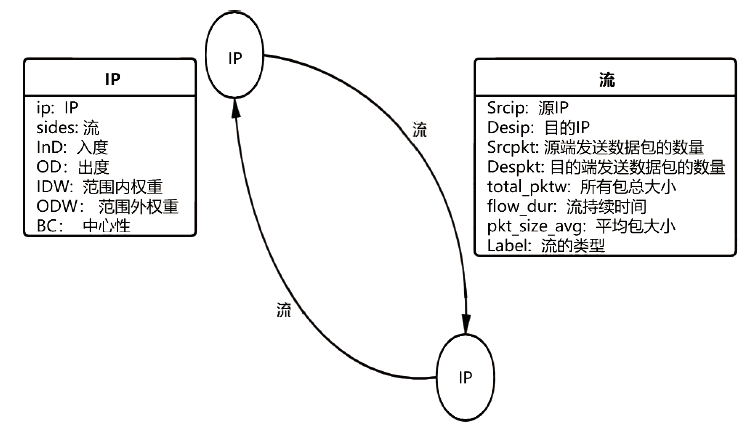
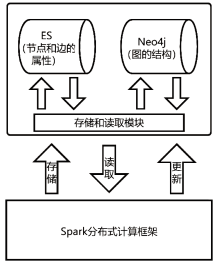
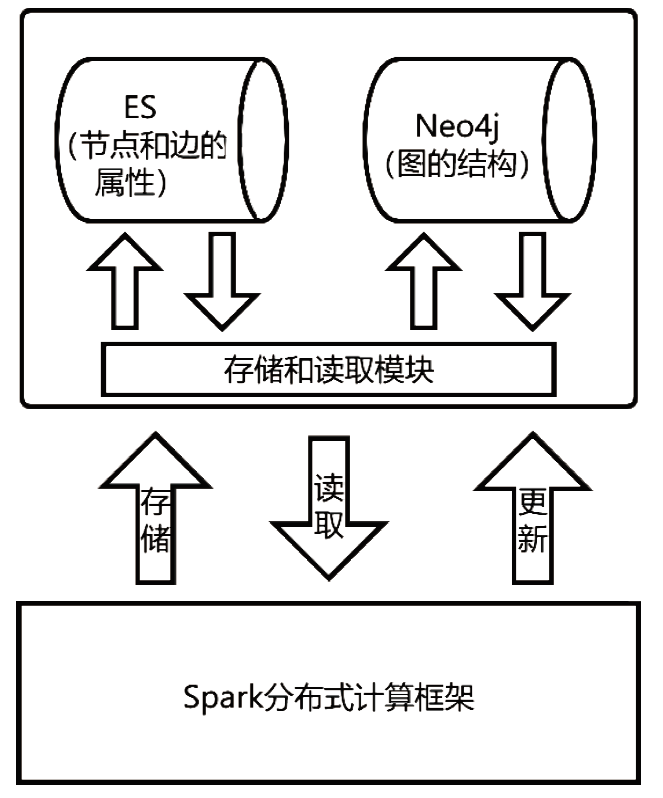
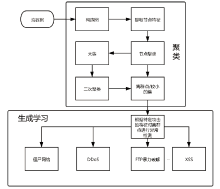
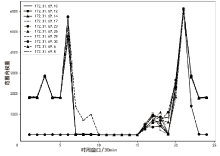
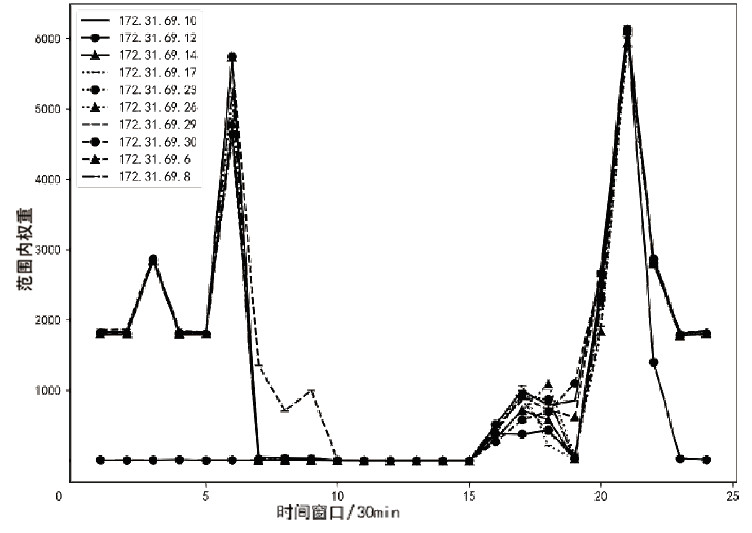
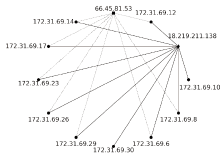
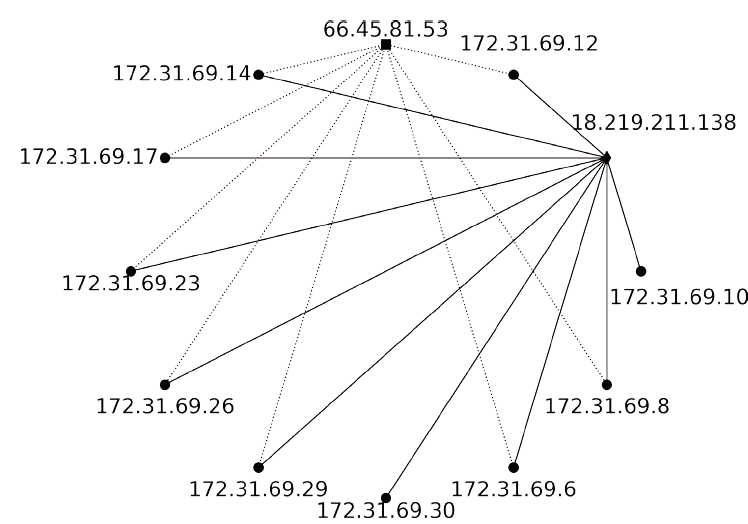
| [1] |
DAYA A A, SALAHUDDIN M A, LIMAM N, et al. A Graph-based Machine Learning Approach for Bot Detection[C]//IEEE. 2019 IEEE Symposium on Integrated Network and Service Management(IM), April 8-12, 2019, Arlington, VA, USA. Piscataway: IEEE, 2019: 144-152.
|
| [2] |
KAUR G. A Novel Distributed Machine Learning Framework for Semi-supervised Detection of Botnet Attacks[C]//IEEE. 2018 11th International Conference on Contemporary Computing (IC3), August 2-4, 2018, Noida, India. Piscataway: IEEE, 2018: 1-7.
|
| [3] |
WANG Kai, CHEN Danwei. Graph Structure Based Anomaly Behavior Detection[C]//Atlantis. 2017 2nd International Conference on Computer Engineering, Information Science & Application Technology (ICCIA 2017), September 8-11, 2017, Beijing, China. Paris: Atlantis Press, 2017: 561-568.
|
| [4] |
WANG Wei, SHANG Yaoyao, HE Yongzhong, et al. BotMark: Automated Botnet Detection with Hybrid Analysis of Flow-based and Graph-based Traffic Behaviors[J]. Information Sciences, 2020, 28(511):284-296.
|
| [5] |
AKOGLU L, MCGLOHON M, FALOUTSOS C. Oddball: Spotting Anomalies in Weighted Graphs[C]//Springer. Pacific-Asia Conference on Knowledge Discovery and Data Mining, June 21-24, 2010, Hyderabad, India. Heidelberg: Springer, 2010: 410-421.
|
| [6] |
NOBLE C C, COOK D J. Graph-based Anomaly Detection[C]//ACM. 2003 9th ACM SIGKDD International Conference on Knowledge Discovery and Data Mining, August 24-27, 2003, Washington, DC, USA. New York: ACM, 2003: 631-636.
|
| [7] |
LAGRAA S, FRANÇOIS J, LAHMADI A, et al. Botgm: Unsupervised Graph Mining to Detect Botnets in Traffic Flows[C]//IEEE. 2017 1st Cyber Security in Networking Conference (CSNet), October 18-20, 2017, Rio De Janeiro, Brazil. Piscataway: IEEE, 2017: 1-8.
|
| [8] |
GAO Jing, LIANG Feng, FAN Wei, et al. On Community Outliers and Their Efficient Detection in Information Networks[C]//ACM. 2010 16th ACM SIGKDD International Conference on Knowledge Discovery and Data Mining, July 25-28, 2010, Washington, DC, USA. New York: ACM, 2010: 813-822.
|
| [9] |
MULLER E, SANCHEZ P I, MULLE Y, et al. Ranking Outlier Nodes in Subspaces of Attributed Graphs[C]//IEEE. 2013 IEEE 29th International Conference on Data Engineering Workshops (ICDEW), April 8-12, 2013, Brisbane, QLD, Australia. Piscataway: IEEE, 2013: 216-222.
|
| [10] |
AKOGLU L, TONG Hanghang, KOUTRA D. Graph Based Anomaly Detection and Description: A Survey[J]. Data Mining & Knowledge Discovery, 2015, 29(3):626-688.
|
| [11] |
BERLINGERIO M, KOUTRA D, ELIASSI-RAD T, et al. NetSimile: A Scalable Approach to Size-Independent Network Similarity[J]. Computer Science, 2012, 12(1):1-28.
|
| [12] |
PAPADIMITRIOU P, DASDAN A, GARCIA-MOLINA H. Web Graph Similarity for Anomaly Detection[J]. Journal of Internet Services & Applications, 2010, 1(1):19-30.
|
| [13] |
GASTON M E, KRAETZL M, WALLIS W D. Using Graph Diameter for Change Detection in Dynamic Networks[EB/OL]. https://www.researchgate.net/publication/267192400_Using_graph_diameter_for_change_detection_in_dynamic_networks, 2006-01-07.
|
| [14] |
KOUTRA D, VOGELSTEIN J T, FALOUTSOS C. DELTACON: A Principled Massive-graph Similarity Function[EB/OL]. https://arxiv.org/abs/1304.4657v1, 2013-04-17.
|
| [15] |
SHARAFALDIN I, LASHKARI A H, GHORBANI A A. Toward Generating a New Intrusion Detection Dataset and Intrusion Traffic Characterization[EB/OL]. https://www.scitepress.org/Documents/2018/66398/, 2018-01-22.
|
 )
)