Netinfo Security ›› 2023, Vol. 23 ›› Issue (4): 61-71.doi: 10.3969/j.issn.1671-1122.2023.04.007
Previous Articles Next Articles
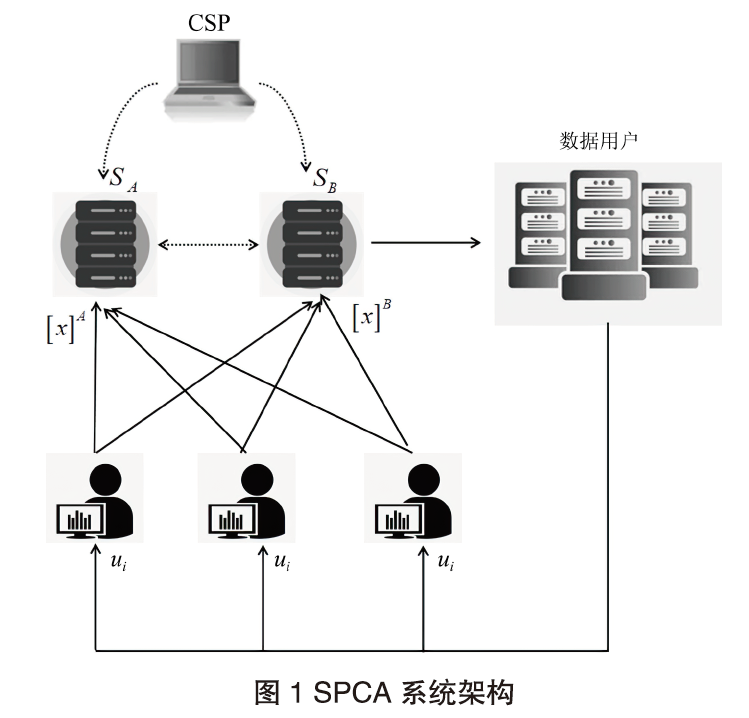
A Principal Component Analysis Scheme for Security Outsourcing in Cloud Environment Based on Secret Sharing
MA Min1,2, FU Yu1( ), HUANG Kai3
), HUANG Kai3
- 1. Department of Information Security, Naval University of Engineering, Wuhan 430033, China
2. Department of Software Engineering, The Hubei Open University, Wuhan 430074, China
3. College of Joint Operation, National Defense University, Shijiazhuang 050084, China
-
Received:2022-12-27Online:2023-04-10Published:2023-04-18 -
Contact:FU Yu E-mail:fuyu0219@163.com
CLC Number:
Cite this article
MA Min, FU Yu, HUANG Kai. A Principal Component Analysis Scheme for Security Outsourcing in Cloud Environment Based on Secret Sharing[J]. Netinfo Security, 2023, 23(4): 61-71.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2023.04.007
| [1] |
LI Fenghua, LI Hui, NIU Ben, et al. Privacy Computing: Concept, Computing Framework, and Future Development Trends[J]. Engineering, 2019, 5(6): 1179-1192.
doi: 10.1016/j.eng.2019.09.002 |
| [2] |
ZHOU Xiao, GUO Ying, LI Fangshun, et al. Identifying and Assessing Innovation Pathways for Emerging Technologies: A Hybrid Approach Based on Text Mining and Altmetrics[J]. IEEE Transactions on Engineering Management, 2020, 68(5): 1360-1371.
doi: 10.1109/TEM.2020.2994049 URL |
| [3] |
FENG Chunmei, XU Yong, LIU Jinxing, et al. Supervised Discriminative Sparse PCA for Com-Characteristic Gene Selection and Tumor Classification on Multiview Biological Data[J]. IEEE Transactions on Neural Networks and Learning Systems, 2019, 30(10): 2926-2937.
doi: 10.1109/TNNLS.2019.2893190 pmid: 30802874 |
| [4] | ZHAO Qing, WANG Huiwen, WANG Shanshan. A Principal Component Analysis of Interval Data Based on Center and Log-Radius[J]. Journal of Beijing University of Aeronautics and Astronautics, 2021, 47(7): 1414-1421. |
| 赵青, 王惠文, 王珊珊. 基于中心-对数半长的区间数据主成分分析[J]. 北京航空航天大学学报, 2021, 47(7):1414-1421. | |
| [5] | SONG Yue, SEBE N, WANG Wei. Batch-Efficient Eigen Decom-position for Small and Medium Matrices[EB/OL]. (2022-07-09)[2022-10-23]. https://arxiv.org/abs/2207.04228v1. |
| [6] |
LI Fenghua, LI Hui, JIA Yan, et al. Privacy Computing: Concept, Connotation and Its Research Trend[J]. Journal on Communications, 2016, 37(4): 1-11.
doi: 10.11959/j.issn.1000-436x.2016078 |
|
李凤华, 李晖, 贾焰, 等. 隐私计算研究范畴及发展趋势[J]. 通信学报, 2016, 37(4): 1-11.
doi: 10.11959/j.issn.1000-436x.2016078 |
|
| [7] | ZHANG Yuqing, WANG Xiaofei, LIU Xuefeng, et al. Survey on Cloud Computing Security[J]. Journal of Software, 2016, 27(6): 1328-1348. |
| 张玉清, 王晓菲, 刘雪峰, 等. 云计算环境安全综述[J]. 软件学报, 2016, 27(6): 1328-1348. | |
| [8] | QIAN Wenjun, SHEN Qingni, WU Pengfei, et al. Research Progress on Privacy-Preserving Techniques in Big Data Computing Environment[J]. Chinese Journal of Computers, 2022, 45(4): 669-701. |
| 钱文君, 沈晴霓, 吴鹏飞, 等. 大数据计算环境下的隐私保护技术研究进展[J]. 计算机学报, 2022, 45(4): 669-701. | |
| [9] | FENG Dengguo, YANG Kang. Concretely Efficient Secure Multi-Party Computation Protocols: Survey and More[EB/OL]. (2022-06-14)[2022-10-23]. https://sands.edpsciences.org/articles/sands/full_html/2022/01/sands20210001/sands20210001.html. |
| [10] |
LIU Yang, MA Zhuo, LIU Ximeng, et al. Privacy-Preserving Object Detection for Medical Images with Faster R-CNN[J]. IEEE Transactions on Information Forensics and Security, 2022, 17: 69-84.
doi: 10.1109/TIFS.2019.2946476 URL |
| [11] |
YING Zuobin, CAO Shuanglong, LIU Ximeng, et al. Privacy Signal: Privacy-Preserving Traffic Signal Control for Intelligent Transportation System[J]. IEEE Transactions on Intelligent Transportation Systems, 2022, 23(9): 16290-16303.
doi: 10.1109/TITS.2022.3149600 URL |
| [12] |
BI Renwan, XIONG Jinbo, TIAN Youliang, et al. Achieving Lightweight and Privacy-Preserving Object Detection for Connected Autonomous Vehicles[J]. IEEE Internet of Things Journal, 2022, 10(3): 2314-2329.
doi: 10.1109/JIOT.2022.3212464 URL |
| [13] |
LI Minghui, CHOW S S M, HU Shengshan, et al. Optimizing Privacy-Preserving Outsourced Convolutional Neural Network Predictions[J]. IEEE Transactions on Dependable and Secure Computing, 2020, 19(3): 1592-1604.
doi: 10.1109/TDSC.2020.3029899 URL |
| [14] | LIU Xiaoning, ZHENG Yifeng, YUAN Xingliang, et al. Securely Outsourcing Neural Network Inference to the Cloud with Lightweight Techniques[J]. IEEE Transactions on Dependable and Secure Computing, 2022. |
| [15] | FENG Qi, HE Debiao, LIU Zhe, et al. SecureNLP: A System for Multi-Party Privacy-Preserving Natural Language Processing[J]. IEEE Transactions on Information Forensics and Security, 2020(15): 3709-3721. |
| [16] | JOLLIFFE I T, CADIMA J. Principal Component Analysis: A Review and Recent Developments[EB/OL]. (2016-04-13)[2022-10-13]. https://royalsocietypublishing.org/doi/10.1098/rsta.2015.0202. |
| [17] | WANG Xinxin. Improvement and Analysis of Lanczos Algorithm for Solving Eigenvalue Problems of Symmetric Matrices[D]. Harbin:Harbin Institute of Technology, 2008. |
| 王欣欣. 求解对称矩阵特征值问题的 Lanczos 算法的改进及分析[D]. 哈尔滨: 哈尔滨工业大学, 2008. | |
| [18] |
DUBRULLE A A. Householder Transformations Revisited[J]. SIAM Journal on Matrix Analysis and Applications, 2000, 22(1): 33-40.
doi: 10.1137/S0895479898338561 URL |
| [19] | GE J, WANG Zhaoran, WANG Mengdi, et al. Minimax-Optimal Privacy-Preserving Sparse PCA in Distributed Systems[EB/OL]. (2020-02-25)[2022-10-20]. http://proceedings.mlr.press/v84/ge18a.html. |
| [20] |
WANG Di, XU Jinhui. Principal Component Analysis in the Local Differential Privacy Model[J]. Theoretical Computer Science, 2020, 809: 296-312.
doi: 10.1016/j.tcs.2019.12.019 URL |
| [21] | LIU Yingting, CHEN Chaochao, ZHENG Longfei, et al. Privacy Preserving PCA for Multiparty Modeling[EB/OL]. (2020-02-06)[2022-10-23]. https://www2.isye.gatech.edu/-fferdinando3/cfp/PPAI20/papers/paper_16.pdf. |
| [22] |
XIANG Can, TANG Chunming, CAI Yunlu, et al. Privacy-Preserving Face Recognition with Outsourced Computation[J]. Soft Computing, 2016, 20(9): 3735-3744.
doi: 10.1007/s00500-015-1759-5 URL |
| [23] | AL-RUBAIE M, WU Peiyuan, CHANG J M, et al. Privacy-Preserving PCA on Horizontally-Partitioned Data[C]// IEEE. 2017 IEEE Conference on Dependable and Secure Computing. New York: IEEE, 2017: 280-287. |
| [24] |
ZHANG Yushu, XIAO Xiangli, YANG Luxing, et al. Secure and Efficient Outsourcing of PCA-Based Face Recognition[J]. IEEE Transactions on Information Forensics and Security, 2019, 15: 1683-1695.
doi: 10.1109/TIFS.10206 URL |
| [25] | REN Yanli, XU Xiao, FENG Guorui, et al. Non-Interactive and Secure Outsourcing of PCA-Based Face Recognition[EB/OL]. (2021-11-01)[2022-10-23]. https://dl.acm.org/doi/10.1016/j.cose.2021.102416. |
| [26] | WEI Lu, SARWATE A D, CORANDER J, et al. Analysis of a Privacy-Preserving PCA Algorithm Using Random Matrix Theory[C]// IEEE. 2016 IEEE Global Conference on Signal and Information Processing (GlobalSIP). New York: IEEE, 2016: 1335-1339. |
| [27] | ANOWAR F, SADAOUI S, SELIM B. Conceptual and Empirical Comparison of Dimensionality Reduction Algorithms (PCA, KPCA, LDA, MDS, SVD, LLE, ISOMAP, LE, ICA, t-SNE)[EB/OL]. (2021-05-01)[2022-10-23]. https://www.sciencedirect.com/science/article/abs/pii/S1574013721000186. |
| [28] | HUANG Kai, LIU Ximeng, FU Shaojing, et al. A Lightweight Privacy-Preserving CNN Feature Extraction Framework for Mobile Sensing[J]. IEEE Transactions on Dependable and Secure Computing, 2019, 18(3): 1441-1455. |
| [29] |
WANG Qian, DU Minxin, CHEN Xiuying, et al. Privacy-Preserving Collaborative Model Learning: The Case of Word Vector Training[J]. IEEE Transactions on Knowledge and Data Engineering, 2018, 30(12): 2381-2393.
doi: 10.1109/TKDE.69 URL |
| [30] | LINDELL Y. How to Simulate It-A Tutorial on the Simulation Proof Technique[J]. Tutorials on the Foundations of Cryptography, 2017(6): 277-346. |
| [1] | ZHANG Xuewang, ZHANG Hao, YAO Yaning, FU Jiali. Privacy Protection Scheme of Consortium Blockchain Based on Group Signature and Homomorphic Encryption [J]. Netinfo Security, 2023, 23(3): 56-61. |
| [2] | LIU Qin, GUO Kaiyuan, TU Hang. Task Data Migration Solution Based on SM2 and SM4 Under TEE [J]. Netinfo Security, 2023, 23(1): 9-17. |
| [3] | YU Chengli, ZHANG Yang, JIA Shijie. Research on Data Security Threats and Protection of Key Technologies in Cloud Environment [J]. Netinfo Security, 2022, 22(7): 55-63. |
| [4] | JIN Bo, TANG Qianjin, TANG Qianlin. Interpretation of the Top 10 Development Trends of Network Security in 2022 by CCF Computer Security Professional Committee [J]. Netinfo Security, 2022, 22(4): 1-6. |
| [5] | CHEN Yan, WEI Xiang, LU Zhen. Research on Testing Approaches for Network Security Products in Cloud Computing Environment [J]. Netinfo Security, 2022, 22(12): 1-6. |
| [6] | LYU Kewei, CHEN Chi. Research on Proactive Generation Protocol of Beaver Triples [J]. Netinfo Security, 2022, 22(12): 16-24. |
| [7] | LIN Faxin, ZHANG Jian. Design and Implementation of Abnormal Behavior Detection System for Virtualization Platform [J]. Netinfo Security, 2022, 22(11): 62-67. |
| [8] | XIAO Xiaolei, ZHAO Xuelian. Overview of the Research on Governance of Cross-Border Data Flow in China [J]. Netinfo Security, 2022, 22(10): 45-51. |
| [9] | YANG Xiaoqi, BAI Lifang, TANG Gang. Research and Design of Data Security Evaluation Model Based on DSMM Model [J]. Netinfo Security, 2021, 21(9): 90-95. |
| [10] | LIU Lu, LI Zhihui, LU Dianjun, YAN Chenhong. Quantum Secret Sharing Scheme Based on Linear Codes [J]. Netinfo Security, 2021, 21(8): 62-69. |
| [11] | CHEN Bowei, XIA Xuan, ZHONG Weidong, WU Liqiang. The Defense Scheme of S-box on LBlock Based on Secret Sharing [J]. Netinfo Security, 2021, 21(7): 80-86. |
| [12] | YOU Wenting, ZHANG Leyou, YE Yadi, LI Hui. Privacy-preserving Attribute-based Dynamic Broadcast Encryption Mechanism in Multi-user Communication System [J]. Netinfo Security, 2021, 21(4): 21-30. |
| [13] | SHI Leyi, XU Xinghua, LIU Yihao, LIU Jia. An Improved Probabilistic Neural Network Method of Security Situation Assessment for Industrial Control System [J]. Netinfo Security, 2021, 21(3): 15-25. |
| [14] | ZHU Yanhua, LIAO Fangyu, HU Lianglin, WANG Zhiqiang. Research on Key Problems of Scientific Data Security Standard [J]. Netinfo Security, 2021, 21(11): 1-8. |
| [15] | LIU Hong, ZHANG Yuejin, ZHAO Wenxia, YANG Mu. A Security Management Framework for Data Sensitivity and Multidimensional Classification [J]. Netinfo Security, 2021, 21(10): 48-53. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||