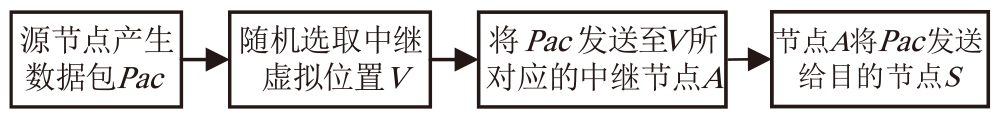
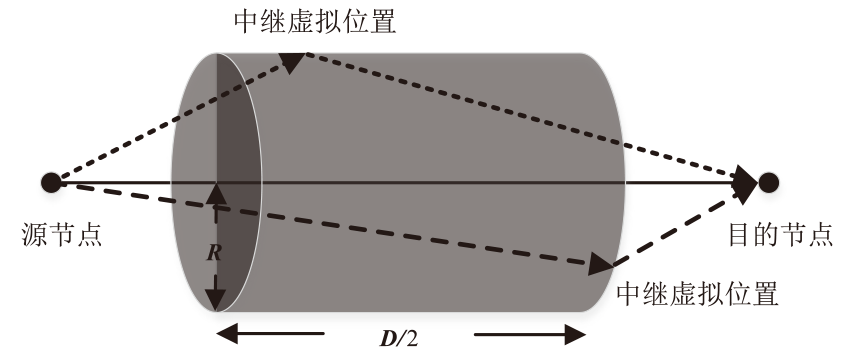
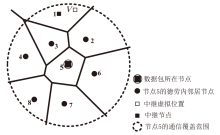
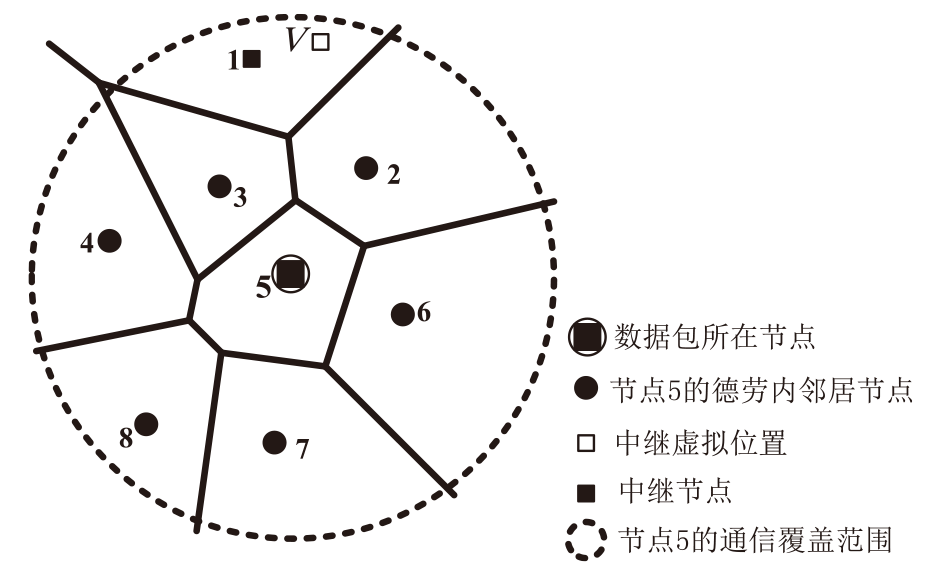
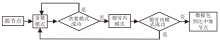
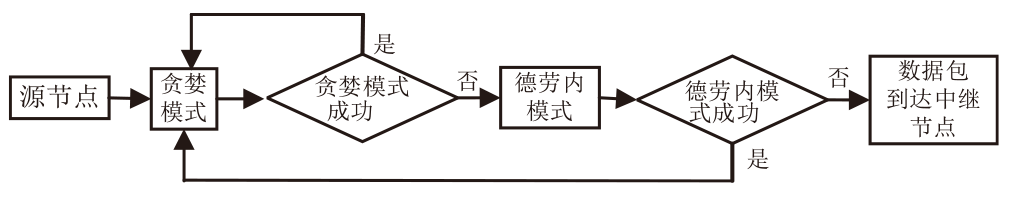
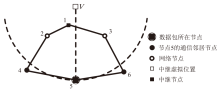
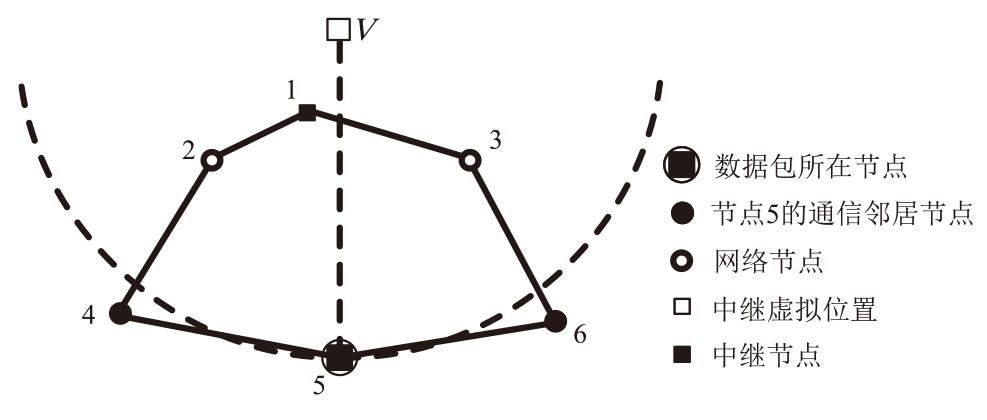
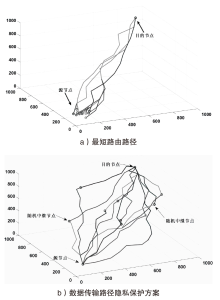
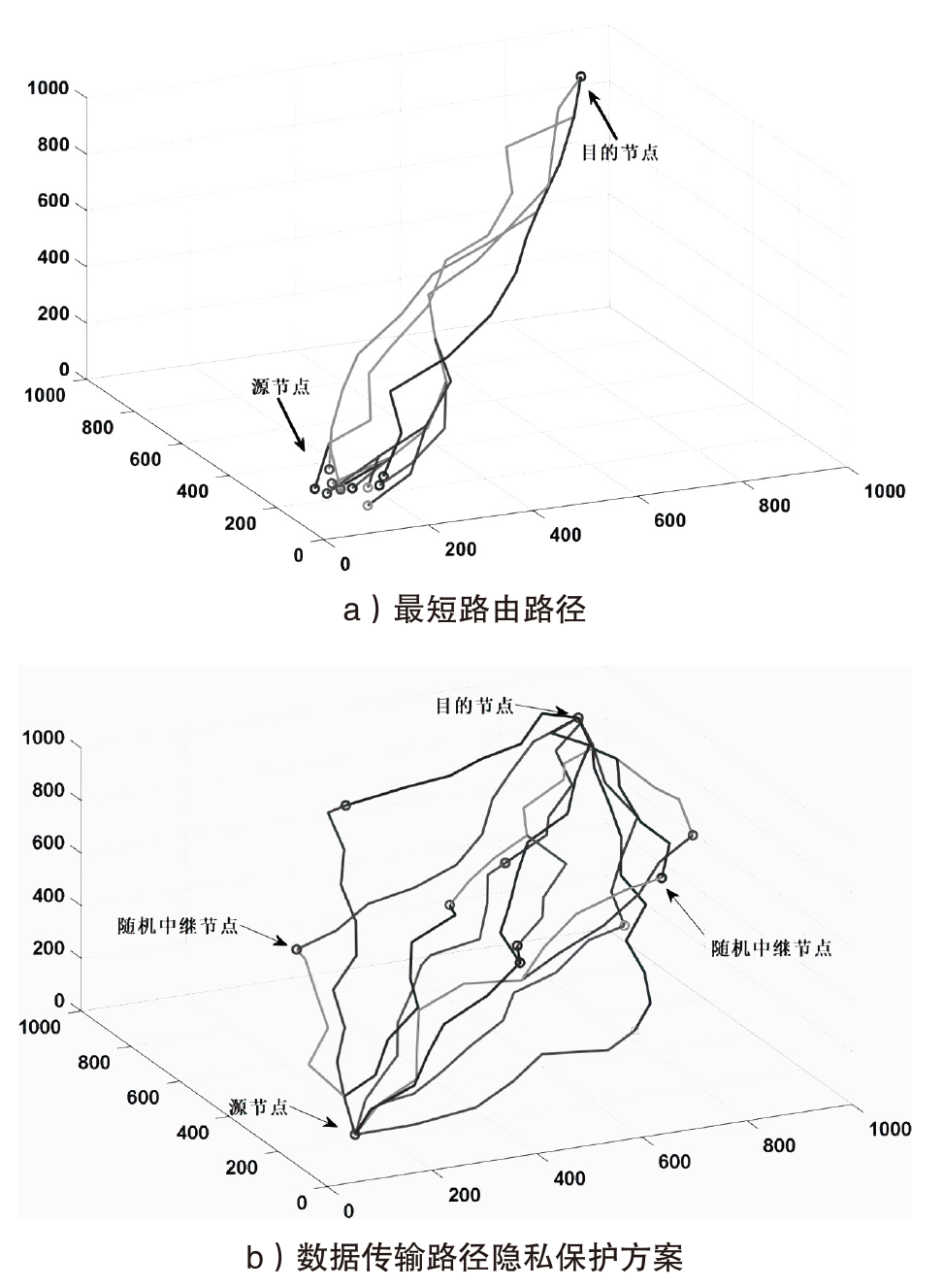
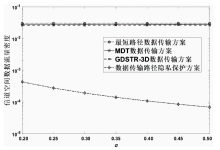
Netinfo Security ›› 2025, Vol. 25 ›› Issue (4): 536-549.doi: 10.3969/j.issn.1671-1122.2025.04.003
Previous Articles Next Articles
Privacy Protection of Data Transmission Paths in 3D Distributed Wireless Intelligent Systems
HU Yuhan1, YANG Gao1( ), CAI Hongye2, FU Junsong1
), CAI Hongye2, FU Junsong1
- 1. School of Cyberspace Security, Beijing University of Posts and Telecommunications, Beijing 100876, China
2. First Research Institute of the Ministry of Public Security of PRC, Beijing 100006, China
-
Received:2024-11-30Online:2025-04-10Published:2025-04-25
CLC Number:
Cite this article
HU Yuhan, YANG Gao, CAI Hongye, FU Junsong. Privacy Protection of Data Transmission Paths in 3D Distributed Wireless Intelligent Systems[J]. Netinfo Security, 2025, 25(4): 536-549.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2025.04.003
| [1] | SHEN Xuemin, CHENG Nan, ZHOU Haibo, et al. Space-Air-Ground Integrated Networks: Review and Prospect[J]. Chinese Journal on Internet of Things, 2020, 4(3): 3-19. |
|
沈学民, 承楠, 周海波, 等. 空天地一体化网络技术:探索与展望[J]. 物联网学报, 2020, 4(3): 3-19.
doi: 10.11959/j.issn.2096-3750.2020.00142 |
|
| [2] | GUO Yike, GUO Liang, CHEN Xiaojie, et al. Typical Applications of Air-Space-Ground Intelligent Perception Technology in Territorial Spatial Planning Implementation and Monitoring[J]. Natural Resources Informatization, 2024(6): 93-100, 116. |
| 郭一珂, 郭亮, 陈小杰, 等. 空天地智能感知技术在国土空间规划实施监测中的典型应用[J]. 自然资源信息化, 2024, (6): 93-100, 116. | |
| [3] | DUAN Junjun. Application of Integrated Intelligent Monitoring System of Air, Sky, and Earth Network in Emergency Response of Natural Disasters[J]. Heilongjiang Science, 2024, 15(24): 139-142. |
| 段俊俊. 空天地网一体化智慧监测体系在自然灾害应急处置中的应用[J]. 黑龙江科学, 2024, 15(24): 139-142. | |
| [4] | ALHAMMADI A, ABRAHAM A, FAKHREDDINE A, et al. Envisioning the Future Role of 3D Wireless Networks in Preventing and Managing Disasters and Emergency Situations[EB/OL]. (2024-02-16)[2024-10-20]. https://arxiv.org/abs/2402.10600. |
| [5] | MARINHO R P, VIEIRA L F M, VIEIRA M A M, et al. SAGIN-CAIN: A 3D Routing Protocol for Post-Disaster SAGIN 6G Network[C]// IEEE.2024 the 20th International Conference on Distributed Computing in Smart Systems and the Internet of Things (DCOSS-IoT). New York: IEEE, 2024: 685-692. |
| [6] | KHAN W, ZUALKERNAN I. SensePods: A ZigBee-Based Tangible Smart Home Interface[J]. IEEE Transactions on Consumer Electronics, 2018: 145-152. |
| [7] | LI Shining, LUO Guojia. Industrial Internet of Things Technology and Application Overview[J]. Telecommunications Network Technology, 2014 (3): 26-31. |
| 李士宁, 罗国佳. 工业物联网技术及应用概述[J]. 电信网技术, 2014 (3): 26-31. | |
| [8] | ZHU Lina, LI Changle, XIA Bing. A Hybrid Routing Protocol for 3-D Vehicular Ad Hoc Networks[J]. IEEE Systems Journal, 2017, 11(3): 1239-1248. |
| [9] | XU Weichao, WANG Guanling, CHEN Mengyuan. Node Localization of Wireless Sensor Networks Based on SR-CKF Assisted by Unmanned Aerial Vehicle[J]. CAAI Transactions on Intelligent Systems, 2019, 14(3): 575-581. |
| 徐魏超, 王冠凌, 陈孟元. 无人机协助下基于SR-CKF 的无线传感器网络节点定位研究[J]. 智能系统学报, 2019, 14(3): 575-581. | |
| [10] | MORIDI M, KAWAMURA Y, SHARIFZADEH M, et al. Performance Analysis of ZigBee Network Topologies for Underground Space Monitoring and Communication Systems[J]. Tunnelling & Underground Space Technology, 2018, 71: 201-209. |
| [11] | YAN Jing, YANG Xian, LUO Xiaoyuan, et al. Energy-Efficient Data Collection over AUV-Assisted Underwater Acoustic Sensor Network[J]. IEEE Systems Journal, 2018, 12(4): 3519-3530. |
| [12] | OZDEMIR S, CAM H. Integration of False Data Detection with Data Aggregation and Confidential Transmission in Wireless Sensor Networks[J]. IEEE/ACM Transactions on Networking, 2010, 18(3): 736-749. |
| [13] | MAHMOUD M, LIN Xiaodong, SHEN Xuemin. Secure and Reliable Routing Protocols for Heterogeneous Multihop Wireless Networks[J]. IEEE Transactions on Parallel and Distributed. Systems, 2015, 26(4): 1140-1153. |
| [14] | QIN Danyang, YANG Songxiang, JIA Shuang, et al. Research on Trust Sensing Based Secure Routing Mechanism for Wireless Sensor Network[J]. IEEE Access, 2017, 5: 9599-9609. |
| [15] | LIU Anfeng, ZHENG Zhongming, ZHANG Chao, et al. Secure and Energy-Efficient Disjoint Multipath Routing for WSNs[J]. IEEE Transactions on Vehicle Technology, 2012, 61(7): 3255-3265. |
| [16] | MAHMOUD M, SHEN Xuemin. A Cloud-Based Scheme for Protecting Source-Location Privacy against Hotspot-Locating Attack in Wireless Sensor Networks[J]. IEEE Transactions on Parallel Distributed System, 2012, 23(10): 1805-1818. |
| [17] |
FAN Chaoqiong, ZHAO Chenglin, LI Bin. Hierarchical Game Based Spectrum Access Optimization for Anti-Jamming in UAV Network[J]. Journal on communications, 2020, 41(6): 26-33.
doi: 10.11959/j.issn.1000-436x.2020114 |
|
范超琼, 赵成林, 李斌. 无人机网络中基于分层博弈的干扰对抗频谱接入优化[J]. 通信学报, 2020, 41(6): 26-33.
doi: 10.11959/j.issn.1000-436x.2020114 |
|
| [18] | WANG Na, FU Junsong, LI Jian, et al. Source-Location Privacy Protection Based on Anonymity Cloud in Wireless Sensor Networks[J]. IEEE Transactions on Information Forensics and Security, 2020, 15: 100-114. |
| [19] | WANG Na, FU Junsong, ZENG Jiwen, et al. Source-Location Privacy Full Protection in Wireless Sensor Networks[J]. Information Sciences, 2018, 444: 105-121. |
| [20] | BICAKCI K, GULREKIN H, TAVLI B, et al. Maximizing Lifetime of Event-Unobservable Wireless Sensor Networks[J]. Computing Standards Interfaces, 2011, 33(4): 401-410. |
| [21] | KARP B, KUNG H. GPSR: Greedy Perimeter Stateless Routing for Wireless Networks[C]// ACM.MobiCom00:The 6th Annual International Conference on Mobile Computing and Networking. New York: ACM, 2000, 243-254. |
| [22] | INTANAGONWIWAT C, GOVINDAN R, ESTRIN D, et al. Directed Diffusion for Wireless Sensor Networking[J]. IEEE/ACM Transactions on Networking, 2003, 11(1):2-16. |
| [23] | KAMAT P, ZHANG Y, TRAPPE W, et al. Enhancing Source Location Privacy in Sensor Network Routing[C]// IEEE. The 25th IEEE International Conference on Distributed Computing Systems (ICDCS'05). New York: IEEE, 2005, 599-608. |
| [24] | WANG Na, ZENG Jiwen. All-Direction Random Routing for Source-Location Privacy Protecting Against Parasitic Sensor Networks[J]. Sensors, 2017, 17(3): 614-631. |
| [25] | ALOMAIR B, CLARK A, CUELLAR J, et al. Toward a Statistical Framework for Source Anonymity in Sensor Networks[J]. IEEE Transactionson Mobile Computing. 2013, 12(2): 248-260. |
| [26] | YANG Yi, SHAO Min, ZHU Sencun, et al. Towards Statistically Strong Source Anonymity for Sensor Networks[J]. ACM Transactions on Sensor Networks (TOSN), 2013, 9(3): 1-23.. |
| [27] | HAN Youjia, HU Huangshui, GUO Yuxin. Energy-Aware and Trust-Based Secure Routing Protocol for Wireless Sensor Networks Using Adaptive Genetic Algorithm[J]. IEEE Access, 2022, 10: 11538-11550. |
| [28] | JI Baofeng, ZHANG Mingkun, XING Ling, et al. Research on Optimal Intelligent Routing Algorithm for IoV with Machine Learning and Smart Contract[J]. Digital Communications and Networks, 2023, 9(1): 47-55. |
| [29] | ZHOU Jiangwei, CHEN Yu, LEONG B, et al. Practical 3D Geographic Routing for Wireless Sensor Networks[C]. // ACM.SenSys '10: Proceedings of the 8th ACM Conference on Embedded Networked Sensor Systems. New York: ACM, 2010: 337-350. |
| [30] | LAM S, QIAN Chen. Geographic Routing in D-Dimensional Spaces with Guaranteed Delivery and Low Stretch[J]. ACM SIGMETRICS Performance Evaluation Review, 2011, 39(1): 217-228. |
| [31] | LEONG B, LISKOV B, MORRIS R T. Geographic Routing Without Planarization[C]// USENIX.NSDI ’06: 3rd Symposium on Networked Systems Design & Implementation.California:USENIX, 2006: 339-352. |
| [32] | FU Junsong, CUI Baojiang, WANG Na, et al. A Distributed Position-Based Routing Algorithm in 3-D Wireless Industrial Internet of Things[J]. IEEE Transactions on Industrial Informatics, 2019, 15(10): 5664-5673. |
| [33] | ZHENG Shannong, HUO Jiuyuan, YANG Jiguang, et al. An Energy-Efficient Multi-Hop Routing Protocol for 3D Bridge Wireless Sensor Network Based on Secretary Bird Optimization Algorithm[J]. IEEE Sensors Journal, 2024: 38045-38060. |
| [34] | REN Z, HUSSAIN K, FAHEEM M. K-Means Online-Learning Routing Protocol (K-MORP) for Unmanned Aerial Vehicles (UAV) Adhoc Networks[EB/OL]. (2024-03-01)[2024-10-20]. https://doi.org/10.1016/j.adhoc.2023.103354. |
| [35] | LE D P C, WANG Dong, TU N H. Power Efficiency Optimization and Enhanced Connectivity for Wireless Sensor Networks with the Fuzzy C-Means 3D Model[EB/OL]. (2024-02-03)[2024-10-20]. https://www.preprints.org/manuscript/202402.0462/download/final_file. |
| [36] |
QIAN Kaiguo, BU Chunfen, WANG Yujian, et al. Reliable Beacon-Based and Density-Aware Distance Localization Algorithm for Wireless Sensor Network[J]. Journal of Computer Applications, 2019 (3): 817-823.
doi: 10.11772/j.issn.1001-9081.2018071661 |
|
钱开国, 卜春芬, 王玉见, 等. 基于可靠信标和节点度估计距离的无线传感器网络定位算法[J]. 计算机应用, 2019 (3): 817-823.
doi: 10.11772/j.issn.1001-9081.2018071661 |
|
| [37] | ZHANG Yanchao, LIU Wei, FANG Yuguang, et al. Secure Localization and Authentication in Ultra-Wideband Sensor Networks[J]. IEEE Journal of Selected Areas Communication, 2006, 24(4): 829-835. |
| [38] | CHENG Xiuzhen, THAELE A, XUE Guoliang, et al. TPS: A Time-Based Positioning Scheme for Outdoor Wireless Sensor Networks[J]. IEEE INFOCOM, 2004, 2685-2696. |
| [39] | ZHOU Peide. Computational Geometry: Algorithm Analysis and Design[M]. Beijing: Tsinghua University Press, 2000. |
| 周培德. 计算几何:算法分析与设计[M]. 北京: 清华大学出版社, 2000. |
| [1] | LI Tao, BI Yue, HU Aiqun. Insider Threat Multi-Source Log Analysis and Detection Method for Intelligent Systems [J]. Netinfo Security, 2025, 25(4): 509-523. |
| [2] | LI Xiao, SONG Xiao, LI Yong. Research on Differential Privacy Methods for Medical Diagnosis Based on Knowledge Distillation [J]. Netinfo Security, 2025, 25(4): 524-535. |
| [3] | ZHANG Xuewang, LU Hui, XIE Haofei. A Data Augmentation Method Based on Graph Node Centrality and Large Model for Vulnerability Detection [J]. Netinfo Security, 2025, 25(4): 550-563. |
| [4] | WANG Fangyuan, LIAN Zhichao, LI Qianmu, GU Huanhuan, ZHAO Qian. Research on Malicious Websites Assessment Method Based on Multidimensional Features and PageRank Optimization [J]. Netinfo Security, 2025, 25(4): 564-577. |
| [5] | LI Yuancheng, SUN Heyang, ZHANG Tong, ZHANG Hefang, YANG Liqun. DACDiff-Based Defense against FDIAs in Distributed Generation Dispatch and Control System [J]. Netinfo Security, 2025, 25(4): 578-586. |
| [6] | WEI Chaoren, XIA Wanxu, QU Gang, BAI Wanrong, YANG Liqun. Research on the Optimization Technology of Open Source Fuzzing Framework for Intelligent Systems [J]. Netinfo Security, 2025, 25(4): 587-597. |
| [7] | WANG Shun, QIU Han, HE Ying. A Safety and Security Co-Analysis and Assessment Method for Intelligent Connected Vehicles Based on Ontology and Attack-Fault Tree [J]. Netinfo Security, 2025, 25(4): 598-609. |
| [8] | XING Hantao, RUAN Shuhua, CHEN Liangguo, ZENG Xuemei. Log Parsing Method Based on Semantic of Parameters [J]. Netinfo Security, 2025, 25(4): 610-618. |
| [9] | GU Huanhuan, LI Qianmu, LIU Zhen, WANG Fangyuan, JIANG Yu. Research on Hidden Backdoor Prompt Attack Methods Based on False Demonstrations [J]. Netinfo Security, 2025, 25(4): 619-629. |
| [10] | HE Ke, WANG Jianhua, YU Dan, CHEN Yongle. Adaptive Sampling-Based Machine Unlearning Method [J]. Netinfo Security, 2025, 25(4): 630-639. |
| [11] | YANG Yatao, DING Yucheng, LIU Peihe, SANG Peng. Research on Blockchain-Based Privacy Preservation and Digital Authentication [J]. Netinfo Security, 2025, 25(4): 640-653. |
| [12] | CHANG Zhenxuan, ZHENG Zhihan, MEI Aohan, TAN Yu’an. An Efficient Gray-Box Fuzzing Approach for Firmware Network Applications [J]. Netinfo Security, 2025, 25(4): 654-663. |
| [13] | ZHANG Yuxuan, HUANG Cheng, LIU Rong, LENG Tao. Smart Contract Vulnerability Detection Method Combining Prompt Tuning [J]. Netinfo Security, 2025, 25(4): 664-673. |
| [14] | XU Zhishuang, ZHANG Kun, FAN Junchao, CHANG Xiaolin. Construction Method of Cybersecurity Knowledge Graph Based on Ontology [J]. Netinfo Security, 2025, 25(3): 451-466. |
| [15] | QIN Guangxue, LI Lisha. ARX Block Cipher Distinguisher Based on Quantum Convolutional Neural Network [J]. Netinfo Security, 2025, 25(3): 467-477. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||