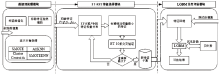
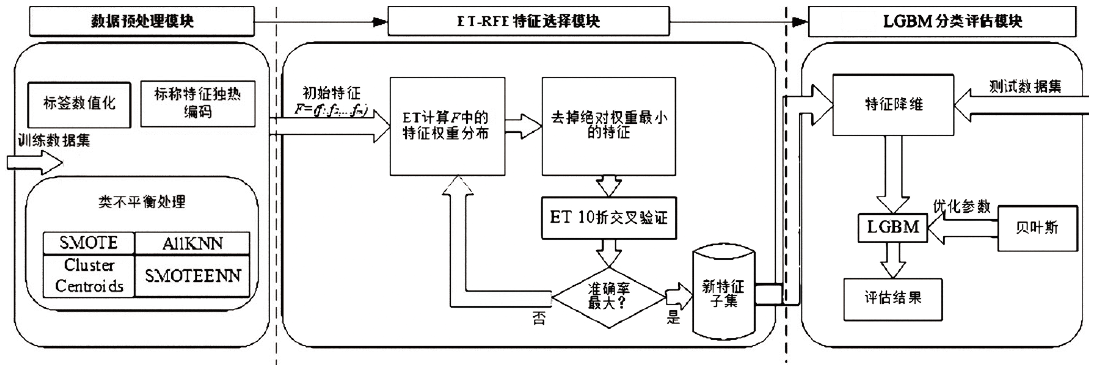
Netinfo Security ›› 2022, Vol. 22 ›› Issue (1): 64-71.doi: 10.3969/j.issn.1671-1122.2022.01.008
Previous Articles Next Articles
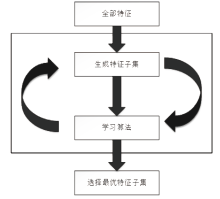
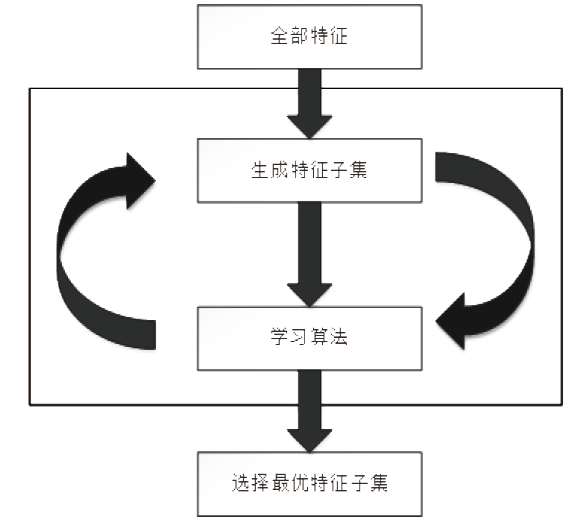
Intrusion Detection Model Based on Extra Trees-recursive Feature Elimination and LightGBM
HE Hongyan1,2, HUANG Guoyan1,2( ), ZHANG Bing1,2, JIA Damiao1,2
), ZHANG Bing1,2, JIA Damiao1,2
- 1. Department of Information Science and Engineering, Yanshan University, Qinhuangdao 066001, China
2. Hebei Key Laboratory of Software Engineering, Qinhuangdao 066001, China
-
Received:2021-08-24Online:2022-01-10Published:2022-02-16 -
Contact:HUANG Guoyan E-mail:hgy@ysu.edu.cn
CLC Number:
Cite this article
HE Hongyan, HUANG Guoyan, ZHANG Bing, JIA Damiao. Intrusion Detection Model Based on Extra Trees-recursive Feature Elimination and LightGBM[J]. Netinfo Security, 2022, 22(1): 64-71.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2022.01.008
| 类别 | 特征名称 | |
|---|---|---|
| 流特征 | Srcip、Sport、Dstip、Dsport、Proto | |
| 基本特性 | state、dur、sbytes、dbytes、sttl、dttl、sloss、dloss、service、sload、dload、spkts、dpkts | |
| 内容特征 | swin、dwin、stcpb、dtcpb、smeansz、dmeansz、trans_depth、res_bdy_len | |
| 时间特征 | sjit、djit、stime、ltime、sintpkt、dintpkt、tcprtt、synack、ackdat | |
| 附加生成的特征 | 通用特征 | is_sm_ips_ports、ct_state_ttl、ct_flw_http_mthd、 is_ftp_login、ct_ftp_cmd |
| 连接特征 | ct_srv_src、ct_srv_dst、ct_dst_ltm、ct_src_ ltm、ct_src_dport_ltm、ct_dst_sport_ltm、ct_dst_src_ltm | |
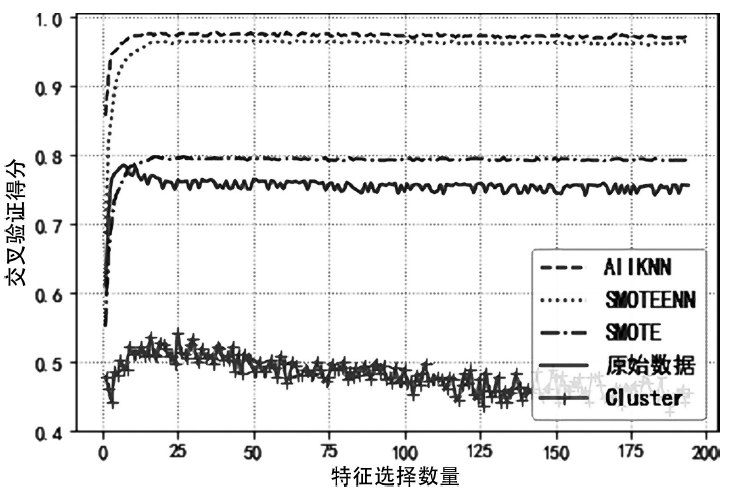
| 类别 | 原数据 /条 | SMOTE /条 | AllKNN /条 | ClusterCentroids /条 | SMOTEENN /条 |
|---|---|---|---|---|---|
| Fuzzers | 18184 | 18184 | 14035 | 130 | 11764 |
| Analysis | 2000 | 18184 | 383 | 130 | 6705 |
| Backdoor | 1746 | 18184 | 101 | 130 | 5851 |
| DOS | 12264 | 18184 | 6161 | 130 | 4723 |
| Reconnaiss- ance | 10491 | 18184 | 6231 | 130 | 10889 |
| Shellcode | 1133 | 18184 | 258 | 130 | 17344 |
| Worms | 130 | 18184 | 130 | 130 | 18059 |
| 算法 | 特征选择方法 | 特征 数量 | 分类 算法 | ACC | FAR |
|---|---|---|---|---|---|
| 文献[ | None | 42 | EM | 78.47% | 23.79% |
| 42 | LR | 83.15% | 18.48% | ||
| 42 | ANN | 81.34% | 21.13% | ||
| 42 | NB | 82.07% | 18.56% | ||
| 42 | DT | 85.56% | 15.78% | ||
| 其他算法 | None | 42 | KNN | 78.30% | 23.53% |
| 42 | SVM | 72.30% | 25.60% | ||
| 42 | RF | 87.14% | 14.13% | ||
| ET-RFE | 89 | Xgboost | 87.58% | 13.65% | |
| 文献[ | GALR | 20 | DT | 81.42% | 6.39% |
| 本文算法 | ET-RFE | 89 | LGBM | 87.64% | 13.59% |
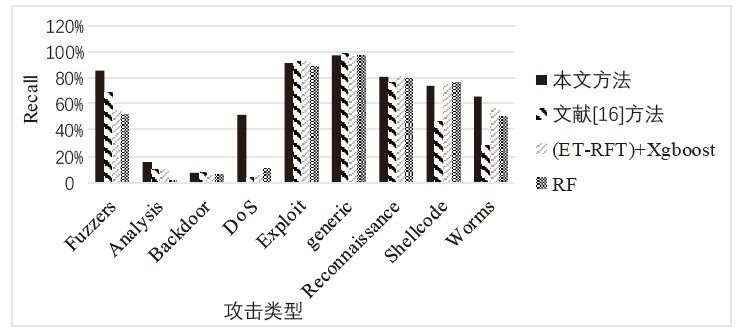
| 攻击类型 | 本文方法 | 文献[ | (ET-RFE) +Xgboost | RF |
|---|---|---|---|---|
| Fuzzers | 85.34% | 69.112% | 54.7% | 51.32% |
| Analysis | 15.95% | 9.929% | 9.45% | 0.89% |
| Backdoor | 7.38% | 6.925% | 4.80% | 5.67% |
| DoS | 51.97% | 4.113% | 4.52% | 10.42% |
| Exploit | 91.32% | 92.317% | 92.81% | 88.99% |
| generic | 97.00% | 97.937% | 96.68% | 97.15% |
| Reconnaissance | 80.75% | 76.150% | 80.92% | 80.18% |
| Shellcode | 74.35% | 47.468% | 75.13% | 76.46% |
| Worms | 65.91% | 28.465% | 56.82% | 50.0% |
| [1] | ZHOU Yuyang, CHENG Guang, JIANG Shanqing, et al. Building an Efficient Intrusion Detection System Based on Feature Selection and Ensemble Classifier[EB/OL]. https://doi.org/10.1016/j.comnet.2020.107247, 2020-06-19. |
| [2] | MUNA A L H, MOUSTAFA N, SITNIKOVA E. Identification of Malicious Activities in Industrial Internet of Things Based on Deep Learning Models[EB/OL]. https://doi.org/10.1016/j.jisa.2018.05.002, 2018-05-22. |
| [3] | AGARAP A F M. A Neural Network Architecture Combining Gated Recurrent Unit (GRU) and Support Vector Machine (SVM) for Intrusion Detection in Network Traffic Data[C]//ACM. Proceedings of the 2018 10th International Conference on Machine Learning and Computing (ICMLC), February 26-28, 2018, Macau, China. New York: ACM, 2018:26-30. |
| [4] |
SANGKATSANEE P N, WATTANAPONGSAKORN C, CHARNSRIPINYO C. Practical Real-time Intrusion Detection Using Machine Learning Approaches[J]. Computer Communications, 2011, 34(18):2227-2235.
doi: 10.1016/j.comcom.2011.07.001 URL |
| [5] | KORONIOTIS N, MOUSTAFA N, SITNIKOVA E, et al. Towards Developing Network Forensic Mechanism for Botnet Activities in the IoT Based on Machine Learning Techniques[EB/OL]. https://doi.org/10.1007/978-3-319-90775-8_3, 2018-05-19. |
| [6] | HU Weiming, HU Wei, MAYBANK S. AdaBoost-based Algorithm for Network Intrusion Detection[J]. IEEE Transactions on Systems, 2008, 38(2):577-583. |
| [7] |
MAZINI M, SHIRAZI B, MAHDAVI I. Anomaly Network-based Intrusion Detection System Using a Reliable Hybrid Artificial Bee Colony and AdaBoost Algorithms[J]. Journal of King Saud University-computer and Information Sciences, 2019, 31(4):541-553.
doi: 10.1016/j.jksuci.2018.03.011 URL |
| [8] | FARID D M, NOURIA H, RAHMAN M Z, et al. Combining Naive Bayes and Decision Tree for Adaptive Intrusion Detection[J]. International Journal of Network Security & Its Applications, 2010, 2(2):12-25. |
| [9] |
ABADEH M S, MOHAMADI H, HABIBI J. Design and Analysis of Genetic Fuzzy Systems for Intrusion Detection in Computer Networks[J]. Expert Systems with Applications, 2011, 38(6):7067-7075.
doi: 10.1016/j.eswa.2010.12.006 URL |
| [10] |
KOC L, MAZZUCHI T A, SARKANI S. A Network Intrusion Detection System Based on a Hidden Naïve Bayes Multiclass Classifier[J]. Expert Systems with Applications, 2012, 39(18):13492-13500.
doi: 10.1016/j.eswa.2012.07.009 URL |
| [11] |
FOSSACECA J M, MAZZUCHI T A, SARKANI S. MARK-ELM: Application of a Novel Multiple Kernel Learning Framework for Improving the Robustness of Network Intrusion Detection[J]. Expert Systems with Applications, 2015, 42(8):4062-4080.
doi: 10.1016/j.eswa.2014.12.040 URL |
| [12] | MANZOOR I, KUMAR N. A Feature Reduced Intrusion Detection System Using ANN Classifier[EB/OL]. https://doi.org/10.1016/j.eswa.2017.07.005, 2017-12-01. |
| [13] | LIU Jinghao, SUN Xiaowei, JIN Jie. Intrusion Detection Model Based on Principle Component Analysis and Recurrent Neural Network[J]. Journal of Chinese Information Processing, 2020, 34(10):105-112. |
| 刘敬浩, 孙晓伟, 金杰. 基于主成分分析和循环神经网络的入侵检测模型[J]. 中文信息学报, 2020, 34(10):105-112. | |
| [14] |
HAMED T, DARA R, KREMER S C. Network Intrusion Detection System Based on Recursive Feature Addition and Bigram Technique[J]. Computers & Security, 2017, 73(3):137-155.
doi: 10.1016/j.cose.2017.10.011 URL |
| [15] |
KHAMMASSI C, KRICHEN S. A GA-LR Wrapper Approach for Feature Selection in Network INTRUSION Detection[J]. Computers & Security, 2017, 70(9):255-277.
doi: 10.1016/j.cose.2017.06.005 URL |
| [16] |
ADHAO R, PACHGHARE V. Feature Selection Using Principal Component Analysis and Genetic Algorithm[J]. Journal of Discrete Mathematical Sciences and Cryptography, 2020, 23(2):595-602.
doi: 10.1080/09720529.2020.1729507 URL |
| [17] |
LATAH M, TOKER L. Towards an Efficient Anomaly-based Intrusion Detection for SoftWare-defined Networks[J]. IET Networks, 2018, 7(6):453-459.
doi: 10.1049/ntw2.v7.6 URL |
| [18] |
NANCY P, MUTHURAJKUMAR S, GANAPATHY S, et al. Intrusion Detection Using Dynamic Feature Selection and Fuzzy Temporal Decision Tree Classification for Wireless Sensor Network[J]. IET Communications, 2020, 14(5):888-895.
doi: 10.1049/cmu2.v14.5 URL |
| [19] | LIANG Jie, CHEN Jiahao, ZHANG Xueqin, et al. One-hot Encoding and Convolutional Neural Network Based Anomaly Detection[J]. Journal of Tsinghua University(Science and Technology), 2019, 59(7):523-529. |
| 梁杰, 陈嘉豪, 张雪芹, 等. 基于独热编码和卷积神经网络的异常检测[J]. 清华大学学报(自然科学版), 2019, 59(7):523-529. | |
| [20] |
CHAWLA N V, BOWYER K W, HALL L O, et al. SMOTE: Synthetic Minority Over-sampling Technique[J]. Journal of Artificial Intelligence Research, 2002, 16(1):321-357.
doi: 10.1613/jair.953 URL |
| [21] | GU Tong, XU Guoliang, LI Wanlin, et al. Intelligent House Price Evaluation Model based on Ensemble LightGBM and Bayesian Optimization Strategy[J]. Journal of Computer Applications, 2020, 361(9):290-295. |
| 顾桐, 许国良, 李万林, 等. 基于集成LightGBM和贝叶斯优化策略的房价智能评估模型[J]. 计算机应用, 2020, 361(9):290-295. | |
| [22] | WEI Zhiqiang, ZHANG Hao, CHEN Long. Web Anomaly Detection Model Using SmoteTomek and LightGBM Algorithm[J]. Journal of Chinese Computer Systems, 2020(3):587-592. |
| 魏志强, 张浩, 陈龙. 一种采用SmoteTomek和LightGBM算法的Web异常检测模型[J]. 小型微型计算机系统, 2020(3):587-592. | |
| [23] | MOUSTAFA N, SLAY J. UNSW-NB15: A Comprehensive Data Set for Network Intrusion Detection Systems[C]//IEEE. Military Communications and Information Systems Conference(MilCIS), November 10-12, 2015, Canberra, Australia. Piscataway: IEEE, 2015: 1-6. |
| [1] | BAI Hongpeng, DENG Dongxu, XU Guangquan, ZHOU Dexiang. Research on Intrusion Detection Mechanism Based on Federated Learning [J]. Netinfo Security, 2022, 22(1): 46-54. |
| [2] | LIU Shuo, ZHANG Xinglan. Intrusion Detection System Based on Dual Attention [J]. Netinfo Security, 2022, 22(1): 80-86. |
| [3] | LI Qun, DONG Jiahan, GUAN Zhitao, WANG Chao. A Clustering and Classification-based Malicious Attack Detection Method for Internet of Things [J]. Netinfo Security, 2021, 21(8): 82-90. |
| [4] | REN Tao, JIN Ruochen, LUO Yongmei. Network Intrusion Detection Algorithm Integrating Blockchain and Federated Learning [J]. Netinfo Security, 2021, 21(7): 27-34. |
| [5] | DU Ye, WANG Zimeng, LI Meihong. Industrial Control Intrusion Detection Method Based on Optimized Kernel Extreme Learning Machine [J]. Netinfo Security, 2021, 21(2): 1-9. |
| [6] | WANG Huazhong, CHENG Qi. Research on Intrusion Detection of Industrial Control System Based on Improved Whale Algorithm [J]. Netinfo Security, 2021, 21(2): 53-60. |
| [7] | SHEN Yeming, LI Beibei, LIU Xiaojie, OUYANG Yuankai. Research on Active Learning-based Intrusion Detection Approach for Industrial Internet [J]. Netinfo Security, 2021, 21(1): 80-87. |
| [8] | LI Qiao, LONG Chun, WEI Jinxia, ZHAO Jing. A Hybrid Model of Intrusion Detection Based on LMDR and CNN [J]. Netinfo Security, 2020, 20(9): 117-121. |
| [9] | XU Guotian. Research on K-Nearest Neighbor High Speed Matching Algorithm in Network Intrusion Detection [J]. Netinfo Security, 2020, 20(8): 71-80. |
| [10] | JIANG Nan, CUI Yaohui, WANG Jian, WU Jinchao. Context-based Attack Scenario Reconstruction Model for IDS Alarms [J]. Netinfo Security, 2020, 20(7): 1-10. |
| [11] | ZHANG Xiaoyu, WANG Huazhong. Intrusion Detection of ICS Based on Improved Border-SMOTE for Unbalance Data [J]. Netinfo Security, 2020, 20(7): 70-76. |
| [12] | PENG Zhonglian, WAN Wei, JING Tao, WEI Jinxia. Research on Intrusion Detection Method Based on Modified CGANs [J]. Netinfo Security, 2020, 20(5): 47-56. |
| [13] | WANG Rong, MA Chunguang, WU Peng. An Intrusion Detection Method Based on Federated Learning and Convolutional Neural Network [J]. Netinfo Security, 2020, 20(4): 47-54. |
| [14] | BIAN Lingyu, ZHANG Linlin, ZHAO Kai, SHI Fei. Ethereum Malicious Account Detection Method Based on LightGBM [J]. Netinfo Security, 2020, 20(4): 73-80. |
| [15] | LUO Wenhua, XU Caidian. Network Intrusion Detection Based on Improved MajorClust Clustering [J]. Netinfo Security, 2020, 20(2): 14-21. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||