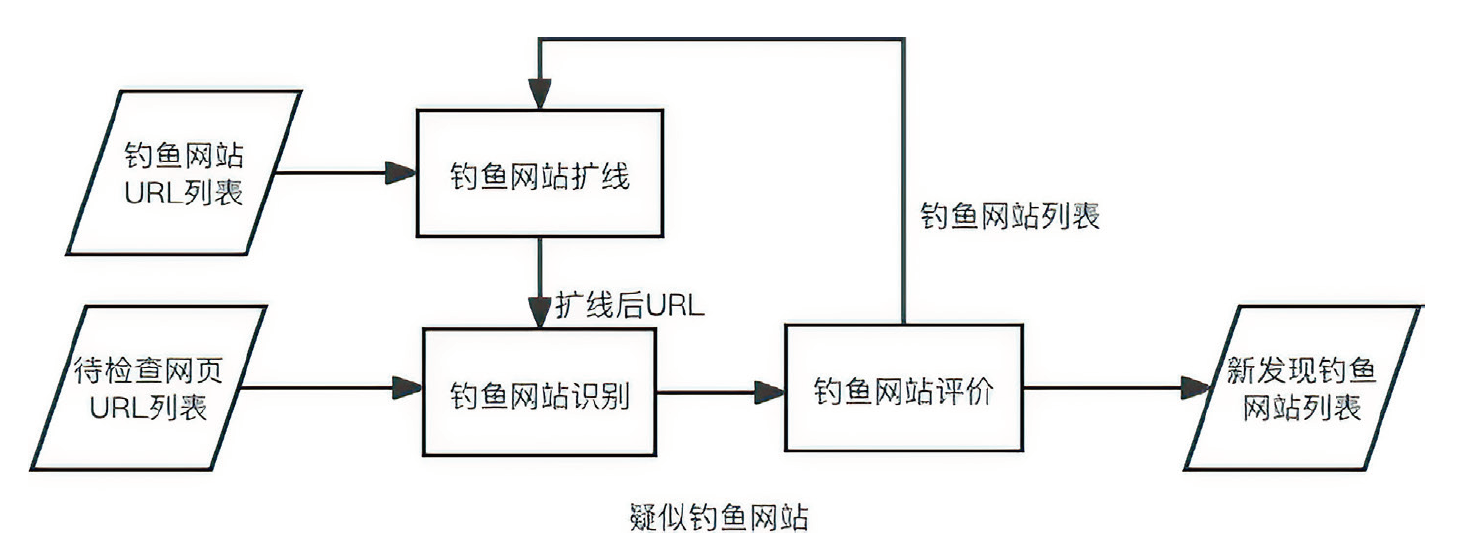
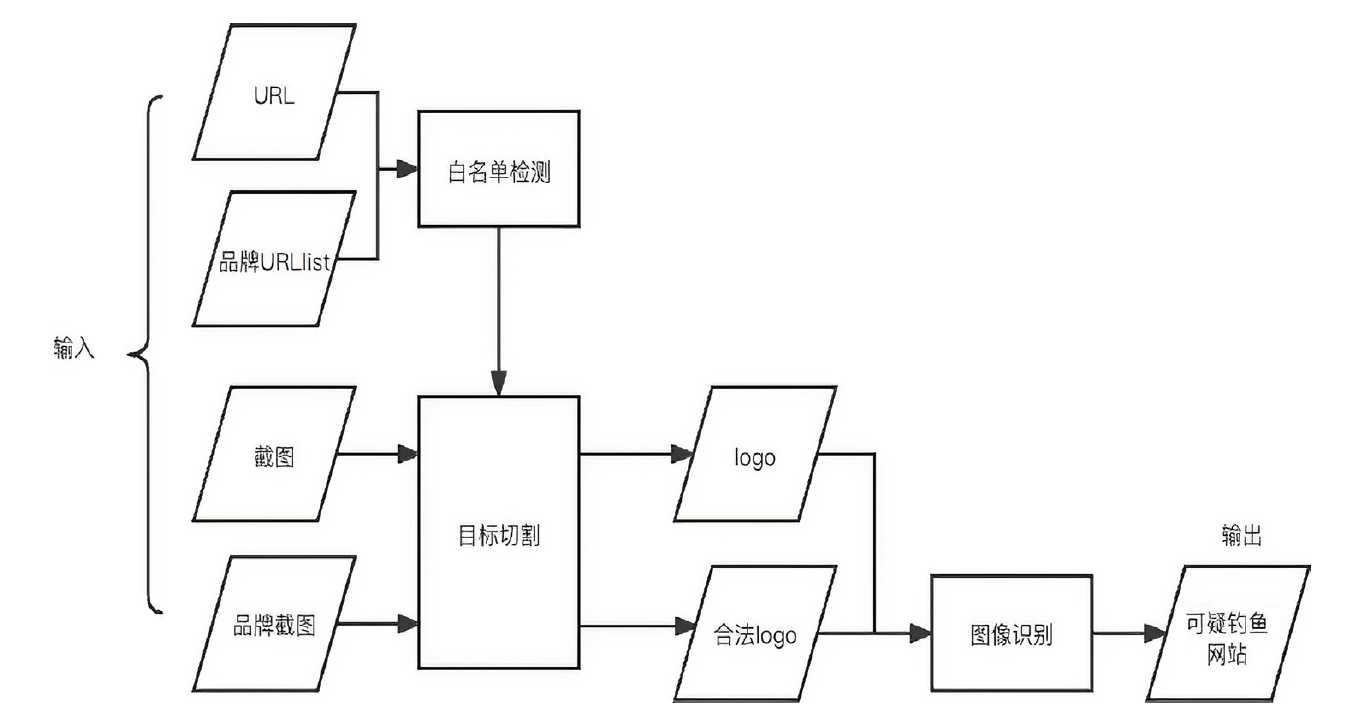
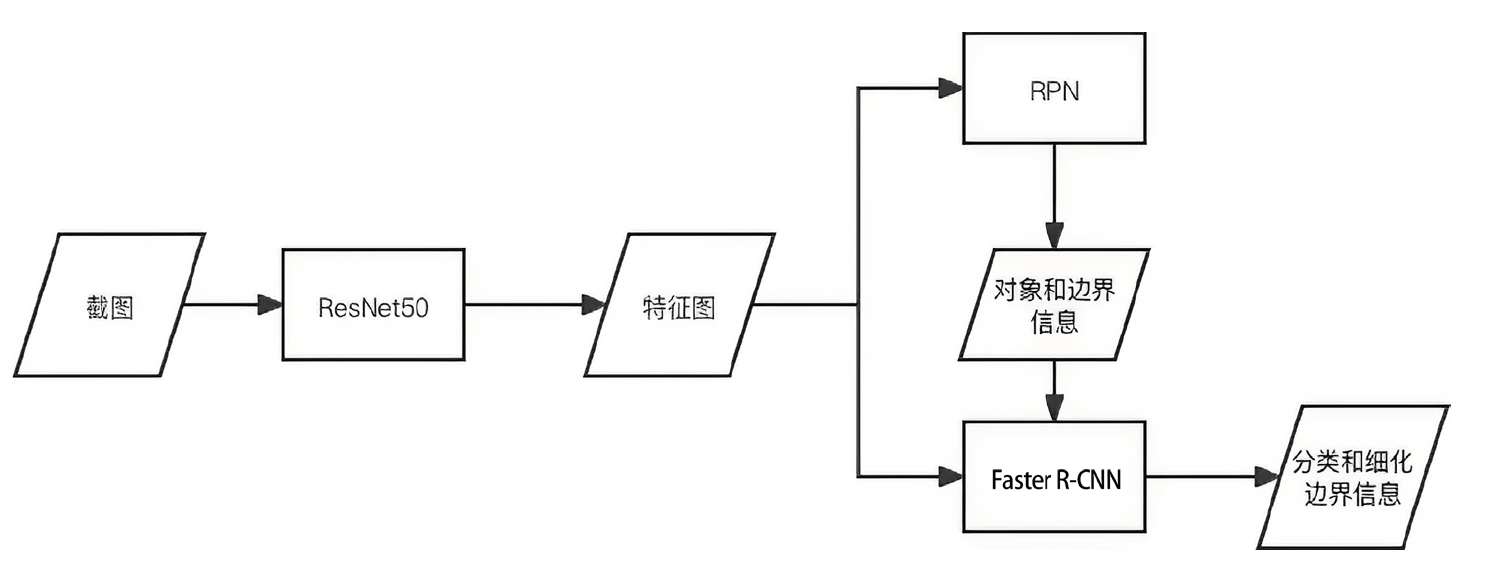
Netinfo Security ›› 2023, Vol. 23 ›› Issue (12): 1-9.doi: 10.3969/j.issn.1671-1122.2023.12.001
Previous Articles Next Articles
Brand-Specific Phishing Expansion and Detection Solutions
WEN Weiping( ), ZHU Yifan, LYU Zihan, LIU Chengjie
), ZHU Yifan, LYU Zihan, LIU Chengjie
- School of Software and Microelectronics, Peking University, Beijing 100080, China
-
Received:2023-08-15Online:2023-12-10Published:2023-12-13
CLC Number:
Cite this article
WEN Weiping, ZHU Yifan, LYU Zihan, LIU Chengjie. Brand-Specific Phishing Expansion and Detection Solutions[J]. Netinfo Security, 2023, 23(12): 1-9.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2023.12.001
| [1] | ITU. Measuring Digital Development: Facts and Figures 2022[EB/OL]. (2023-08-01)[2023-08-14]. https://www.itu.int/en/ITU-D/Statistics/Pages/facts/default.aspx. |
| [2] | HULME G V, GOODCHILD J. Social Engineering: The Basics[EB/OL]. (2010-01-14)[2023-08-14]. https://www2. cso.com.au/article/print/625643/social-engineering-basics/. |
| [3] |
CATAL C, GIRAY G, TEKINERDOGAN B, et al. Applications of Deep Learning for Phishing Detection: A Systematic Literature Review[J]. Knowledge and Information Systems, 2022, 64(6): 1457-1500.
doi: 10.1007/s10115-022-01672-x pmid: 35645443 |
| [4] | Google. Google Safe Browsing[EB/OL]. (2021-11-14)[2023-08-14]. https://safebrowsing.google.com. |
| [5] | VERMA R, DYER K. On the Character of Phishing URLs: Accurate and Robust Statistical Learning Classifiers[C]// ACM. Proceedings of the 5th ACM Conference on Data and Application Security and Privacy(CODASPY’15). New York: ACM, 2015: 111-122. |
| [6] | KARIM A, SHAHROZ M, MUSTOFA K, et al. Phishing Detection System through Hybrid Machine Learning Based on URL[J]. IEEE Access, 2023(11): 36805-36822. |
| [7] | ALJOFEY A, JIANG Qingshan, QU Qiang, et al. An Effective Phishing Detection Model Based on Character Level Convolutional Neural Network from URL[EB/OL]. (2020-09-15)[2023-08-14]. https://www.mdpi.com/2079-9292/9/9/1514. |
| [8] |
SAFI A, SINGH S. A Systematic Literature Review on Phishing Website Detection Techniques[J]. Journal of King Saud University-Computer and Information Sciences, 2023, 35(2): 590-611.
doi: 10.1016/j.jksuci.2023.01.004 URL |
| [9] |
FU A Y, LIU Wenyin, DENG Xiaotie. Detecting Phishing Web Pages with Visual Similarity Assessment Based on Earth Mover’s Distance (EMD)[J]. IEEE Transactions on Dependable and Secure Computing, 2006, 3(4): 301-311.
doi: 10.1109/TDSC.2006.50 URL |
| [10] | ABDELNABI S, KROMBHOLZ K, FRITZ M. VisualPhishNet: Zero-Day Phishing Website Detection by Visual Similarity[C]// ACM. Proceedings of the 2020 ACM SIGSAC Conference on Computer and Communications Security(CCS’20). New York: ACM, 2020: 1681-1698. |
| [11] | AFROZ S, GREENSTADT R. Phishzoo: Detecting Phishing Websites by Looking at Them[C]// IEEE. 2011 IEEE Fifth International Conference on Semantic Computing. New York: IEEE, 2011: 368-375. |
| [12] | BOZKIR A S, AYDOS M. LogoSENSE: A Companion HOG Based Logo Detection Scheme for Phishing Web Page and E-Mail Brand Recognition[EB/OL]. (2020-08-01)[2023-08-14]. https://www.sciencedirect.com/science/article/abs/pii/S0167404820301279. |
| [13] | CHANG E H, CHIEW K L, TIONG W K, et al. Phishing Detection via Identification of Website Identity[C]// IEEE. 2013 International Conference on IT Convergence and Security (ICITCS). New York: IEEE, 2013: 1-4. |
| [14] | WANG Ge, LIU He, BECERRA S, et al. Verilogo: Proactive Phishing Detection via Logo Recognition[EB/OL]. (2011-01-01)[2023-08-14]. https://hovav.net/ucsd/dist/verilogo.pdf. |
| [15] | YUN Lei, LI Dan, WANG Huanhuan. Summary of Research on Phishing Website Detection Technology[J]. Reliability and Environmental Testing of Electronic Products, 2021, 39(5): 114-119. |
| 云雷, 李丹, 王欢欢. 钓鱼网站检测技术研究综述[J]. 电子产品可靠性与环境试验, 2021, 39(5): 114-119. | |
| [16] | ASIRI S, XIAO Yang, ALZAHRANI S, et al. A Survey of Intelligent Detection Designs of HTML URL Phishing Attacks[J]. IEEE Access, 2023(11): 6421-6443. |
| [17] | BU S J, CHO S B. Deep Character-Level Anomaly Detection Based on a Convolutional Autoencoder for Zero-Day Phishing URL Detection[EB/OL]. (2021-06-17)[2023-08-14]. https://doi.org/10.3390/electronics10121492. |
| [18] | SOMESHA M, PAIS A R, RAO R S, et al. Efficient Deep Learning Techniques for the Detection of Phishing Websites[EB/OL]. (2020-06-17)[2023-08-14]. https://link.springer.com/article/10.1007/s12046-020-01392-4. |
| [19] | ADEBOWALE M A, LWIN K T, HOSSAIN M A. Intelligent Phishing Detection Scheme Using Deep Learning Algorithms[EB/OL]. (2020-06-04)[2023-08-14]. https://www.emerald.com/insight/content/doi/10.1108/JEIM-01-2020-0036/full/html. |
| [20] | HE Kaiming, ZHANG Xiangyu, REN Shaoqing, et al. Deep Residual Learning for Image Recognition[C]// IEEE. Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition. New York: IEEE, 2016: 770-778. |
| [21] |
REN Shaoqing, HE Kaiming, GIRSHICK R, et al. Faster R-CNN: Towards Real-Time Object Detection with Region Proposal Networks[J]. IEEE Transactions on Pattern Analysis and Machine Intelligence, 2015, 39(6): 1137-1149.
doi: 10.1109/TPAMI.2016.2577031 URL |
| [22] | ABDILLAH R, SHUKUR Z, MOHD M, et al. Performance Evaluation of Phishing Classification Techniques on Various Data Sources and Schemes[J]. IEEE Access, 2023(11): 38721-38738. |
| [23] | TAN Mingxing, LE Q V. Efficientnetv2: Smaller Models and Faster Training[C]// PMLR. International Conference on Machine Learning. New York: PMLR, 2021: 10096-10106. |
| [24] |
DAVOUDI M R, YARI A R. Improving the Feature Section Method Based on Genetic Algorithm to Increase the Efficiency of Detecting Phishing Websites[J]. Automatic Control and Computer Sciences, 2023, 57(3): 213-221.
doi: 10.3103/S0146411623030045 |
| [25] | LIN Yun, LIU Ruofan, DIVAKARAN D M, et al. Phishpedia: A Hybrid Deep Learning Based Approach to Visually Identify Phishing Webpages[C]// USENIX. In 30th USENIX Security Symposium. Berlin:USENIX, 2021: 3793-3810. |
| [26] | WANG Jing, MIN Weiqing, HOU Sujuan, et al. Logo-2K+: A Large-Scale Logo Dataset for Scalable Logo Classification[C]// IEEE. Proceedings of the AAAI Conference on Artificial Intelligence. New York: IEEE, 2020, 34(4): 6194-6201. |
| [1] | XUE Yu, ZHANG Yixuan. Survey on Deep Neural Architecture Search [J]. Netinfo Security, 2023, 23(9): 58-74. |
| [2] | LIU Yuxiao, CHEN Wei, ZHANG Tianyue, WU Lifa. Explainable Anomaly Traffic Detection Based on Sparse Autoencoders [J]. Netinfo Security, 2023, 23(7): 74-85. |
| [3] | JIANG Yingzhao, CHEN Lei, YAN Qiao. Distributed Denial of Service Attack Detection Algorithm Based on Two-Channel Feature Fusion [J]. Netinfo Security, 2023, 23(7): 86-97. |
| [4] | ZHAO Caidan, CHEN Jingqian, WU Zhiqiang. Automatic Modulation Recognition Algorithm Based on Multi-Channel Joint Learning [J]. Netinfo Security, 2023, 23(4): 20-29. |
| [5] | TAN Liuyan, RUAN Shuhua, YANG Min, CHEN Xingshu. Educational Data Classification Based on Deep Learning [J]. Netinfo Security, 2023, 23(3): 96-102. |
| [6] | XU Zhanyang, CHENG Luofei, CHENG Jianchun, XU Xiaolong. A Scheme of Optimizing Deep Learning Model Using Bi-ADMM [J]. Netinfo Security, 2023, 23(2): 54-63. |
| [7] | CHEN Depeng, LIU Xiao, CUI Jie, ZHONG Hong. Research on Membership Inference Attack Method Based on Double Threshold Function [J]. Netinfo Security, 2023, 23(2): 64-75. |
| [8] | LIU Jun, WU Zhichao, WU Jian, TAN Zhenhua. A Malicious Code Recognition Model Fusing Image Spatial Feature Attention Mechanism [J]. Netinfo Security, 2023, 23(12): 29-37. |
| [9] | LIAO Liyun, ZHANG Bolei, WU Lifa. IoT Anomaly Detection Model Based on Cost-Sensitive Learning [J]. Netinfo Security, 2023, 23(11): 94-103. |
| [10] | JIA Fan, KANG Shuya, JIANG Weiqiang, WANG Guangtao. Vulnerability Similarity Algorithm Evaluation Based on NLP and Feature Fusion [J]. Netinfo Security, 2023, 23(1): 18-27. |
| [11] | GAO Bo, CHEN Lin, YAN Yingjian. Research on Side Channel Attack Based on CNN-MGU [J]. Netinfo Security, 2022, 22(8): 55-63. |
| [12] | ZHENG Yaohao, WANG Liming, YANG Jing. A Defense Method against Adversarial Attacks Based on Neural Architecture Search [J]. Netinfo Security, 2022, 22(3): 70-77. |
| [13] | GUO Sensen, WANG Tongli, MU Dejun. Anomaly Detection Model Based on Generative Adversarial Network and Autoencoder [J]. Netinfo Security, 2022, 22(12): 7-15. |
| [14] | ZHANG Zhi, LI Xin, YE Naifu, HU Kaixi. CAPTCHA Security Enhancement Method Incorporating Multiple Style Migration and Adversarial Examples [J]. Netinfo Security, 2022, 22(10): 129-135. |
| [15] | LIU Shuo, ZHANG Xinglan. Intrusion Detection System Based on Dual Attention [J]. Netinfo Security, 2022, 22(1): 80-86. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||