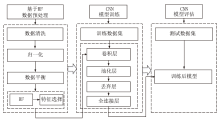
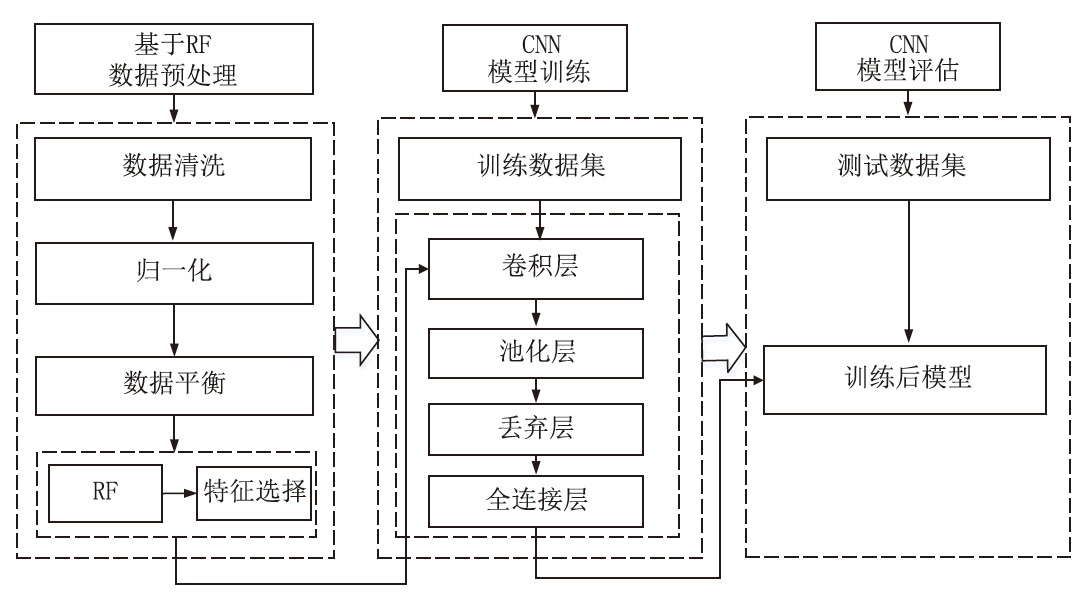
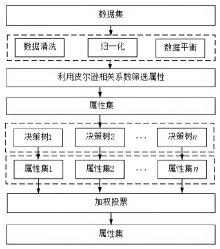
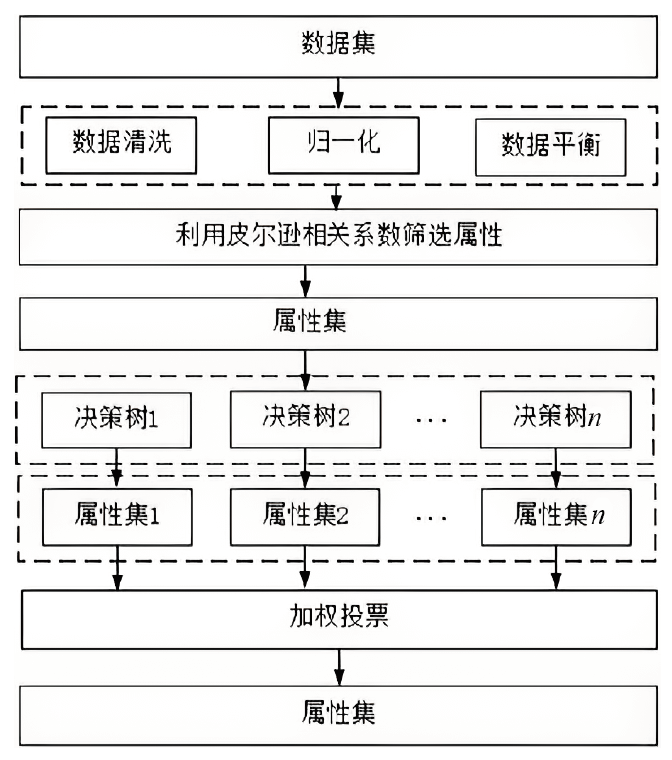
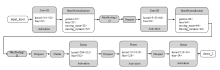
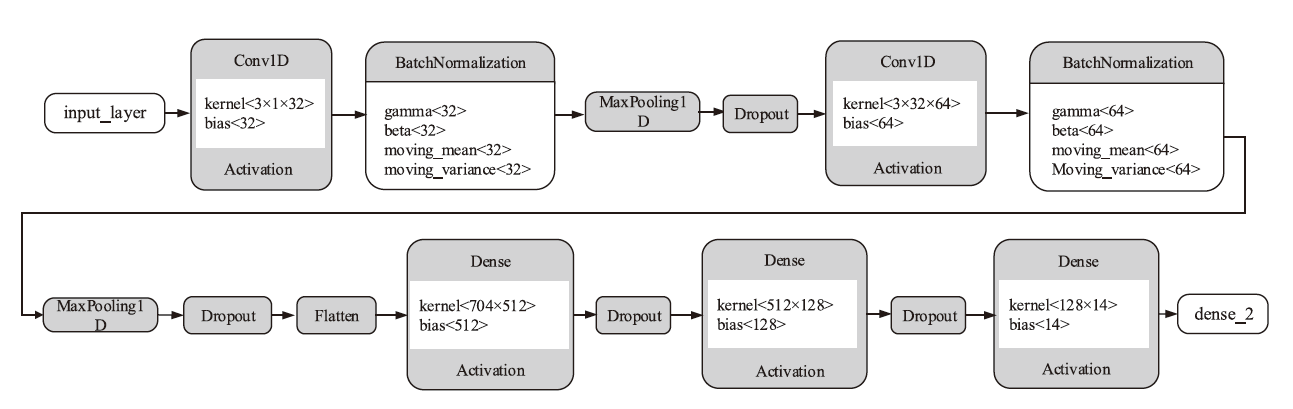
Netinfo Security ›› 2024, Vol. 24 ›› Issue (11): 1655-1664.doi: 10.3969/j.issn.1671-1122.2024.11.005
Previous Articles Next Articles
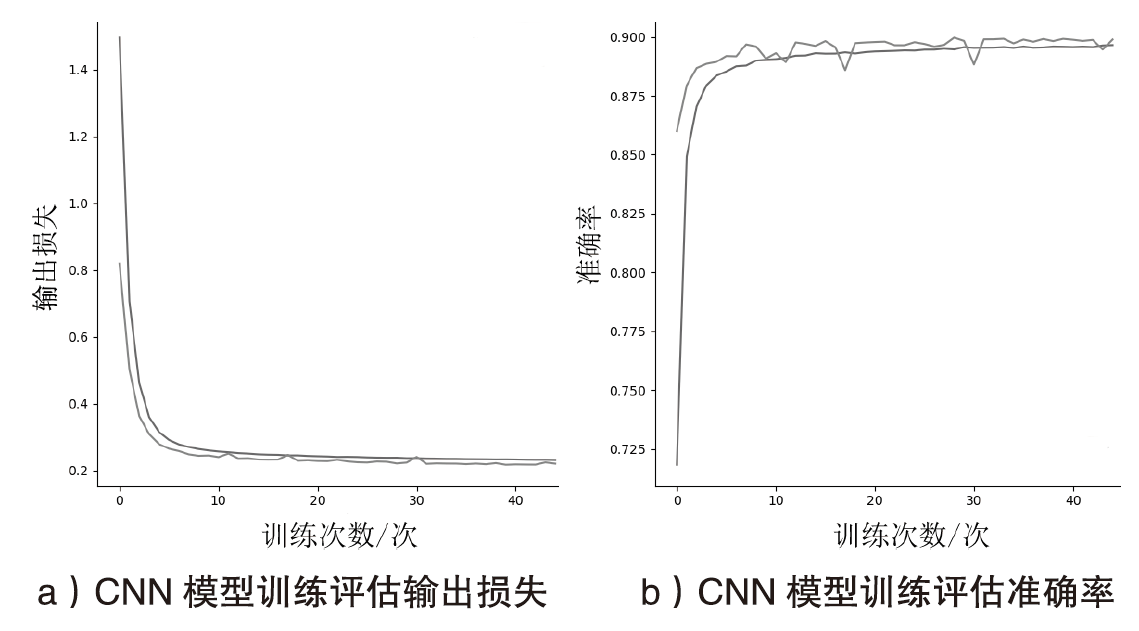
Anomaly Traffic Detection Algorithm Integrating RF and CNN
- Department of Network Security, Shanxi Police College, Taiyuan 030401, China
-
Received:2024-06-16Online:2024-11-10Published:2024-11-21
CLC Number:
Cite this article
ZHANG Zhiqiang, BAO Yadong. Anomaly Traffic Detection Algorithm Integrating RF and CNN[J]. Netinfo Security, 2024, 24(11): 1655-1664.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2024.11.005
| 算法分类 | 主要优点 | 主要缺点 |
|---|---|---|
| 卷积神经网络(CNN) | CNN能够自动学习输入数据中的层次特征,能够捕捉网络流量中的模式 | 不适合时间序列数据,虽然可以使用一维CNN处理时间序列数据,但不如专门为此设计的模型有效;CNN的训练过程在处理大规模数据集时,可能需要大量的计算资源 |
| 循环神经网络(RNN)/长短期记忆网络(LSTM) | RNN特别是LSTM适合处理带有时间依赖性的数据,LSTM能够很好捕捉上下文信息 | 训练难度大,RNN容易受到梯度消失或爆炸的问题,而LSTM虽然有所改善,但仍需要小心调参;由于RNN是按顺序处理数据的,所以处理速度较慢,尤其是在长序列的情况下 |
| 自编码器(AE)/变分自编码器(VAE) | 适用于大量未标记的网络流量数据。能够将高维数据映射到低维空间,有助于发现隐藏的模式 | 仅仅依赖重建误差来检测异常可能会忽略一些重要的特征。在面对未曾见过的新类型异常时,自编码器可能无法很好地泛化 |
| 生成对抗网络(GAN) | 能够生成逼真的正常流量数据,帮助检测异常。能够适应不断变化的流量模式 | 稳定性差,训练GAN的过程可能不稳定,需要仔细调整超参数;对于异常检测任务,GAN的性能难以量化 |
| 图神经网络(GNN) | 非常适合处理网络拓扑结构中的数据,能够捕捉节点间的相互作用,对于检测基于拓扑的异常非常有用 | 数据准备复杂,需要将数据转换为图的形式,过程复杂;相比于其他模型,GNN的训练效率较低 |
| 深度信念网络(DBN) | 具有自动提取层次化特征的能力,减少了人工特征工程的需求;采用无监督预训练的方法,能够有效初始化模型,从而改善后续的有监督学习过程 | DBN 的训练过程相对复杂,需要多阶段的训练,这增加了模型的训练难度。同时对计算资源的需求较高,训练和推理时可能面临较大的计算负担 |
| 算法分类 | 时间复杂度 | 参数说明 |
|---|---|---|
| CNN | O(N×K2×C×H×W×L)+ O(K×H'×W'×L) | 输入数据的尺寸为H×W×C,卷积层的数量为L,每个卷积层的卷积核数量为K,H'和W'是输出特征图的高度和宽度 |
| 融合RF和 CNN | O(T×N×log2N+T×F×log2F)+ O(N×K2×C×H'×W'×L)+ O(K×H''×W''×L+T×N) | T表示RF树的数量,N表示样本数量,F表示特征数量。H'和W'是基于选择特征的输入数据的高度和宽度。H''×W''表示CNN输出特征图的大小 |
| RF | O(T×N×d)+O(T×d) | T表示树的数量,N表示数据集中样本数量,d表示树的平均深度 |
| 决策树 | O(N×M×log2N)+O(log2N) | N表示样本数,M表示特征数,logN为树的深度 |
| K均值聚类 | O(K×N×I×M)+O(K×N×M) | K为聚类的数量,N是样本数,I是迭代次数,M是特征数 |
| [1] |
ZHANG Hongbin, YIN Yan, ZHAO Dongmei, et al. Network Security Situational Awareness Model Based on Threat Intelligence[J]. Journal on Communications, 2021, 42(6): 182-194.
doi: 10.11959/j.issn.1000-436x.2021106 |
|
张红斌, 尹彦, 赵冬梅, 等. 基于威胁情报的网络安全态势感知模型[J]. 通信学报, 2021, 42(6): 182-194.
doi: 10.11959/j.issn.1000-436x.2021106 |
|
| [2] | PANDA M, PATRA M R. Network Intrusion Detection Using Naive Bayes[J]. International Journal of Computer Science and Network Security, 2007, 7(12): 258-263. |
| [3] | MEHEDI H M A, NASSER M, PAL B, et al. Support Vector Machine and Random Forest Modeling for Intrusion Detection System (IDS)[J]. Journal of Intelligent Learning Systems and Applications, 2014, 6(1): 45-52. |
| [4] | DA T, QU Y R, PRASANNA V K. Accelerating Decision Tree Based Traffic Classification on FPGA and Multicore Platforms[J]. IEEE Transactions on Parallel and Distributed Systems, 2017, 28(11): 3046-3059. |
| [5] | LI Hongcheng, WU Xiaoping, JIANG Honghai. Traffic Anomaly Detection Method in Networks Based on Improved Clustering Algorithm[J]. Netinfo Security, 2015, 15(1): 66-71. |
| 李洪成, 吴晓平, 姜洪海. 基于改进聚类分析的网络流量异常检测方法[J]. 信息网络安全, 2015, 15(1): 66-71. | |
| [6] | PARMAR N, SHARMA A, JAIN H, et al. Email Spam Detection Using Naive Bayes and Particle Swarm Optimization[J]. International Journal of Innovative Research in Technology, 2020, 6(10): 367-373. |
| [7] | MIAO Xianghua, SHAN Xiaoche. Research on Intrusion Detection Technology Based on Densely Connected Convolutional Neural Networks[J]. Journal of Electronics & Information Technology, 2020, 42(11): 2706-2712. |
| 缪祥华, 单小撤. 基于密集连接卷积神经网络的入侵检测技术研究[J]. 电子与信息学报, 2020, 42(11): 2706-2712. | |
| [8] | ZHANG Chenglei, FU Yulong, LI Hui, et al. Research on Security Scenarios and Security Models for 6G Networking[J]. Chinese Journal of Network and Information Security, 2021, 7(1): 28-45. |
| 张成磊, 付玉龙, 李晖, 等. 6G网络安全场景分析及安全模型研究[J]. 网络与信息安全学报, 2021, 7(1): 28-45. | |
| [9] | YING Ming, LI Jianhua, TIE Ling. Design of System for Detecting Network TrafficAnomalies Based on Conditional Rules[J]. Communications Technology, 2003(10): 107-109. |
| 应明, 李建华, 铁玲. 基于条件规则库的流量异常检测系统设计[J]. 通信技术, 2003(10): 107-109. | |
| [10] | YEUNG D, JIN Shuyuan, WANG Xizhao. Covariance-Matrix Modeling and Detecting Various Flooding Attacks[J]. IEEE Transactions on Systems, Man, and Cybernetics-Part A: Systems and Humans, 2007, 37(2): 157-169. |
| [11] | XIE Miao, HU Jiankun, GUO Song. Segment-Based Anomaly Detection with Approximated Sample Covariance Matrix in Wireless Sensor Networks[J]. IEEE Transactions on Parallel and Distributed Systems, 2015, 26(2): 574-583. |
| [12] | BANG J H, CHO Y J, KANG K. Anomaly Detection of Network-Initiated LTE Signaling Traffic in Wireless Sensor and Actuator Networks Based on a Hidden Semi-Markov Model[J]. Computers & Security, 2017, 65: 108-120. |
| [13] | ZHENG Liming, ZOU Peng, JIA Yan. Anomaly Detection Using Multi-Level and Multi-Dimensional Analyzing of Network Traffic[J]. Journal of Computer Research and Development, 2011, 48(8): 1506-1516. |
| 郑黎明, 邹鹏, 贾焰. 多维多层次网络流量异常检测研究[J]. 计算机研究与发展, 2011, 48(8): 1506-1516. | |
| [14] | TONG D, QU Y R, PRASANNA V K. Accelerating Decision Tree Based Traffic Classification on FPGA and Multicore Platforms[J]. IEEE Transactions on Parallel and Distributed Systems, 2017, 28(11): 3046-3059. |
| [15] | FARNAAZ N, JABBAR M A. Random Forest Modeling for Network Intrusion Detection System[J]. Procedia Computer Science, 2016(6): 213-217. |
| [16] | KOC L, MAZZUCHI T A, SARKANI S. A Network Intrusion Detection System Based on a Hidden Naive Bayes Multiclass Classifier[J]. Expert Systems with Applications, 2012, 39(18): 13492-13500. |
| [17] |
DUAN Xueyuan, FU Yu, WANG Kun, et al. Network Traffic Anomaly Detection Method Based on Multi-Scale Characteristic[J]. Journal on Communications, 2022, 43(10): 65-76.
doi: 10.11959/j.issn.1000-436x.2022195 |
|
段雪源, 付钰, 王坤, 等. 基于多尺度特征的网络流量异常检测方法[J]. 通信学报, 2022, 43(10): 65-76.
doi: 10.11959/j.issn.1000-436x.2022195 |
|
| [18] | ALDARWBI M Y, LASHKARI A H, GHORBANI A A. The Sound of Intrusion: A Novel Network Intrusion Detection System[J]. Computers and Electrical Engineering, 2022, 104: 455-466. |
| [19] | ZHANG Qiang, HE Junjiang, LI Wenshan, et al. Anomaly Traffc Detection Based on Deep Metric Learning. Anomaly Traffc Detection Based on Deep Metric Learning[J]. Netinfo Security, 2024, 24(3): 462-472. |
| 张强, 何俊江, 李汶珊, 等. 基于深度度量学习的异常流量检测方法[J]. 信息网络安全, 2024, 24(3): 462-472. | |
| [20] | DUAN Xueyuan, FU Yu, WANG Kun. Network Traffic Anomaly Detection Method Based on Multi-Scale Residual Classifier[J]. Computer Communications, 2023, 198: 206-216. |
| [21] | CICE (Canadian Institute For Cyber Security). CSE-CIC-IDS2018[EB/OL]. (2018-03-16)[2024-06-01]. https://registry.opendata.aws/cse-cic-ids2018. |
| [1] | TU Xiaohan, ZHANG Chuanhao, LIU Mengran. Design and Implementation of Malicious Traffic Detection Model [J]. Netinfo Security, 2024, 24(4): 520-533. |
| [2] | ZHANG Qiang, HE Junjiang, LI Wenshan, LI Tao. Anomaly Traffic Detection Based on Deep Metric Learning [J]. Netinfo Security, 2024, 24(3): 462-472. |
| [3] | ZHANG Yuchen, ZHANG Yawen, WU Yue, LI Cheng. A Method of Feature Extraction for Network Traffic Based on Time-Frequency Diagrams and Improved E-GraphSAGE [J]. Netinfo Security, 2023, 23(9): 12-24. |
| [4] | LI Zhihua, WANG Zhihao. IoT Device Identification Method Based on LCNN and LSTM Hybrid Structure [J]. Netinfo Security, 2023, 23(6): 43-54. |
| [5] | ZHAO Xiaolin, WANG Qiyao, ZHAO Bin, XUE Jingfeng. Research on Anonymous Traffic Classification Method Based on Machine Learning [J]. Netinfo Security, 2023, 23(5): 1-10. |
| [6] | QIN Yifang, ZHANG Jian, LIANG Chen. Research on Feature Extraction Technology of Electronic Medical Record Data Based on Neural Networks [J]. Netinfo Security, 2023, 23(10): 70-76. |
| [7] | ZHAO Xinhe, XIE Yongheng, WAN Yueliang, WANG Jinmiao. Detection and Identification Model of Gambling Websites Based on Multi-Modal Data [J]. Netinfo Security, 2023, 23(10): 77-82. |
| [8] | GAO Bo, CHEN Lin, YAN Yingjian. Research on Side Channel Attack Based on CNN-MGU [J]. Netinfo Security, 2022, 22(8): 55-63. |
| [9] | LYU Guohua, HU Xuexian, YANG Ming, XU Min. Ship AIS Trajectory Classification Algorithm Based on Federated Random Forest [J]. Netinfo Security, 2022, 22(4): 67-76. |
| [10] | CAI Manchun, WANG Tengfei, YUE Ting, LU Tianliang. ARF-based Tor Website Fingerprint Recognition Technology [J]. Netinfo Security, 2021, 21(4): 39-48. |
| [11] | YANG Ming, ZHANG Jian. Static Detection Model of Malware Based on Image Recognition [J]. Netinfo Security, 2021, 21(10): 25-32. |
| [12] | XU Guotian. Android Malicious Process Identification Method Based on Abnormal Encrypted Traffic Annotation [J]. Netinfo Security, 2020, 20(7): 30-41. |
| [13] | ZHANG Hao, CHEN Long, WEI Zhiqiang. Abnormal Traffic Detection Technology Based on Data Augmentation and Model Update [J]. Netinfo Security, 2020, 20(2): 66-74. |
| [14] | Xin SONG, Kai ZHAO, Linlin ZHANG, Wenbo FANG. Research on Android Malware Detection Based on Random Forest [J]. Netinfo Security, 2019, 19(9): 1-5. |
| [15] | Jian KANG, Jie WANG, Zhengxu LI, Guangda ZHANG. A Model for Anomaly Intrusion Detection with Different Feature Extraction Strategies in IoT [J]. Netinfo Security, 2019, 19(9): 21-25. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||