Netinfo Security ›› 2024, Vol. 24 ›› Issue (2): 262-271.doi: 10.3969/j.issn.1671-1122.2024.02.009
Previous Articles Next Articles
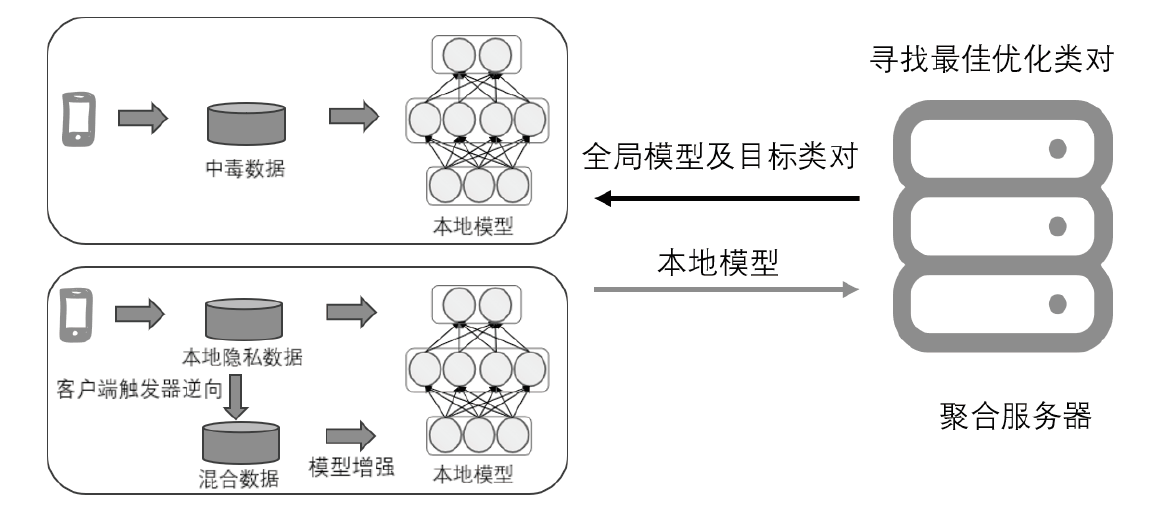
Federated Learning Backdoor Defense Method Based on Trigger Inversion
LIN Yihang, ZHOU Pengyuan( ), WU Zhiqian, LIAO Yong
), WU Zhiqian, LIAO Yong
- School of Cyber Science and Technology, University of Science and Technology of China, Hefei 230031, China
-
Received:2023-10-23Online:2024-02-10Published:2024-03-06 -
Contact:ZHOU Pengyuan E-mail:pyzhou@ustc.edu.cn
CLC Number:
Cite this article
LIN Yihang, ZHOU Pengyuan, WU Zhiqian, LIAO Yong. Federated Learning Backdoor Defense Method Based on Trigger Inversion[J]. Netinfo Security, 2024, 24(2): 262-271.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2024.02.009
| 基线 | MNIST | Fashion-MNIST | CIFAT-10 | |||
|---|---|---|---|---|---|---|
| 主任务精度 | 攻击 成功率 | 主任务精度 | 攻击 成功率 | 主任务精度 | 攻击 成功率 | |
| 无防御 | 94.03% | 99.68% | 77.93% | 99.8% | 74.06% | 88.41% |
| DP | 94.08% | 100% | 77.79% | 99.65% | 71.18% | 89.20% |
| Trimmed Mean | 97.88% | 0.44% | 81.49% | 11.82% | 75.78% | 15.59% |
| RFA | 97.60% | 0.43% | 79.72% | 7.83% | 78.84% | 7.83% |
| CP | 62.38% | 35.33% | 62.35% | 29.08% | 64.66% | 74.20% |
| Flame | 97.50% | 0.43% | 76.92% | 15.93% | 79.26% | 5.53% |
| 本文方法 | 97.24% | 0.16% | 79.84% | 14.64% | 79.84% | 8.95% |
| 基线 | MNIST | Fashion-MNIST | CIFAT-10 | |||
|---|---|---|---|---|---|---|
| 主任务精度 | 攻击 成功率 | 主任务精度 | 攻击 成功率 | 主任务精度 | 攻击 成功率 | |
| 无防御 | 96.20% | 99.82% | 82.37% | 99.89% | 77.96% | 82.13% |
| DP | 95.32% | 86.52% | 79.57% | 99.70% | 78.13% | 81.21% |
| Trimmed Mean | 98.74% | 99.89% | 80.37% | 99.75% | 62.62% | 83.67% |
| RFA | 97.97% | 2.24% | 82.26% | 22.93% | 76.92% | 63.10% |
| CP | 95.73% | 58.08% | 67.77% | 25.43% | 62.51% | 63.97% |
| Flame | 98.08% | 0.31% | 77.23% | 17.81% | 77.44% | 81.60% |
| 本文方法 | 96.67% | 1.53% | 78.88% | 15.21% | 70.54% | 22.03% |
| [1] | LECUN Y, BENGIO Y. Convolutional Networks for Images, Speech, and Time Series[J]. The Handbook of Brain Theory and Neural Networks, 1995, 3361(10): 255-258. |
| [2] | CHAN Y S, ROTH D. Exploiting Syntactico-Semantic Structures for Relation Extraction[C]// ACM. The 49th Annual Meeting of the Association for Computational Linguistics:Human Language Technologies. New York: ACM, 2011: 551-560. |
| [3] | WEN Long, LU Zhichen, CUI Lingxiao. Deep Learning-Based Feature Engineering for Stock Price Movement Prediction[J]. Knowledge-Based Systems, 2019(164): 163-173. |
| [4] | VOIGT P, VON D B A. A Practical Guide[M]. Heidelberg: Springer, 2017. |
| [5] | PARDAU S L. The California Consumer Privacy Act: Towards a European-Style Privacy Regime in the United States[J]. Journal of Technology Law & Policy, 2018(23): 68-114. |
| [6] | CHESTERMAN S. After Privacy: The Rise of Facebook, the Fall of Wikileaks, and Singapore’s Personal Data Protection Act 2012[EB/OL]. (2012-12-01)[2023-10-17]. https://www.jstor.org/stable/24872218. |
| [7] | MCMAHAN B, MOORE E, RAMAGE D, et al. Communication-Efficient Learning of Deep Networks from Decentralized Data[EB/OL]. (2016-02-17)[2023-10-17]. https://arxiv.org/abs/1602.05629. |
| [8] | ANTUNES R S, ANDRE D C C, KUDERLE A, et al. Federated Learning for Healthcare: Systematic Review and Architecture Proposal[J]. ACM Transactions on Intelligent Systems and Technology (TIST), 2022, 13(4): 1-23. |
| [9] | DASH B, SHARMA P, ALI A. Federated Learning for Privacy-Preserving: A Review of PII Data Analysis in Fintech[J]. International Journal of Software Engineering & Applications (IJSEA), 2022, 13(4): 1-13. |
| [10] |
ZHENG Zhaohua, ZHOU Yize, SUN Yilong, et al. Applications of Federated Learning in Smart Cities: Recent Advances, Taxonomy, and Open Challenges[J]. Connection Science, 2022, 34(1): 1-28.
doi: 10.1080/09540091.2021.1936455 URL |
| [11] | LUO Xinjian, WU Yuncheng, XIAO Xiaokui, et al. Feature Inference Attack on Model Predictions in Vertical Federated Learning[C]// IEEE. 2021 IEEE 37th International Conference on Data Engineering (ICDE). New York:IEEE, 2021: 181-192. |
| [12] | ZHU Ligeng, LIU Zhijian, HAN Song. Deep Leakage from Gradients[J]. Advances in Neural Information Processing Systems, 2019(32): 14747-14756. |
| [13] | BHAGOJI A N, CHAKRABORTY S, MITTAL P, et al. Analyzing Federated Learning Through an Adversarial Lens[EB/OL]. (2019-11-25)[2023-10-17]. https://arxiv.org/abs/1811.12470. |
| [14] | BAGDASARYAN E, VEIT A, HUA Yiqing, et al. How to Backdoor Federated Learning[EB/OL]. (2019-08-06)[2023-10-17]. https://arxiv.org/abs/1807.00459. |
| [15] | MCMAHAN H B, MOORE E, RAMAGE D, et al. Communication-Efficient Learning of Deep Networks from Decentralized Data[EB/OL]. (2023-01-26)[2023-10-17]. https://arxiv.org/abs/1602.05629. |
| [16] | WANG Hongyi, SREENIVASAN K, RAJPUT S, et al. Attack of the Tails: Yes, You Really Can Backdoor Federated Learning[J]. Advances in Neural Information Processing Systems, 2020(33): 16070-16084. |
| [17] | ZHANG Zhiyuan, SU Qi, SUN Xu. Dim-Krum: Backdoor-Resistant Federated Learning for NLP with Dimension-Wise Krum-Based Aggregation[EB/OL]. (2022-10-13)[2023-10-17]. https://arxiv.org/abs/2210.06894. |
| [18] | NGUYEN T D, RIEGER P, MIETTINEN M, et al. Poisoning Attacks on Federated Learning-Based IoT Intrusion Detection System[EB/OL]. (2020-01-01)[2023-10-17]. https://www.semanticscholar.org/paper/Poisoning-Attacks-on-Federated-Learning-based-IoT-Nguyen-Rieger/35ff04db3be0e98c40c6483081484308daa9ad82. |
| [19] | NGUYEN T D, RIEGER P, CHEN Huili, et al. FLAME: Taming Backdoors in Federated Learning[C]// USENIX. 31st USENIX Security Symposium (USENIX Security 22). Berkeley:USENIX, 2022: 1415-1432. |
| [20] | DWORK C. Differential Privacy[C]// Springer. International Colloquium on Automata, Languages, and Programming. Heidelberg: Springer, 2006: 1-12. |
| [21] | BLANCHARD P, EL M E M, GUERRAOUI R, et al. Machine Learning with Adversaries: Byzantine Tolerant Gradient Descent[J]. Advances in Neural Information Processing Systems, 2017(30): 119-129. |
| [22] | XIE Cong, KOYEJO O, GUPTA I. Generalized Byzantine-Tolerant SGD[EB/OL]. (2018-02-27)[2023-10-17]. https://doi.org/10.48550/arXiv.1802.10116. |
| [23] | FUNG C, YOON C J, BESCHASTNIKH I. The Limitations of Federated Learning in Sybil Settings[C]// USENIX. 23rd International Symposium on Research in Attacks, Intrusions and Defenses(RAID 2020). Berkeley:USENIX, 2020: 301-316. |
| [24] | MUÑOZ-GONZÁLEZ L, CO K T, LUPU E C. Byzantine-Robust Federated Machine Learning Through Adaptive Model Averaging[EB/OL]. (2019-09-11)[2023-10-17]. https://doi.org/10.48550/arXiv.1909.05125. |
| [25] | SEKHARI A, ACHARYA J, KAMATH G, et al. Remember What You Want to Forget: Algorithms for Machine Unlearning[J]. Neural Information Processing Systems, 2021(34): 18075-18086. |
| [26] | WU Chen, ZHU Sencun, PRASENJIT M. Federated Unlearning with Knowledge Distillation[EB/OL]. (2022-01-24)[2023-10-17]. https://doi.org/10.48550/arXiv.2201.09441. |
| [27] | LI Zhuohang, ZHANG Jiaxin, LIU Yuyang, et al. Auditing Privacy Defenses in Federated Learning via Generative Gradient Leakage[C]// IEEE. 2022 IEEE/CVF Conference on Computer Vision and Pattern Recognition. New York: IEEE, 2022: 10132-10142. |
| [28] | TAO Guanhong, LIU Yingqi, SHEN Guangyu, et al. Model Orthogonalization: Class Distance Hardening in Neural Networks for Better Security[C]// IEEE. 2022 IEEE Symposium on Security and Privacy (SP). New York:IEEE, 2022: 1372-1389. |
| [29] | CAO Xiaoyu, FANG Minghong, LIU Jia, et al. FLTrust: Byzantine-Robust Federated Learning via Trust Bootstrapping[EB/OL]. (2020-04-12)[2023-10-17]. https://doi.org/10.48550/arXiv.2012.13995. |
| [30] | WATKINS C J C H. Learning from Delayed Rewards[EB/OL]. (1989-01-01)[2023-10-17]. https://www.researchgate.net/publication/33784417_Learning_From_Delayed_Rewards. |
| [31] | XIE Chulin, HUANG Keli, CHEN Pinyu, et al. DBA: Distributed Backdoor Attacks against Federated Learning[EB/OL]. (-12-20)[2023-10-17]. https://openreview.net/forum?id=rkgyS0VFvr. |
| [32] | PILLUTLA K, KAKADE S M, HARCHAOUI Z. Robust Aggregation for Federated Learning[J]. IEEE Transactions on Signal Processing, 2022(70): 1142-1154. |
| [33] | XIE Chulin, CHEN Minghao, CHEN Pinyu, et al. CRFL: Certifiably Robust Federated Learning against Backdoor Attacks[C]// ICML. International Conference on Machine Learning 2021. New York: PMLR, 2021: 11372-11382. |
| [34] | ZHANG Hongyi, CISSE M, DAUPHIN Y N, et al. Mixup: Beyond Empirical Risk Minimization[EB/OL]. (2017-10-25)[2023-10-17]. https://doi.org/10.48550/arXiv.1710.09412. |
| [35] | DEVRIES T, TAYLOR G W. Improved Regularization of Convolutional Neural Networks with Cutout[EB/OL]. (2017-08-15)[2023-10-17]. https://doi.org/10.48550/arXiv.1708.04552. |
| [1] | JIN Zhigang, DING Yu, WU Xiaodong. Federated Intrusion Detection Algorithm with Bilateral Correction Merging Gradient Difference [J]. Netinfo Security, 2024, 24(2): 293-302. |
| [2] | WU Haotian, LI Yifan, CUI Hongyan, DONG Lin. Federated Learning Incentive Scheme Based on Zero-Knowledge Proofs and Blockchain [J]. Netinfo Security, 2024, 24(1): 1-13. |
| [3] | ZHAO Jia, YANG Bokai, RAO Xinyu, GUO Yating. Design and Implementation of Tor Traffic Detection Algorithm Based on Federated Learning [J]. Netinfo Security, 2024, 24(1): 60-68. |
| [4] | XU Ruzhi, DAI Lipeng, XIA Diya, YANG Xin. Research on Centralized Differential Privacy Algorithm for Federated Learning [J]. Netinfo Security, 2024, 24(1): 69-79. |
| [5] | LAI Chengzhe, ZHAO Yining, ZHENG Dong. A Privacy Preserving and Verifiable Federated Learning Scheme Based on Homomorphic Encryption [J]. Netinfo Security, 2024, 24(1): 93-105. |
| [6] | PENG Hanzhong, ZHANG Zhujun, YAN Liyue, HU Chenglin. Research on Intrusion Detection Mechanism Optimization Based on Federated Learning Aggregation Algorithm under Consortium Chain [J]. Netinfo Security, 2023, 23(8): 76-85. |
| [7] | CHEN Jing, PENG Changgen, TAN Weijie, XU Dequan. A Multi-Server Federation Learning Scheme Based on Differential Privacy and Secret Sharing [J]. Netinfo Security, 2023, 23(7): 98-110. |
| [8] | LIU Changjie, SHI Runhua. A Smart Grid Intrusion Detection Model for Secure and Efficient Federated Learning [J]. Netinfo Security, 2023, 23(4): 90-101. |
| [9] | LIU Jiqiang, WANG Xuewei, LIANG Mengqing, WANG Jian. A Hierarchical Federated Learning Framework Based on Shared Dataset and Gradient Compensation [J]. Netinfo Security, 2023, 23(12): 10-20. |
| [10] | LIU Xin, LI Yunyi, WANG Miao. A Lightweight Authentication Protocol Based on Confidential Computing for Federated Learning Nodes [J]. Netinfo Security, 2022, 22(7): 37-45. |
| [11] | LYU Guohua, HU Xuexian, YANG Ming, XU Min. Ship AIS Trajectory Classification Algorithm Based on Federated Random Forest [J]. Netinfo Security, 2022, 22(4): 67-76. |
| [12] | BAI Hongpeng, DENG Dongxu, XU Guangquan, ZHOU Dexiang. Research on Intrusion Detection Mechanism Based on Federated Learning [J]. Netinfo Security, 2022, 22(1): 46-54. |
| [13] | XU Shuo, ZHANG Rui, XIA Hui. Privacy-preserving Strategies for Federated Learning Based on Data Attribute Modification [J]. Netinfo Security, 2022, 22(1): 55-63. |
| [14] | LU Honglin, WANG Liming, YANG Jing. A New Parameter Masking Federated Learning Privacy Preserving Scheme [J]. Netinfo Security, 2021, 21(8): 26-34. |
| [15] | REN Tao, JIN Ruochen, LUO Yongmei. Network Intrusion Detection Algorithm Integrating Blockchain and Federated Learning [J]. Netinfo Security, 2021, 21(7): 27-34. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||