65-82. |
| [4] |
LANG Huan, ZHANG Lei, WU Wenling. Fast Software Implementation of SM4[J]. Journal of University of Chinese Academy of Sciences, 2018, 35(2): 180-187.
doi: 10.7523/j.issn.2095-6134.2018.02.005 |
|
郎欢, 张蕾, 吴文玲. SM4的快速软件实现技术[J]. 中国科学院大学学报, 2018, 35(2):180-187.
doi: 10.7523/j.issn.2095-6134.2018.02.005 |
|
| [5] | ZHANG Xiaocong, GUO Hua, ZHANG Xiyong, et al. Fast Software Implementation of SM4[J]. Journal of Cryptologic Research, 2020, 7(6): 799-811. |
|
张笑从, 郭华, 张习勇, 等. SM4算法快速软件实现[J]. 密码学报, 2020, 7(6):799-811.
doi: 10.13868/j.cnki.jcr.000407 |
|
| [6] | WANG Lei, GONG Zheng, LIU Zhe, et al. Fast Software Implementation of SM4 Based on Tower Field[J]. Journal of Cryptologic Research, 2022, 9(6): 1081-1098. |
| 王磊, 龚征, 刘哲, 等. 基于塔域的SM4算法快速软件实现[J]. 密码学报, 2022, 9(6):1081-1098. | |
| [7] | JI Zhuoran, ZHANG Zhiyuan, XU Jiming, et al. Accelerating Multi-Scalar Multiplication for Efficient Zero Knowledge Proofs with Multi-GPU Systems[C]// ACM. Proceedings of the 29th ACM International Conference on Architectural Support for Programming Languages and Operating Systems. New York: ACM, 2024: 57-70. |
| [8] | CHENG Wangzhao, ZHENG Fangyu, PAN Wuqiong, et al. High-Performance Symmetric Cryptography Server with GPU Acceleration[C]// Springer. Information and Communications Security:19th International Conference, ICICS 2017. Heidelberg: Springer, 2018: 529-540. |
| [9] | Li Jun, Xie Wenbo, Li Lingchen, et al. Parallel Implementation and Optimization of SM4 Based on CUDA[C]// Springer. Applied Cryptography in Computer and Communications:First EAI International Conference. Heidelberg: Springer, 2021: 93-104. |
| [10] | LI Xiaodong, HU Yiming, CHI Yaping, et al. Parallel Implementation and Optimization of SM4-CTR Algorithm Based on General Computing Platform[J]. Journal of Cryptologic Research, 2022, 9(4): 663-676. |
| 李晓东, 胡一鸣, 池亚平, 等. 基于通用计算平台SM4-CTR算法并行实现与优化[J]. 密码学报, 2022, 9(4):663-676. | |
| [11] | ARMANUZZAMAN M, SADEGHI A R, ZHAO Ziming. Building Your Own Trusted Execution Environments Using FPGA[C]// ACM. Proceedings of the 19th ACM Asia Conference on Computer and Communications Security. New York: ACM, 2024: 1584-1599. |
| [12] | DI M S, ZULBERTI L, LAPENNA F C, et al. A PUF-Based Secure Boot for RISC-V Architectures[C]// Springer. International Conference on Applications in Electronics Pervading Industry, Environment and Society. Heidelberg: Springer, 2023: 87-94. |
| [13] | BOMMANA S R, VEERAMACHANENI S, ERSHAD S, et al. Mitigating Side Channel Attacks on FPGA Through Deep Learning and Dynamic Partial Reconfiguration[J]. Scientific Reports, 2025, 15(1): 1-10. |
| [14] |
ZHAO Jun, GUO Zhichuan, ZENG Xunwen. High Throughput Implementation of SMS4 on FPGA[J]. IEEE Access, 2019, 7: 88836-88844.
doi: 10.1109/ACCESS.2019.2923440 |
| [15] | HE Shiyang, LI Hui, LI Fenghua. FPGA Optimized Implementation of SM4 Algorithm[J]. Journal of Xidian University, 2021, 48(3): 155-162. |
| 何诗洋, 李晖, 李凤华. SM4算法的FPGA优化实现方法[J]. 西安电子科技大学学报, 2021, 48(3):155-162. | |
| [16] |
ZHAI Jiaqi, LI Bin, ZHOU Qinglei, et al. High-Performance Scalable SM4-GCM Algorithm Implementation Based on FPGA[J]. Computer Science, 2022, 49(10): 74-82.
doi: 10.11896/jsjkx.210900137 |
|
翟嘉琪, 李斌, 周清雷, 等. 基于FPGA的高性能可扩展SM4-GCM算法实现[J]. 计算机科学, 2022, 49(10):74-82.
doi: 10.11896/jsjkx.210900137 |
|
| [17] | WANG Kai, LIU Kai, LI Tuo, et al. Design and Implementation of Reconfigurable High-Speed Data Encryption System[J]. Electronic Measurement Technology, 2021, 44(19): 8-15. |
| 王凯, 刘凯, 李拓, 等. 可重构高速数据加密系统设计和实现[J]. 电子测量技术, 2021, 44(19):8-15. | |
| [18] | ZHAO Kun, LIU Wei, MU Qi, et al. PCIe Cryptographic Accelerator Based on Domestic FPGA[C]// IEEE. 2022 International Conference on Computing, Communication, Perception and Quantum Technology (CCPQT). New York: IEEE, 2022: 25-31. |
| [19] | GAO Xianwei, LU Erhong, XIAN Liqin, et al. FPGA Implementation of the SMS4 Block Cipher in the Chinese WAPI Standard[C]// IEEE. 2008 International Conference on Embedded Software and Systems Symposia. New York: IEEE, 2008: 104-106. |
| [20] | JIN Yi’er, SHEN Haibin, YOU Rongquan. Implementation of SMS4 Block Cipher on FPGA[C]// IEEE. 2006 First International Conference on Communications and Networking in China. New York: IEEE, 2006: 1-4. |
| [21] | GUAN Zhenyu, LI Yunhao, SHANG Tao, et al. Implementation of SM4 on FPGA: Trade-off Analysis between Area and Speed[C]// IEEE. 2018 IEEE International Conference on Intelligence and Safety for Robotics (ISR). New York: IEEE, 2018: 192-197. |
| [22] | MOHAMED N A, JABBAR M H. Performance Analysis of Different Neuron Activation Function Implementations on FPGA Using Artificial Neural Network[J]. Evolution in Electrical and Electronic Engineering, 2021, 2(2): 951-958. |
| [23] | CHENG Hai, DING Qun, HUANG Chunguang, et al. Improvements of SM4 Algorithm and Application in Ethernet Encryption System Based on FPGA[J]. Journal of Information Hiding and Multimedia Signal Processing, 2014, 5(3): 518-526. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||