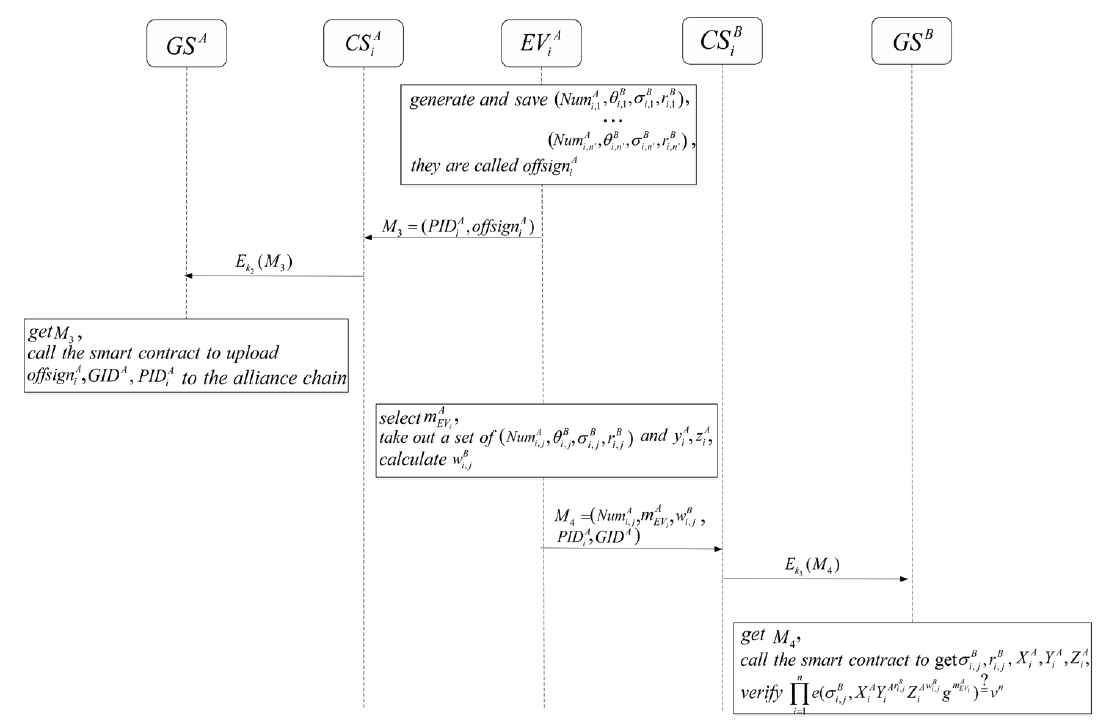
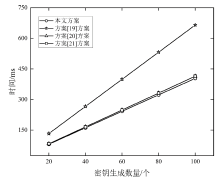
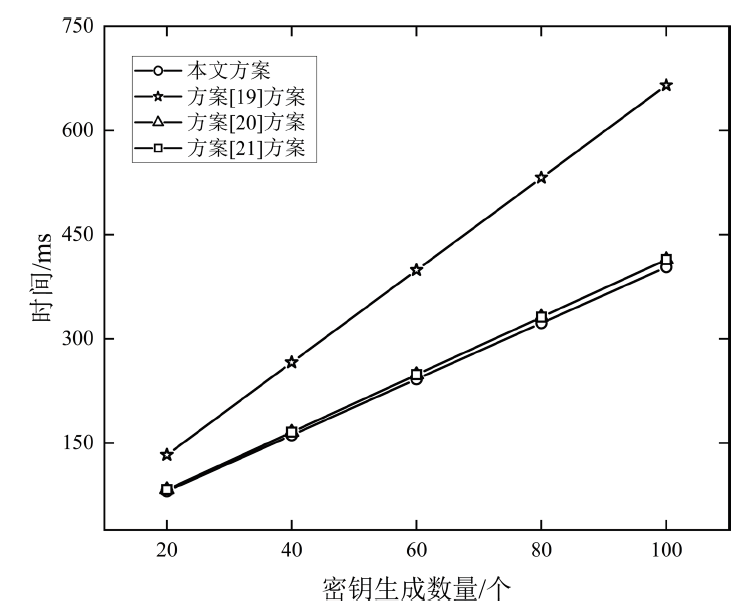
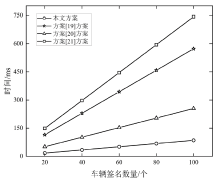
Netinfo Security ›› 2024, Vol. 24 ›› Issue (4): 587-601.doi: 10.3969/j.issn.1671-1122.2024.04.009
Previous Articles Next Articles
Online/Off line Cross-Domain Identity Authentication Scheme Based on Blockchain in Vehicle to Grid
SHI Runhua( ), YANG Jingyi, WANG Pengbo, LIU Huawei
), YANG Jingyi, WANG Pengbo, LIU Huawei
- School of Control and Computer Engineering, North China Electric Power University, Beijing 102206, China
-
Received:2024-01-12Online:2024-04-10Published:2024-05-16
CLC Number:
Cite this article
SHI Runhua, YANG Jingyi, WANG Pengbo, LIU Huawei. Online/Off line Cross-Domain Identity Authentication Scheme Based on Blockchain in Vehicle to Grid[J]. Netinfo Security, 2024, 24(4): 587-601.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2024.04.009
| 相关符号 | 含义说明 |
|---|---|
| A区域的电网服务器 | |
| B区域的电网服务器 | |
| 密钥生成中心 | |
| A区域的第i个充电桩 | |
| B区域的第i个充电桩 | |
| A区域的第i辆汽车 | |
| A区域第i辆汽车的假名 | |
| A区域第i辆汽车的公钥 | |
| A区域第i辆汽车的私钥 | |
| A区域电网服务器的身份标识 | |
| 待签名消息 | |
| 离线签名 | |
| 在线签名 |
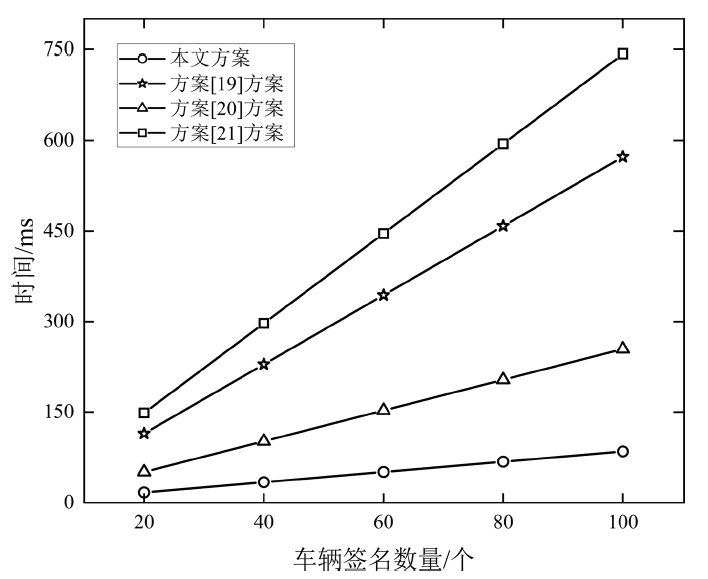
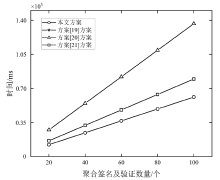
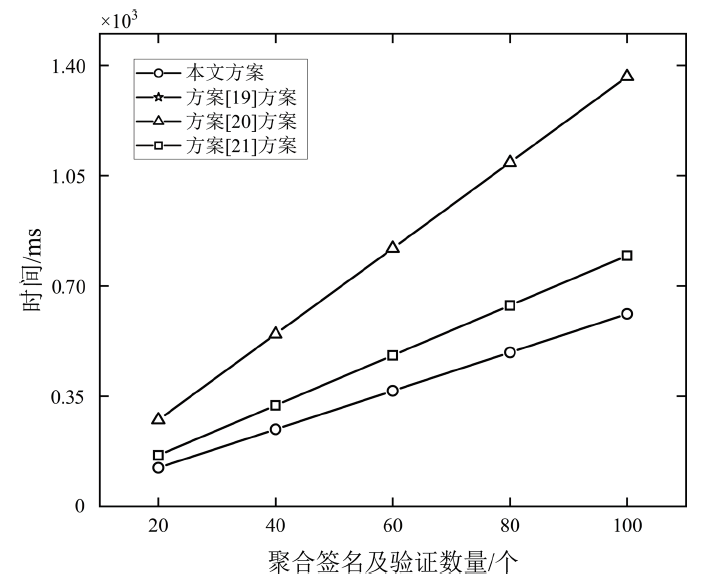
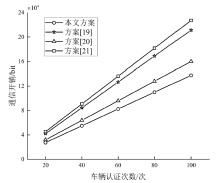
| 方案 | 车辆签名 | 聚合签名及认证 |
|---|---|---|
| 文献[ | — | |
| 文献[ | ||
| 文献[ | ||
| 本文方案 |
| [1] | LIU Jianan, WENG Jian. Survey on Smart Grid Security[J]. Netinfo Security, 2016, 16(5): 78-84. |
| 刘家男, 翁健. 智能电网安全研究综述[J]. 信息网络安全, 2016, 16 (5): 78-84. | |
| [2] | LIU Xiaofei, ZHANG Qianfan, CUI Shumei. Review of Electric Vehicle V2G Technology[J]. Transactions of China Electrotechnical Society, 2012, 27(2): 121-127. |
| 刘晓飞, 张千帆, 崔淑梅. 电动汽车V2G技术综述[J]. 电工技术学报, 2012, 27(2): 121-127. | |
| [3] | TSENG H R. A Secure and Privacy-Preserving Communication Protocol for V2G Networks[C]// IEEE. 2012 IEEE Wireless Communications and Networking Conference(WCNC). New York: IEEE, 2012: 2706-2711. |
| [4] | ABDALLAH A, SHEN X S. Lightweight Authentication and Privacy-Preserving Scheme for V2G Connections[J]. IEEE Transactions on Vehicular Technology, 2017, 66(3): 2615-2629. |
| [5] | LUIS F A R, PAULO R L G, JAIME L. Pairing-Based Authentication Protocol for V2G Networks in Smart Grid[EB/OL]. (2018-08-20)[2023-12-20]. https://linkinghub.elsevier.com/retrieve/pii/S1570870518305997. |
| [6] | VAIDYA B, MAKRAKIS D, MOUFTAH H T. Security Mechanism for Multi-Domain Vehicle-to-Grid Infrastructure[C]// IEEE. 2011 IEEE Global Telecommunications Conference(GLOBECOM). New York: IEEE, 2011: 1-5. |
| [7] | VAIDYA B, MAKRAKIS D, MOUFTAH H T. Multi-Domain Public Key Infrastructure for Vehicle-to-Grid Network[C]// IEEE. 2015 IEEE Military Communications Conference. New York: IEEE, 2015: 1572-1577. |
| [8] |
ZHOU Zhicheng, LI Lixin, LI Zuohui. Efficient Cross-Domain Authentication Scheme Based on Blockchain Technology[J]. Journal of Computer Applications, 2018, 38(2): 316-320.
doi: 10.11772/j.issn.1001-9081.2017082170 |
|
周致成, 李立新, 李作辉. 基于区块链技术的高效跨域认证方案[J]. 计算机应用, 2018, 38(2): 316-320.
doi: 10.11772/j.issn.1001-9081.2017082170 |
|
| [9] | LIU Donglan, LI Dong, LIU Xin, et al. Research on a Cross-Domain Authentication Scheme Based on Consortium Blockchain in V2G Networks of Smart Grid[C]// IEEE. 2nd IEEE Conference on Energy Internet and Energy System Integration(EI2). New York: IEEE, 2018: 1-5. |
| [10] | GARG S, KAUR K, KADDOUM G, et al. An Efficient Blockchain Based Hierarchical Authentication Mechanism for Energy Trading in V2G Environment[C]// IEEE. 2019 IEEE International Conference on Communications Workshops(ICC Workshops). New York: IEEE, 2019: 1-6. |
| [11] | AGGARWAL S, KUMAR N, GOPE P. An Efficient Blockchain-Based Authentication Scheme for Energy-Trading in V2G Networks[J]. IEEE Transactions on Industrial Informatics, 2021, 17(10): 6971-6980. |
| [12] | SHI Runhua, WANG Shuhao, LI Kunchang. A Lightweight Cross-Domain Mutual Authentication Scheme in V2G Networks[J]. Netinfo Security, 2022, 23(3): 20-28. |
| 石润华, 王树豪, 李坤昌. V2G中一种轻量级的跨域双向认证方案[J]. 信息网络安全, 2022, 23(3): 20-28. | |
| [13] | XUE Lingyan, HUANG Haiping, XIAO Fu, et al. A Cross-Domain Authentication Scheme Based on Cooperative Blockchains Functioning with Revocation for Medical Consortiums[J]. IEEE Transactions on Network and Service Management, 2022, 19(3): 2409-2420. |
| [14] | ZHANG Xuewang, YAO Yaning, LI Zhihong, et al. Data Sharing Scheme Based on Consortium Blockchain and Asmuth-Bloom Secret Sharing Algorithm[J]. Netinfo Security, 2022, 22(11): 17-23. |
| 张学旺, 姚亚宁, 黎志鸿, 等. 基于联盟链和Asmuth-Bloom秘密共享算法的数据共享方案[J]. 信息网络安全, 2022, 22(11): 17-23. | |
| [15] | LI Chunxiao, WANG Yaofei, XU Enliang, et al. Enabling Privacy-Preserving Range Queries in Blockchain-Based Collaborative Databases with Bilinear Pairings[J]. Netinfo Security, 2023, 23(3): 22-34. |
| 李春晓, 王耀飞, 徐恩亮, 等. 基于双线性映射的区块链安全范围搜索技术研究[J]. 信息网络安全, 2023, 23(3): 22-34. | |
| [16] | HUA Jingyu, HUANG Daming. Survey of Formal Specification Methods in Theorem Proving of Ethereum Smart Contract[J]. Netinfo Security, 2022, 22(5): 11-20. |
| 华景煜, 黄达明. 以太坊智能合约定理证明中的形式化规约研究综述[J]. 信息网络安全, 2022, 22(5): 11-20. | |
| [17] | ZHAO Xingwen, DUAN Yiru. NFC Secure Payment Protocol Based on Pseudonym[J]. Journal of Information Security Research, 2022, 8(12): 1178-1186. |
| 赵兴文, 段懿入. 基于假名的NFC安全支付认证协议[J]. 信息安全研究, 2022, 8(12): 1178-1186. | |
| [18] | LIU Yuanni, LI Yi, CHEN Shanzhi. A Survey of Internet of Vehicles/Vehicle to Everything Security Based on Blockchain[J]. Scientia Sinica Informationis, 2023, 53(5): 841-877. |
| 刘媛妮, 李奕, 陈山枝. 基于区块链的车联网安全综述[J]. 中国科学(信息科学), 2023, 53(5): 841-877. | |
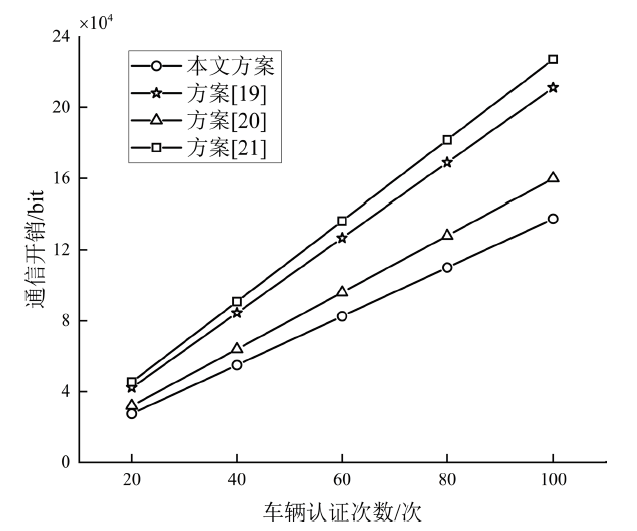
| [19] | KARATI A, ISLAM S H, KARUPPIAH M. Provably Secure and Lightweight Certificateless Signature Scheme for IoT Environments[J]. IEEE Transactions on Industrial Informatics, 2018, 14(8): 3701-3711. |
| [20] | WU Ge, ZHANG Futai, SHEN Limin, et al. Certificateless Aggregate Signature Scheme Secure against Fully Chosen-Key Attacks[J]. Information Sciences, 2019, 514: 288-301. |
| [21] | SHIM K A. Forgery Attacks on Two Provably Secure Certificateless Signature Schemes[J]. Information Sciences, 2020, 521: 81-87. |
| [1] | HU Haiyang, LIU Chang, WANG Dong, WEI Xu. Clean Energy Data Traceability Mechanism Based on Blockchain [J]. Netinfo Security, 2024, 24(4): 626-639. |
| [2] | XUE Mingzhu, HU Liang, WANG Ming, WANG Feng. TAP Rule Processing System Based on Federated Learning and Blockchain Technology [J]. Netinfo Security, 2024, 24(3): 473-485. |
| [3] | ZHAI Peng, HE Jingsha, ZHANG Yu. An Identity Authentication Method Based on SM9 and Blockchain in the IoT Environment [J]. Netinfo Security, 2024, 24(2): 179-187. |
| [4] | GU Yanyan, SHEN Limin, GAO Chenxu, ZHU Ting. Efficient and Secure Certificateless Aggregate Signature Scheme in Vehicle Networks [J]. Netinfo Security, 2024, 24(2): 188-202. |
| [5] | HE Yefeng, QUAN Jiahui, LIU Yan. A Location Privacy Protection Scheme Based on Hybrid Blockchain [J]. Netinfo Security, 2024, 24(2): 229-238. |
| [6] | WU Haotian, LI Yifan, CUI Hongyan, DONG Lin. Federated Learning Incentive Scheme Based on Zero-Knowledge Proofs and Blockchain [J]. Netinfo Security, 2024, 24(1): 1-13. |
| [7] | ZHU Guocheng, HE Debiao, AN Haoyang, PENG Cong. The Proxy Voting Scheme Based on the Blockchain and SM9 Digital Signature [J]. Netinfo Security, 2024, 24(1): 36-47. |
| [8] | LAI Chengzhe, ZHAO Yining, ZHENG Dong. A Privacy Preserving and Verifiable Federated Learning Scheme Based on Homomorphic Encryption [J]. Netinfo Security, 2024, 24(1): 93-105. |
| [9] | GONG Pengfei, XIE Sijiang, CHENG Andong. The Multi-Leader Consensus Algorithm Based on Improvements to HotStuff [J]. Netinfo Security, 2023, 23(9): 108-117. |
| [10] | ZHOU Quan, CHEN Minhui, WEI Kaijun, ZHENG Yulong. Blockchain Access Control Scheme with SM9-Based Attribute Encryption [J]. Netinfo Security, 2023, 23(9): 37-46. |
| [11] | ZHAO Jiahao, JIANG Jiajia, ZHANG Yushu. Cross-Chain Data Consistency Verification Model Based on Dynamic Merkle Hash Tree [J]. Netinfo Security, 2023, 23(9): 95-107. |
| [12] | SHAO Zhenzhe, JIANG Jiajia, ZHAO Jiahao, ZHANG Yushu. An Improved Weighted Byzantine Fault Tolerance Algorithm for Cross-Chain System [J]. Netinfo Security, 2023, 23(8): 109-120. |
| [13] | QIN Sihang, DAI Weiqi, ZENG Haiyan, GU Xianjun. Secure Sharing of Power Application Data Based on Blockchain [J]. Netinfo Security, 2023, 23(8): 52-65. |
| [14] | PENG Hanzhong, ZHANG Zhujun, YAN Liyue, HU Chenglin. Research on Intrusion Detection Mechanism Optimization Based on Federated Learning Aggregation Algorithm under Consortium Chain [J]. Netinfo Security, 2023, 23(8): 76-85. |
| [15] | YU Huifang, QIAO Yifan, MENG Ru. Attribute-Based Anti-Quantum Threshold Ring Signcryption Scheme for Blockchain-Based Finance [J]. Netinfo Security, 2023, 23(7): 44-52. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||