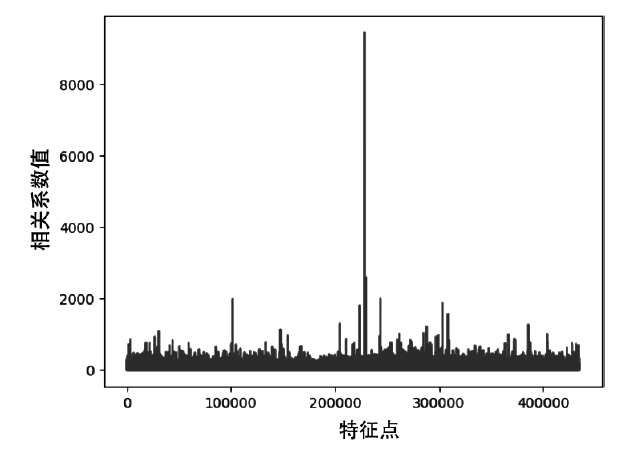
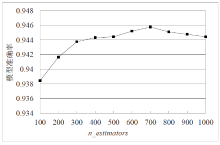
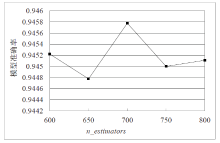
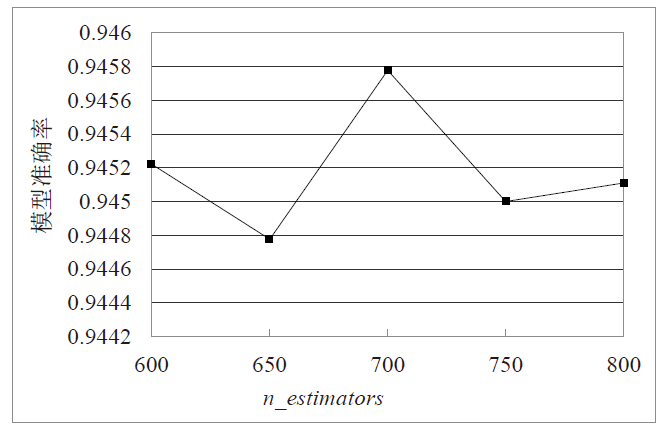
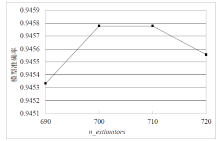
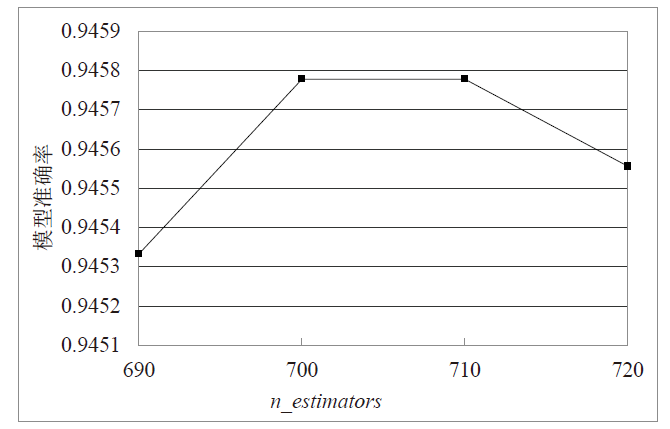
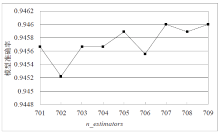
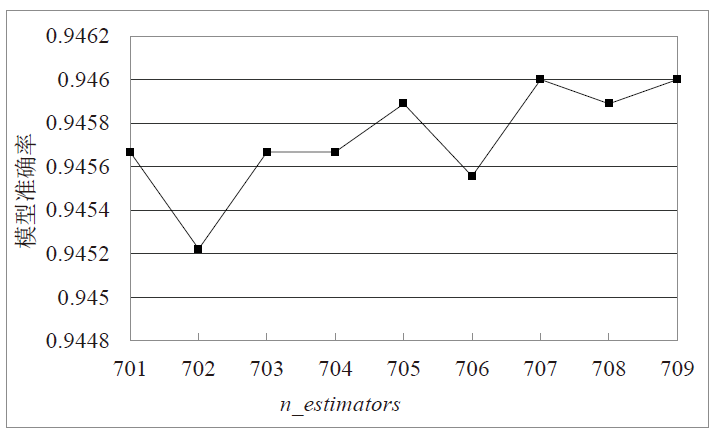
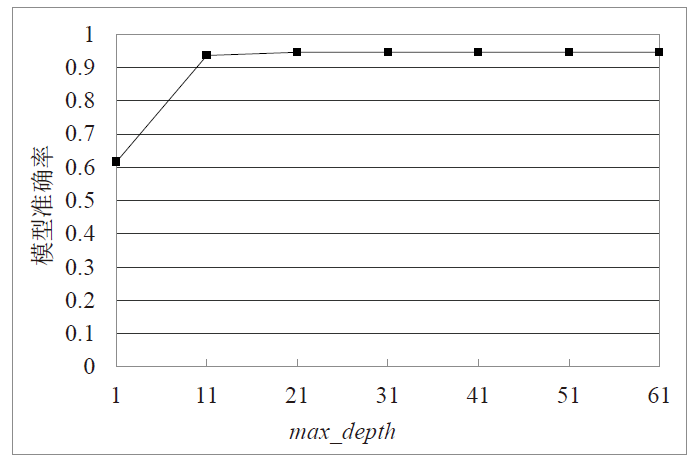
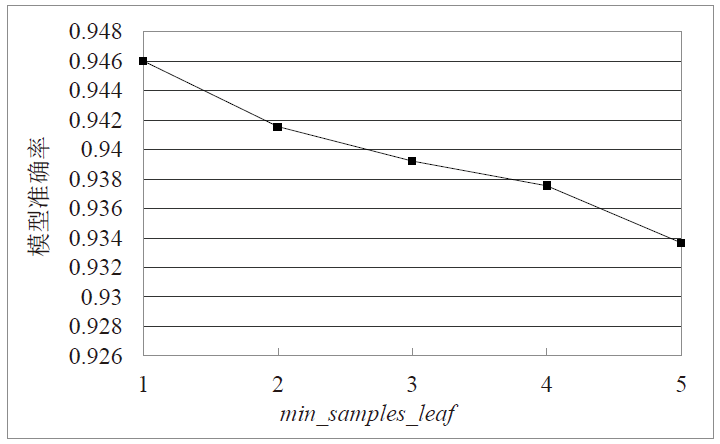
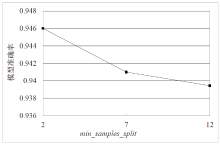
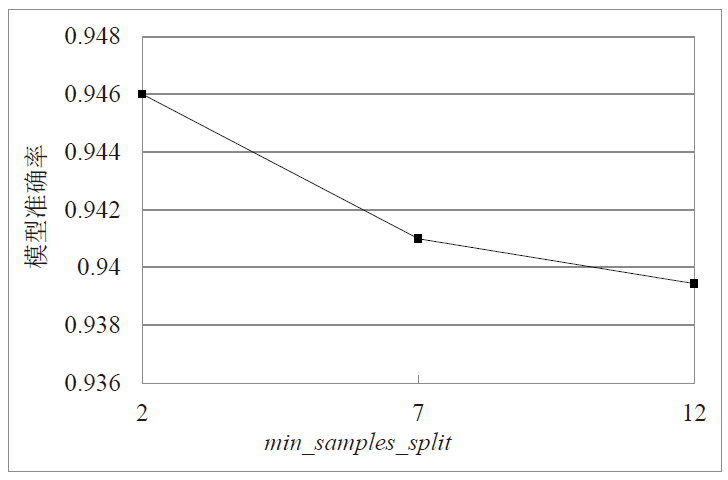
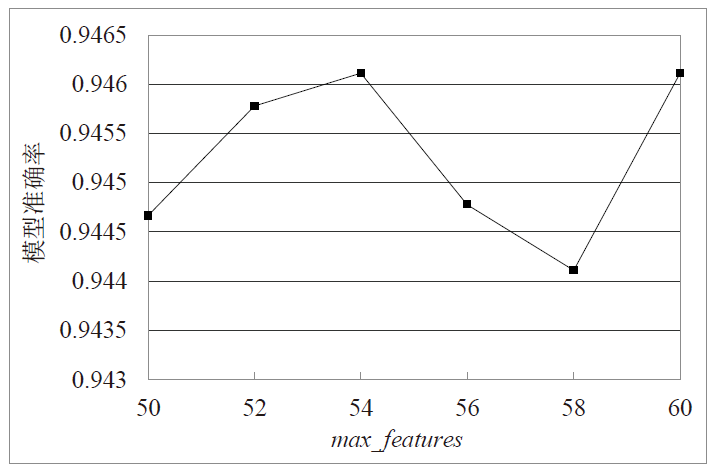
Netinfo Security ›› 2022, Vol. 22 ›› Issue (1): 19-26.doi: 10.3969/j.issn.1671-1122.2022.01.003
Previous Articles Next Articles
Research on the Method of Side Channel Attack Based on RF Algorithm
DUAN Xiaoyi, LI You, LINGHU Yunxing, HU Ronglei( )
)
- Department of Electronics and Information Engineering, Beijing Electronic Science and Technology Institute, Beijing 100070, China
-
Received:2021-06-11Online:2022-01-10Published:2022-02-16 -
Contact:HU Ronglei E-mail:huronglei@sina.com
CLC Number:
Cite this article
DUAN Xiaoyi, LI You, LINGHU Yunxing, HU Ronglei. Research on the Method of Side Channel Attack Based on RF Algorithm[J]. Netinfo Security, 2022, 22(1): 19-26.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2022.01.003
| [1] |
HOSPODAR G, GIERLICHS B, MULDER E D, et al. Machine Learning in Side-channel Analysis: A First Study[J]. Journal of Cryptographic Engineering, 2011, 1(4):293-302.
doi: 10.1007/s13389-011-0023-x URL |
| [2] |
LERMAN L, BONTEMPI G, MARKOWITCH O. A Machine Learning Approach Against a Masked AES[J]. Journal of Cryptographic Engineering, 2014, 5(2):123-139.
doi: 10.1007/s13389-014-0089-3 URL |
| [3] |
HOSPODAR G, GIERLICHS B, MULDER E D, et al. Machine Learning in 420 Side-channel Analysis: a First Study[J]. Journal of Cryptographic Engineering, 2011, 1(4):293-302.
doi: 10.1007/s13389-011-0023-x URL |
| [4] | HEUSER A, ZOHNER M. Constructive Side-channel Analysis and Secure Design[M]. Heidelberg: Intelligent Homicide, 2012. |
| [5] | WANG Feiyu, CHEN Botao, LIU Jianfeng, et al. Combined Attack of Selective Plaintext and Second-order DPA against Masked AES[J]. Journal of Cryptography, 2014, 1(6):525-536. |
| [6] | TIMON B. Non-profiled Deep Learning-based Side-channel Attacks with Sensitivity Analysis[EB/OL]. https://doi.org/10.13154/tches.v2019.i2.107-131, 2021-03-11. |
| [7] | KIM J, PICEK S, HEUSER A, et al. Make Some Noise. Unleashing the Power of Convolutional Neural Networks for Profiled Side-channel Analysis[EB/OL]. https://doi.org/10.13154/tches.v2019.i3.148-179, 2021-03-12. |
| [8] |
BENADJILA R, PROUFF E, STRULLU R, et al. Deep Learning for Side-channel Analysis and Introduction to ASCAD Database[J]. Journal of Cryptographic Engineering, 2020, 10(2):163-188.
doi: 10.1007/s13389-019-00220-8 URL |
| [9] | MA Xiangliang, WANG Hong, LI Bing, et al. Chip Backdoor Instruction Analysis Method Based on Energy Analysis Technology[J]. Chinese Journal of Electronics, 2019, 47(3):686-691. |
|
马向亮, 王宏, 李冰, 等. 基于能量分析技术的芯片后门指令分析方法[J]. 电子学报, 2019, 47(3):686-691.
doi: 10.3969/j.issn.0372-2112.2019.03.024 |
|
| [10] | CAI Xiaomin, LI Renfa, KUANG Shijie, et al. An Energy Trace Compression Method for Differential Power Analysis Attack[EB/OL]. https://ieeexplore.ieee.org/document/9091021, 2021-03-12. |
| [11] | DUAN Xiaoyi, CHEN Dong, FAN Xiaohong, et al. Research and Implementation on Power Analysis Attacks for Unbalanced Data[EB/OL]. https://doi.org/10.1155/2020/5695943, 2020-05-22. |
| [12] | SHI Rongxi, YANG Borui, JIANG Yang, et al. Energy Attack: on Transferring Adversarial Examples[EB/OL]. https://arxiv.org/abs/2109.04300v1, 2021-03-14. |
| [13] | CHARI S, RAO J R. Pankaj Rohatgi: Template Attacks[EB/OL]. https://www.researchgate.net/publication/244437815_Pankaj_Rohatgi_Template_attacks, 2021-03-15. |
| [1] | GUO Chun, CAI Wenyan, SHEN Guowei, ZHOU Xuemei. Research on SQL Injection Attacks Detection Method Based on the Truncated Key Payload [J]. Netinfo Security, 2021, 21(7): 43-53. |
| [2] | MA Xiao, CAI Manchun, LU Tianliang. Malicious Domain Name Training Data Generation Technology Based on Improved CNN Model [J]. Netinfo Security, 2021, 21(10): 69-75. |
| [3] | XU Yu, ZHOU You, LIN Lu, ZHANG Cong. Applied Research of Unsupervised Machine Learning in Game Anti-fraud [J]. Netinfo Security, 2020, 20(9): 32-36. |
| [4] | GUO Chun, CHEN Changqing, SHEN Guowei, JIANG Chaohui. A Ransomware Classification Method Based on Visualization [J]. Netinfo Security, 2020, 20(4): 31-39. |
| [5] | DU Yifeng, GUO Yuanbo. A Dynamic Access Control Method for Fog Computing Based on Trust Value [J]. Netinfo Security, 2020, 20(4): 65-72. |
| [6] | Zewen MA, Yang LIU, Hongping XU, Hang YI. DoS Traffic Identification Technology Based on Integrated Learning [J]. Netinfo Security, 2019, 19(9): 115-119. |
| [7] | Guanheng CHEN, Jinshu SU. Abnormal Traffic Detection Algorithm Based on Deep Neural Network [J]. Netinfo Security, 2019, 19(6): 68-75. |
| [8] | Chunqi TIAN, Jing LI, Wei WANG, Liqing ZHANG. A Method for Improving the Performance of Spark on Container Cluster Based on Machine Learning [J]. Netinfo Security, 2019, 19(4): 11-19. |
| [9] | Jianwei HU, Wei ZHAO, Zheng YAN, Rui ZHANG. Analysis and Implementation of SQL Injection Vulnerability Mining Technology Based on Machine Learning [J]. Netinfo Security, 2019, 19(11): 36-42. |
| [10] | Jian ZHANG, Bohan CHEN, Liangyi GONG, Zhaojun GU. Research on Malware Detection Technology Based on Image Analysis [J]. Netinfo Security, 2019, 19(10): 24-31. |
| [11] | Weiping WEN, Jingwei LI, Yingnan JIAO, Hailin LI. A Vulnerability Detection Method Based on Random Detection Algorithm and Information Aggregation [J]. Netinfo Security, 2019, 19(1): 1-7. |
| [12] | Yingchao YU, Lin DING, Zuoning CHEN. Research on Attacks and Defenses towards Machine Learning Systems [J]. Netinfo Security, 2018, 18(9): 10-18. |
| [13] | Yang ZHANG, Yuangang YAO. Research on Network Intrusion Detection Based on Xgboost [J]. Netinfo Security, 2018, 18(9): 102-105. |
| [14] | Weiping WEN, Bozhi WU, Yingnan JIAO, Yongqiang HE. Design and Implementation on Malicious Documents Detection Tool Based on Machine Learning [J]. Netinfo Security, 2018, 18(8): 1-7. |
| [15] | Xiang HE, Sheng LIU, Jiguo JIANG. Comparative Study of Intrusion Detection Methods Based on Machine Learning [J]. Netinfo Security, 2018, 18(5): 1-11. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||