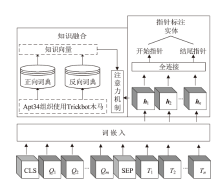
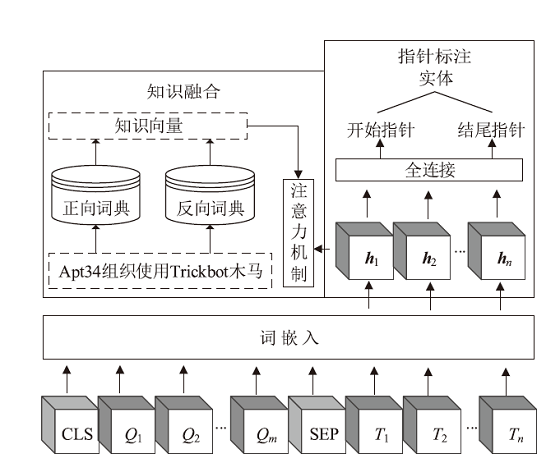
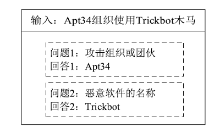
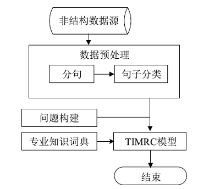
| [1] |
LAFFERTY J, MCCALLUM A, PEREIRA F. Conditional Random Fields: Probabilistic Models for Segmenting and Labeling Sequence Data [C]//ACM. 18th International Conference on Machine Learning, June 1-28, 2001, San Prancisco, CA, USA. San Francisco: Margan Kaufmann, 2001: 282-289.
|
| [2] |
SUTTON C, MCCALLUM A, ROHANIMANESH K, et al. Dynamic Conditional Random Fields: Factorized Probabilistic Models for Labeling and Segmenting Sequence Data[J]. Journal of Machine Learning Research, 2007, 8(3):693-723.
|
| [3] |
HOCHREITER S, SCHMIDHUNER J. Long Short-term Memory[J]. Neural Computation, 1997, 9(8):1735-1780.
doi: 10.1162/neco.1997.9.8.1735
URL
|
| [4] |
CHIU J, NICHOLS E. Named Entity Recognition with Bidirectional LSTM-CNNs[EB/OL]. https://arxiv.org/pdf/1511.08308.pdf, 2021-02-22.
|
| [5] |
VASWANI A, SHAZEER N, PARMAR N, et al. Attention Is All You Need [C]//ACM. 31st Internation Conference on Neural Information Processing Systems, December 4-9, 2017, Red Hook, NY, USA. New York: ACM, 2017: 6000-6010.
|
| [6] |
RADFORD A, NARASIMHAN K, SALIMANS T, et al. Improving Language Understanding by Generative Pre-training[EB/OL]. https://s3-us-west-2.amazonaws.com/openai-assets/research-covers/language-unsupervised/language_understanding_paper.pdf, 2018-11-19.
|
| [7] |
DEVLIN J, CHANG Mingwei, LEE K, et al. Bert: Pre-training of Deep Bidirectional Transformers for Language Understanding[EB/OL]. https://arxiv.org/abs/1810.04805, 2019-05-24.
|
| [8] |
LI Xiaoya, FENG Jingrong, MENG Yuxian, et al. A Unified MRC Framework for Named Entity Recognition[EB/OL]. https://arxiv.org/abs/1910.11476, 2020-05-23.
|
| [9] |
LIAO Xiaojing, YUAN Kan, WANG Xiaofeng, et al. Acing the IOC Game: Toward Automatic Discovery and Analysis of Open-source Cyber Threat Intelligence [C]//ACM. ACM SIGSAC Conference on Computer & Communications Security, October 24-28, 2016, Vienna, Austria. New York: ACM, 2016: 755-766.
|
| [10] |
LONG Zi, TAN Lianzhi, ZHOU Shengping, et al. Collecting Indicators of Compromise from Unstructured Text of Cybersecurity Articles using Neural-based Sequence Labelling [C]//IEEE. 2019 International Joint Conference on Neural Networks(IJCNN), July 14-19, 2019, Budapest, Hungary. New Jersey: IEEE, 2019: 1-8.
|
| [11] |
DIONÍSIO N, ALVES F, FERREIRA P M, et al. Cyberthreat Detection from Twitter Using Deep Neural Networks [C]//IEEE. 2019 International Joint Conference on Neural Networks(IJCNN), July 14-19, 2019, Budapest, Hungary. New Jersey: IEEE, 2019: 1-8.
|
| [12] |
QIN Ya, SHEN Guowei, ZHAO Wenbo, et al. A Network Security Entity Recognition Method based on Feature Template and Cnn-bilstm-crf[J]. Frontiersof Information Technology & Electronic Engineering, 2019, 20(6):872-884.
|
| [13] |
DASGUPTA S, PIPLAI A, KOTAL A, et al. A Comparative Study of Deep Learning Based Named Entity Recognition Algorithms for Cybersecurity [C]//IEEE. 2020 IEEE International Conference on Big Data(Big Data), December 10-13, 2020, Atlanta, GA, USA. New Jersey: IEEE, 2021: 2596-2604.
|
| [14] |
WANG Qinxin, YANG Wang. Extraction of Threat Intelligence Entities Based on STIX[J]. Cyberspace Security, 2020, 11(8):86-91.
|
|
王沁心, 杨望. 基于STIX标准的威胁情报实体抽取研究[J]. 网络空间安全, 2020, 11(8):86-91.
|
| [15] |
WU Han, LI Xiaoyong, GAO Yali. An Effective Approach of Named Entity Recognition for Cyber Threat Intelligence [C]//IEEE. 4th Information Technology, Networking, Electronic and Automation Control Conference(IT-NEC), June 12-14, 2020, Chongqing, China. New Jersey: IEEE, 2020: 1370-1374.
|
| [16] |
MÉTAIS E, MEZIANE F, HORACEK H, et al. Natural Language Processing and Information Systems[M]. Cham: Springer Inter-national Publishing, 2020.
|