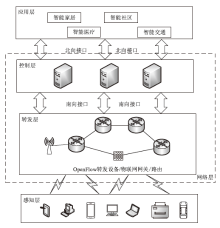
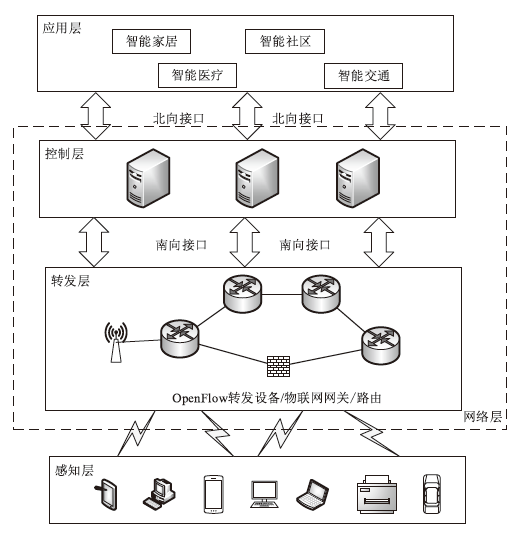
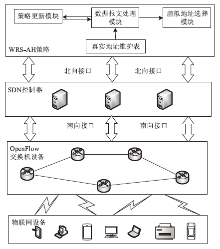
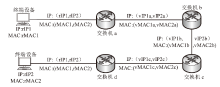
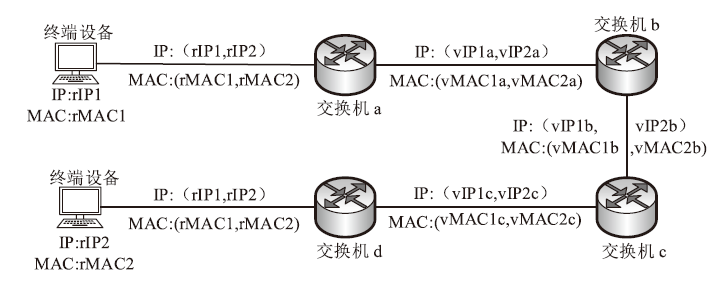
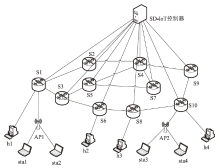
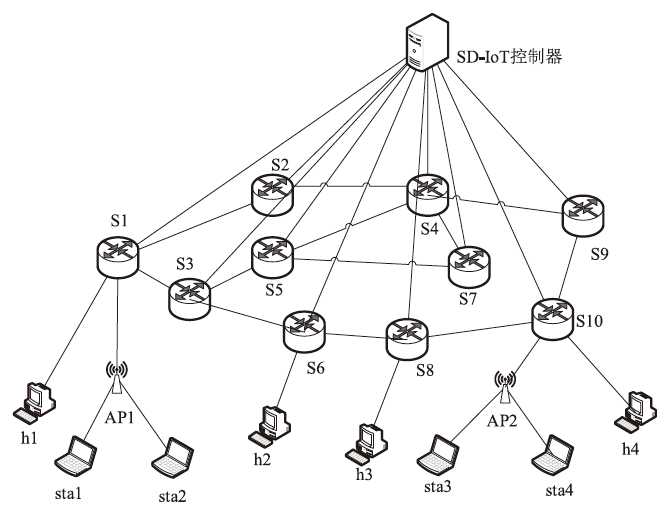
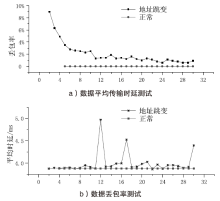
| [1] |
GUBBI J, BUYYA R, MARUSIC S, et al. Internet of Things (IoT): A Vision Architectural Elements and Future Directions[J]. Future Generation Computer Systems, 2013, 29(7): 1645-1660.
doi: 10.1016/j.future.2013.01.010
URL
|
| [2] |
VAILSHERY L S. IoT and Non-IoT Connections Worldwide 2010-2025[EB/OL]. (2021-03-08)[2022-06-10]. .
|
| [3] |
JIAN M S, WU J M T. Hybrid Internet of Things (IoT) Data Transmission Security Corresponding to Device Verification[EB/OL]. (2021-03-30)[2022-06-10]. .
|
| [4] |
ANTHI E, AHMAD S, RANA O, et al. EclipseIoT: A Secure and Adaptive Hub for the Internet of Things[J]. Computers & Security, 2018, 78: 477-490.
doi: 10.1016/j.cose.2018.07.016
URL
|
| [5] |
IQBAL W, ABBAS H, DANESHMAND M, et al. An In-Depth Analysis of IoT Security Requirements, Challenges, and their Countermeasures via Software-Defined Security[J]. IEEE Internet of Things Journal, 2020, 7(10): 10250-10276.
doi: 10.1109/JIOT.2020.2997651
URL
|
| [6] |
LIU Gang, QUAN Wei, CHENG Nan, et al. Softwarized IoT Network Immunity Against Eavesdropping with Programmable Data Planes[J]. IEEE Internet of Things Journal, 2021, 8(8): 6578-6590.
doi: 10.1109/JIOT.2020.3048842
URL
|
| [7] |
TAN S Y, YEOW K W, HWANG S O. Enhancement of a Lightweight Attribute-Based Encryption Scheme for the Internet of Things[J]. IEEE Internet of Things Journal, 2019, 6(4): 6384-6395.
doi: 10.1109/JIOT.2019.2900631
URL
|
| [8] |
ZHANG Yuntong, XU Jingye, WANG Zhiwei, et al. Efficient and Intelligent Attack Detection in Software Defined IoT Networks[C]// IEEE. 2020 IEEE International Conference on Embedded Software and Systems (ICESS). New York:IEEE, 2020: 1-9.
|
| [9] |
ESKANDARI M, JANJUA Z H, VECCHIO M, et al. Passban IDS: An Intelligent Anomaly-Based Intrusion Detection System for IoT Edge Devices[J]. IEEE Internet of Things Journal, 2020, 7(8): 6882-6897.
doi: 10.1109/JIOT.2020.2970501
URL
|
| [10] |
ZHOU Yuyang, CHENG Guang, GUO Chunsheng, et al. Survey on Attack Surface Dynamic Transfer Technology Based on Moving Target Defense[J]. Journal of Software, 2018, 29(9): 2799-2820.
|
|
周余阳, 程光, 郭春生, 等. 移动目标防御的攻击面动态转移技术研究综述[J]. 软件学报, 2018, 29(9):2799-2820.
|
| [11] |
ZHANG Chaokun, CUI Yong, TANG Heyi, et al. State-of-the-Art Survey on Software-Defined Networking (SDN)[ J]. Journal of Software, 2015, 26(1): 62-81.
|
|
张朝昆, 崔勇, 唐翯祎, 等. 软件定义网络(SDN)研究进展[J]. 软件学报, 2015, 26(1):62-81.
|
| [12] |
CHEN Liang, LI Feng, REN Baoquan, et al. Software-Defined Internet of Things: A Survey[J]. Acta Electronica Sinica, 2021, 49(5): 1019-1032.
doi: 10.12263/DZXB.20200561
|
|
陈亮, 李峰, 任保全, 等. 软件定义物联网研究综述[J]. 电子学报, 2021, 49(5):1019-1032.
doi: 10.12263/DZXB.20200561
|
| [13] |
OJO M, ADAMI D, GIORDANO S. A SDN-IoT Architecture with NFV Implementation[C]// IEEE.2016 IEEE Globecom Workshops (GC Wkshps). New York:IEEE, 2016: 1-6.
|
| [14] |
LIU Xiangju, LIU Pengcheng, XU Hui, et al. Distributed Denial of Service Attack Detection Method Based on Software Defined Internet of Things[J]. Journal of Computer Applications, 2020, 40(3): 753-759.
doi: 10.11772/j.issn.1001-9081.2019091611
|
|
刘向举, 刘鹏程, 徐辉, 等. 基于软件定义物联网的分布式拒绝服务攻击检测方法[J]. 计算机应用, 2020, 40(3):753-759.
doi: 10.11772/j.issn.1001-9081.2019091611
|
| [15] |
NAVAS R E, CUPPENS F, CUPPENS N B, et al. MTD, Where Art Thou? A Systematic Review of Moving Target Defense Techniques for IoT[J]. IEEE Internet of Things Journal, 2021, 8(10): 7818-7832.
doi: 10.1109/JIOT.2020.3040358
URL
|
| [16] |
KARMAKAR K K, VARADHARAJAN V, NEPAL S, et al. SDN-Enabled Secure IoT Architecture[J]. IEEE Internet of Things Journal, 2021, 8(8): 6549-6564.
doi: 10.1109/JIOT.2020.3043740
URL
|
| [17] |
MERCADO-VELÁZQUEZ A A, ESCAMILLA-AMBROSIO P J, ORTIZ-RODRÍGUEZ F. A Moving Target Defense Strategy for Internet of Things Cybersecurity[J]. IEEE Access, 2021, 9: 118406-118418.
doi: 10.1109/ACCESS.2021.3107403
URL
|
| [18] |
NIZZI F, PECORELLA T, ESPOSITO F, et al. IoT Security via Address Shuffling: The Easy Way[J]. IEEE Internet of Things Journal, 2019, 6(2): 3764-3774.
doi: 10.1109/JIOT.2019.2892003
|
| [19] |
ALMOHAIMEED A, GAMPA S, SINGH G. Privacy-Preserving IoT Devices[C]// IEEE. 2019 IEEE Long Island Systems, Applications and Technology Conference (LISAT). New York:IEEE, 2019: 1-5.
|
| [20] |
PAPPA A C, ASHOK A, GOVINDARASU M. Moving Target Defense for Securing Smart Grid Communications: Architecture, Implementation & Evaluation[C]// IEEE. 2017 IEEE Power & Energy Society Innovative Smart Grid Technologies Conference (ISGT). New York:IEEE, 2017: 1-5.
|
| [21] |
HE Yun, ZHANG Min, YANG Xiaolong, et al. The Intelligent Offense and Defense Mechanism of Internet of Vehicles Based on the Differential Game-IP Hopping[J]. IEEE Access, 2020, 8: 115217-115227.
doi: 10.1109/ACCESS.2020.3004255
URL
|
| [22] |
LI Zhaoyang, TAN Jinglei, HU Ruiqin, et al. Moving Target Defense Method Based on Double Address Hopping[J]. Netinfo Security, 2021, 21(2): 24-33.
|
|
李朝阳, 谭晶磊, 胡瑞钦, 等. 基于双重地址跳变的移动目标防御方法[J]. 信息网络安全, 2021, 21(2):24-33.
|
| [23] |
HU Ruiqin, TAN Jinglei, PENG Xinhe, et al. Dynamic Hopping Technology of Double Virtual IP Address for SDN Data Layer[J]. Netinfo Security, 2022, 22(2): 76-85.
|
|
胡瑞钦, 谭晶磊, 彭心荷, 等. 面向SDN数据层的双虚假IP地址动态跳变技术[J]. 信息网络安全, 2022, 22(2):76-85.
|
| [24] |
SANABRIA-RUSSO L, ALONSO-ZARATE J, VERIKOUKIS C. SDN-Based Pro-Active Flow Installation Mechanism for Delay Reduction in IoT[C]// IEEE. 2018 IEEE Global Communications Conference (GLOBECOM). New York:IEEE, 2018: 1-6.
|
| [25] |
FONTES R R, AFZAL S, BRITO S H B, et al. Mininet-WiFi: Emulating Software-Defined Wireless Networks[C]// IEEE. 2015 11th International Conference on Network and Service Management (CNSM). New York:IEEE, 2015: 384-389.
|
| [26] |
LI Zhenyu, DING Yong, YUAN Fang, et al. An Integrated Protection Method of Moving Target Defense and Access Control Based on IPv6 Network[J]. Journal of Computer Research and Development, 2022, 59(5): 1105-1119.
|
|
李振宇, 丁勇, 袁方, 等. 基于IPv6网络的移动目标防御与访问控制融合防护方法[J]. 计算机研究与发展, 2022, 59(5):1105-1119.
|
 )
)