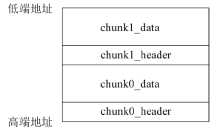
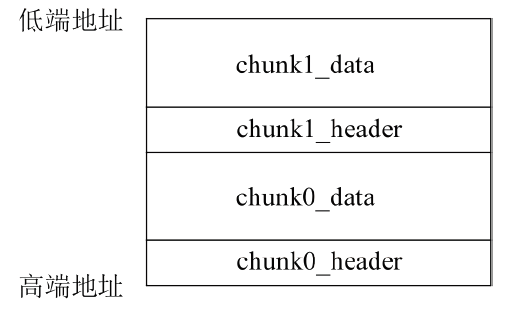
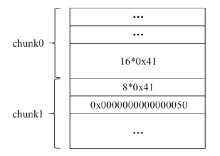
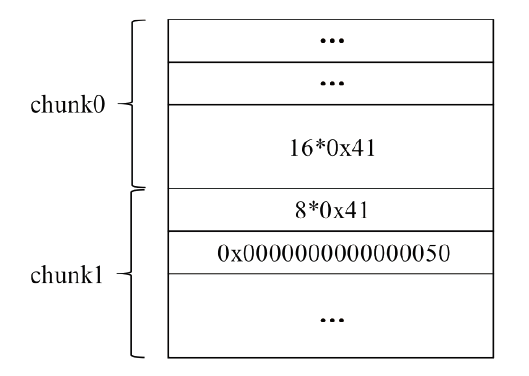
Netinfo Security ›› 2022, Vol. 22 ›› Issue (11): 47-54.doi: 10.3969/j.issn.1671-1122.2022.11.006
Previous Articles Next Articles
Analysis of SM2 Encryption and Decryption Vulnerability in OpenSSL
LIU Zhenya1,2, LIN Jingqiang1,2,3( )
)
- 1. University of Science and Technology, Hefei 230027, China
2. Key Laboratory of Electromagnetic Space Information, Hefei 230027, China
3. Beijing Research Institute of USTC, Beijing 100193, China