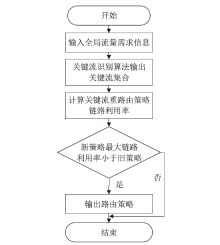
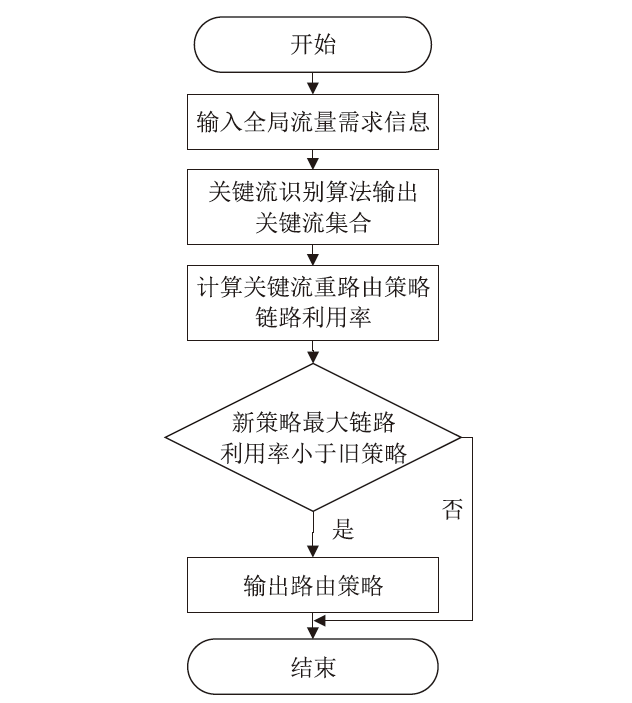
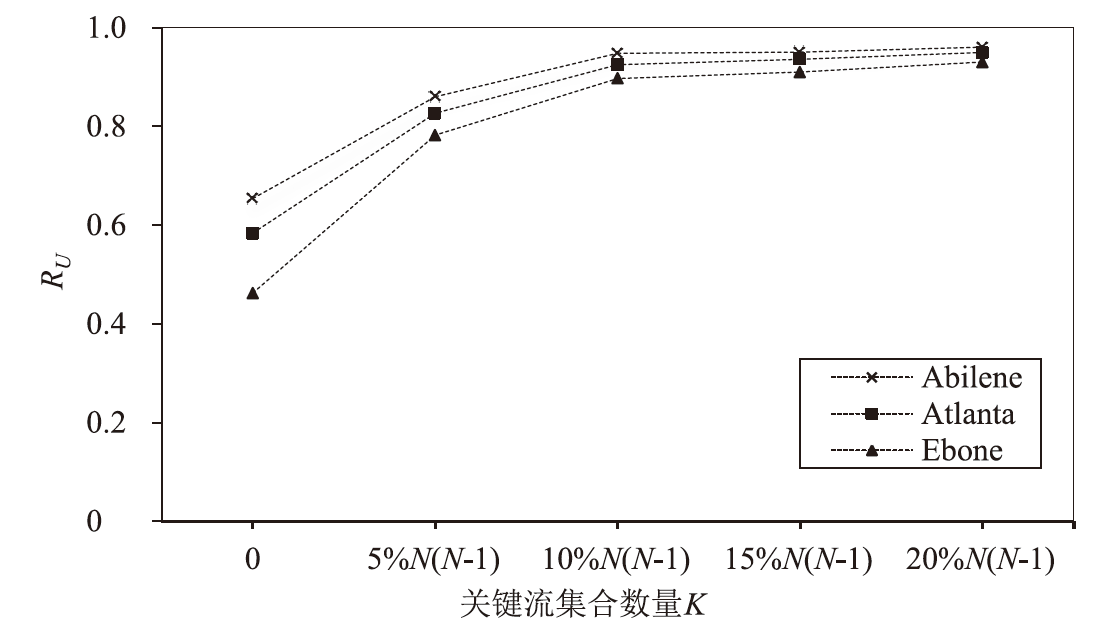
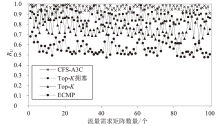
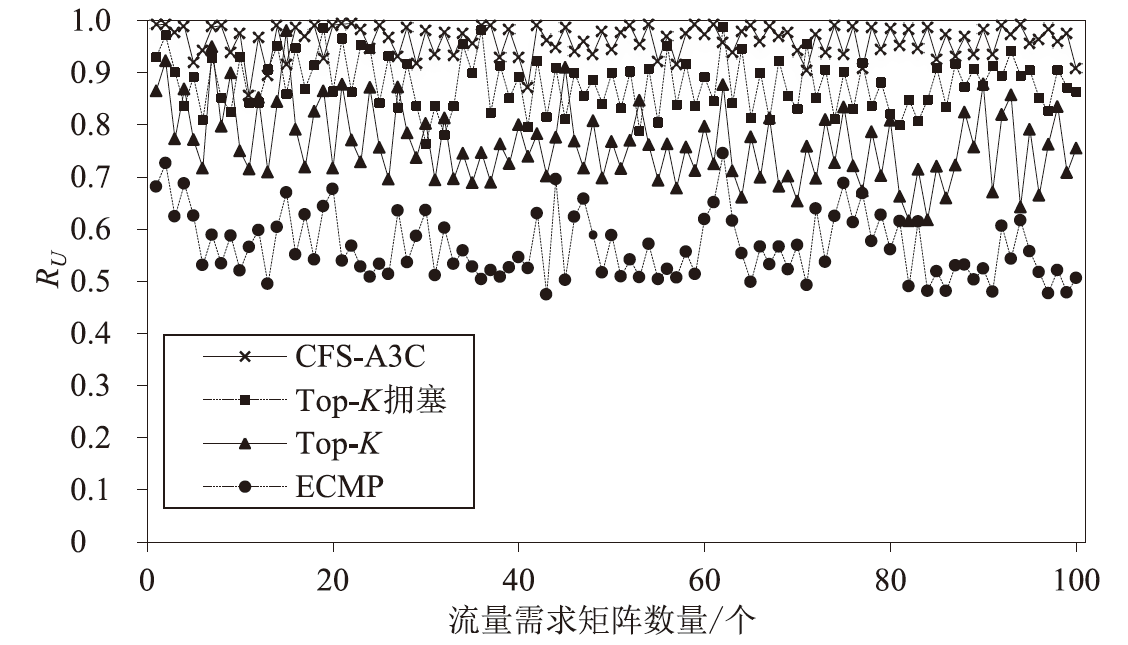
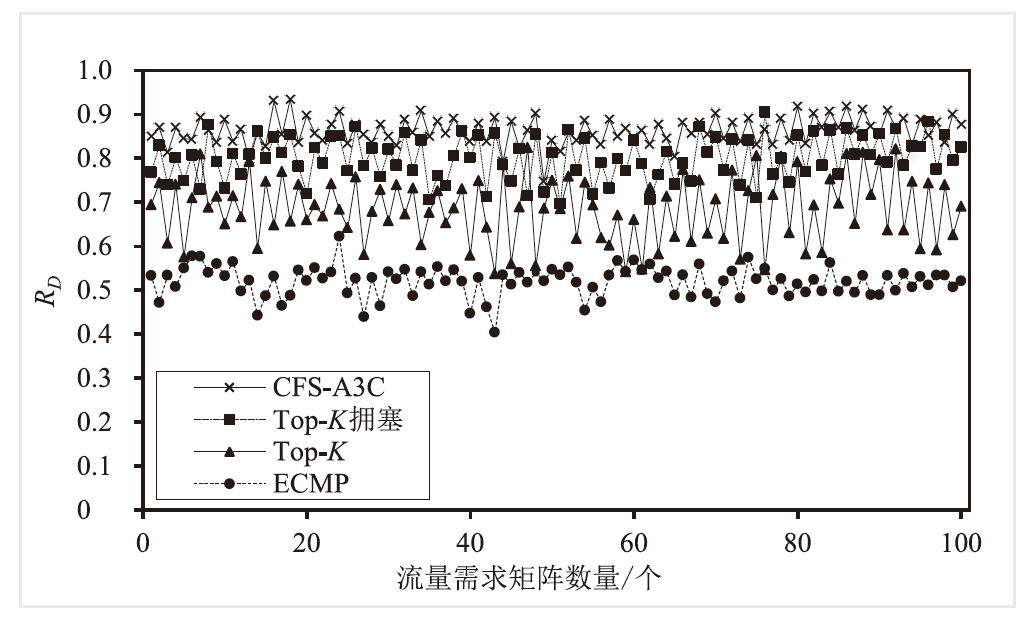
Netinfo Security ›› 2024, Vol. 24 ›› Issue (2): 272-281.doi: 10.3969/j.issn.1671-1122.2024.02.010
Previous Articles Next Articles
An Optimal Algorithm for Traffic Scheduling in SRv6 Network Based on Deep Learning
ZHAO Pengcheng1, YU Junqing1,2( ), LI Dong2
), LI Dong2
- 1. School of Cyber Science and Engineering, Huazhong University of Science and Technology, Wuhan 430074, China
2. Network and Computation Center, Huazhong University of Science and Technology, Wuhan 430074, China
-
Received:2023-10-18Online:2024-02-10Published:2024-03-06 -
Contact:YU Junqing E-mail:yjqing@hust.edu.cn
CLC Number:
Cite this article
ZHAO Pengcheng, YU Junqing, LI Dong. An Optimal Algorithm for Traffic Scheduling in SRv6 Network Based on Deep Learning[J]. Netinfo Security, 2024, 24(2): 272-281.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2024.02.010
| [1] |
KREUTZ D, RAMOS F M V, VERISSIMO P E, et al. Software-Defined Networking: A Comprehensive Survey[J]. Proceedings of the IEEE, 2014, 103(1): 14-76.
doi: 10.1109/JPROC.2014.2371999 URL |
| [2] | VENTRE P L, SALSANO S, POLVERINI M, et al. Segment Routing: A Comprehensive Survey of Research Activities, Standardization Efforts, and Implementation Results[J]. IEEE Communications Surveys & Tutorials, 2020, 23(1): 182-221. |
| [3] |
CHENG Weiqiang, LIU Yisong, JIANG Wenying, et al. Research and Application of G-SRv6 Head Compressions Optimization Technology[J]. Telecommunications Science, 2020, 36(8): 22-27.
doi: 10.11959/j.issn.1000-0801.2020254 |
|
程伟强, 刘毅松, 姜文颖, 等. G-SRv6 头压缩优化技术研究与应用[J]. 电信科学, 2020, 36(8):22-27.
doi: 10.11959/j.issn.1000-0801.2020254 |
|
| [4] |
WU Wei, ZHANG Wenqiang, YANG Guangming, et al. SRv6 +EVPN Technology Research and Scale Deployment of 5G Bearer Network[J]. Telecommunications Science, 2020, 36(8): 43-52.
doi: 10.11959/j.issn.1000-0801.2020253 |
|
吴伟, 张文强, 杨广铭, 等. 5G 承载网的“SRv6+ EVPN”技术研究与规模部署[J]. 电信科学, 2020, 36(8):43-52.
doi: 10.11959/j.issn.1000-0801.2020253 |
|
| [5] |
CHEN Kefan, ZHAO Shanghou, LV Na, et al. Segment Routing Based Traffic Scheduling for the Software-Defined Airborne Backbone Network[J]. IEEE Access, 2019, 7: 106162-106178.
doi: 10.1109/ACCESS.2019.2930229 |
| [6] | STAMPA G, ARIAS M, SÁNCHEZ-CHARLES D, et al. A Deep-Reinforcement Learning Approach for Software-Defined Networking Routing Optimization[EB/OL]. (2017-09-20)[2023-08-10]. https://arxiv.org/abs/1709.07080.pdf. |
| [7] | CASAS N. Deep Deterministic Policy Gradient for Urban Traffic Light Control[EB/OL]. (2017-03-27)[2023-08-10]. https://arxiv.org/pdf/1703.09035.pdf. |
| [8] | TENG Yuantao, XIA Zhengyou. A Traffic Engineering Technology Based on Segment Routing in SDN[C]// IEEE. 2020 16th International Conference on Mobility, Sensing and Networking(MSN). New York:IEEE, 2020: 636-641. |
| [9] | LI Cheng, MAO Jianwen, PENG Shuping, et al. Application-Aware G-SRv6 Network Enabling 5G Services[C]// IEEE. 2021 IEEE Conference on Computer Communications Workshops(INFOCOM WKSHPS). New York:IEEE, 2021: 1-2. |
| [10] |
REN Bangbang, GUO Deke, YUAN Yali, et al. Optimal Deployment of SRv6 to Enable Network Interconnection Service[J]. IEEE/ACM Transactions on Networking, 2021, 30(1): 120-133.
doi: 10.1109/TNET.2021.3105959 URL |
| [11] |
ANAND R, AGGARWAL D, KUMAR V. A Comparative Analysis of Optimization Solvers[J]. Journal of Statistics and Management Systems, 2017, 20(4): 623-635.
doi: 10.1080/09720510.2017.1395182 URL |
| [12] | MAO Hongzi, ALIZADEH M, MENACHE I, et al. Resource Management with Deep Reinforcement Learning[C]// ACM. 15th ACM Workshop on Hot Topics in Networks. New York: ACM, 2016: 50-56. |
| [13] | WILLIAMS R J. Simple Statistical Gradient-Following Algorithms for Connectionist Reinforcement Learning[J]. Reinforcement Learning, 1992, 8: 5-32. |
| [14] | JIANG J R, HUANG H W, LIAO J H, et al. Extending Dijkstra’s Shortest Path Algorithm for Software Defined Networking[C]// IEEE. The 16th Asia-Pacific Network Operations and Management Symposium. New York: IEEE, 2014: 1-4. |
| [15] |
CIANFRANI A, LISTANTI M, POLVERIN M. Incremental Deployment of Segment Routing into an ISP Network: A Traffic Engineering Perspective[J]. IEEE/ACM Transactions on Networking, 2017, 25(5): 3146-3160.
doi: 10.1109/TNET.2017.2731419 URL |
| [16] |
SPRING N, MAHAJAN R, WETHERALL D. Measuring ISP Topologies with Rocketfuel[J]. ACM SIGCOMM Computer Communication Review, 2002, 32(4): 133-145.
doi: 10.1145/964725.633039 URL |
| [17] |
KODIALAM M, LAKSHMAN T V, ORLIN J, et al. Oblivious Routing of Highly Variable Traffic in Service Overlays and IP Backbones[J]. IEEE/ACM Transactions on Networking, 2008, 17(2): 459-472.
doi: 10.1109/TNET.2008.927257 URL |
| [18] | TUNE P, ROUGHAN M. Spatiotemporal Traffic Matrix Synthesis[C]// ACM. 2015 ACM Conference on Special Interest Group on Data Communication. New York: ACM, 2015: 579-592. |
| [19] | ZHANG Junjie, XI Kang, ZHANG Liren, et al. Optimizing Network Performance Using Weighted Multipath Routing[C]// IEEE. 21st International Conference on Computer Communications and Networks(ICCCN). New York:IEEE, 2012: 1-7. |
| [20] | ZHANG Hailong, GUO Xiao, YAN Jinyao, et al. SDN-Based ECMP Algorithm for Data Center Networks[C]// IEEE. 2014 IEEE Computers, Communications and IT Applications Conference. New York: IEEE, 2014: 13-18. |
| [21] | LIU Jing, LI Jie, SHOU Guochu, et al. SDN Based Load Balancing Mechanism for Elephant Flow in Data Center Networks[C]// IEEE. 2014 International Symposium on Wireless Personal Multimedia Communications(WPMC). New York:IEEE, 2014: 486-490. |
| [22] | YAO Guohao, WU Muqing, XU Yang. A Data Center Load Balancing Algorithm Based on Artificial Bee Colony Algorithm[C]// IEEE. 2020 IEEE 6th International Conference on Computer and Communications(ICCC). New York:IEEE, 2020: 1770-1775. |
| [1] | FENG Guangsheng, JIANG Shunpeng, HU Xianlang, MA Mingyu. New Research Progress on Intrusion Detection Techniques for the Internet of Things [J]. Netinfo Security, 2024, 24(2): 167-178. |
| [2] | JIN Zhigang, DING Yu, WU Xiaodong. Federated Intrusion Detection Algorithm with Bilateral Correction Merging Gradient Difference [J]. Netinfo Security, 2024, 24(2): 293-302. |
| [3] | XUE Yu, ZHANG Yixuan. Survey on Deep Neural Architecture Search [J]. Netinfo Security, 2023, 23(9): 58-74. |
| [4] | LIU Yuxiao, CHEN Wei, ZHANG Tianyue, WU Lifa. Explainable Anomaly Traffic Detection Based on Sparse Autoencoders [J]. Netinfo Security, 2023, 23(7): 74-85. |
| [5] | JIANG Yingzhao, CHEN Lei, YAN Qiao. Distributed Denial of Service Attack Detection Algorithm Based on Two-Channel Feature Fusion [J]. Netinfo Security, 2023, 23(7): 86-97. |
| [6] | ZHAO Caidan, CHEN Jingqian, WU Zhiqiang. Automatic Modulation Recognition Algorithm Based on Multi-Channel Joint Learning [J]. Netinfo Security, 2023, 23(4): 20-29. |
| [7] | TAN Liuyan, RUAN Shuhua, YANG Min, CHEN Xingshu. Educational Data Classification Based on Deep Learning [J]. Netinfo Security, 2023, 23(3): 96-102. |
| [8] | XU Zhanyang, CHENG Luofei, CHENG Jianchun, XU Xiaolong. A Scheme of Optimizing Deep Learning Model Using Bi-ADMM [J]. Netinfo Security, 2023, 23(2): 54-63. |
| [9] | CHEN Depeng, LIU Xiao, CUI Jie, ZHONG Hong. Research on Membership Inference Attack Method Based on Double Threshold Function [J]. Netinfo Security, 2023, 23(2): 64-75. |
| [10] | WEN Weiping, ZHU Yifan, LYU Zihan, LIU Chengjie. Brand-Specific Phishing Expansion and Detection Solutions [J]. Netinfo Security, 2023, 23(12): 1-9. |
| [11] | LIU Jun, WU Zhichao, WU Jian, TAN Zhenhua. A Malicious Code Recognition Model Fusing Image Spatial Feature Attention Mechanism [J]. Netinfo Security, 2023, 23(12): 29-37. |
| [12] | LIAO Liyun, ZHANG Bolei, WU Lifa. IoT Anomaly Detection Model Based on Cost-Sensitive Learning [J]. Netinfo Security, 2023, 23(11): 94-103. |
| [13] | WANG Zhi, ZHANG Hao, Jason GU. A Hybrid Method of Joint Entropy and Multiple Clustering Based DDoS Detection in SDN [J]. Netinfo Security, 2023, 23(10): 1-7. |
| [14] | JIA Fan, KANG Shuya, JIANG Weiqiang, WANG Guangtao. Vulnerability Similarity Algorithm Evaluation Based on NLP and Feature Fusion [J]. Netinfo Security, 2023, 23(1): 18-27. |
| [15] | GAO Bo, CHEN Lin, YAN Yingjian. Research on Side Channel Attack Based on CNN-MGU [J]. Netinfo Security, 2022, 22(8): 55-63. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||