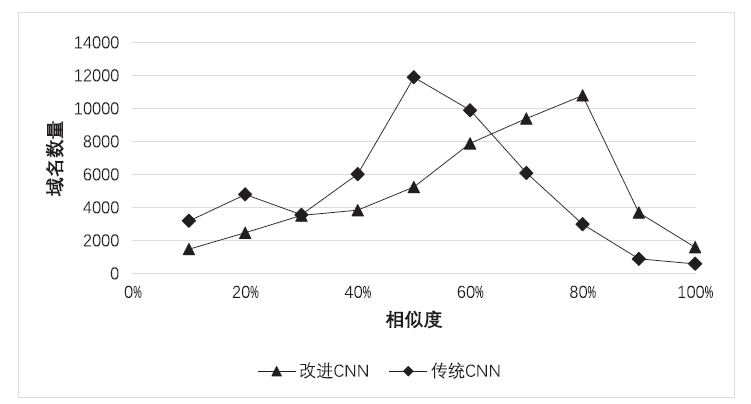
Netinfo Security ›› 2021, Vol. 21 ›› Issue (10): 69-75.doi: 10.3969/j.issn.1671-1122.2021.10.010
Previous Articles Next Articles
Malicious Domain Name Training Data Generation Technology Based on Improved CNN Model
MA Xiao, CAI Manchun( ), LU Tianliang
), LU Tianliang
- College of Information Network Security, People’s Public Security University of China, Beijing 100038, China
-
Received:2021-05-06Online:2021-10-10Published:2021-10-14 -
Contact:CAI Manchun E-mail:caimanchun@ppsuc.edu.cn
CLC Number:
Cite this article
MA Xiao, CAI Manchun, LU Tianliang. Malicious Domain Name Training Data Generation Technology Based on Improved CNN Model[J]. Netinfo Security, 2021, 21(10): 69-75.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2021.10.010
| [1] | YUAN Chen, QIAN Liping, ZHANG Hui, et al. Generation of Malicious Domain Training Data Based on Generative Adversarial Network[J]. Application Research of Computers, 2019, 36(5):1540-1543. |
| 袁辰, 钱丽萍, 张慧, 等. 基于生成对抗网络的恶意域名训练数据生成[J]. 计算机应用研究, 2019, 36(5):1540-1543. | |
| [2] | YERIMA S, ALZAYLAEE M, SHAJAN A. Deep Learning Techniques for Android Botnet Detection[J]. Electronics (Basel), 2021, 10(4):519-535. |
| [3] | LIN Shaoqing, ZHONG Shangping, CHENG Kaizhi, et al. Method with Pre-trained Word Vectors for Detecting Wordlist-based Malicious Domain Names[J]. Journal of Physics Conference Series, 2021, 1757(1):12171-12177. |
| [4] |
TRAN D, MAC H, TONG V, et al. A LSTM Based Framework for Handling Multiclass Imbalance in DGA Botnet Detection[J]. Neurocomputing, 2018, 275(1):2401-2413.
doi: 10.1016/j.neucom.2017.11.018 URL |
| [5] | WOODBRIDGE J, ANDERSON H S, AHUJA A, et al. Predicting Domain Generation Algorithms with Long Short-term Memory Networks[EB/OL]. https://arxiv.org/abs/1611. 00791, 2016-11-02. |
| [6] | XU Guotian. Generation Algorithm Crack Based on DGA Domain Name of Malicious Program[J]. Netinfo Security, 2017, 17(9):26-29. |
| 徐国天. 基于DGA的恶意程序域名生成算法破解[J]. 信息网络安全, 2017, 17(9):26-29. | |
| [7] | YANG Luhui, LIU Guangjie, ZHAI Jiangtao, et al. Improved Algorithm for Detection of the Malicious Domain Name Based on the Convolutional Neural Network[J]. Journal of Xidian University, 2020, 47(1):37-43. |
| 杨路辉, 刘光杰, 翟江涛, 等. 一种改进的卷积神经网络恶意域名检测算法[J]. 西安电子科技大学学报, 2020, 47(1):37-43. | |
| [8] |
CUCCHIARELLI A, MORBIDONI C, SPALAZZI L, et al. Algorithmically Generated Malicious Domain Names Detection Based on N-grams Features[J]. Expert Systems with Applications, 2021, 170(5):114551-114566.
doi: 10.1016/j.eswa.2020.114551 URL |
| [9] | WANG Yuanyuan, WU Chunjiang, LIU Qihe, et al. Overview of Malicious Domain Name Detection and Appliciation[J]. Computer Applications and Software, 2019, 36(9):310-316. |
| 王媛媛, 吴春江, 刘启和, 等. 恶意域名检测研究与应用综述[J]. 计算机应用与软件, 2019, 36(9):310-316. | |
| [10] | CHEN Zhao, XU Ruifeng, GUI Lin, et al. Combining Convolutional Neural Networks and Word Sentiment Sequences Features for Chinese Text Sentiment Analysis[J]. Journal of Chinese Information Processing, 2015, 29(6):172-178. |
| 陈钊, 徐睿峰, 桂林, 等. 结合卷积神经网络和词语情感序列特征的中文情感分析[J]. 中文信息学报, 2015, 29(6):172-178. | |
| [11] | WANG Jingbo, MENG Lingjun. Convolutional Neural Network Face Detection Algorithm[J]. Application of Electronic Technique, 2020, 46(1):34-38. |
| 王静波, 孟令军. 卷积神经网络人脸检测算法[J]. 电子技术应用, 2020, 46(1):34-38. | |
| [12] | LU Yubo, LIU Derun, CAI Yichao, et al. Chinese Weibo Sentiment Classification Based on cw2vec and CNN-BiLSTM Attention Model[J]. Software Guide, 2021, 20(3):51-56. |
| 卢昱波, 刘德润, 蔡奕超, 等. 基于cw2vec与CNN-BiLSTM注意力模型的中文微博情感分类[J]. 软件导刊, 2021, 20(3):51-56. | |
| [13] | CAO Zhengzhi, YE Chunming. Prediction of Bearing Remaining useful Life Based on Parallel CNN-SE-Bi-LSTM[EB/OL]. https://doi.org/10.19734/j.issn.1001-3695.2020.08.0224, 2021-03-05. |
| 曹正志, 叶春明. 基于并联CNN-SE-Bi-LSTM的轴承剩余使用寿命预测[EB/OL]. https://doi.org/10.19734/j.issn.1001-3695.2020.08.0224, 2021-03-05. | |
| [14] |
ZHONG Rui, WANG Rui, ZOU Yang, et al. Graph Attention Networks Adjusted Bi-LSTM for Video Summarization[J]. IEEE Signal Processing Letters, 2021, 28(1):663-667.
doi: 10.1109/LSP.2021.3066349 URL |
| [15] | YIN Liangliang, SUN Hongguang, JIA Huiting, et al. Text Sentiment Analysis Method Based on a Two-way Multi-dimensional Selfattention Mechanism[J]. China Computer and Communication, 2019, 7(9):45-48. |
| 尹良亮, 孙红光, 贾慧婷, 等. 基于双向多维度自注意力机制的文本情感分析方法[J]. 信息与电脑(理论版), 2019, 7(9):45-48. | |
| [16] | DU Lin, CAO Dong, LIN Shuyuan, et al. Extraction and Automatic Classification of TCM Medical Records Based on Attention Mechanism of BERT and Bi-LSTM[J]. Computer Science, 2020, 47(S2):416-420. |
| 杜琳, 曹东, 林树元, 等. 基于BERT与Bi-LSTM融合注意力机制的中医病历文本的提取与自动分类[J]. 计算机科学, 2020, 47(S2):416-420. | |
| [17] | CHENG Hua, CAI Jing, FANG Yiquan. RL-Gen: A Character Level Text Generation Framework with Reinforcement Learning in Domain Generation Algorithm Case [C]//Springer. International Conference on Neural Information Processing, December 12-15, 2019, Sydney, Australia. Berlin: Springer, 2019: 690-697. |
| [18] | LUO Quan, LIU Zhi. A Word Operation Exercises Auto-scoring Algorithm Based on Levenshtein Distance[J]. Modern Computer, 2020, 32(1):90-93. |
| 罗泉, 刘芝. 基于Levenshtein距离的Word操作题自动评分算法[J]. 现代计算机, 2020, 32(1):90-93. | |
| [19] | CAMARA A, DAN G. Research on Information Processing in Management Information System of Soguifret S.a.r.l Company in Guinea Based Levenshtein Algorithm[J]. Journal of Physics Conference Series, 2021, 1820(1):12155-12161. |
| [20] | WANG Jing, BAO Gui. Comparison of Bayesian Statistics with Traditional Statistical Methods[J]. Statistics and Decision, 2021, 37(1):24-29. |
| 王婧, 鲍贵. 贝叶斯统计与传统统计方法的比较[J]. 统计与决策, 2021, 37(1):24-29. | |
| [21] | LI Jing. Land Complex was Classified Based on an Object-oriented Approach Based on Random Forest Versus J48 Decision Tree[J]. Technology Innovation and Application, 2021, 1(10):136-139. |
| 李靖. 基于随机森林与J48决策树的面向对象方法的土地覆被分类[J]. 科技创新与应用, 2021, 1(10):136-139. | |
| [22] | ZHENG Xiandong, FENG Wenlong, HUANG Mengxing, et al. Optimization of PBFT Algorithm Based on Improved C4.5[J]. Mathematical Problems in Engineering, 2021, 2021(2):1-7. |
| [23] | WANG Yanguang, ZHU Hongbin, XU Weichao. A Review on ROC Curve and Analysis[J]. Journal of Guangdong University of Technology, 2021, 38(1):46-53. |
| 王彦光, 朱鸿斌, 徐维超. ROC曲线及其分析方法综述[J]. 广东工业大学学报, 2021, 38(1):46-53. |
| [1] | LI Yanlin, CAI Manchun, LU Tianliang, XI Rongkang. A Website Fingerprinting Attack Method via Convolutional Neural Network Optimized by Genetic Algorithm [J]. Netinfo Security, 2021, 21(9): 59-66. |
| [2] | GUO Chun, CAI Wenyan, SHEN Guowei, ZHOU Xuemei. Research on SQL Injection Attacks Detection Method Based on the Truncated Key Payload [J]. Netinfo Security, 2021, 21(7): 43-53. |
| [3] | XU Guotian, SHENG Zhenwei. DGA Malicious Domain Name Detection Method Based on Fusion of CNN and LSTM [J]. Netinfo Security, 2021, 21(10): 41-47. |
| [4] | XU Yu, ZHOU You, LIN Lu, ZHANG Cong. Applied Research of Unsupervised Machine Learning in Game Anti-fraud [J]. Netinfo Security, 2020, 20(9): 32-36. |
| [5] | WANG Xiangyi, ZHANG Jian. Abnormal Behavior Detection of Virtualization Platform Based on Image and Machine Learning [J]. Netinfo Security, 2020, 20(9): 92-96. |
| [6] | LIU Jing, ZHANG Xueqian, LIU Quanming. Research on Captcha Recognition of Lightweight Convolutional Neural Network with Gabor [J]. Netinfo Security, 2020, 20(7): 77-84. |
| [7] | LUO Zheng, ZHANG Xueqian. A Malicious Domain Name Detection Model Based on S-Kohonen Neural Network Optimized by Evolutionary Thinking Algorithm [J]. Netinfo Security, 2020, 20(6): 82-89. |
| [8] | ZHANG Leihua, HUANG Jin, ZHANG Tao, WANG Shengyu. Portrait Intelligent Analysis Application and Algorithm Optimization in Video Investigation [J]. Netinfo Security, 2020, 20(5): 88-93. |
| [9] | GUO Chun, CHEN Changqing, SHEN Guowei, JIANG Chaohui. A Ransomware Classification Method Based on Visualization [J]. Netinfo Security, 2020, 20(4): 31-39. |
| [10] | DU Yifeng, GUO Yuanbo. A Dynamic Access Control Method for Fog Computing Based on Trust Value [J]. Netinfo Security, 2020, 20(4): 65-72. |
| [11] | GU Zhaojun, HAO Jintao, ZHOU Jingxian. Classification of Malicious Network Traffic Based on Improved Bilinear Convolutional Neural Network [J]. Netinfo Security, 2020, 20(10): 67-74. |
| [12] | Zewen MA, Yang LIU, Hongping XU, Hang YI. DoS Traffic Identification Technology Based on Integrated Learning [J]. Netinfo Security, 2019, 19(9): 115-119. |
| [13] | Guanheng CHEN, Jinshu SU. Abnormal Traffic Detection Algorithm Based on Deep Neural Network [J]. Netinfo Security, 2019, 19(6): 68-75. |
| [14] | Chunqi TIAN, Jing LI, Wei WANG, Liqing ZHANG. A Method for Improving the Performance of Spark on Container Cluster Based on Machine Learning [J]. Netinfo Security, 2019, 19(4): 11-19. |
| [15] | Jianwei HU, Wei ZHAO, Zheng YAN, Rui ZHANG. Analysis and Implementation of SQL Injection Vulnerability Mining Technology Based on Machine Learning [J]. Netinfo Security, 2019, 19(11): 36-42. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||